How to defeat Hashcat !? 🛡️ Well, I think I found a workaround😈
Use a password with the following format :
⚔️ '$HEX[xxxx]' ⚔️ (where xxxx are only hex characters)
Unless a specific flag is added to hashcat, the attacker will never be able to crack it ! #hashcat
1/5⬇️⬇️⬇️
Use a password with the following format :
⚔️ '$HEX[xxxx]' ⚔️ (where xxxx are only hex characters)
Unless a specific flag is added to hashcat, the attacker will never be able to crack it ! #hashcat
1/5⬇️⬇️⬇️

As you can see on the screenshot, the🚩'--wordlist-autohex-disable' needs to be added to hashcat to crack this pwd👻
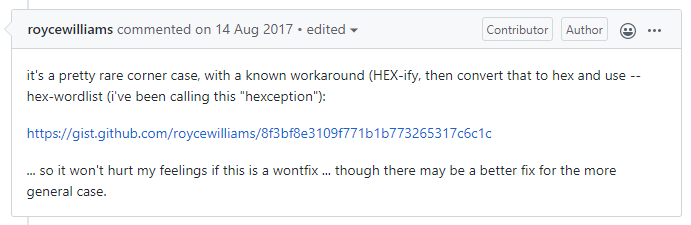
This issue is already known by the hashcat team as you can see on Github and called an "hexception" 😆
github.com/hashcat/hashca…
2/5⬇️⬇️⬇️
This issue is already known by the hashcat team as you can see on Github and called an "hexception" 😆
github.com/hashcat/hashca…
2/5⬇️⬇️⬇️
But why Hashcat failed to crack the password w/s🚩?
When a pwd contains a mixture of bytes outside 0x20-0x80, HC converts it as hex using this format $HEX[xxxx].
Using this, Hashcat can makes a diff between a plaintext pwd using only hex chars and the encoded one 🦾
3/5⬇️⬇️
When a pwd contains a mixture of bytes outside 0x20-0x80, HC converts it as hex using this format $HEX[xxxx].
Using this, Hashcat can makes a diff between a plaintext pwd using only hex chars and the encoded one 🦾
3/5⬇️⬇️
But wait, when Hashcat try to read your l33t password "$HEX[DEADBEEF]", he thinks it's an encoded one and not a plaintext password following his own logic !
And this is why without the flag ''--wordlist-autohex-disable" he cannot crack it ! 😈
4/5⬇️⬇️
And this is why without the flag ''--wordlist-autohex-disable" he cannot crack it ! 😈
4/5⬇️⬇️
Now let's check how you can configure KeePass⛏️ to automate this process :
1⃣ Go to Tools -> Generate Password
2⃣ Select "Generate using Pattern"
3⃣ Add this pattern '$\HEX\[h{30}\]'
4⃣ Don't forget to save the profile
5⃣ Go to Preview tab to check
That all I have for today !✌️

1⃣ Go to Tools -> Generate Password
2⃣ Select "Generate using Pattern"
3⃣ Add this pattern '$\HEX\[h{30}\]'
4⃣ Don't forget to save the profile
5⃣ Go to Preview tab to check
That all I have for today !✌️


• • •
Missing some Tweet in this thread? You can try to
force a refresh





