As promised, here’s my little thread with (bad) ruminations of mine about Tatsu Auth Debug and KIS or Why Those Keys & Dumps Are So Valuable
Important: I have never touched any of the devices mentioned below myself. So I can only interpret the data their actual owners sent me…
Important: I have never touched any of the devices mentioned below myself. So I can only interpret the data their actual owners sent me…

…thus, the information in this thread may turn out partially or completely WRONG. Proceed with reading on your own risk!
So a certain source of prototypes contacted me to ask help with A14 prototypes - they couldn’t JTAG into them. Astris was showing standard error message telling that debugging is not supported
My first advice was to use the latest available to that moment Kanzi FW (0.99) and enable KIS:
astrisctl kis 1
astrisctl kis 1
What’s KIS? Apparently some new Apple’s debugging protocol to replace (or supplement?) SWD. As I mentioned above, I don’t have a personal access to dev-fused A14 devices, so I couldn’t sniff it on physical level
Anyway, after enabling KIS first we tried to reconnect the DVT iPhone 12 (CPRV 10 or 11, CPFM 01). And pow! The output changed! 

Long before the A14 release I’ve started to hear stories about the debug authentication coming to Apple’s SoCs. Probably to stop people like me leaking ROMs and decrypting production firmware. And here it is!
Now we can do whatever with the device - dump SecureROM/SEPROM, decrypt KBAGs and etc.
Now let’s try with disabled Internet to find out if it requires auth. Oh no! Doesn’t work
So apparently auth is already here with A14 rev 00 (KIS is still enabled - it’s important), but Apple allows it! It also means that debug auth:
1) Can be passed outside of Apple (actually a good old gs.apple.com is used)
1) Can be passed outside of Apple (actually a good old gs.apple.com is used)
2) Apparently is basically a black/white list, so as long it’s in the white list (or outside of the black list) you can debug it without Apple Connect account or something like this
Also means that either you pass or not pass the auth, Apple will have your IP! But apparently they either don’t check logs or just do not care - the (pre-) EVT device was whitelisted for a long time, and maybe still is
But the time goes, and new things leak. One of those things was Kanzi FW 1.26. There’re quite many changes, but that’s a different story. The (pre-) EVT device owner got it pretty quickly too
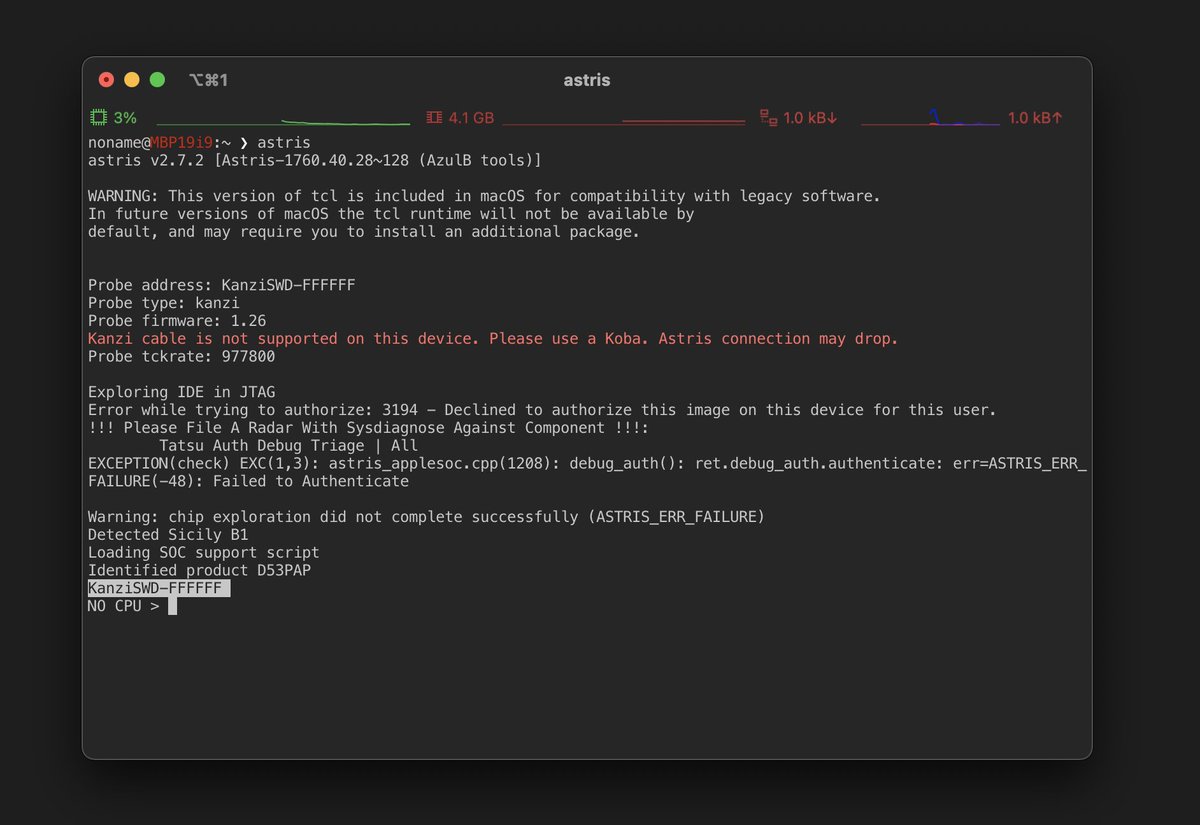
And wow! Debug auth is now requested in SWD mode too (this is DVT)!
(That scary red text about Koba though. And it also decreases the tckrate to 1 MHz)
(That scary red text about Koba though. And it also decreases the tckrate to 1 MHz)
Here’s what KobaSWD looks like, btw (basically glorified Kanzi - and I’m not just about its exterior design) 

Let’s try with the (pre-) EVT device now. The same warning, but it works. The owner reported they tried the same without the Internet connected and it worked too! So maybe that’s why debug auth is enabled with KIS on Apple’s side - because it’s pointless to disable anyway? 

Conclusions:
1) A14 of revisions 10/11 are likely useless toys (they are pretty common)
2) A14 of revision 00 (I’ve only seen one) + Kanzi with FW 1.26 (or better Koba) is the way to go
3) A15 and later are probably useless in any revision
1) A14 of revisions 10/11 are likely useless toys (they are pretty common)
2) A14 of revision 00 (I’ve only seen one) + Kanzi with FW 1.26 (or better Koba) is the way to go
3) A15 and later are probably useless in any revision
Now that Koba and the (pre-) EVT device are a little bit nearer to me, you can expect more information in the future - at the very least would be nice to sniff whatever happens between Astris and TAD. But for today, that would be all!
Quick update on this: apparently KIS works without the auth on CPRV 00 A14 too - just got another report
https://twitter.com/nyan_satan/status/1402707718276800512
• • •
Missing some Tweet in this thread? You can try to
force a refresh













