Of interest to advanced users.
uBlock Origin can function as a fully-fledged script blocker in default-deny mode:
1) Check "Disable JavaScript" in Settings pane
2) Enable "Medium mode"
github.com/gorhill/uBlock…

uBlock Origin can function as a fully-fledged script blocker in default-deny mode:
1) Check "Disable JavaScript" in Settings pane
2) Enable "Medium mode"
github.com/gorhill/uBlock…


Result when visiting a typical webpage (note the "domains connected" figure, and the pluses in overview pane in the screenshots).
Only passive content resources allowed, such as images, CSS, etc.
Only passive content resources allowed, such as images, CSS, etc.

Result when turning off the no-scripting switch.
This will allow only 1st-party JavaScript to execute.
This will allow only 1st-party JavaScript to execute.

A capability specific to uBO: allow scripts from a specific 3rd-party domain, but ONLY for the current site: scripts from disqus\.com are given permission to execute. With NoScript, allowing disqus\.com would allow it everywhere, on all sites. 

But then if you really want to allow disqus\.com everywhere by default, it's just a matter of creating a global rule for it. 
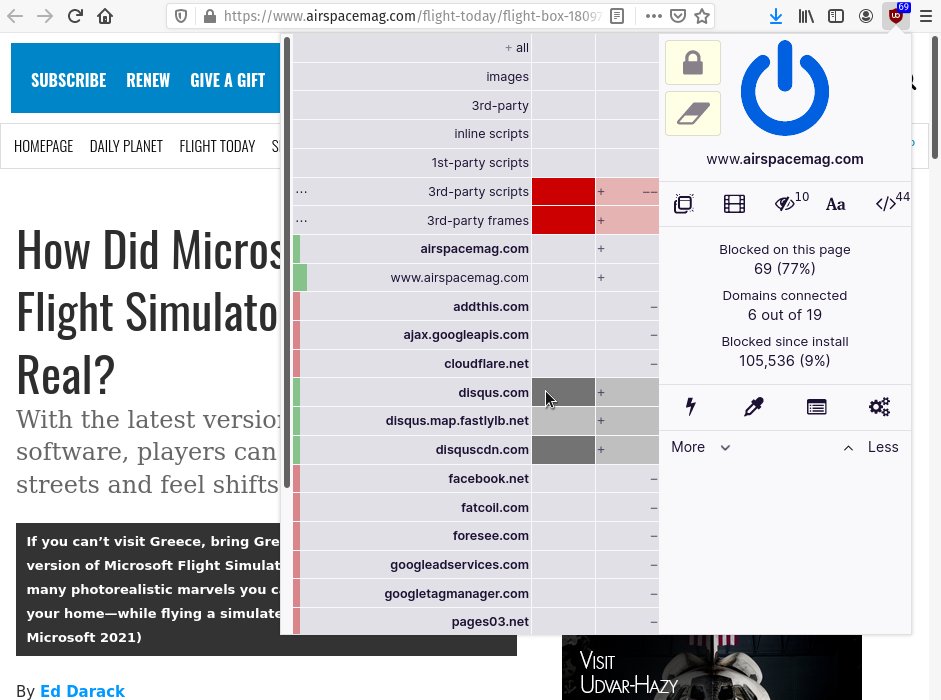
If you do not have time/patience to find the minimal set of 3rd parties which are needed to un-break a site, you can also just remove the block rule for all 3rd-party scripts (and frames) -- this will affect ONLY the current site. 

If you have block rules for specific domains, they will still be enforced when removing the block rule for 3rd-party scripts, because they are more specific. 

Note that at any step, uBO creates rules which are temporary. Use the padlock if you want to keep the changes -- this ensures you are not bloating your ruleset with every single change. Typically, your permanent ruleset is for sites you visit regularly. 

Gray ("no-op") rule means "remove block rules affecting this cell, but keep applying filters from lists".
When you disable block rules, you will never ever end up being less protected than you would be with default settings/lists ("Easy mode" in graph).
When you disable block rules, you will never ever end up being less protected than you would be with default settings/lists ("Easy mode" in graph).

You can assign a keyboard shortcut to the "Relax blocking mode" command, to lower blocking mode in steps, without having to visit the popup panel:
No JavaScript => No 3rd-party JavaScript => block as per filter lists.
No JavaScript => No 3rd-party JavaScript => block as per filter lists.

Sorry for the noise, I had to re-post one of the tweet, it had too many typos in it, and I want to be able to use this thread as a reference.
• • •
Missing some Tweet in this thread? You can try to
force a refresh
















