Laying out Hacking DCCC concludes. Laying out Hacking DNC. Laying out Theft of DCCC & DNC docs begins. Whew!
On/ab April 20, 2016 ➡️ directed X-Agent malware on DCCC comps to connect to “middle server” & receive directions. 
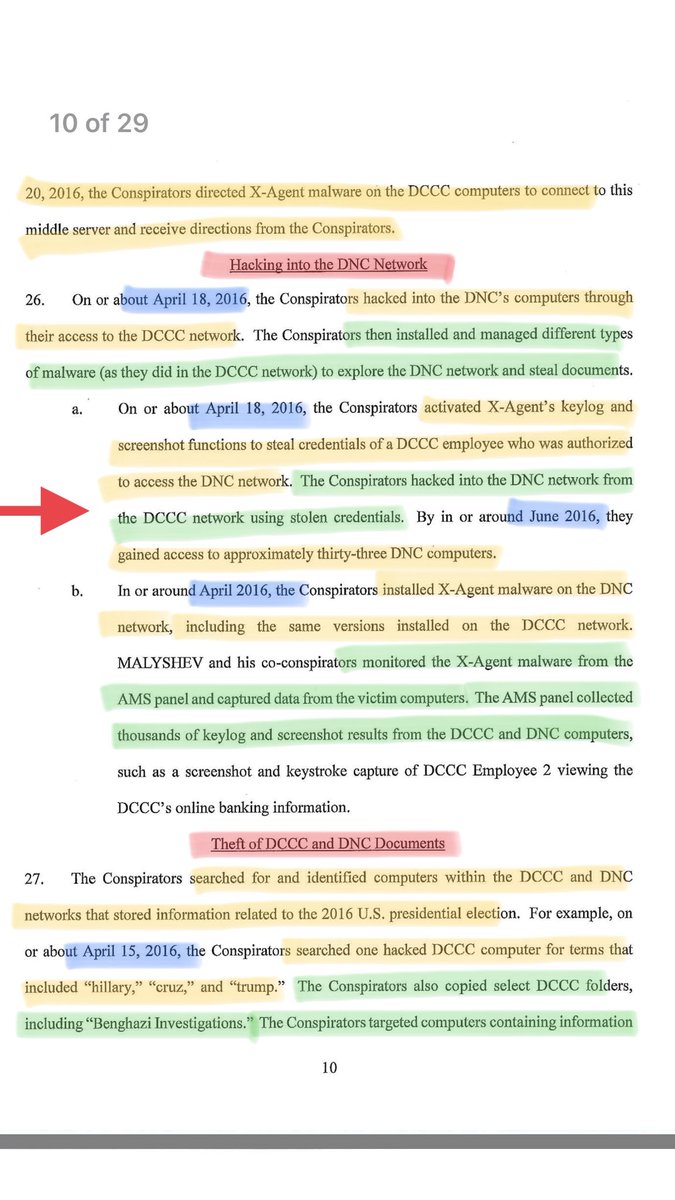
👆Hacking DNC ➡️ on/ab April 18, 2016 ➡️ hacked DNC through their access to the DCCC ➡️ again installed/managed diff types of malware ➡️ to explore DNC network & steal docs.
👆On/ab April 18, 2016 ➡️ activated X-Agent keylog/screenshot to steal DCCC employee credentials who had access to DNC network ➡️ hacked DNC using these stolen creds from X-Agent installation ⏺ By ab June 2016 ➡️ had access to appx 33 DNC computers 👀
👆April 2016 ➡️ installed X-Agent malware on DNC network ➡️ monitored from AMS panel (in AZ) ➡️ captured THOUSANDS of keylogs/screenshots from DCCC & DNC computers.
👆Laying out theft of DCCC & DNC docs begins ➡️ searched for & ID’d computers within DCCC/DNC that stored info related to 2016 election 👀 On/ab April 15, 2016 ➡️ searched hacked DCCC comp for “hillary”, “cruz”, “trump”
👆Also copies select folders ➡️ including “Benghazi investigations” 👀🤔
👆👇Targeted computers containing OPPOSITION RESEARCH & FIELD OP plans ⏺ To steal large amts of data ➡️ publicly avail tool to compress multiple docs ⏺ Then used other GRU malware ➡️ X-Tunnel 📌 ➡️ move stolen docs thru encrypted channels. 

👆 On/ab April 22, 2016 ➡️ compressed GIGABYTES of data via X-Tunnel ➡️ to a GRU-leased server in ILLINOIS📌
👆On/ab April 28, 2016 ➡️ connected/tested GRU-leased server in IL ⏺ Later SAME day ➡️ used X-Tunnel to connect & steal additional docs
👆May 25-June 1, 2016 ➡️ hacked DNC Microsoft Exchange server ➡️ stole THOUSANDS of emails from work accts ⏺ Researched PowerShell commands ➡️ related to accessing/managing Microsoft Exchange Server.
👆On/ab May 30, 2016 ➡️ accessed AMS panel (in AZ) ➡️ to upgrade custom AMS software on server ⏺ SAME DAY ➡️ AMS panel received updates from appx 13 DIFFERENT X-Agent malware implants on DCCC/DNC computers
👆During hack ➡️ covered tracks ➡️ by intentionally deleting logs & computer files 👀⏺ Cleared event logs from DNC computer.
👆👇Theft of DCCC/DNC docs concludes ➡️ June 20, 2016 ➡️ deleted logs from AMS panel that documented their activities on the panel ➡️ including login history 🤔 

👆Laying out Efforts to remain on the DCCC/DNC networks begins ➡️ Despite trying to hide tracks ➡️ May 2016 ➡️ Company 1 hired to ID extent of intruders
👆June 2016 ➡️ Linux-based version of X-Agent ➡️ programmed to communicate with GRU-registered domain ➡️ linuxkrnl .net ➡️ remained on DNC network until October 2016 👀
👆In response to efforts of Company 1 ➡️ countermeasures taken by GRU to maintain control of DCCC/DNC networks ⏺ May 31, 2016 ➡️ Searched for info ab Company 1 And it’s reporting on X-Agent/X-Tunnel
👆June 1, 2016 ➡️ tried to delete traces on DCCC network ➡️ using CCleaner ⏺ June 14, 2016 ➡️ registered domain ➡️ actblues .com ➡️ mimicked site ➡️ 🚨used stolen DCCC creds to modify DCCC website ➡️ redirected visitors to GRU-created mimicked site 🚨👀
June 20, 2016 ➡️ Company 1 disabled X-Agent on DCCC Network ➡️ spent OVER 7 hours trying unsuccessfully to connect to X-Agent ➡️ Alsi tried to access DCCC via previously stolen creds 👀
Brb. Is this beneficial at all? 🤣
👆👇 Same timeframe Hannigan wondered wtf the RU were doing in DNC 👀🚨
https://twitter.com/righteousbabe4/status/1016691437579186176?s=21
Ok. Back to indictment
Wrapping up efforts to remain on DCCC/DNC networks and laying out Reoease of Stolen docs via DCLeaks. 

👆Sept 2016➡️ gained access to DNC computers hosted on 3rd party cloud-computing service ➡️ 🚨contained apps related to DNC analytics🚨➡️recon/create backups of DNC cloud-based systems using the provider’s own technology ➡️moved backups to their accts with same service 👀
👆Stolen docs & DCLeaks ➡️ > a month to create DCLeaks to release/publicize stolen docs ⏺ Apt 19, 2016 ➡️ registered DCLeaks .com ➡️ with $ from online cryptocurrency service ➡️ SAME ONE used to register vpn lease ➡️ operational email dirbinsaabol@ mail .com 👀
👆dirbinsaabol email ➡️ also used to register ➡️ john356gh url-shortening acct for spearfishing attacks ⏺ Jim 8, 2016 ➡️ DCLeaks launch ➡️ shut down in Mar 2017 ➡️ received > 1 MILLION VIEWS ➡️ lied that it was “American hacktivists” when it was GRU
👆Jun 2016 - election ➡️ DCLeaks used to release stolen emails from individuals from HRC campaign ➡️ Also previous spearfishing attacks from 2015 ➡️ GOP 🤔👀
Wrapping up laying out DCLeaks to release stolen data and laying out Stolen docs released through Guccifer 2.0 

👆Jun 8, 2016 ➡️ created DCLeaks FB Page under “Alice Donovan” ➡️ used other social media to promote DCLeaks under “Jason Scott” & “Richard Gingrey” ➡️ all accts accessed by GRU-controlled computers
👆Jun 8, 2016 ➡️ created DCLeaks on Twitter ➡️ again same computers used for other fake “Baltimoreiswhr” ➡️ used to promote anti-HRC flash mobs & # blacksagainsthillary
👆 Stolen docs via Guccifer 2.0 begins ➡️ Jun 14, 2016 ➡️ DNC thru Company 1 public announcement of hack by RU government actors ➡️ response was creation of Guccifer 2.0 ➡️ claimed to be lone Romanian hacker to shift blame away from GRU
👆Jun 15, 2016 ➡️ logged into Moscow-based server ➡️ used/managed by Unit 74455 ➡️ between 4:19 pm-4:56 pm Moscow Standard Time 👀
👆👇Searched for words/phrases: “some hundred sheets”. “Some hundreds of sheets”. “DCLeaks”. “Illuminati”. “<widely known translation>”. “Worldwide known”. “Think twice about”. “Company’s competence” 🤔 

👆Later on Jun 15, 2016 at 7:02 pm (Moscow) ➡️ Guccifer 2.0 published 1st post on WordPress ➡️ “DNC’s servers hacked by alone hacker” ➡️ included numerous words/phrases from those in above tweet.
👆Jun-Oct 2016 ➡️ used Guccifer 2.0 to release stolen DCCC/DNC docs via WordPress ⏺ Guccifer 2.0 alsi shares stolen docs with certain individuals.
👆👇Aug 15, 2016 ➡️ Guccifer 2.0 transmitted stolen docs to US Congressional candidate related to opponent ⏺ Aug 22, 2016 ➡️ Guccifer 2.0 transferred 2.5 GIGABYTES of stolen data to lobbyist/online news source📌 ➡️ 🚨including personal info on > 2,000 donor records 🚨 

👆Aug 22, 2916 ➡️ Guccifer 2.0 sent reporter stolen docs about BLM ➡️ reporter responded by discussing when to release docs & offering to write article🤔
👆Also used Guccifer to communicate with US persons about release of stolen docs ⏺ Aug 15, 2016 ➡️ Guccifer to person in regular contact with senior memberS 👀 of Trump campaign. 🚨 Note: members - PLURAL🚨📌
👆Conducted ops as Guccifer 2.0 & DCLeaks ➡️ with OVERLAPPING computer infrastructure & money 👀
👆Mar 14-Apr 28, 2016 ➡️ Same pool of BITCOIN funds ➡️ purchase vpn acct & lease server in Malaysia ⏺ Jun 2016 ➡️ used Malaysia server to host DCLeaks website ⏺ Jul 6, 2016 ➡️ used vpn to log into “Guccifer_2” twitter acct ➡️ vpn opened from same DCCC/DNC hack server
👆Jun 27, 2016 ➡️ Guccifer 2.0 ➡️ contacted reporter ➡️ offered to provide stolen emails from “Hillary Clinton staff” ➡️ then sent reporter password to access non-public, password-protected portion of DCLeaks site ➡️ contained emails from Victim 1 (from Mar 2016)
👆Jan 12, 2017 ➡️ publishes statement on Guccifer 2.0 WordPress site ➡️ lies that intrusions & release of stolen docs had “totally no relation to the Russian government”
👆Use of Organization 1 begins ➡️ To expand interference in 2016 election ➡️ transferred MANY of the docs stolen from DNC & Podesta to Organization 1 ➡️ discussed release & TIMING of releases to heighten impact 🤔 Note: many vs all & curious why only DNC not DCCC 🤔🤔🤔
👆👇Jun 22, 2016 ➡️ Organization 1 sent private message to Guccifer 2.0 ➡️ to “[s]end any new material [stolen from DNC] here for us to review and it will haveva much higher impact than what you are doing.” 

👆Jul 6, 2016 ➡️ Organization 1 added “if you have anything hillary related we want it in the next tweo [sic] days prefable [sic] because the DNC is approaching and she will solidify bernie supporters behind her after.” ➡️ Response “ok...i see” (1/2)
👆(2/2) Organization 1 responds “we think trump has only a 25% chance of winning against hillary ... so conflict between bernie and hillary is interesting.” 👀
Ok. FULL F*CKING 🛑 When was all of this communication uncovered? And why exactly were the GOP 💩🤡 attacking Strzok yesterday?!? Cuz, um don’t think this info leaked out. JFC.
👆Late Jun-Jul 1, 2016 ➡️ after failed attemptS (plural) to transfer stolen docs ➡️ Guccifer 2.0 sent email to Org 1 with attachment “wk dnc link1.txt.gpg” ➡️ encrypted file with instructions on how to access online archive of stolen docs 👀
👆Jul 18, 2016 ➡️ Org 1 conformed it had “the 1 Gb or so archive” & would release stolen docs “this week” ⏺ Jul 22, 2916 ➡️ Org 1 released > 20,000 emails & other stolen docs from DNC ➡️ appx 3 days before start of Dem Convention🚨➡️Org 1 didn’t disclose Guccifer role
👆latest date for released stolen docs ➡️ May 26, 2016 ➡️ appt same time of Microsoft Exchange server hack 👀
👆👇Wrapping up Use of Org 1: Oct 7, 2016 ➡️ Org 1 released first set of stolen Podesta emails ⏺ Oct 7-Nov 7, 2017 ➡️ Org 1 released appt 33 tranches of stolen Podesta docs ➡️ totaling > 50,000 stolen docs released 

Statutory Allegations begin: Paragraphs 1-49 re-alleged & incorporated by reference. Note: not gonna re-hash. 🤣 

Conclusion Of counts 2-9 (Aggravated Identuty Theft) & Beginning of Count 10 (Conspiracy to Launder Money) 

👆 Defendants conspired to launder equivalent of > $95,000 through a web of transactions structured to capitalize on the perceived anonymity of cryptocurrencies/bitcoin ➡️ Principally used bitcoin to purchase servers, register domains, & to further other hacking activities
👆👇Many of payments processed by companies located in US ➡️ provided payments to hosting cos, domain registrars, & other international/domestic vendors ⏺ Bitcoin allowed avoiding direct relationships with traditional institutions ➡️ evaded scrutiny of IDs & source of $ 

👆To further avoid creating centralized paper trailof all purchases ➡️ purchased infrastructure using HUNDREDS of different email accts ➡️ sometimes a new acct of each purchase ⏺ used fake names to obscure IDs & links to RU & RU government
👆used several dedicated email accts to track basic bitcoin transaction info & to facilitate bitcoin payments to vendors ➡️ 1 of these accts registered with username “gfade147” ➡️ received HUNDREDS of bitcoin payment requests from appx 100 different email accts
👆👇occasionally facilitated bitcoin payments using same computers used for hacking activities - like to create/test spearfishing emails ➡️ one dedicated acct used in 2015 to renew domain reg for “linuxkrnl.net” ➡️ encoded in X-Agebt malware used in DNC network 

👆Funded part their purchase of computer infrastructure by “mining” bitcoin ➡️ pool of bitcoin generated from GRU mining ➡️ paid Romanian co to register DCLeaks domain ➡️ thru payment processing co in US 👀
👆also acquired bitcoin by variety of means to obscure origin of $ ➡️ peer-to-peer exchanges. Moving $ thru other digital currencies. Using pre-paid cards ⏺ also enlisted assistance of >= 3rd party exchangers ➡️ facilitated layered transactions 👀
👆Used same funding structure ➡️ even same pool of $ ➡️ to purchase key accts, servers, & domains for hacking activity ⏺ bitcoin mining ➡️ DCLeaks ➡️ “Daniel Farell” ➡️ linuxkrnl.net & servers/domains used in GRU spearfishing ops 👀
👆Mar 14, 2016 ➡️ using $ in bitcoin address ➡️ purchased vpn acct ➡️ used to log into “ Guccifer_2” twitter acct ⏺ Apr 28, 2016 ➡️ Remaining $ from that bitcoin address ➡️ lease Malaysian server ➡️ hosted DCLeaks site.
👆Used different set of fake names (“Ward DeClaur” & “Mike Long”) ➡️ send $ to US co ➡️ lease server to administer X-Tunnel malware implanted on DCCC/DNC networks ⏺ also used to lease 2 servers to hack DNC cloud network
👆Statutory Allegations ➡️ “together with others, known and unknown to the Grabd Jury, did knowingly and intentionally conspire to transport, transmit, and transfer money instruments...with the intent to promote the carrying on of specified unlawful activity, ...”
Count 11 (Conspiracy to Commit an Offense Against the United States) ⏺ Defendant summaries ⏺ Object of the Conspiracy ⏺ Manner & Means of the Conspiracy ➡️ Jun 2016 ➡️ researched domains used by US state bds of elections, Secs of State, etc for vulnerabilities (1/2) 

👆(2/2) Also searched for state political party email addresses, including filtered queries for email addresses listed on state Republican Party websites 📌
Count 11 (Conspiracy to Commit an Offense Against the US) ➡️ Manner & Means of the Conspiracy continues 

👆Jul 2016 ➡️ hacked website of a state board of elections (SBOE) ➡️ stole info related to appx 500, I promise voters ➡️ names. Addresses. Partial social security numbers. DOBs. Driver’s License Numbers.
👆Aug 2016 ➡️ hacked into computers of US Vendor 1 ➡️ supplied software used to verify voter registration info for 2016 elections ➡️ used some of same infrastructure to hack Vendor 1 that was used to hack SBOE 1 👀
👆Aug 2016 ➡️ FBI issued alert about SBOE 1 hack & ID’d some of the infrastructure used to conduct hacking📌 ⏺ Response ➡️ deleted search history ➡️ deleted records from accts used in their ops targeting SBOEs & similar election-related entitles
👆Oct 2016 ➡️ further targeted state & county offices responsible for administering 2016 elections ⏺ Oct 28, 2016 ➡️ visited websites of certain counties in GA, IA, FL to ID vulnerabilities 🚨Note: that’s just ab example 👀
👆Nov 2016 ➡️ used email acct designed to look like a Vendor 1 email address ➡️ used to send > 100 spearfishing emails to orgs/personnel involved in administering elections in NUMEROUS counties in FL ➡️ contained malware embedded into Word docs bearing Vendor 1 logo📌
👆👇Forfeiture Allegation & Substitute Assets➡️”Notice is further given that, upon conviction, the United States intends to seek a judgment against each Defendant for a sum of money representing the property described in this paragraph, as applicable to each Defendant...”❤️ 



Taking a break. 🤣🤣 Will come back to the remaining 📌 in a bit. ❤️👊
@threadreaderapp unroll please ❤️
• • •
Missing some Tweet in this thread? You can try to
force a refresh