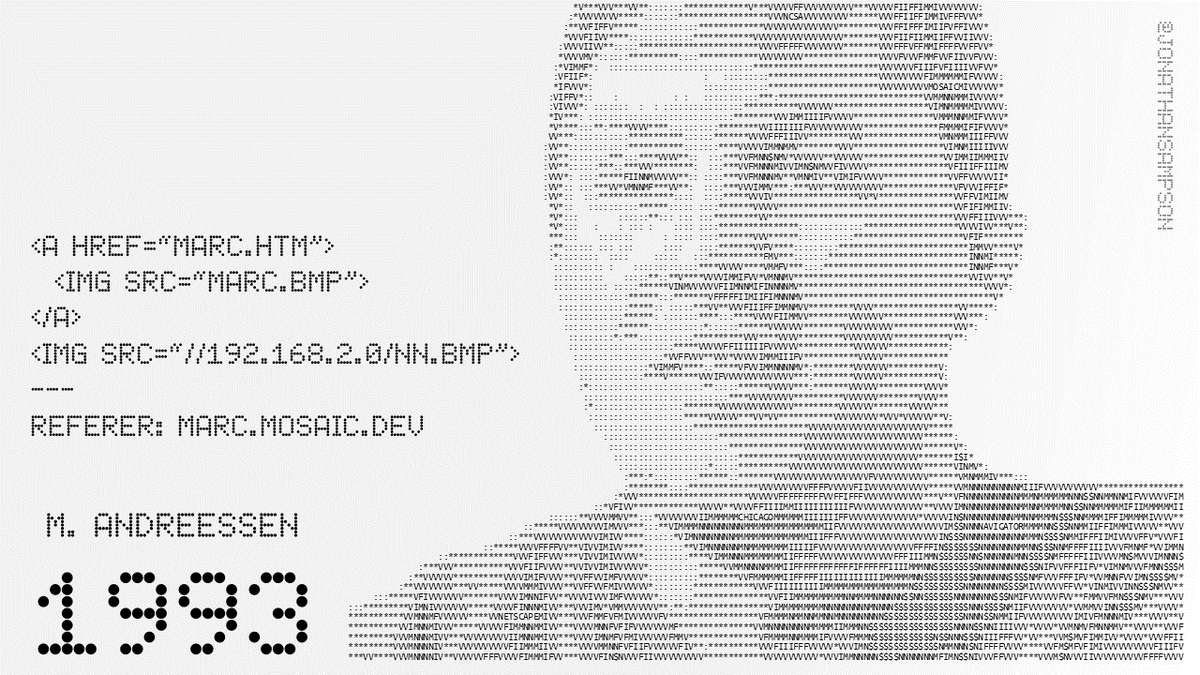
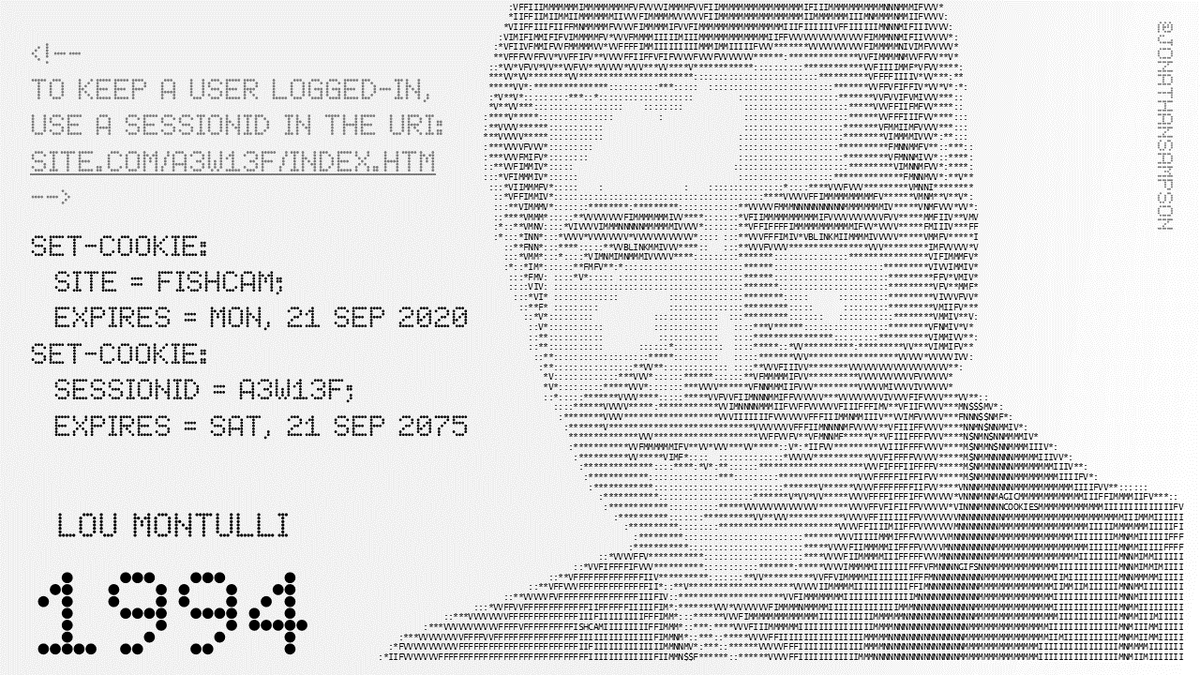
Curious what happens when you fire up a web browser for the first time? Me too. I often do this for @brave to make sure things are staying neat and tidy.
Today I would like to do it for a few other web browsers. First, let's take a look at Opera.
Today I would like to do it for a few other web browsers. First, let's take a look at Opera.
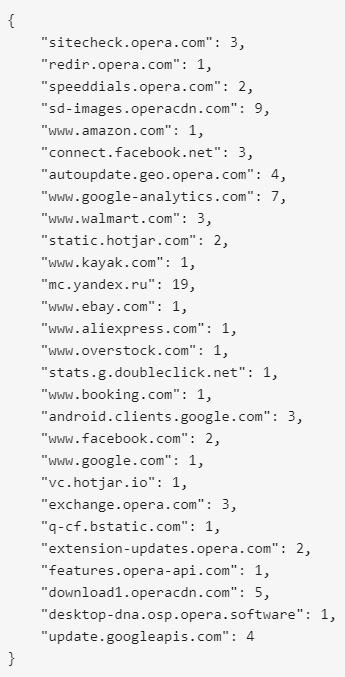
Launching Opera (and leaving it in its default state for a few minutes) resulted in the following calls being made.
Calls to opera and operacdn made sense. But 19 calls to yandex.ru was a surprise. Note also Amazon, FB, Walmart, Kayak, Ebay, Ali Express, and more.
Calls to opera and operacdn made sense. But 19 calls to yandex.ru was a surprise. Note also Amazon, FB, Walmart, Kayak, Ebay, Ali Express, and more.
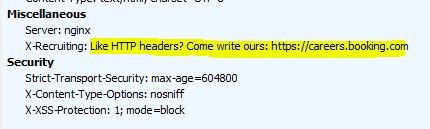
Some of these are fairly heavy calls too; here's a subset ordered by their response size (descending). Overstock sets a dozen cookies. Amazon, Kayak, Ali Express, and more set me up with novel session IDs as well. Google is there too. Ready to monitor my movement across the Web. 

On a fun note, booking.com apparently knew that we'd inspect their headers 😉 
Back to Yandex though. Opera not only pings them, but informs them that I am setting up a new profile with Opera (via the referer header and query string). This header also goes to Facebook, Google, and hotjar. All of these now know that I am a fresh Opera user.
A closer look reveals that Opera is sending extra bits too, including my native resolution, browser window size, and a lot more. Unfortunately, it isn't clear what the other bits are representing. One parameter is called "gdpr" with a value of 14. I wonder what that one is. 

Another call is made to android.clients.google.com, and includes a unique user ID, as well as a distinct device and sender ID. Why is Opera sending this information to Google? 
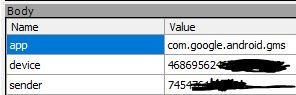
Just as a reminder, this is a fresh profile. No previous activity. And no activity taken beyond opening the browser up for the first time.
Ah, I forgot to mention the call to walmart.com over HTTP, which responds with a 301 redirect. AFAIK, that's an opportunity for trouble.
Compared to Opera, Vivaldi is very lightweight. Firing up a fresh profile in Vivaldi resulted in only 31 or so calls (most of which are to vivaldi.com).
This looks pretty standard. It downloads the SafeBrowsing database, some 835K extension, and a domain blacklist.

This looks pretty standard. It downloads the SafeBrowsing database, some 835K extension, and a domain blacklist.
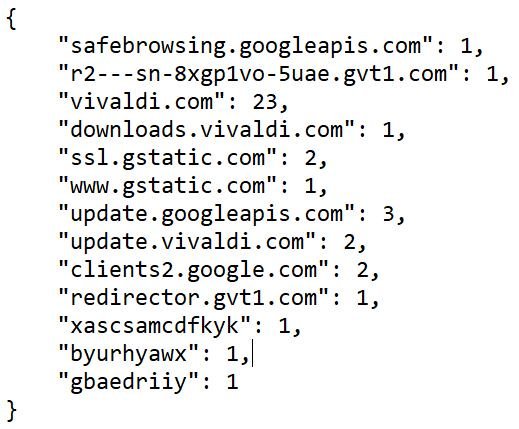
Unlike Opera, Vivaldi doesn't inform others that I am a fresh user (via the Referer header).
The extension they download appears to be for Chrome Cast. This, too, is expected for compat reasons. I'd say Vivaldi gets a clean bill of health based on this cursory glance. Nice job, @vivaldibrowser!
Note, again, that I am only reviewing the first-run experience. Not making any claims about how privacy/secure things are beyond that.
• • •
Missing some Tweet in this thread? You can try to
force a refresh