How to DELETE 99.9% of your digital footprint from the internet [a thread]
Step 1: Preliminary Requirements
Go through each email you can think of that you've used in the past 10 years.
You'll want to recover them if you've lost access, so that you can access other websites you may have signed up to using them.
Go through each email you can think of that you've used in the past 10 years.
You'll want to recover them if you've lost access, so that you can access other websites you may have signed up to using them.
Step 2: Deleting old accounts from forgotten services
Use the search function on your e-mail and look for phrases such as "Sign up" or "Welcome"
Recover account and login into each service that pops up (that you received a sign-up email) from
Use the search function on your e-mail and look for phrases such as "Sign up" or "Welcome"
Recover account and login into each service that pops up (that you received a sign-up email) from
Step 2b:
Now look around the service for a delete account function, google around by searching ``"delete account" + "<service>"
If there isn't one, google or look around for a support e-mail to request for them to delete your account.
Now look around the service for a delete account function, google around by searching ``"delete account" + "<service>"
If there isn't one, google or look around for a support e-mail to request for them to delete your account.
Step 2c:
For some services, you may want to purge all content and messages before you delete the account, as the account may be archived and a hacker or external entity may access this information at a later date.
That's something to bare in mind.
For some services, you may want to purge all content and messages before you delete the account, as the account may be archived and a hacker or external entity may access this information at a later date.
That's something to bare in mind.
Step 3: Checking if your information has been compromised already.
Now you should have a list of all your usernames and all the services, ranging from streaming services to e-mails.
You need to use something called boolean searches to properly use Google to locate this info
Now you should have a list of all your usernames and all the services, ranging from streaming services to e-mails.
You need to use something called boolean searches to properly use Google to locate this info
Step 3b: I'll be using ``s to denote normal quotations, as you will need to use the normal "" signs to perform these searches.
You need to google your account name
"<account_name>"
Sometimes maybe your account name + password like so:
"<account>" + "<password>"
You need to google your account name
"<account_name>"
Sometimes maybe your account name + password like so:
"<account>" + "<password>"
Step 3c: You should see possibly pastebin links or underground databases publicly accessible on the internet, or possibly leaked private information.
This is normal. It happens to a lot of services.
Note down what passwords/information was comprimised.
This is normal. It happens to a lot of services.
Note down what passwords/information was comprimised.
Step 3d: Some database leaks are a bit more private and are still being shared/sold in private circles, but you can use this website:
To check if you've been compromised, so you can change your live information to be different..haveibeenpwned.com
To check if you've been compromised, so you can change your live information to be different..haveibeenpwned.com
Step 4: Removing yourself from Google.
So now you've deleted your Facebook accounts, but when you google your name and location using boolean searches, there is cached information/links about yourself.
There is a solution for that, called the Google Console.
So now you've deleted your Facebook accounts, but when you google your name and location using boolean searches, there is cached information/links about yourself.
There is a solution for that, called the Google Console.
Step 4b: You can use Google Console at:
You can request for them to delete/update their search engine (which usually takes months organically) to remove those cached results if you provide a link to each.
Go through various google searches and do thisgoogle.com/webmasters/too…
You can request for them to delete/update their search engine (which usually takes months organically) to remove those cached results if you provide a link to each.
Go through various google searches and do thisgoogle.com/webmasters/too…
Step 5: Protecting yourself against Google legally tracking you (for the most part).
You should be disallowing Google to legally touch any of your data
Here you can go through each of Google's services: myaccount.google.com/activitycontro…
You should be disallowing Google to legally touch any of your data
Here you can go through each of Google's services: myaccount.google.com/activitycontro…
Step 5b: Protecting yourself against other services
Any other services you wish to use, you need to strip down the privacy settings to the absolute core.
If you want to use Facebook, make sure you make it almost entirely private, so people can't access private photos.
Any other services you wish to use, you need to strip down the privacy settings to the absolute core.
If you want to use Facebook, make sure you make it almost entirely private, so people can't access private photos.
Step 6: Deleting old e-mails
Now you've just access to your old e-mails, it's time to delete them too.
Delete any e-mails you no longer need access to
DO NOT DELETE E-MAILS YOU MAY NEED IN THE FUTURE.
If you do need them, change security questions and password.
Now you've just access to your old e-mails, it's time to delete them too.
Delete any e-mails you no longer need access to
DO NOT DELETE E-MAILS YOU MAY NEED IN THE FUTURE.
If you do need them, change security questions and password.
Step 7: Securing accounts
You should be REGULARLY changing your passwords on services every 6 months
Why?
Because new hackers gain access to new databases daily, and they'll start using that information to bruce force, or in the future, to personally attack you.
You should be REGULARLY changing your passwords on services every 6 months
Why?
Because new hackers gain access to new databases daily, and they'll start using that information to bruce force, or in the future, to personally attack you.
Step 7b: Do NOT use any passwords similar to each other.
Hackers are smart. Especially when it's a personal attack.
They will easily combine your old passwords with your home address, or date of birth to accomplish finding your password to something they need.
Hackers are smart. Especially when it's a personal attack.
They will easily combine your old passwords with your home address, or date of birth to accomplish finding your password to something they need.
Once they are in, some services will give them access to EVERYTHING and it's damn near impossible to get them out after they are in.
Good news is a lot of services are updating this, so that you can only have one session active at once.
Before you never knew who was in.
Good news is a lot of services are updating this, so that you can only have one session active at once.
Before you never knew who was in.
Step 8: PROTECTING your internet connection.
You should be using a VPN when using the internet.
DO NOT use a VPN when dealing with banking services or anything confidential, but do use it when publicly surfing the internet.
Using DuckDuckGo in combination with this will help
You should be using a VPN when using the internet.
DO NOT use a VPN when dealing with banking services or anything confidential, but do use it when publicly surfing the internet.
Using DuckDuckGo in combination with this will help
Step 8b: Using a VPN that has no logs.
You need to make sure your VPN has had a PUBLIC audit to ensure that it has NO LOGS.
this means that it has no record of what you have used their internet connection for.
And when you use a VPN, it's hard for your ISP to know either.
You need to make sure your VPN has had a PUBLIC audit to ensure that it has NO LOGS.
this means that it has no record of what you have used their internet connection for.
And when you use a VPN, it's hard for your ISP to know either.
Step 9: USING Burner accounts
You should be using burner accounts on known intrusive services such as Google by using a fake name and information.
This is LEGAL and you should do it to avoid having your information data mined across services.
You should be using burner accounts on known intrusive services such as Google by using a fake name and information.
This is LEGAL and you should do it to avoid having your information data mined across services.
Step 10: REGULARLY deleting your internet content.
You should be regularly deleting your tweets and old photos.
This data can be used against you to cross-reference your accounts and find more personal information.
Hackers will find a target and analyze them for months.
You should be regularly deleting your tweets and old photos.
This data can be used against you to cross-reference your accounts and find more personal information.
Hackers will find a target and analyze them for months.
Step 10b:
Hackers will use your old internet information to do some of this analyzing in retrospect to piece together who your social circle is to find a vulnerability.
Anyone can be attacked. You just haven't been a target yet.
Defend yourself through prevention.
Hackers will use your old internet information to do some of this analyzing in retrospect to piece together who your social circle is to find a vulnerability.
Anyone can be attacked. You just haven't been a target yet.
Defend yourself through prevention.
Step 10c:
Don't believe me?
This is nothing. Very simple with the tools EVERYONE has access to today.theverge.com/2019/10/11/209…
Don't believe me?
This is nothing. Very simple with the tools EVERYONE has access to today.theverge.com/2019/10/11/209…
That's it for now.
I'll have a few more steps for you guys who want to be EXTRA secure.
I'll have a few more steps for you guys who want to be EXTRA secure.
This thread was brought to you by someone who hacking accounts and systems at the age of 11.
There is much more talented and scarier threats out there now,
Not to mention most of your money is now online.
Protect yourself at all costs, it's only a few hours.
There is much more talented and scarier threats out there now,
Not to mention most of your money is now online.
Protect yourself at all costs, it's only a few hours.
I'm gonna drop some Reverse Engineering game if you ever wanted to get your feet wet in reversing mobile applications or games.
*next week*
Actually...
I'll do a part two in regards to your opsec in the future.
How you can protect yourself from fraud and prevent being RAT'd.
As well as what to do in a panic situation where you are compromised.
I'll do a part two in regards to your opsec in the future.
How you can protect yourself from fraud and prevent being RAT'd.
As well as what to do in a panic situation where you are compromised.
I'm going to repeat myself here:
DO NOT enter your password in Google search UNLESS you know it's a publicly compromised password already.
This will give you an idea of how many PUBLIC, CLEAR internet resources that are indexed that have it stored.
DO NOT enter your password in Google search UNLESS you know it's a publicly compromised password already.
This will give you an idea of how many PUBLIC, CLEAR internet resources that are indexed that have it stored.
The idea was for you to see how many times that password has been breached that a very low level hacker could get his hands on after a few Google's.
That's it.
That's it.
This explanation would require a whole thread itself, but it's reasonable for anyone in this day and age to need to know this.
https://x.com/al3ashiq64/status/1184257110596620289
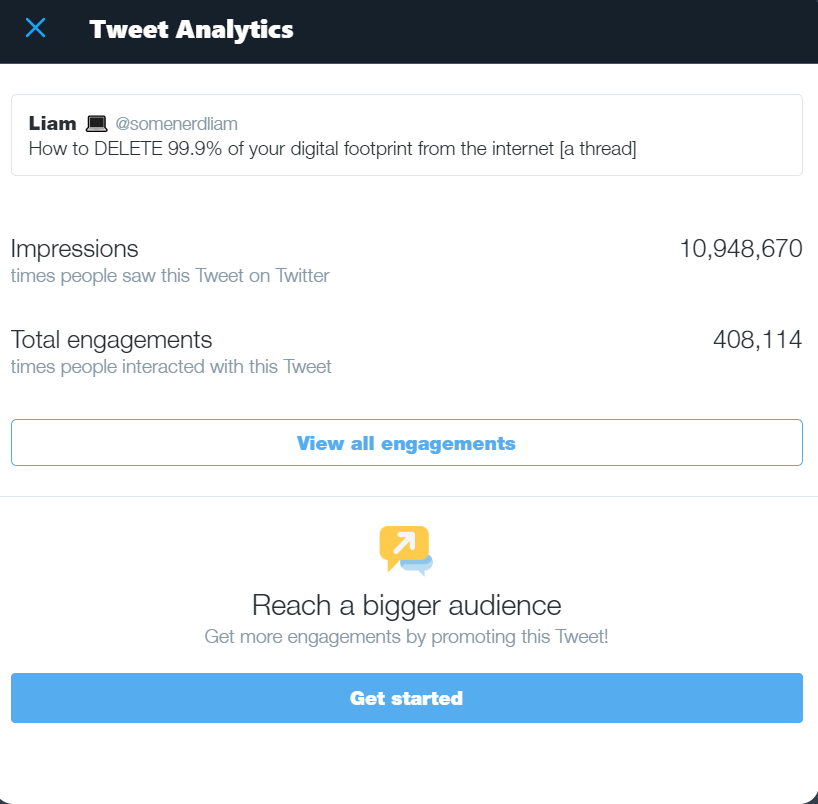
Wild. We reached 10m people collectively.
I got a lot more to give out in terms of tech,
Make sure to follow me up if that's your thing.
I got a lot more to give out in terms of tech,
Make sure to follow me up if that's your thing.
• • •
Missing some Tweet in this thread? You can try to
force a refresh




