Revealing eight buildings across the US, hidden in plain sight, that documents & sources indicate are central to one of NSA's largest & most controversial internet surveillance programs: theintercept.com/2018/06/25/att… 

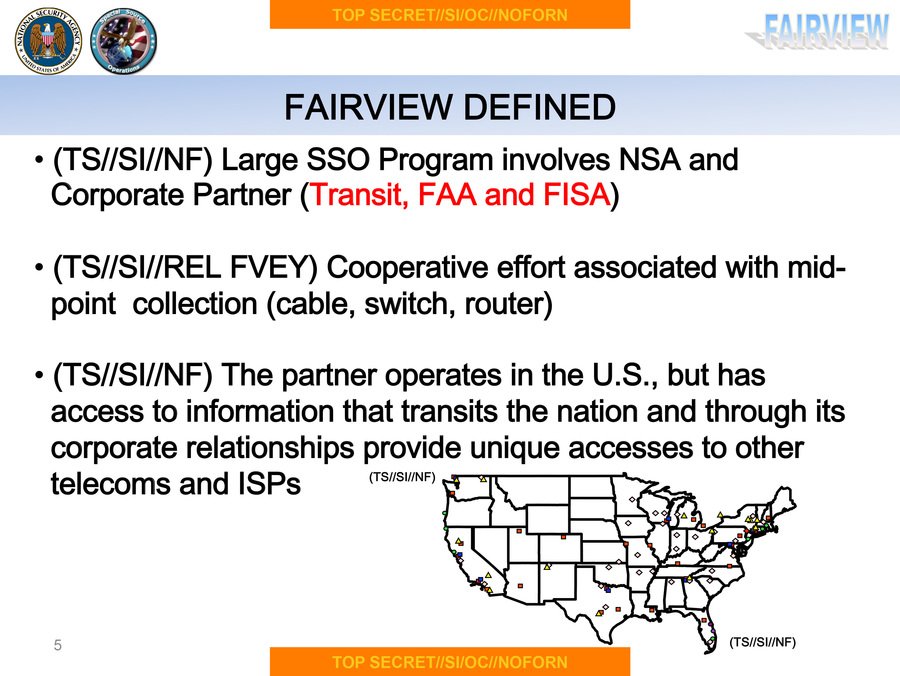
The eight buildings are involved in an NSA program called FAIRVIEW, which has collected communications from AT&T's networks since 1985.
In 2003, the agency launched an internet surveillance initiative under FAIRVIEW & had within a few months swept up some 400 billion records about people’s online communications. AT&T sent millions of emails weekly to an NSA “keyword selection system.”
NSA says it values AT&T not only because it “has access to information that transits the nation,” but also because it maintains unique relationships with other phone and internet providers. 
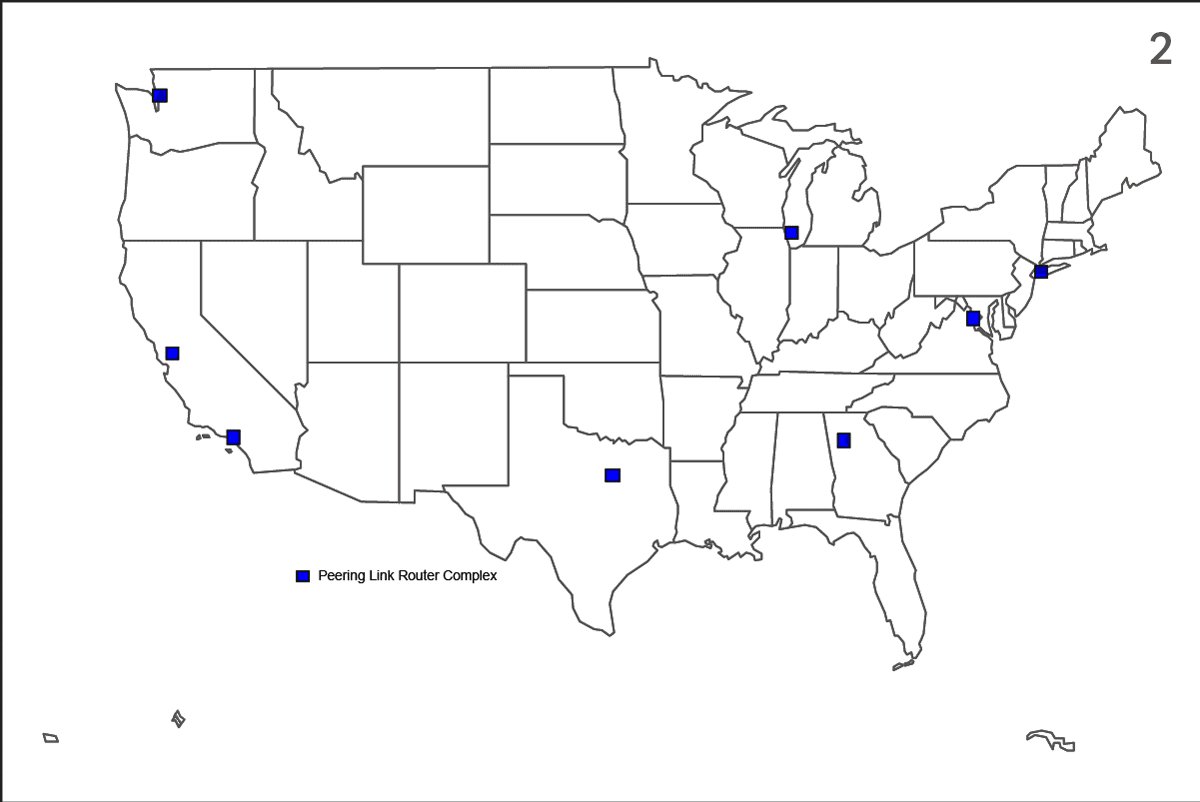
Our story shows how NSA used AT&T's infrastructure to tap into communications processed by other companies. Data from the likes of Sprint, Cogent, Level 3, Telia, Tata, Telecom Italia, & Deutsche Telekom is sent across AT&T's networks as part of so-called "peering" exchanges.
The NSA monitors what it calls "peering circuits" inside the eight buildings, which one former AT&T technician said "are liable to carry everybody’s [internet] traffic at one point or another during the day, or the week, or the year.”
AT&T developed a strategy to help the NSA electronically eavesdrop the peering circuits at the eight sites, which the agency said connected to the “common backbone,” major data routes carrying internet traffic. 
AT&T worked with the NSA to rank communications flowing through its networks on the basis of intelligence value, prioritizing data depending on which country it was derived from, according to a top-secret document.
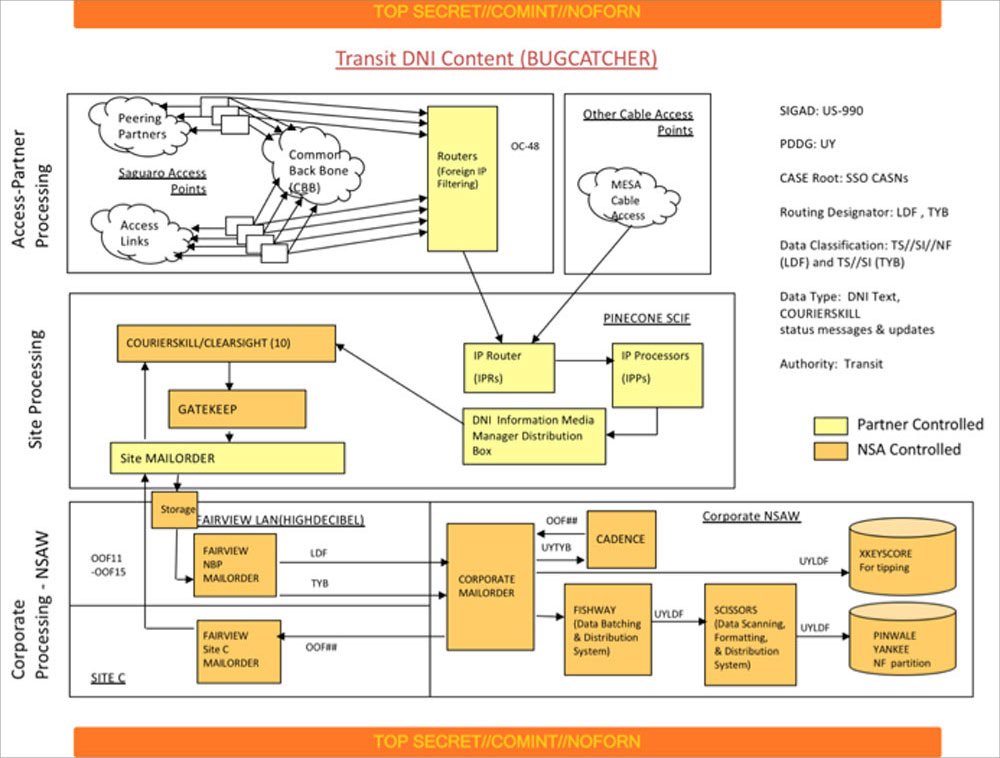
Internet data NSA collects from AT&T’s networks is sent to a “centralized processing facility” code-named PINECONE, located somewhere in New Jersey. There, the internet data passes through an AT&T “distribution box” to two NSA systems.
We used maps of NSA's infrastructure & AT&T's networks to pinpoint the eight facilities where the surveillance takes place. They are towering windowless skyscrapers & fortress-like concrete structures, built to withstand earthquakes & even nuclear attack.
We sought out AT&T employees to confirm the locations of the buildings.
“You put a gun to my head,” said AT&T’s former chief technology officer, “I’m not going to tell you.”
Other people we spoke to, however, were more forthcoming.
“You put a gun to my head,” said AT&T’s former chief technology officer, “I’m not going to tell you.”
Other people we spoke to, however, were more forthcoming.
The buildings are in:
Atlanta theintercept.com/2018/06/25/att…
Chicago theintercept.com/2018/06/25/att…
Dallas theintercept.com/2018/06/25/att…
LA theintercept.com/2018/06/25/att…
NYC theintercept.com/2018/06/25/att…
San Francisco theintercept.com/2018/06/25/att…
Seattle theintercept.com/2018/06/25/att…
DC theintercept.com/2018/06/25/att…



Atlanta theintercept.com/2018/06/25/att…
Chicago theintercept.com/2018/06/25/att…
Dallas theintercept.com/2018/06/25/att…
LA theintercept.com/2018/06/25/att…
NYC theintercept.com/2018/06/25/att…
San Francisco theintercept.com/2018/06/25/att…
Seattle theintercept.com/2018/06/25/att…
DC theintercept.com/2018/06/25/att…




“It’s eye-opening & ominous the extent to which this is happening right here on American soil,” said the Brennan Center's @LizaGoitein. “It puts a face on surveillance that we could never think of before in terms of actual buildings...in our own cities, in our own backyards.”
AT&T said it was “required by law to provide information to government & law enforcement entities by complying with court orders, subpoenas, lawful discovery requests, & other legal requirements.”
You can read the full story here: theintercept.com/2018/06/25/att… And review the documents we published here: documentcloud.org/public/search/…
Another bit from the story: a previously undisclosed NSA memo reveals new details about a secret Foreign Intelligence Surveillance Court ruling from 2011, which declared one of the agency's surveillance programs to be unconstitutional.
A judge at the court ruled the agency had been unlawfully collecting tens of thousands of internet communications from “non-target United States persons and persons in the United States," b/c its systems were “generally incapable of distinguishing” between some kinds of data.
The memo reveals for the first time exactly what was happening: the agency was sweeping up people's entire email inboxes if they sent or received a single message that mentioned an identifier - like a phone number or email address - associated w/ a person on a target list.
That could have potentially included, for example, emails sent between two American lawyers or journalists, which mentioned a phone number for a person on NSA's target list. The lawyers or journalists inboxes would then have been swept up & their messages stored in NSA databases.
The judge, John D. Bates, said the spying violated the Fourth Amendment, which protects against unreasonable searches and seizures. He ordered the agency to shut down the surveillance or modify the program so its analysts would not view the unlawfully collected messages.
The agency chose the latter option, and created a “cautionary banner” that warned its analysts not to read particular messages. But that did not solve the problem. And the violations continued for several years.
You can read the memo here: theintercept.com/document/2018/… The court ruling here: documentcloud.org/documents/4522… And the full story here: theintercept.com/2018/06/25/att…
An NSA spokesperson said he wouldn't "confirm nor deny [the agency's] role in alleged classified intelligence activities." NSA operates "under the legal authorities established by Congress & is bound by both policy & law to protect US persons’ privacy & civil liberties,” he said.
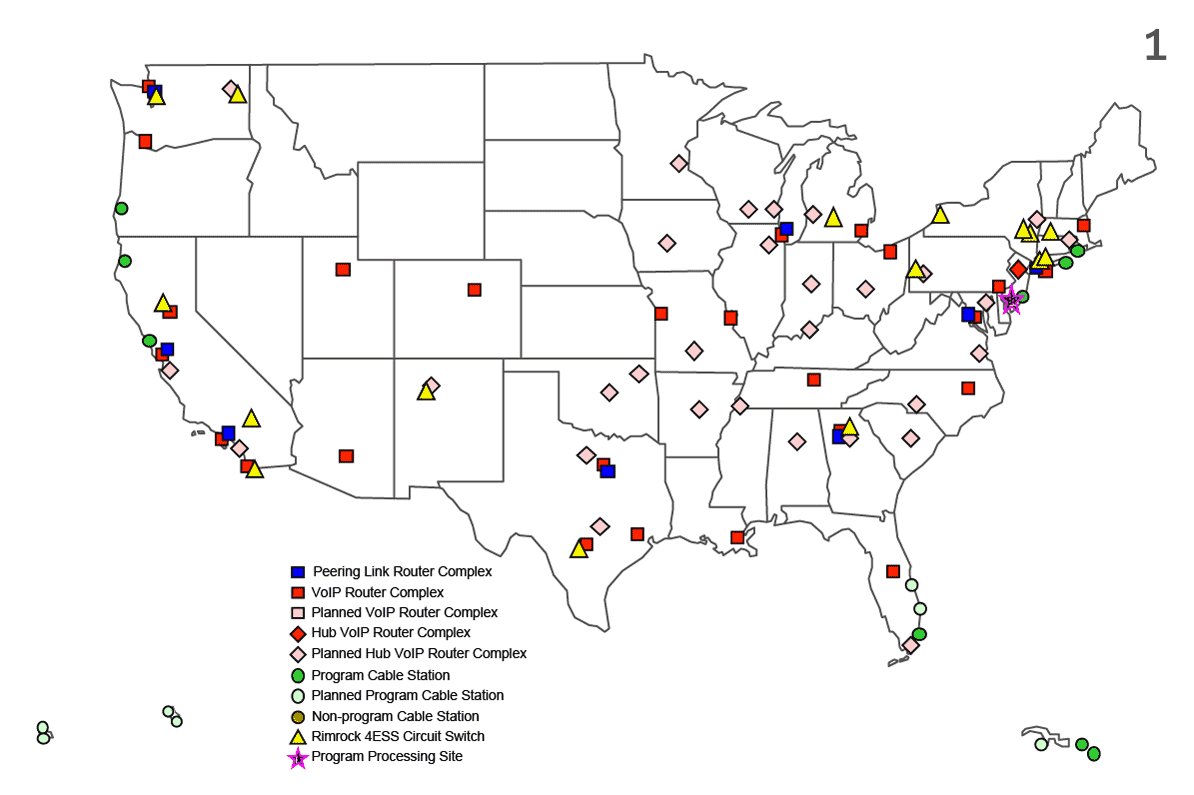
Here are non-animated versions of the maps that appear in the story, for those who're interested. Numbers 1 & 2 are derived from an NSA document about the FAIRVIEW program; 3 & 4 are AT&T network maps. Learn more about them in my colleague Henrik's thread: 



https://twitter.com/moltke/status/1011221135411826689
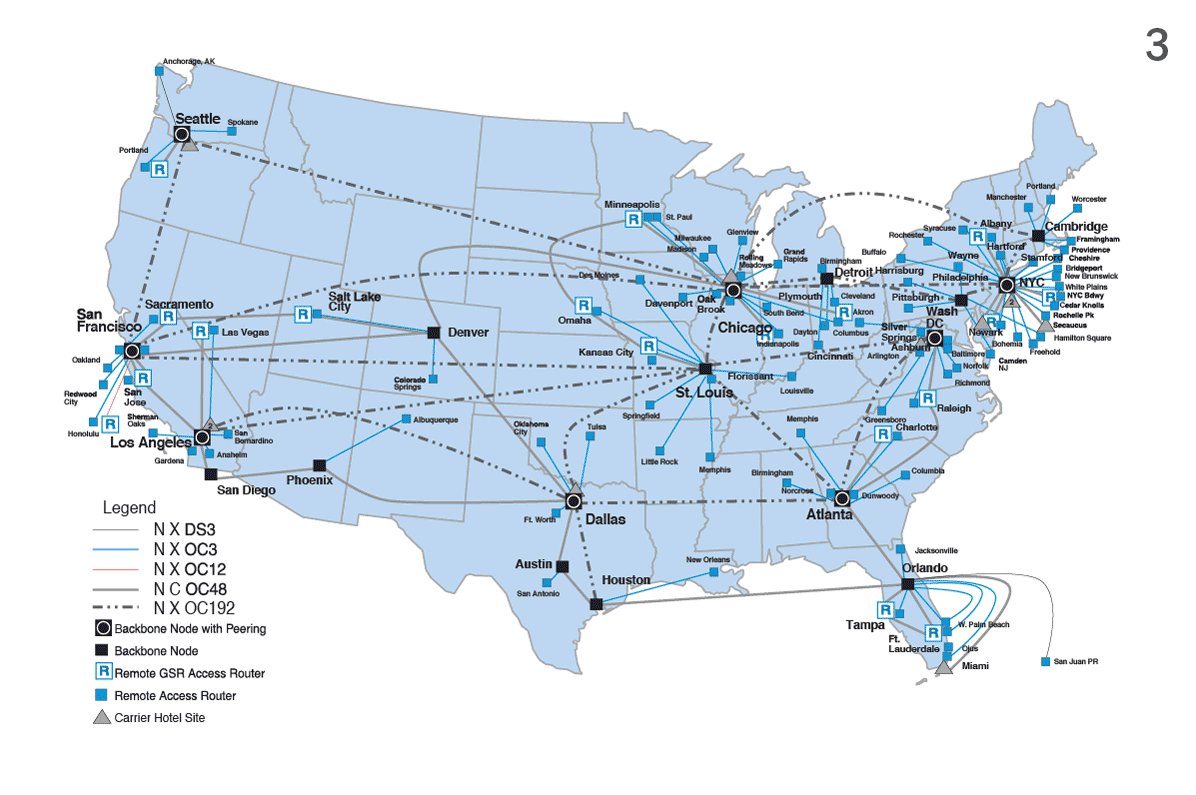
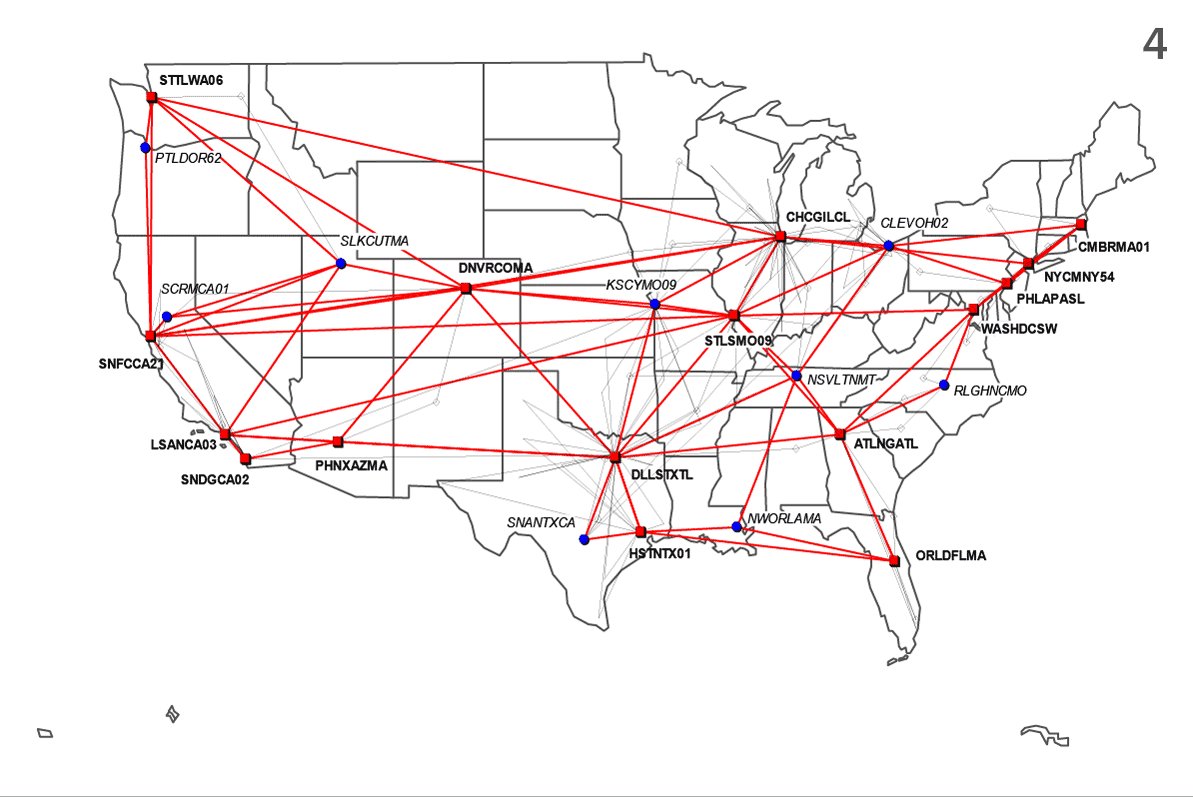
I'm going to post a bunch of tweets answering some of the questions we've had since we published this story yesterday.
We don't believe there are any NSA personnel located at any of the eight facilities. They likely contain secure rooms, off limits to most AT&T employees, where the data "filtering" for NSA takes place.
The San Francisco facility we named was 1st linked w/ NSA in 2006, when AT&T technician Mark Klein said it was fitted w/ a secure room ("641A") containing NSA technology. We believe the SF facility was set up before the other seven we identified & that all are similarly equipped. 



You can read more info from Mark Klein in this court declaration: eff.org/files/filenode… (pdf) There is still an ongoing legal case against the NSA based on the undisputed evidence he provided (Jewel v. NSA): eff.org/cases/jewel
This diagram from an NSA doc shows that at the eight buildings ("Saguaro Access Points"), internet data is filtered using AT&T equipment then sent to a place called "PINECONE." There, the data passes from AT&T to NSA systems & is forwarded to NSA's Maryland HQ ("Corporate NSAW"). 
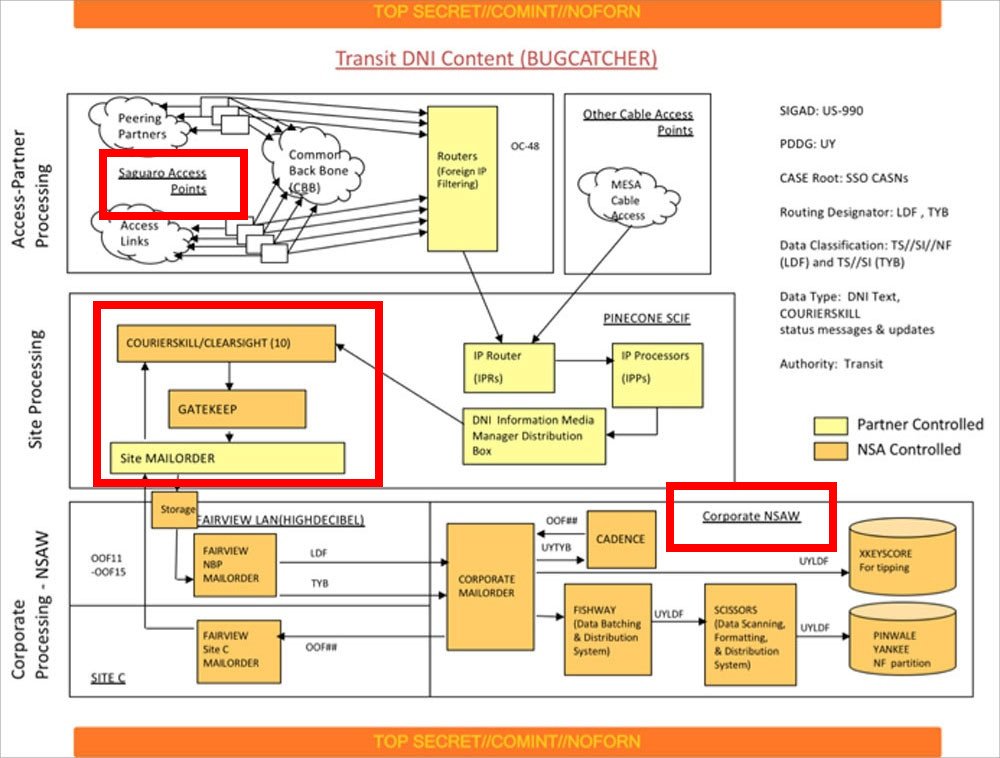
We know PINECONE is in New Jersey, but have not (yet) verified exactly where.
As of 2013, AT&T had installed surveillance equipment inside facilities in at least 59 locations across the US, according to NSA documents. The number could be more or less today, we are not sure.
The eight buildings we identified are among the most important of them all, because they are the only ones that connect to the "common backbone," key data routes that carry vast amounts of internet traffic. 







The eight facilities are not targeting US domestic internet traffic for NSA. They target data from foreign countries that passes across US territory. But it can be hard to distinguish between foreign and US traffic, which means NSA sometimes sweeps up Americans' communications.
Section 702 of the Foreign Intelligence Surveillance Act (FISA) gives NSA the authority to target people who are "reasonably believed" to be foreigners overseas. If those targets are talking with/messaging Americans, NSA is allowed to "incidentally" collect those communications.
Most of NSA's surveillance is carried out with no court oversight under the authority of Executive Order 12333. The agency says it uses this power to eavesdrop on “communications which originate & terminate in foreign countries, but traverse US territory.”
Sometimes under the 12333 authority, Americans' communications are collected, because of the filtering problems I mentioned above. When that happens, the NSA calls it a "domestic incident," the agency's documents say. How frequently this happens we don't know.
EO 12333 deserves more public scrutiny. Much about it remains unclear. In 2014, a State Dept whistleblower said EO 12333 surveillance was violating the US constitution: washingtonpost.com/opinions/meet-…
The eight facilities we identified are involved in surveillance carried out under both EO 12333 and FISA 702. We will publish some new information about EO 12333 in the coming days.
AT&T is not the only company involved in all of this. We believe other companies in the US have similar surveillance equipment inside their networks, because they have been legally compelled to put it there.
AT&T, however, has gone far beyond mere legal compliance; at times, it has closely collaborated w/ NSA to aid surveillance carried out within its buildings. The agency's docs say AT&T has been "aggressively involved" & exhibited an "extreme willingness to help."
We focused on AT&T because we were able to find documents & sources about what was happening in its buildings. It wasn't easy; it took us about a year & a half to do it.
We would welcome any information from insiders with *direct knowledge or evidence* about similar operations at other companies in the US or elsewhere. You can reach us securely by following instructions on this page: theintercept.com/source/
We just published an additional document that shines light on NSA's secretive use of Executive Order 12333, mentioned in the story. It explains "transit authority," a very significant but little-known power NSA uses to collect foreign comms on US soil: theintercept.com/document/2018/…
"Service providers identify & forward foreign communications transiting their networks for subsequent processing & selection. This supports transit content collection as well as transit-authorized bulk metadata." 

“I was involved in very, very top, heavy-duty projects for a few of these three-letter agencies,” said AT&T's former chief technology officer, apparently referencing US intelligence agencies. “They all loved me.” theintercept.com/2018/06/25/att…
• • •
Missing some Tweet in this thread? You can try to
force a refresh








