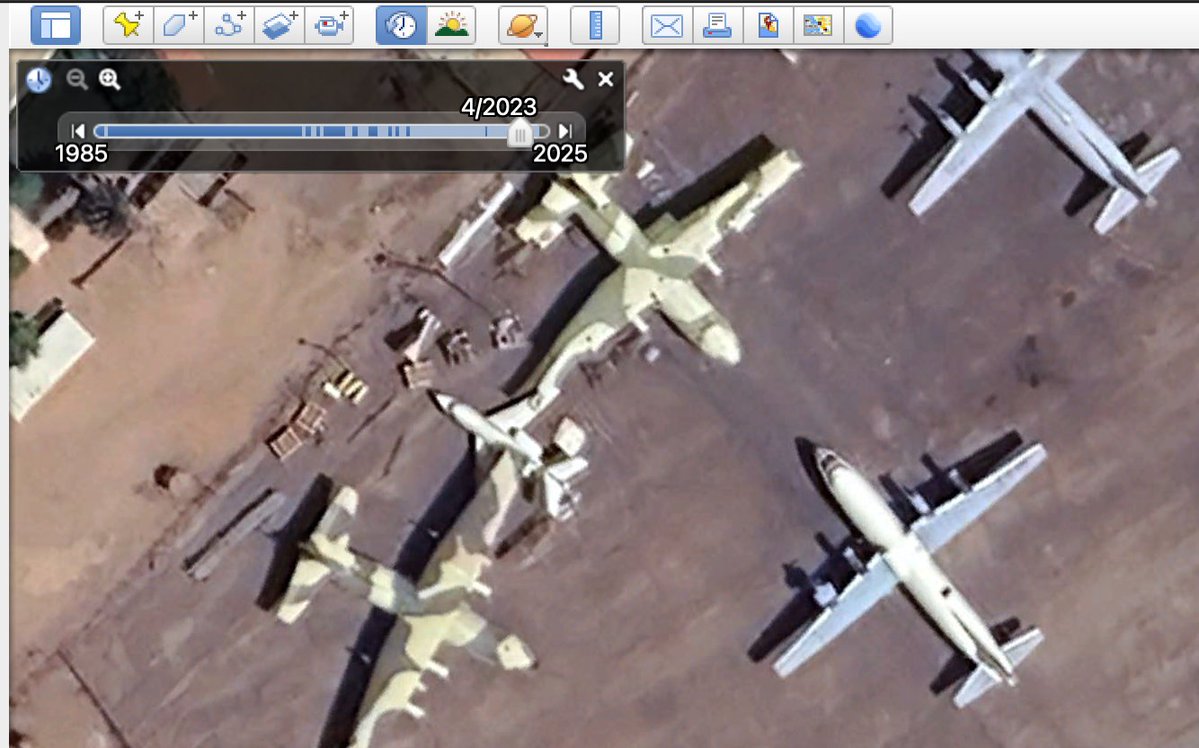
Italian arms have been sold to Russia, transported to Syria, & used by sanctioned Syrian Army militia breaching European trade & arms safeguards.
After 12 months of digging w/ @leone_hadavi, @Bashar24836440, we show how they got to places like this 👇👇
bellingcat.com/news/2019/12/2…
After 12 months of digging w/ @leone_hadavi, @Bashar24836440, we show how they got to places like this 👇👇
bellingcat.com/news/2019/12/2…
First, what about the rules on arms control in Europe? Italy must observe the Common Position (eur-lex.europa.eu/legal-content/…) & consider human rights when granting an export license. Plus there’s an arms embargo on dealing with Russia (europa.eu/newsroom/highl…) 





We cross-referenced Italian Govt records on export licences to reveal items granted for sale, transaction value & end-user country. For example we can see this 2011 lic. for sale of 10 Iveco M65E19WMs paid for & exported to Russia. Big H/T to @FrancescaCost2 for her skills here. 





Why have those safeguards? Well it's to stop things like this happening - people like Al-Hassan (سهيل الحسن), commander of Syrian Army's Tiger Forces, using EU arms. He’s also subject to EU-restrictive measures for "violent oppression against the population in Syria" 



Through #geolocation, we can tell that the above footage (from here ) of Al-Hassan & the Iveco was filmed during the attack on Aleppo Power Station (محطة حلب الحرارية). The power station is located here: goo.gl/maps/5PqEPsqRr…. 

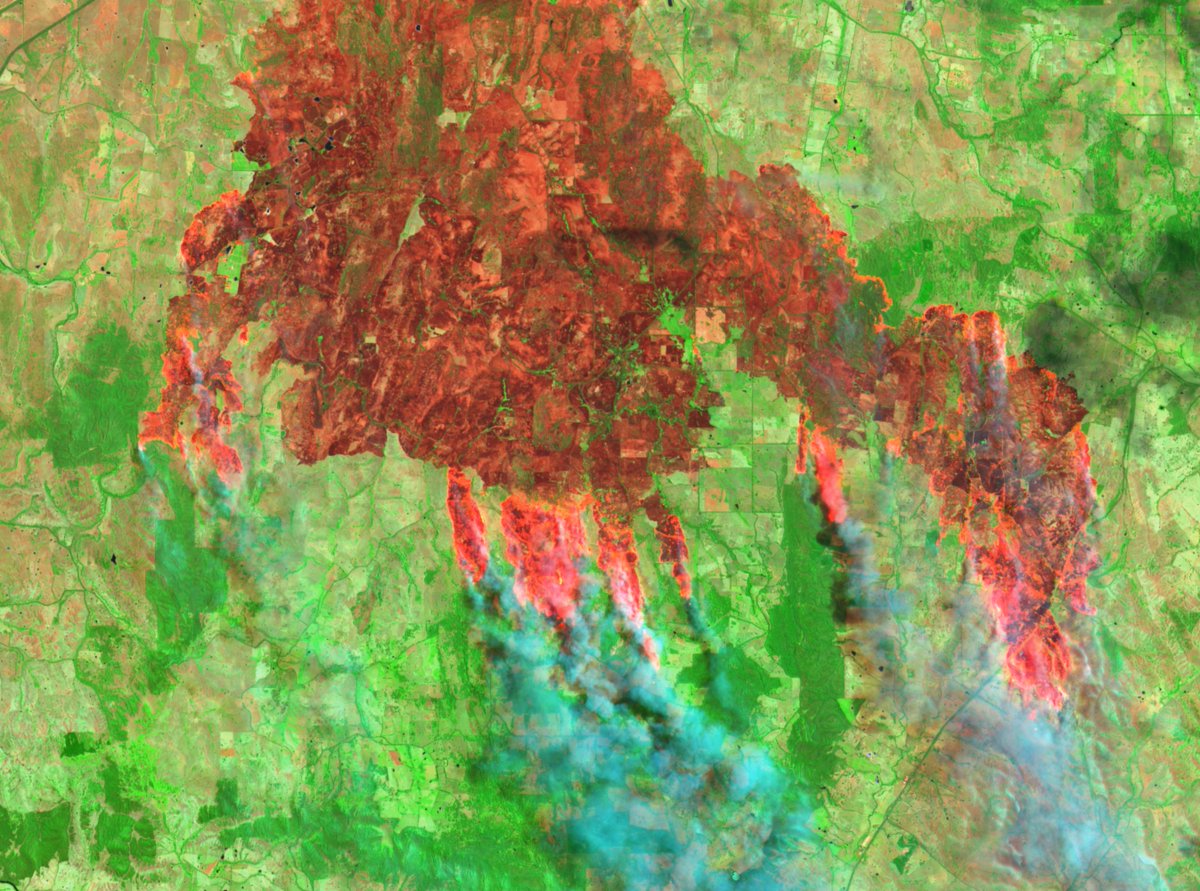
Through #chronolocation, we can tell when this video was filmed. Notice smoke coming from power station? It coincides with Sentinel-2 imagery from Feb 16, 2016 on @sentinel_hub (apps.sentinel-hub.com/sentinel-playg…). Sentinel imagery layered in @googleearth with @Pierre_Markuse fire script. 

Images from after the attack on the Aleppo Thermal Power Plant also locate an Iveco LMV at the power plant. Image below was taken here: goo.gl/maps/eXMwTAccn…, as Syrian Army forces moved in. Original imagery of attack posted by @LinaArabii ✌️ 

We’ve also geolocated the Iveco LMV used by Desert Hawks in Al-Rassafah (below) & by Desert Hawks/Hezbollah in Palmyra Offensive at Western Bayarat. You can read up on the full documentation of the geolocation and chronolocation in our @bellingcat post. bellingcat.com/news/2019/12/2… 



So we’ve located the LMV in Syria & we’ve found some of the people that use it. But how did it get to Syria? It was transported by air, and by sea. For instance: below we can see Iveco LMVs en route to Syria by sea (H/T to the legendary @YorukIsik ✌️) 👇
https://twitter.com/YorukIsik/status/985539834461683712?s=20
In this footage () we can see the Ivecos loading on a plane at Chkalovsiy Airport in Schyolkovo (Щёлково) and landing in Syria’s Hmeimim Air Base (قاعدة حميميم الجوية), here: goo.gl/maps/HXptj2QFn…. 







The continued sale of the Iveco LMV to Russia indicates a breach of safeguards. But Iveco is just one of many arms manufacturers identified in the @bellingcat & @LightouseReports #EUArms project that has breached these safeguards: bellingcat.com/news/uk-and-eu…
Through this methodology of arms tracing, over countless projects in Europe we have geo/chronolocated & dug paper trail of arms transfers that fall outside commitments of these rules. Through this work, we’ve been able to contribute to claims like this
https://twitter.com/lindebryk/status/1205203957607534594
A big part (& underplayed) is the work of investigators such as @leone_hadavi, @Bashar24836440 & @FrancescaCost2 who worked on this project from their laptops at home. These great investigators are up for hire - this work is a testament to their skills. H/T to you all ✊
• • •
Missing some Tweet in this thread? You can try to
force a refresh