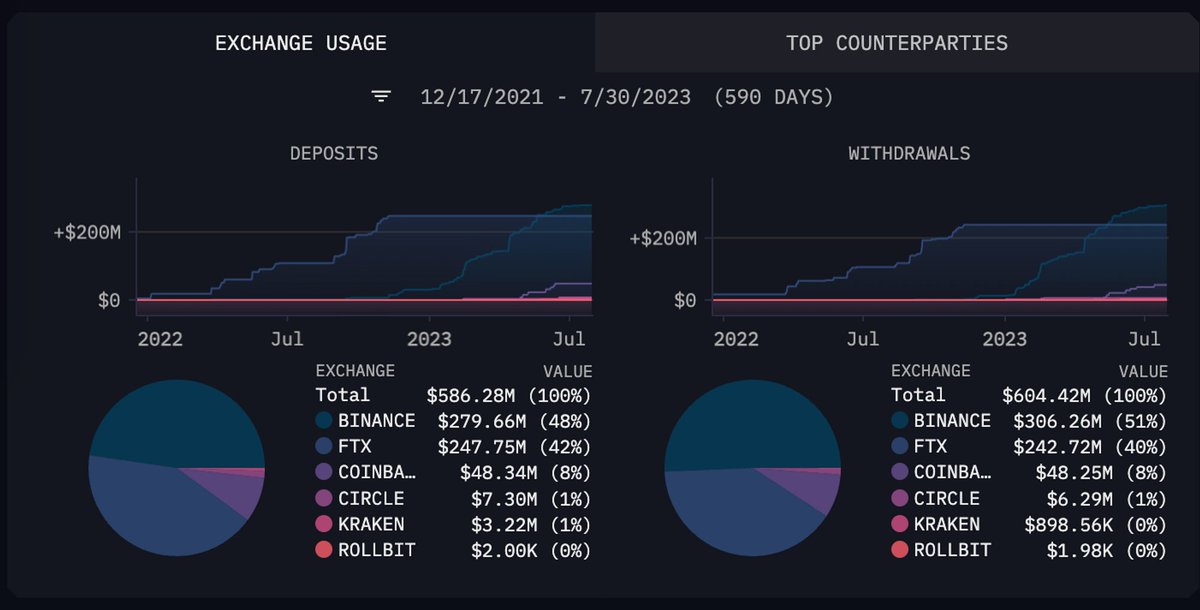
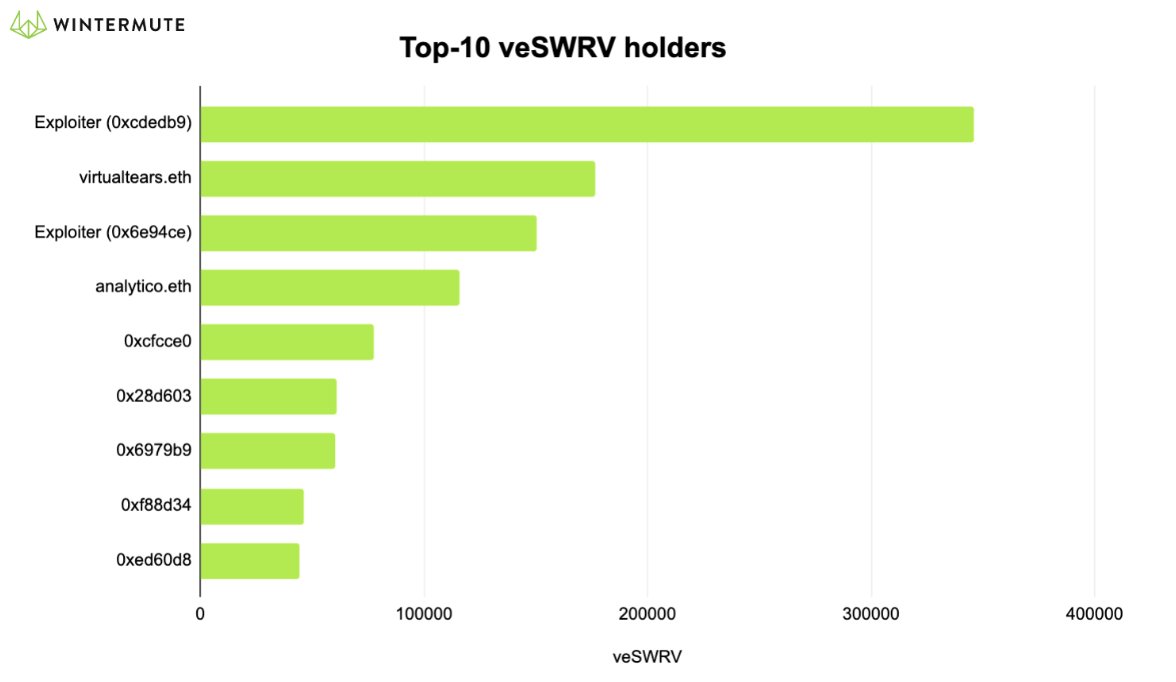
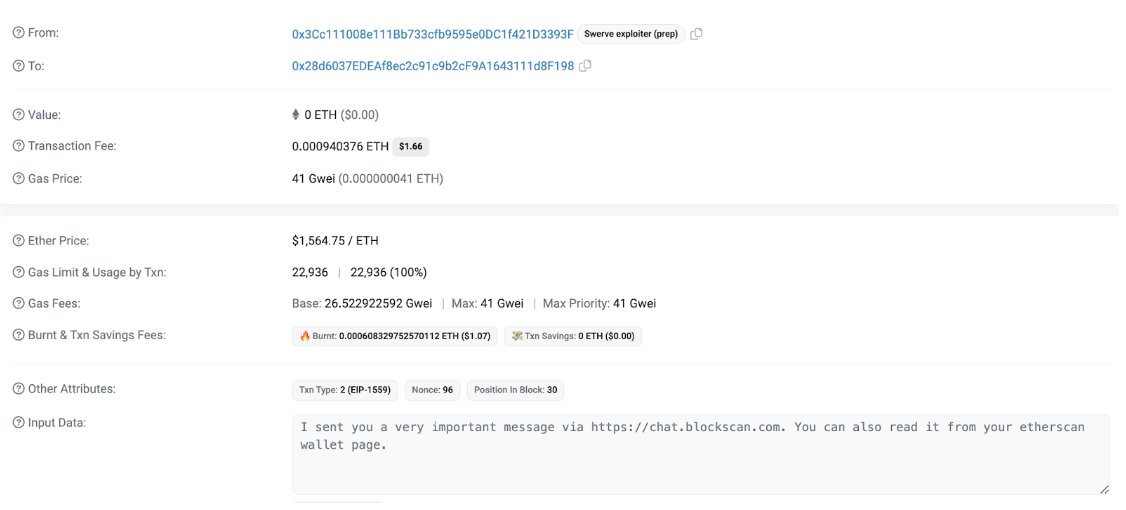
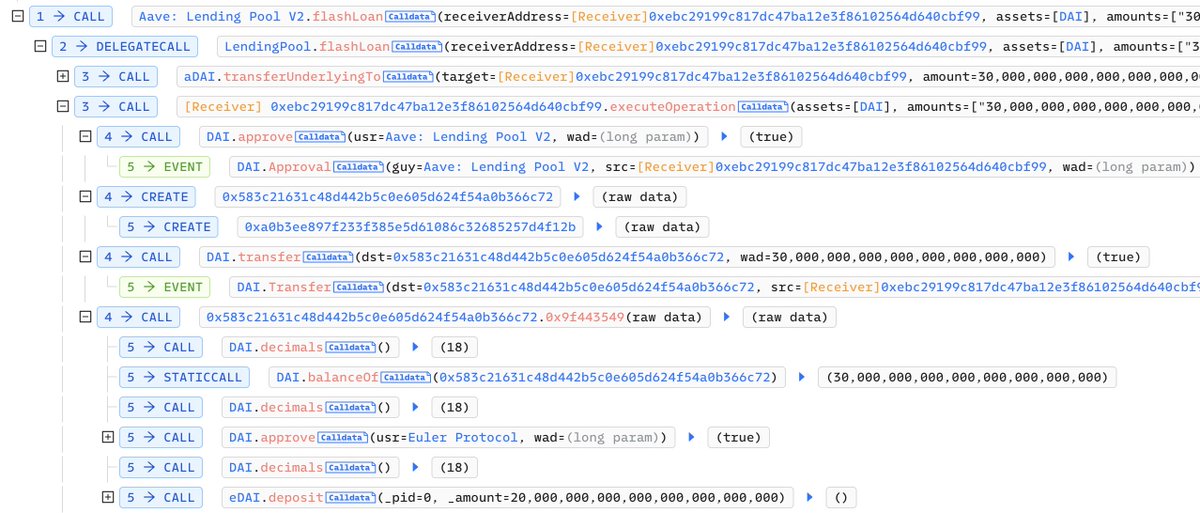
Hm, interestingly, #mempool is crammed with heavy transactions. Need details? Easy
All txs generated from one address: 1FoWyxwPXuj4C6abqwhjDWdz6D4PZgYRjA
blockchair.com/bitcoin/mempoo…)
blockchair.com/bitcoin/mempoo…)
• • •
Missing some Tweet in this thread? You can try to
force a refresh