Steam Accounts Being Stolen Through Elaborate Free Game Scam - by @LawrenceAbrams
bleepingcomputer.com/news/security/…
bleepingcomputer.com/news/security/…
A Steam scam is underway that begins with a user receiving a Steam message from a friend telling them about a site that they can use to get a free game. 

Little does the recipient know that the person's account that is sending the message has been hacked and sucked into a elaborate scam campaign targeting Steam users.
When a user clicks the link they will be redirected through a gateway that then takes them to another working "free game" site. This site says a user can click the "Roll" link to get a random free game. 
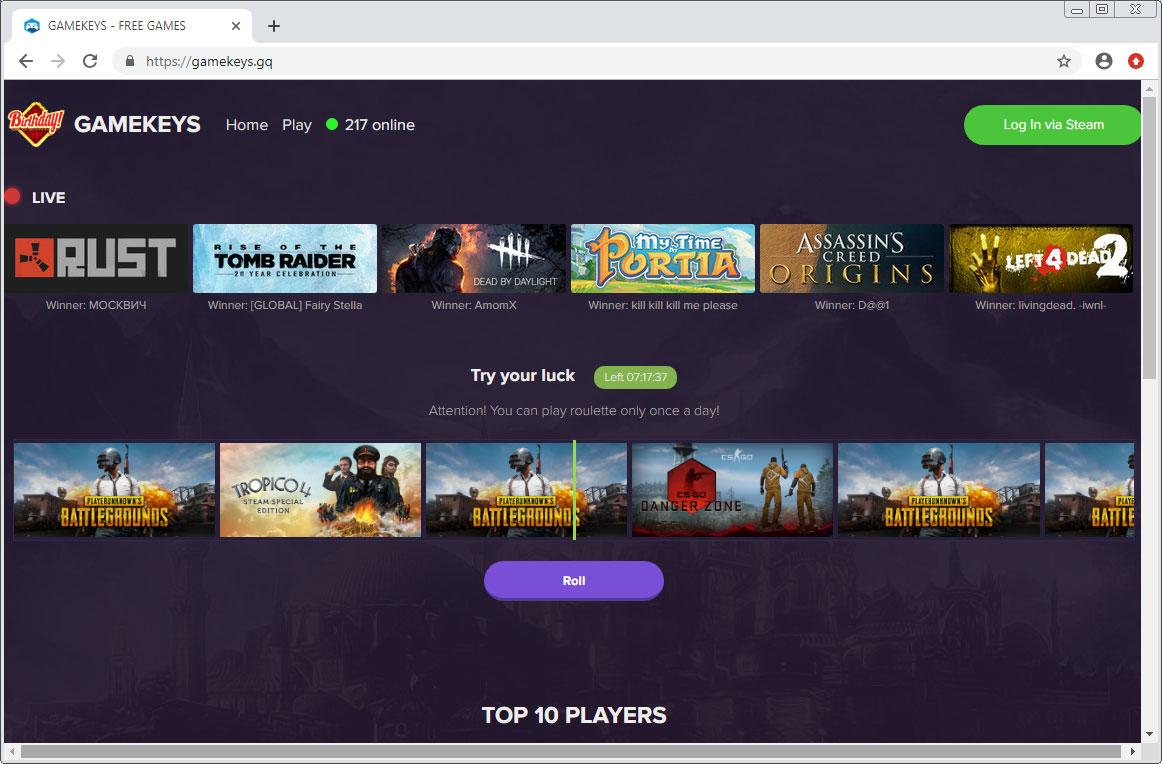
Clicking the login button will generate a fake Steam SSO login page. While it looks identical to Steam's normal SSO login pages, this is a fake page hosted on the game site. 

If you enter your credentials, the server will try to log you in behind the scenes. If 2FA is enabled or Steam Guard pops up, which it will as Steam will see it as a login from a new computer, the site will prompt you to enter the code you receive. 

This looks like a normal SSO sign in process, but cone the Steam Guard code is entered, the server will once again, behind-the-scenes, login to the account, change the email address, password, and phone number.
They have now stolen the victim's account.
They have now stolen the victim's account.
Now that the account has been stolen, it has been added as another bot in this scam's campaign and will be used to further spread the site through Steam messages.
Rinse and repeat.
Rinse and repeat.
• • •
Missing some Tweet in this thread? You can try to
force a refresh









