172.217.23.202 > Google
172.217.23.238 > Google
216.58.201.110 > Google
216.58.201.106 > Google
172.217.23.227 > Google
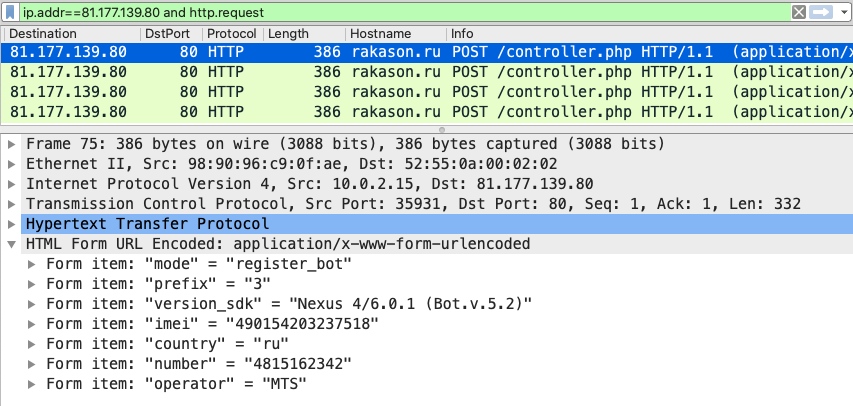
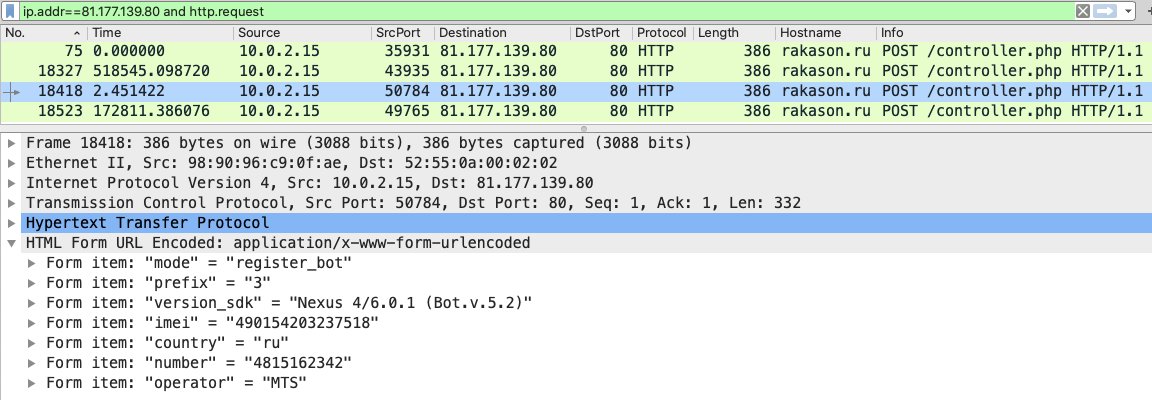
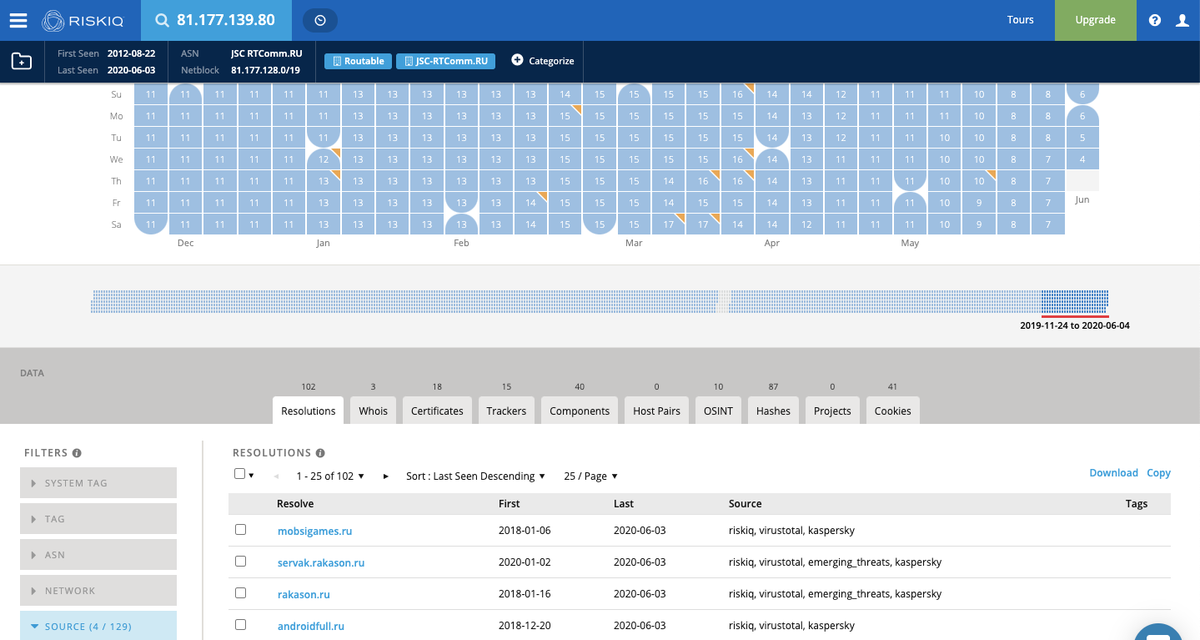
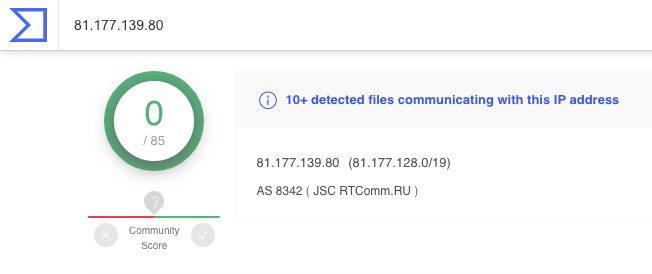
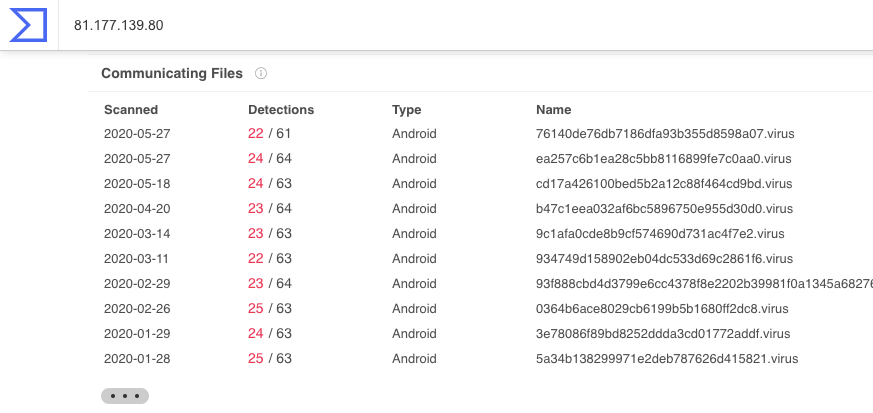
81.177.139.80 > not google. Investigate.
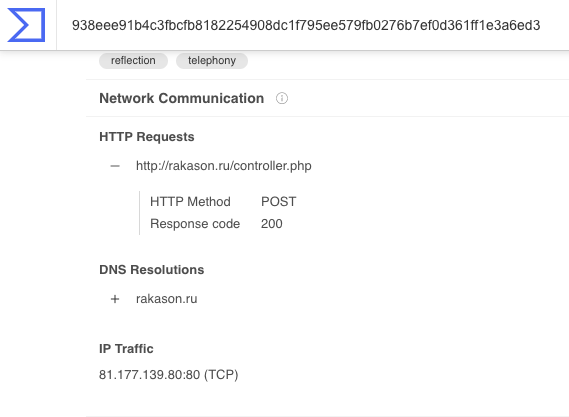
[1] virustotal.com/gui/file/8195a…
[2] virustotal.com/gui/file/89941…