1/
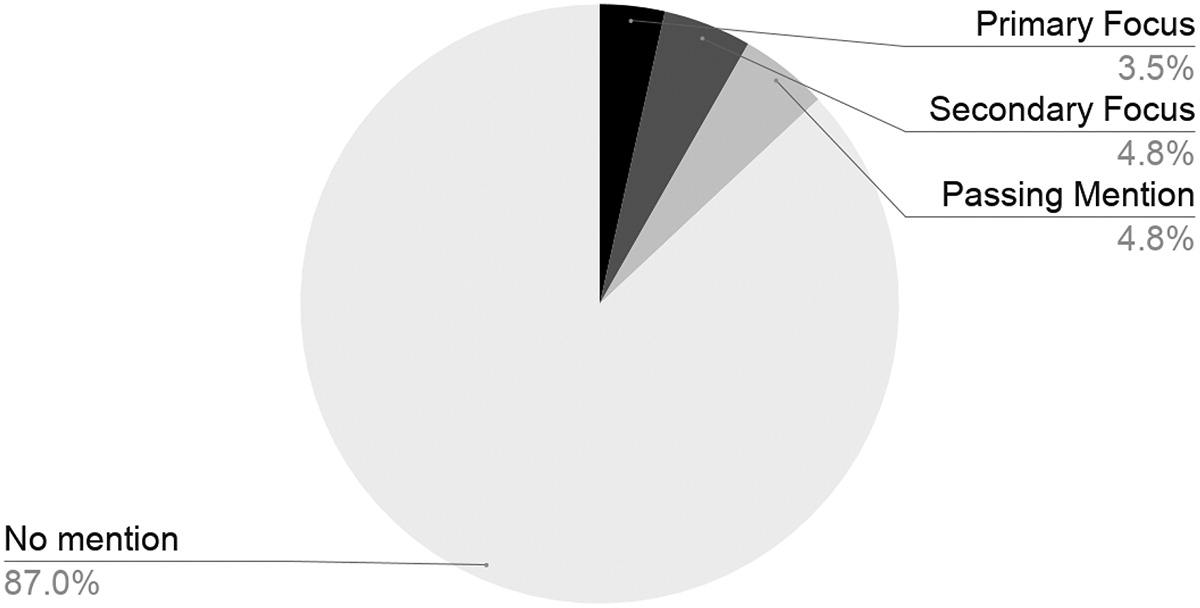
tandfonline.com/doi/full/10.10…
2/
3/
4/
5/
6/
7/
8/
9/
10/
11/
12/
NSO's Pegasus was also implicated in the murder and dismemberment of Jamal Khashoggi.
13/
14/
15/
Ron Deibert, who runs Citizen Lab, wrote a powerful afterword for ATTACK SURFACE, the forthcoming Little Brother novel.
read.macmillan.com/promo/attacksu…
16/
17/
18/
19/
"Above all, I hope you become inspired to use them to create a better world than the one in which we now live."
eof/




