ERC20 is safer than ERC777 in the same way that Bitcoin is safer than Ethereum. It's safe because it's limited.
Here's some thoughts:
eips.ethereum.org/EIPS/eip-777
However, it's very "underpowered" for a system that's trying to create "programmable money". Many of Ethereum's UX problems come from limitations of the ERC-20 standard.
You could even use many dapps by just sending tokens, instead of needing Metamask.
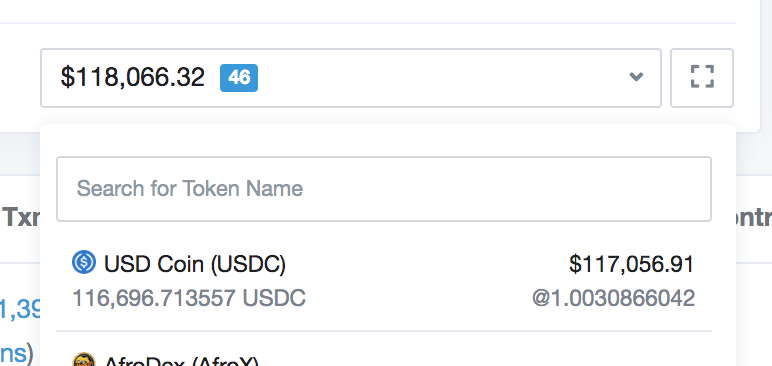
Imagine sending Dai to compound.eth and getting cDai. Then withdraw it by sending cDai back to compound.eth.
Uniswap V2 has already patched this issue:
It does open up a vulnerability, but it's a vulnerability that Ethereum developers have been handling for years.
Don't write off a good piece of technology just because one contract got hacked.