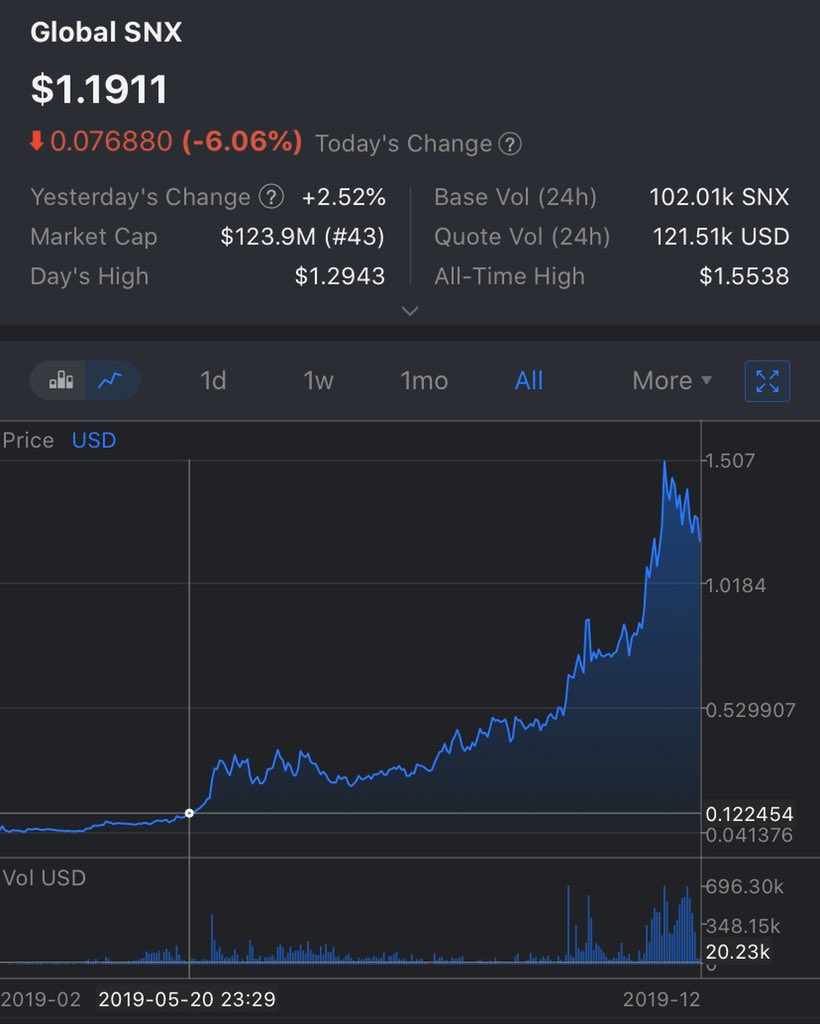
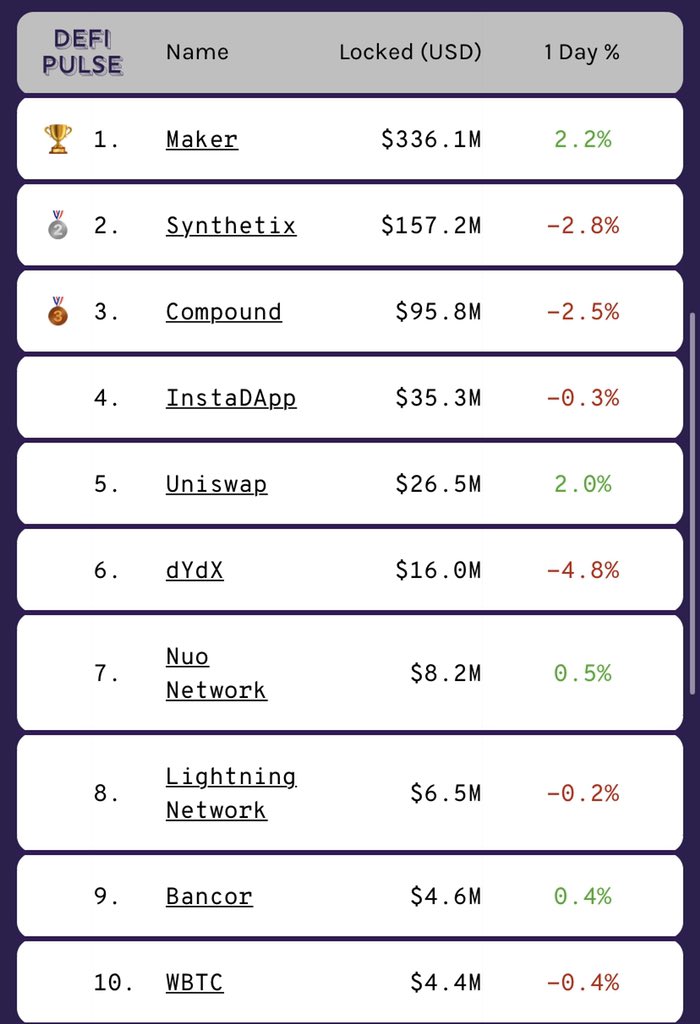
A simple explainer of what happened, as I understand it:
1/x
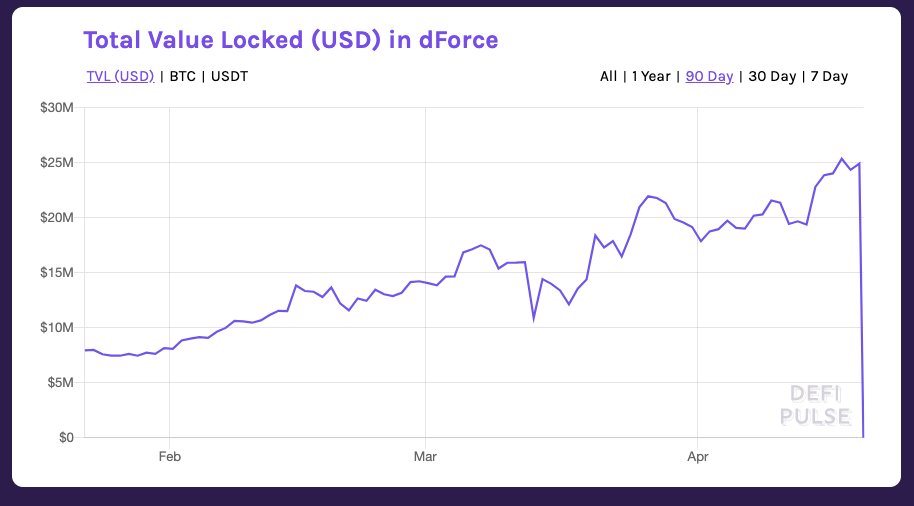
It seems like an attacker was able to supply imBTC to @LendfMe...then withdraw more than he deposited.
What was happening?
2/x
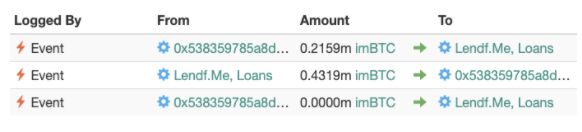
When a process is interrupted in the middle, initiated again, then both the original and "re-entered" processes execute, a re-entrancy attack has occurred.
pic source: @hackernoon
3/x
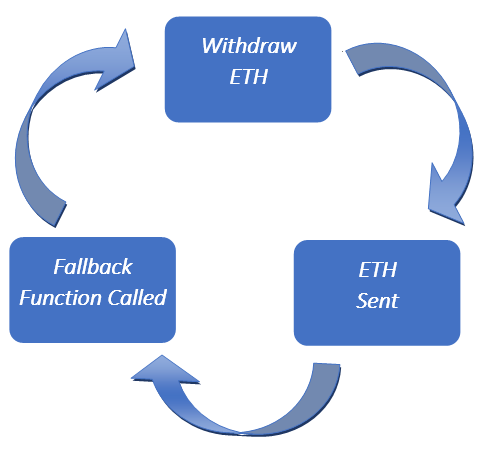
In simplistic terms, during the hack, you:
- Submit a legitimate withdrawal
- Before the contract could update your balance...
- ...recursively withdrew more than you are entitled to
hackingdistributed.com/2016/06/18/ana…
4/x
Hacker deposited imBTC as collateral, then initiated a re-entrancy attack, withdrawing much more collateral than he deposited ($25M) initially.
But how was this possible?
5/x
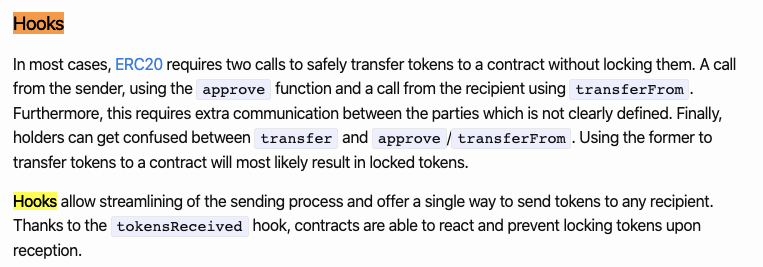
It’s like a more flexible version of ERC20. One of its features, “hook”, streamlines transactions, but also makes re-entrancy attacks easier.
@Consensys did a code audit that explains how this works:
github.com/ConsenSys/Unis…
6/x
This is a testament to the fact that code audits are not just security theater. They are a worthwhile investment!
7/x
Chinese readers, a more detailed walkthrough from @SlowMist_Team:
matataki.io/p/3460?c=83748…
8/x
9/x
afaik Uniswap v1 is made for ERC20. ERC777 promises backwards compatibility. The imBTC pool was supplied by users, not Uniswap.
defirate.com/imbtc-uniswap-…
10/x