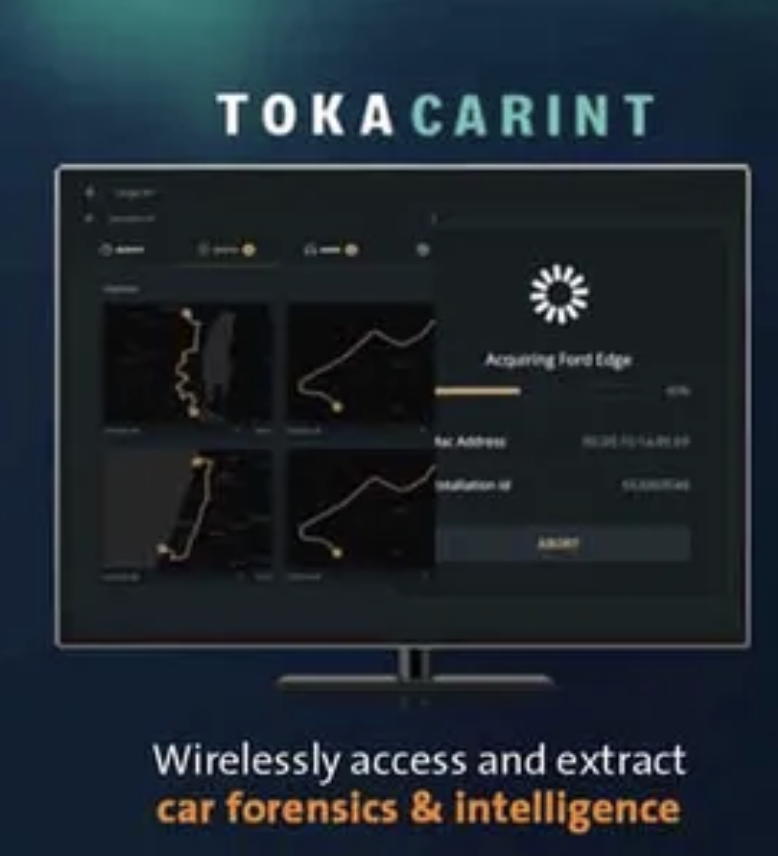
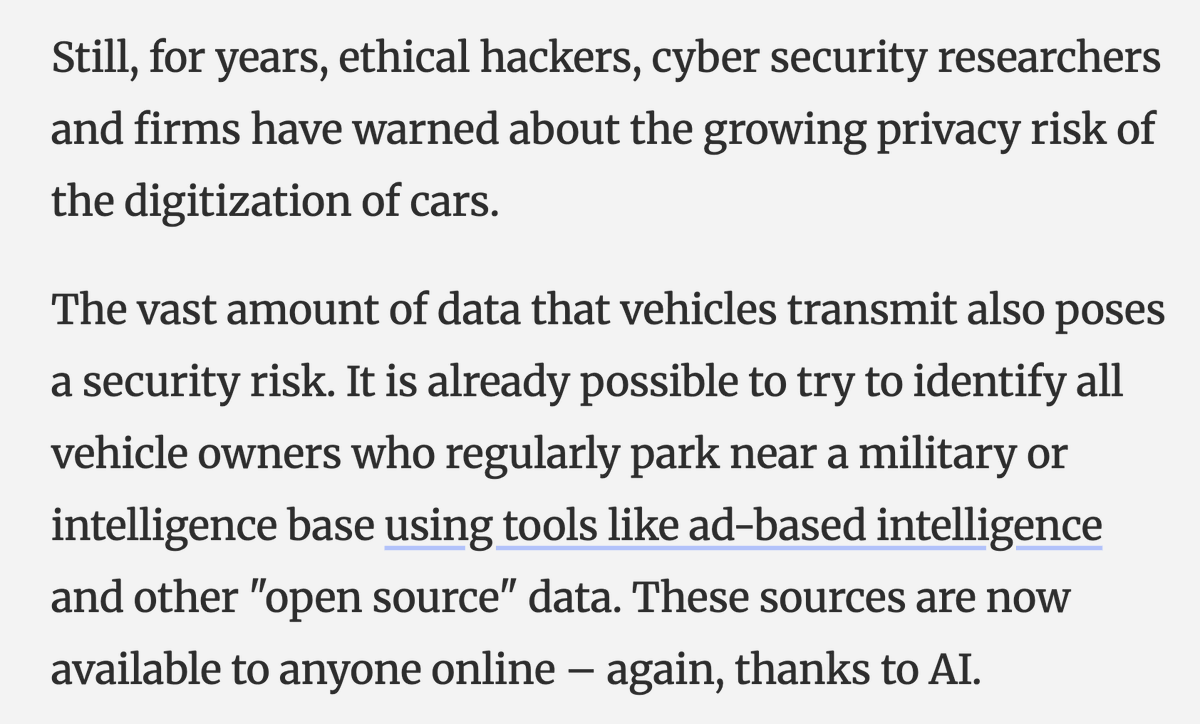
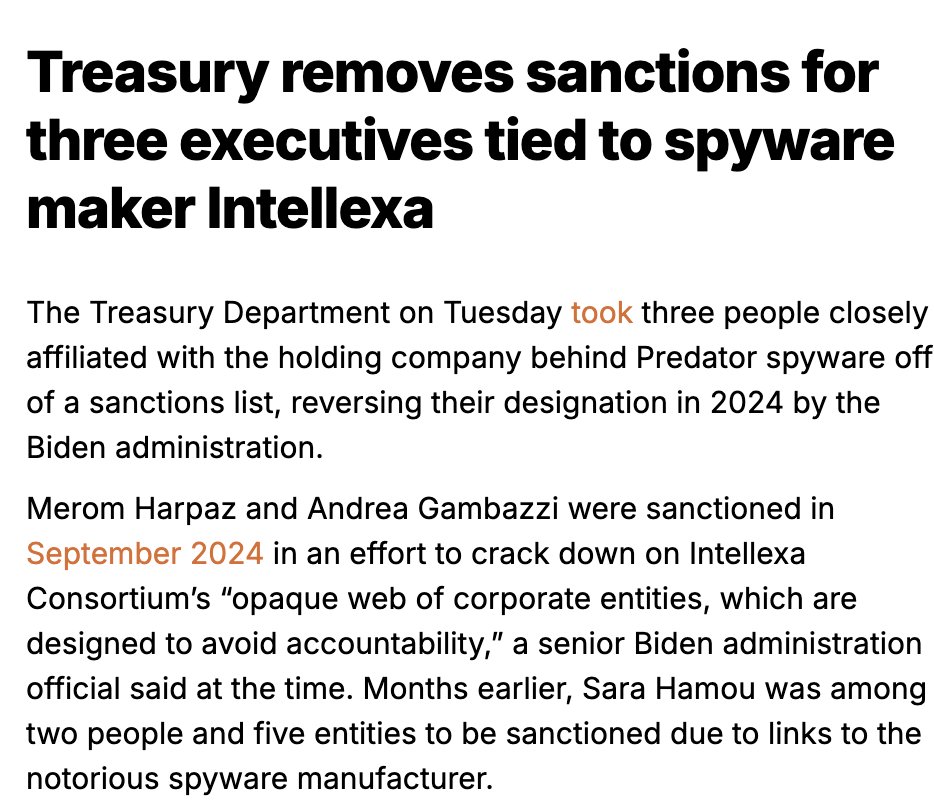
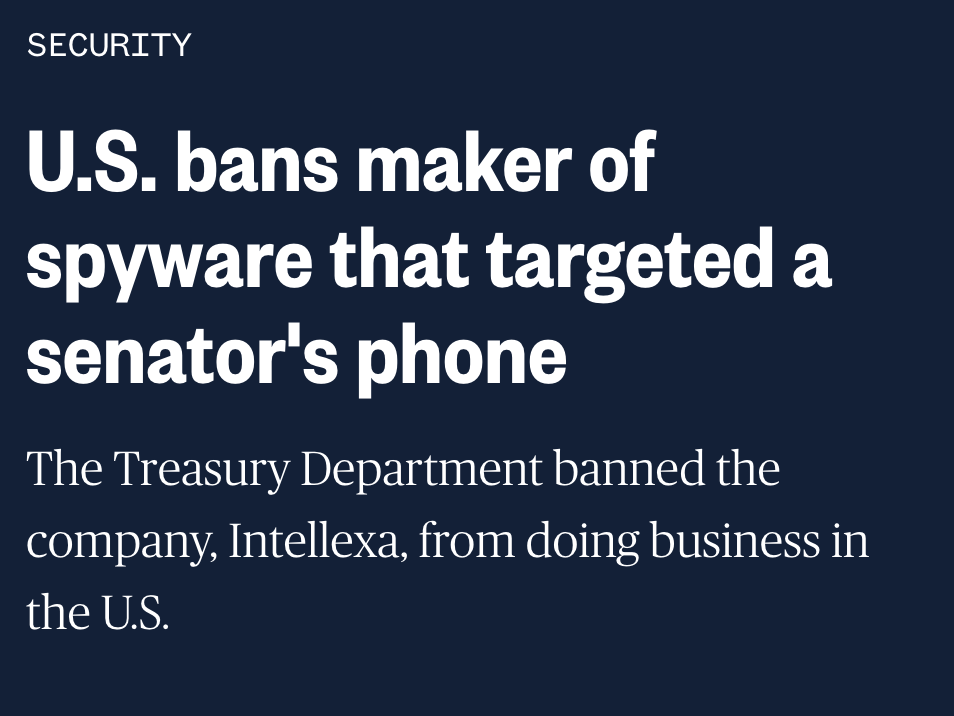
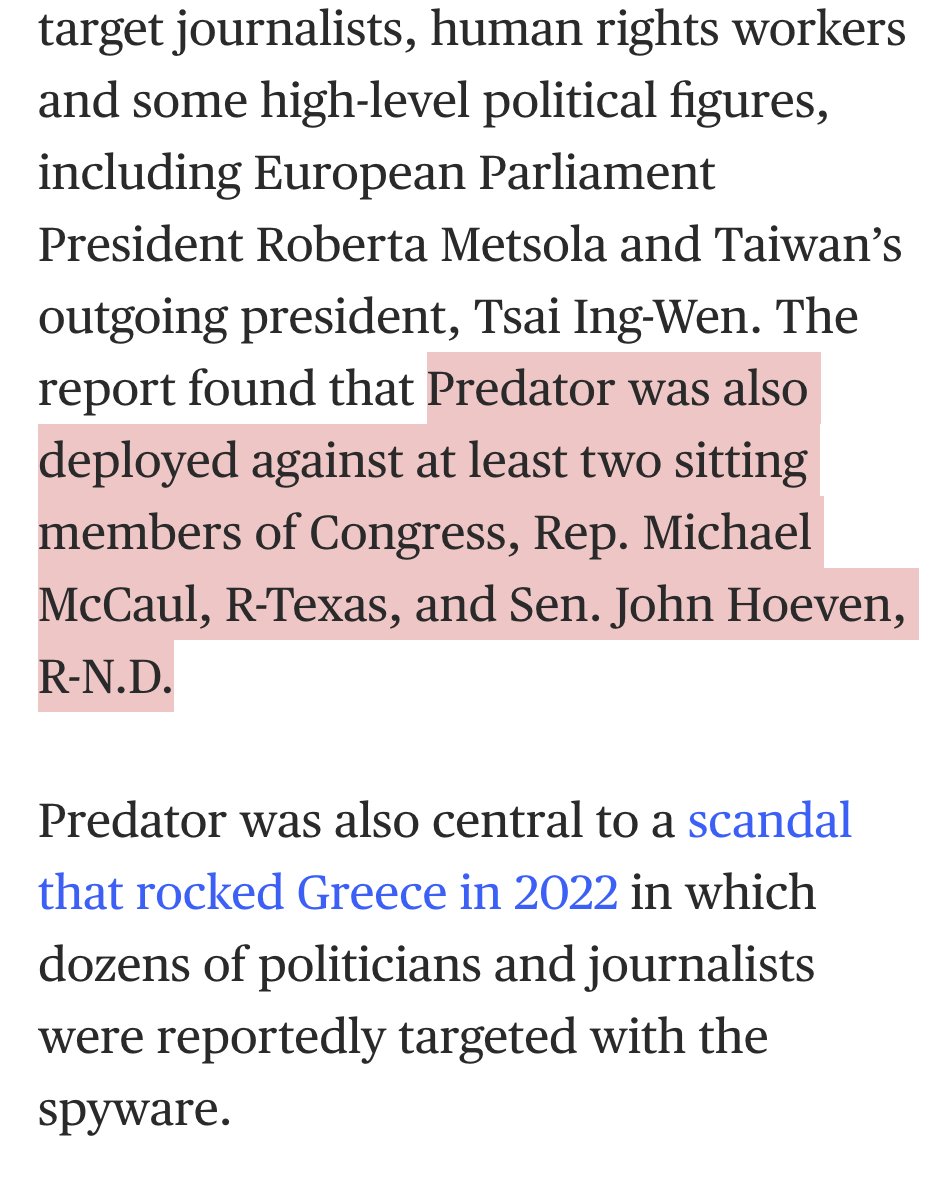
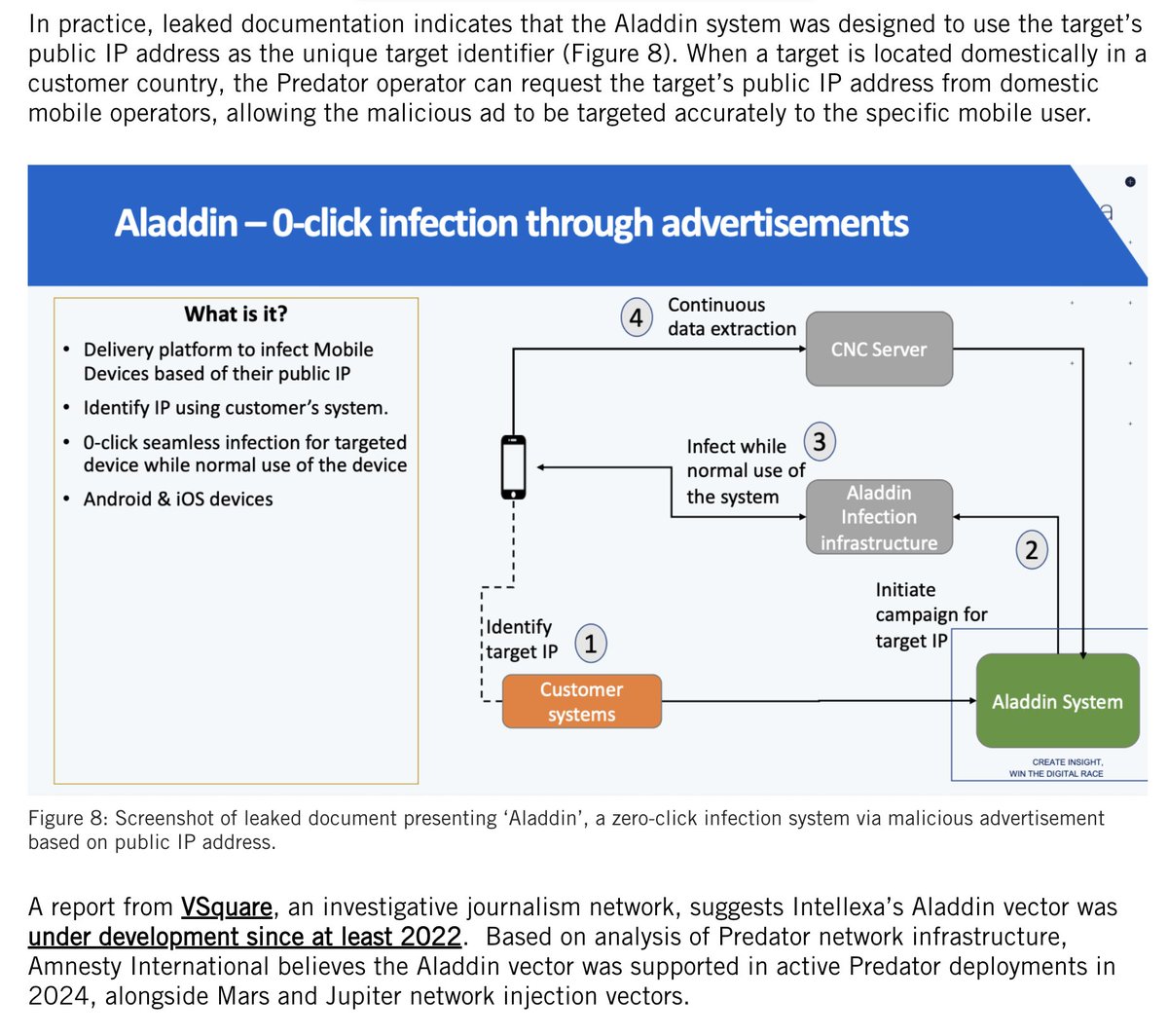
After reviewing a lot of footage there seem to be 2 types of ppl at the #capitolbreach.
Group 1: Selfies. Unsure what to do once inside #CapitolBuilding
Group 2: Purposeful. men who know each other & head for senate floor w/tactical gear & backpacks.
Group 1: Selfies. Unsure what to do once inside #CapitolBuilding
Group 2: Purposeful. men who know each other & head for senate floor w/tactical gear & backpacks.
https://twitter.com/jsrailton/status/1347011413101998080
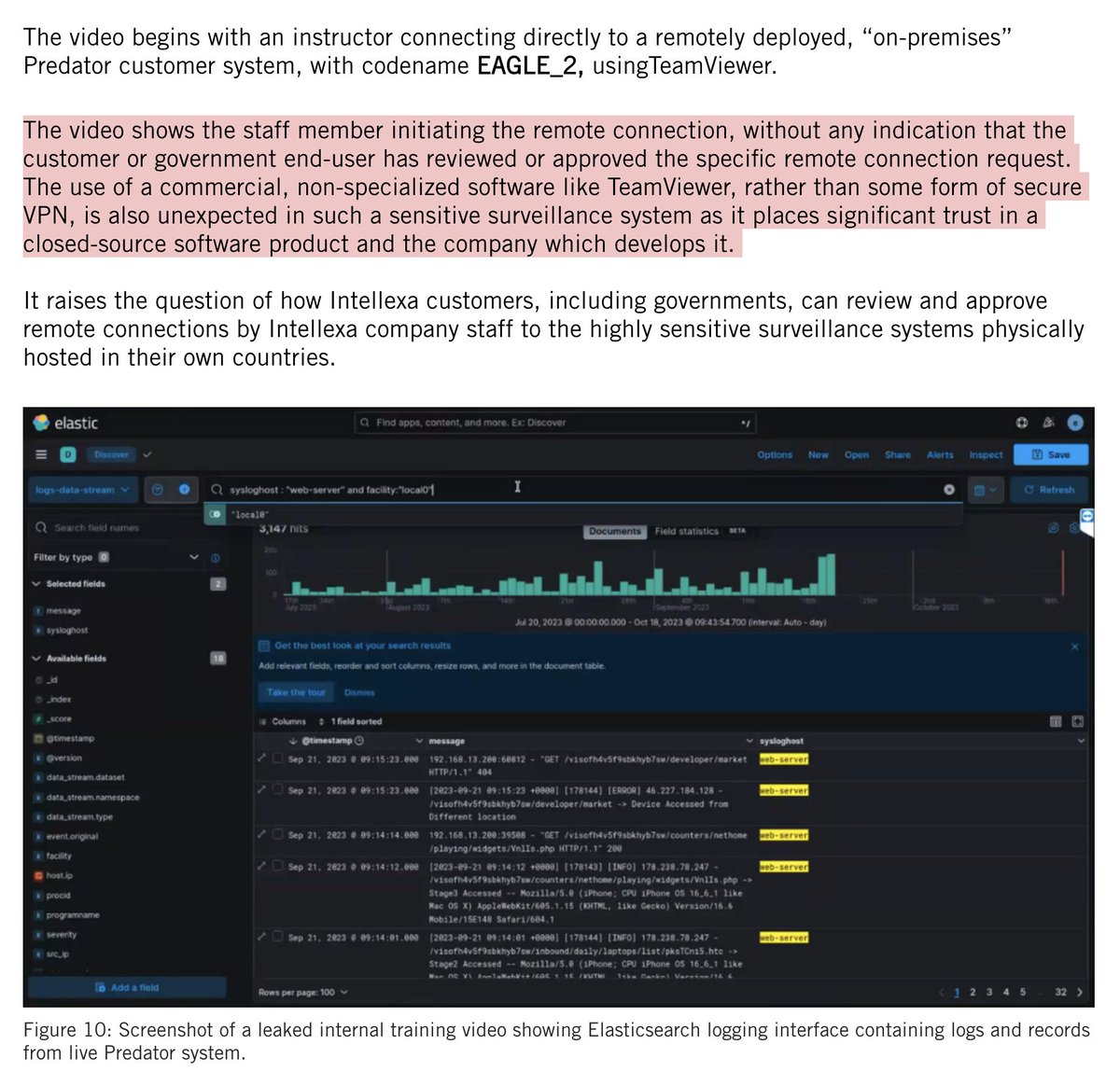
Group 2: Take a look at how quickly these men move in and make entry as soon as the outer glass (& inner shutters) of the window are breached.
https://twitter.com/jsrailton/status/1347035153860853761
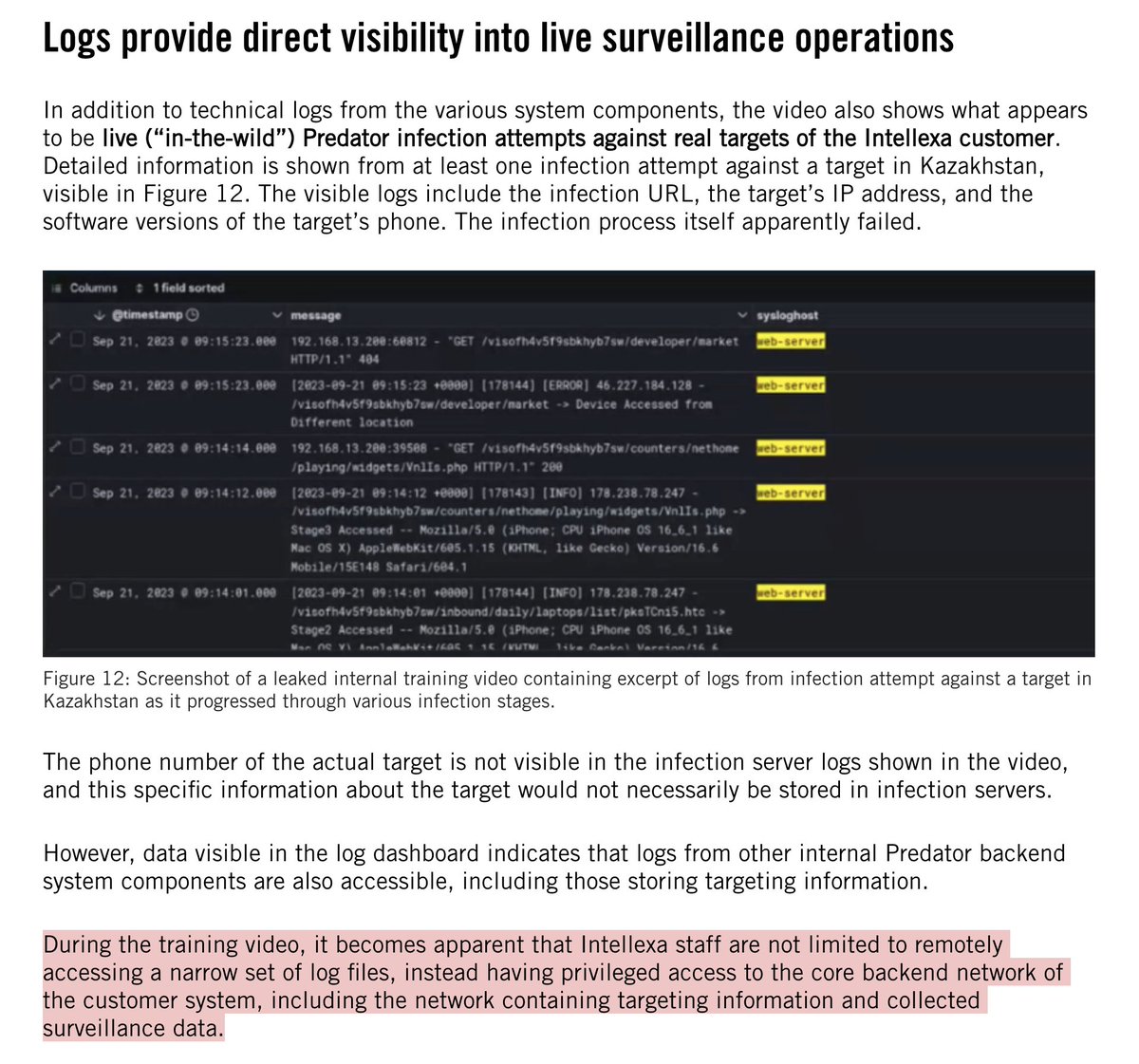
Group 2: window entry. First man in helped by others, is wearing a bulletproof plate visible as a bulge under his jacket. Other men with kevlar helmets follow with heavy military backpacks & gear. 



• • •
Missing some Tweet in this thread? You can try to
force a refresh