1/
toool.us
2/
3/
4/
5/
6/
dl.acm.org/doi/abs/10.114…
7/
cacm.acm.org/news/246744-pi…
8/
9/
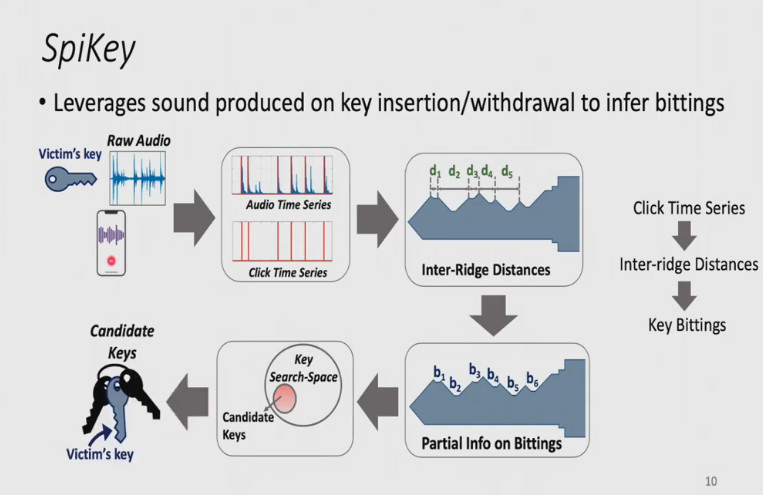
10/
What's more, it dispenses with the need for lockpicking altogether: obtain an advance recording, infer the key, make the key, enter the premises.
11/
12/
sparrowslockpicks.com
eof/





