Does everyone realize that this is almost assuredly @Merck using the Ad ID Consortium to target ads to cancer patients? BOK's former company left this data-co-op (adexchanger.com/online-adverti…)
I'll do a thread on this, explaining how you can audit a website like keytruda.)com ⚖️⛈️🧵
I'll do a thread on this, explaining how you can audit a website like keytruda.)com ⚖️⛈️🧵
https://twitter.com/bokelley/status/1405568632244125697

First, BOK's old company used to own the domain facilitating these data flows "adnxs.com" - this domain was used in the Ad ID Consortium & was the most popular. AT&T bought appnexus, pulled out of the AD ID C, & seemingly "gave the domain up"
admonsters.com/universal-id-a…
admonsters.com/universal-id-a…

*I haven't 100% confirmed that Appnexus/AT&T has zero control over their old adnxs.com domain, but I know this domain is still used heavily by the Ad ID Consortium syncs, which AppNexus/Xander isn't part of, so this seems to indicate the domain was donated. TBD!🧐🖖
It's extremely common for Big Pharma to make websites for each product/medicine. Keytruda.)com is tied to other sites via similar tactics... random ass domains used to hide that they are cross-domain tracking vectors.
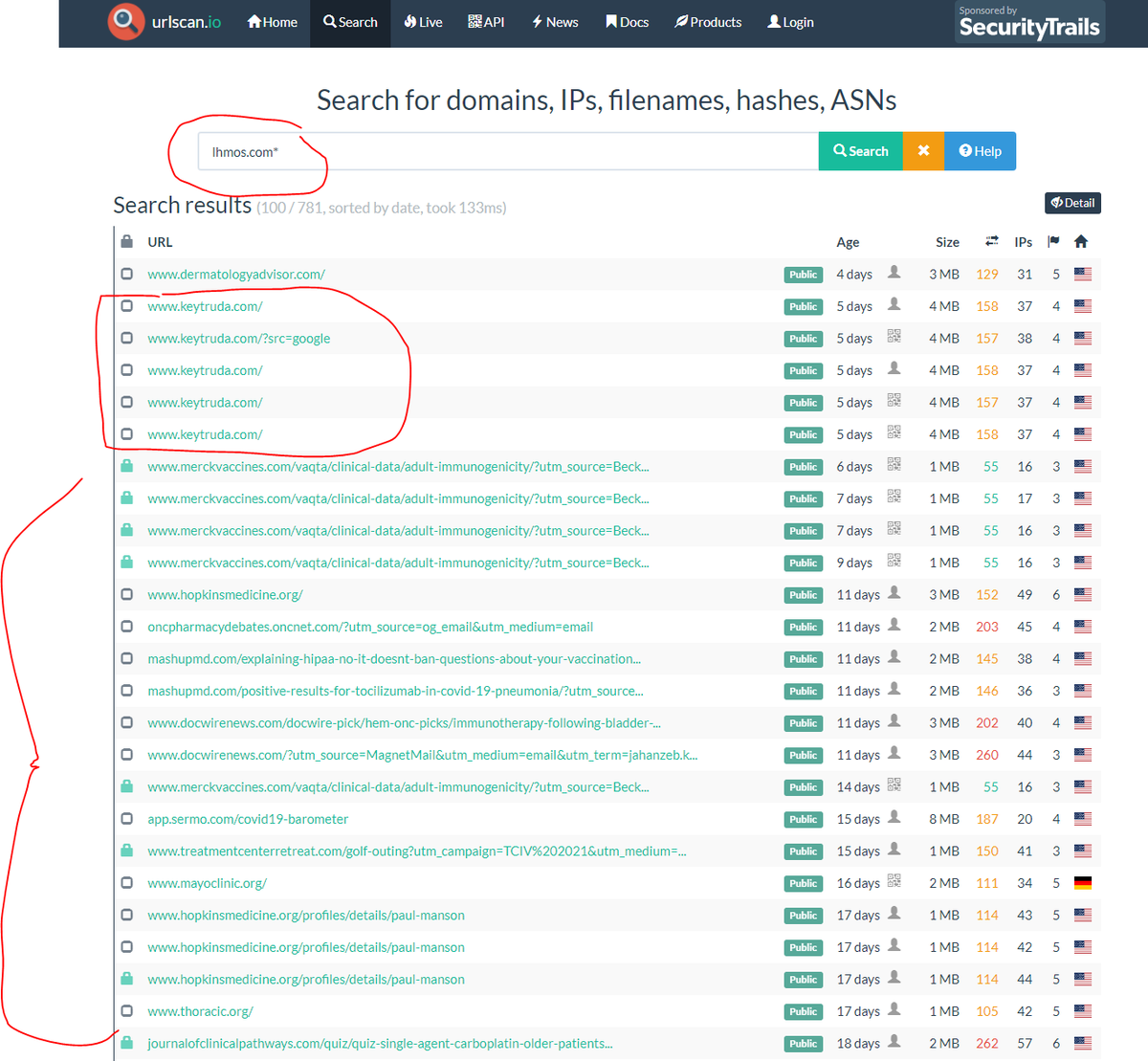
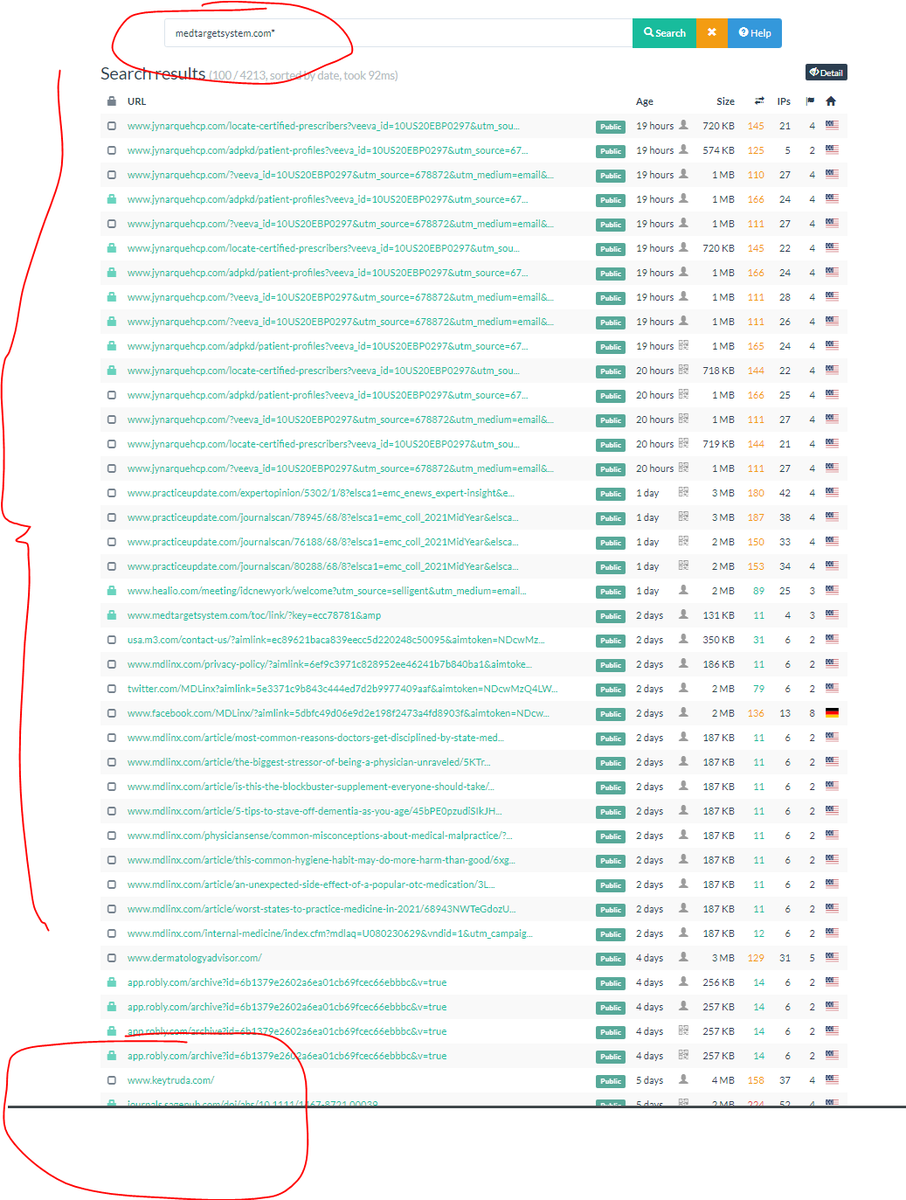
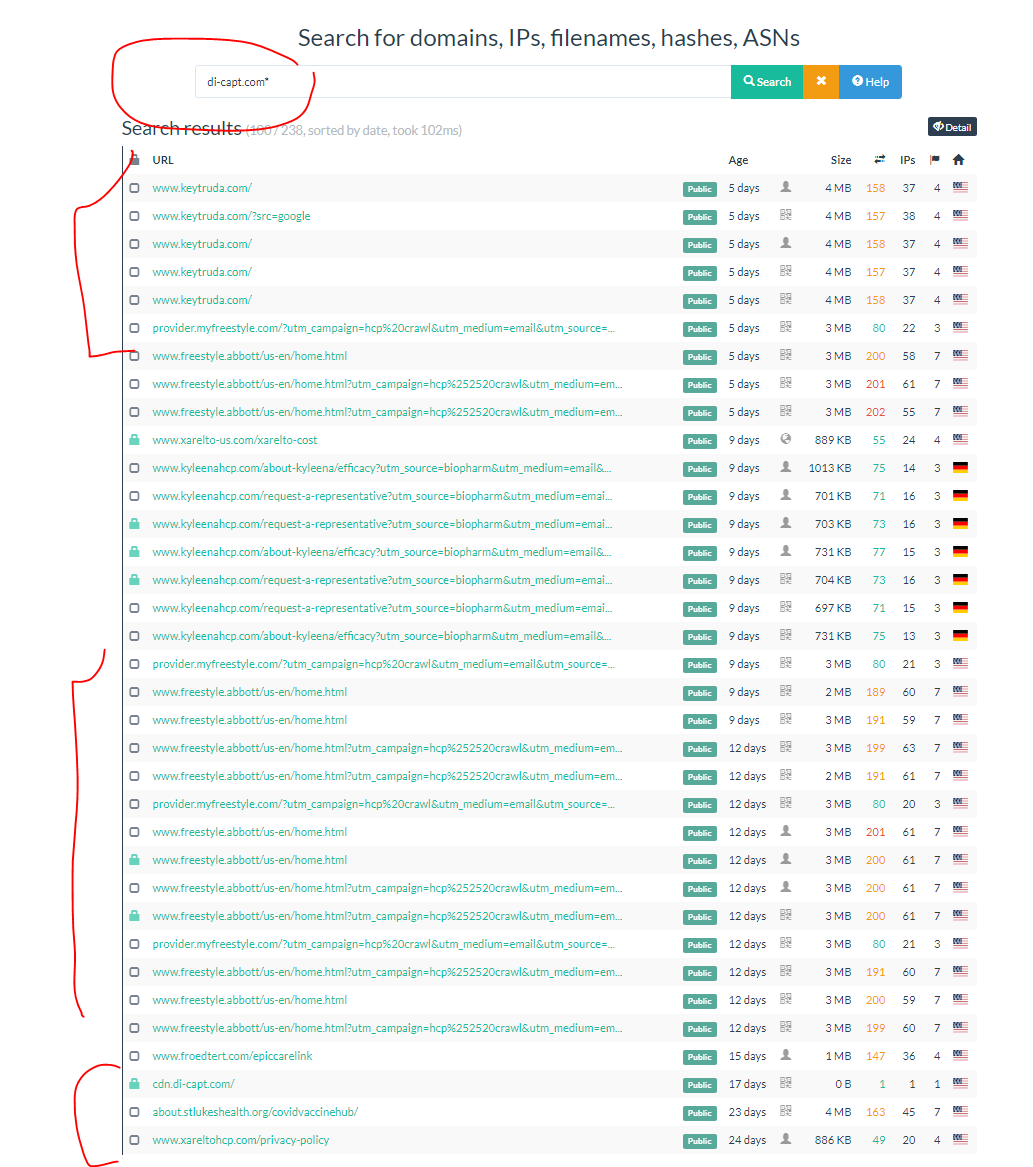
KT uses lhmos.)com + medtargetsystem.)com + di-capt.)com..


KT uses lhmos.)com + medtargetsystem.)com + di-capt.)com..
You will also see the domain "Adnxs.com" across these selling-cancer-patient-data-flows - this domain is where the Ad ID Consortium has been syncing IdentityLink people-based identifiers. The membership in the AD ID Consortium is big (investors.liveramp.com/news-and-event…) 


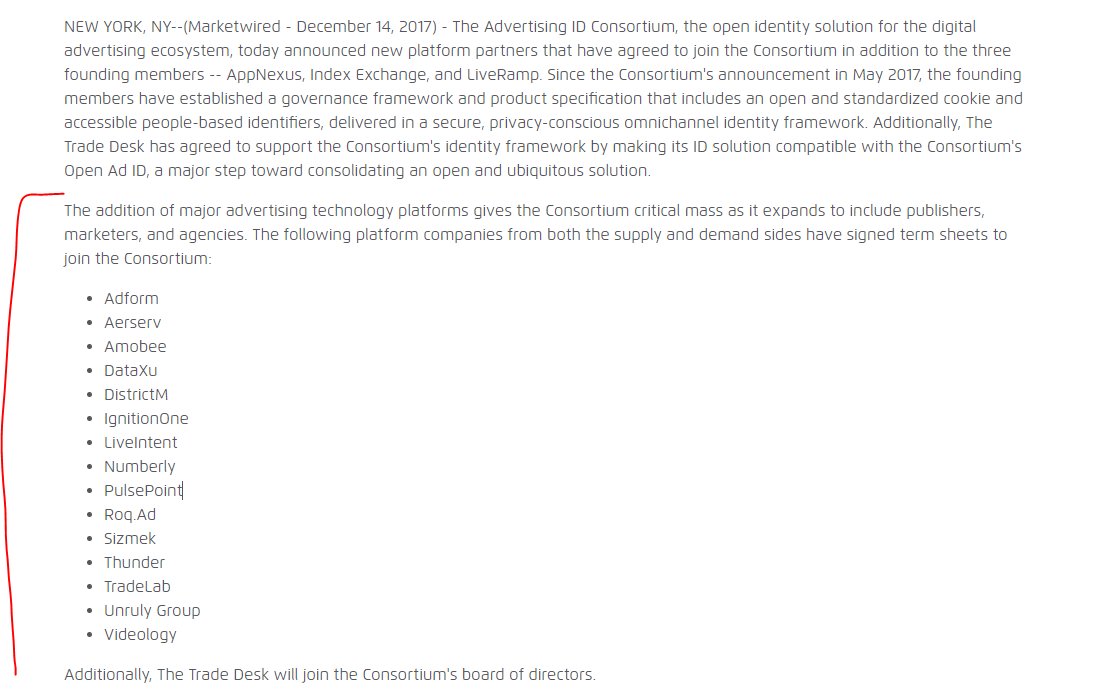
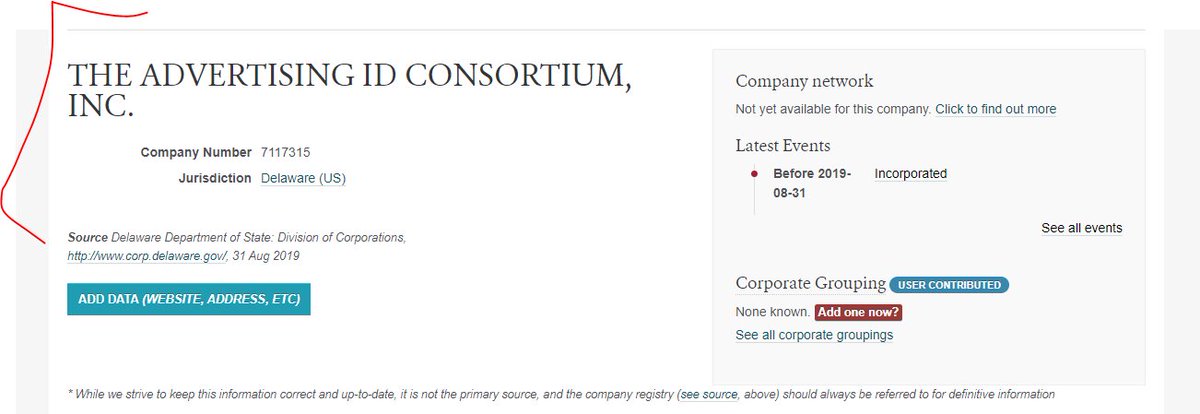
Is the AD ID Consortium a non-profit? Is it a for-profit? adidentity.org/what-we-do // Their FAQ notes that this is technically a Corporation, which has corporate registration in Delaware // This corp has not registered as a data broker in California or Vermont #illegalCCorpCoOp 



The Ad ID Consortium was abandoned by AT&T after the acquisition of AppNexus went through. I was on the conference call when it was announced and it was the least surprising ton of bricks to fall since GDPR was enacted - but the effort continued!! ⛈️💸⛈️⚖️ adexchanger.com/online-adverti…
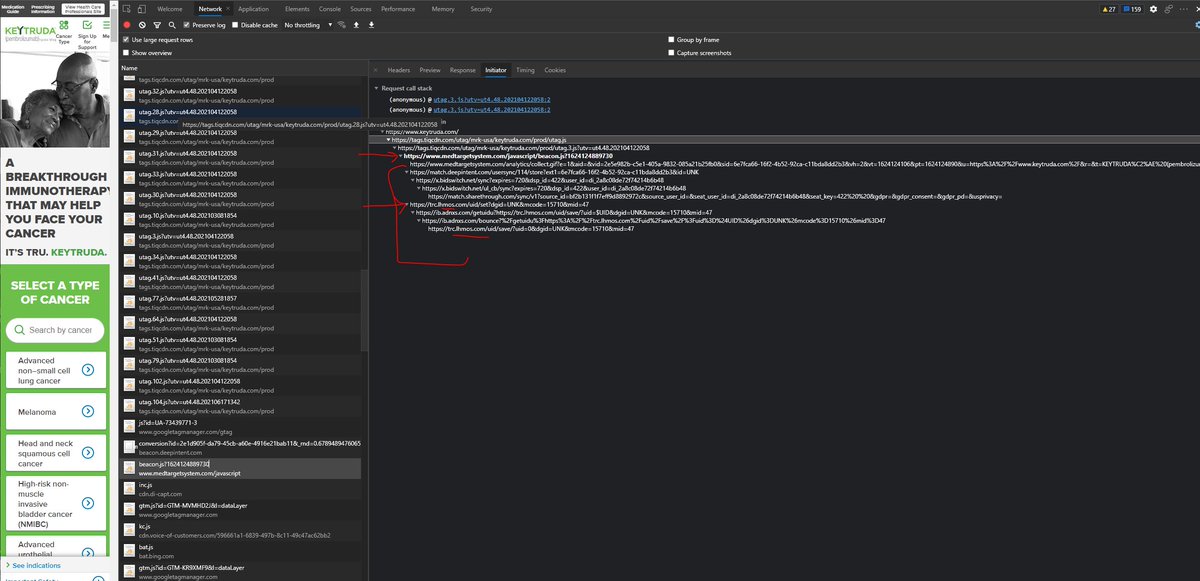
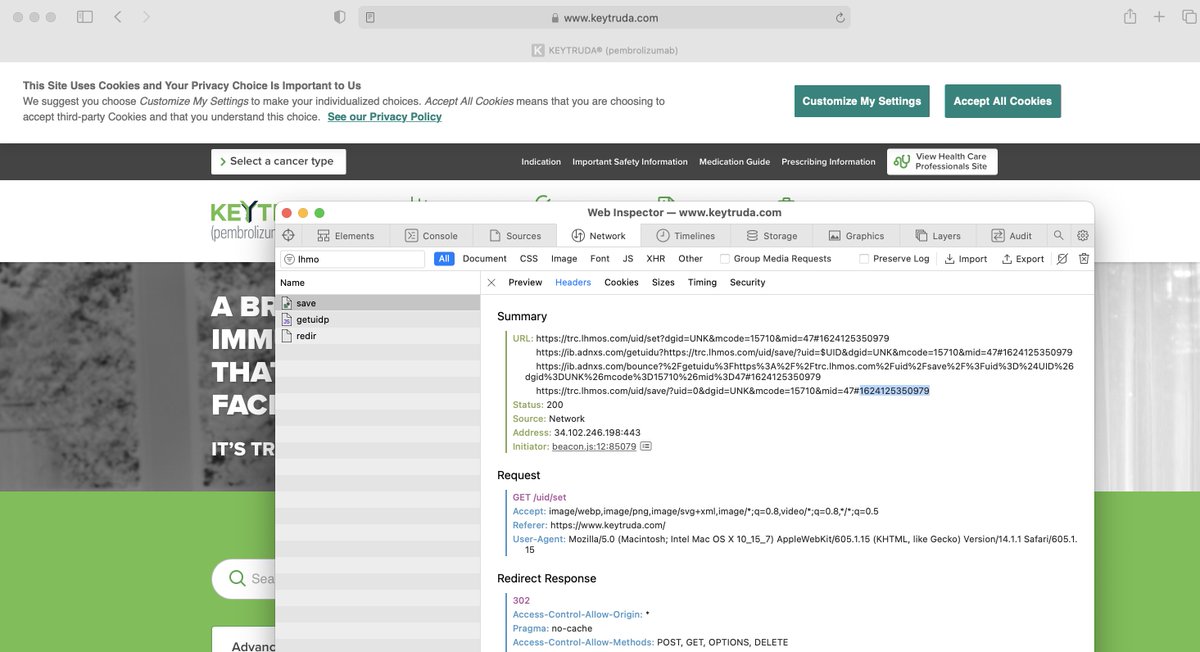
So to sync data from Keytruda to ad tech orgs, a javascript file hosted @ medtargetsystem.com/javascript/bea… (very obfuscated) will fingerprint the user + share data via triangle syncs to the Ad ID Consortium Domain + the cross-site Pharma tracking domain of lhmos.com 


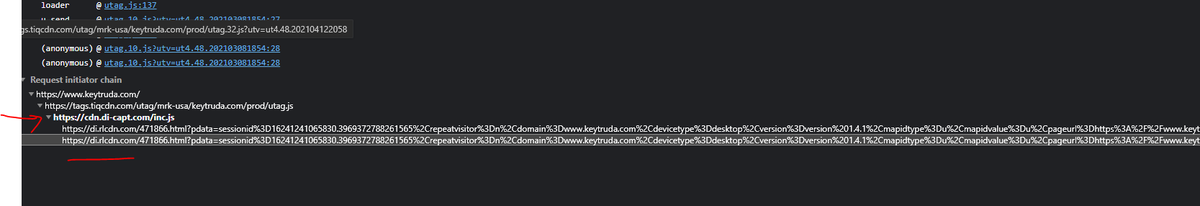
Another one of the Pharma cross-site domains @ di-capt.com conducts a sync with data sale company Tower Data -- Pharma is using separate domains for these syncs to reduce Safari's/other browsers/orgs ability to see the domain as a cross site tracking vector 
There seems to be over 800 websites tied to this Pharma advertising network tied to the Ad ID Consortium @ securitytrails.com/list/ip/13.248… - go to these sites, you'll see similar data flows to the Keytruda website
Example: worseninghf.com
The triangle syncs flow as-expected⤵️


Example: worseninghf.com
The triangle syncs flow as-expected⤵️
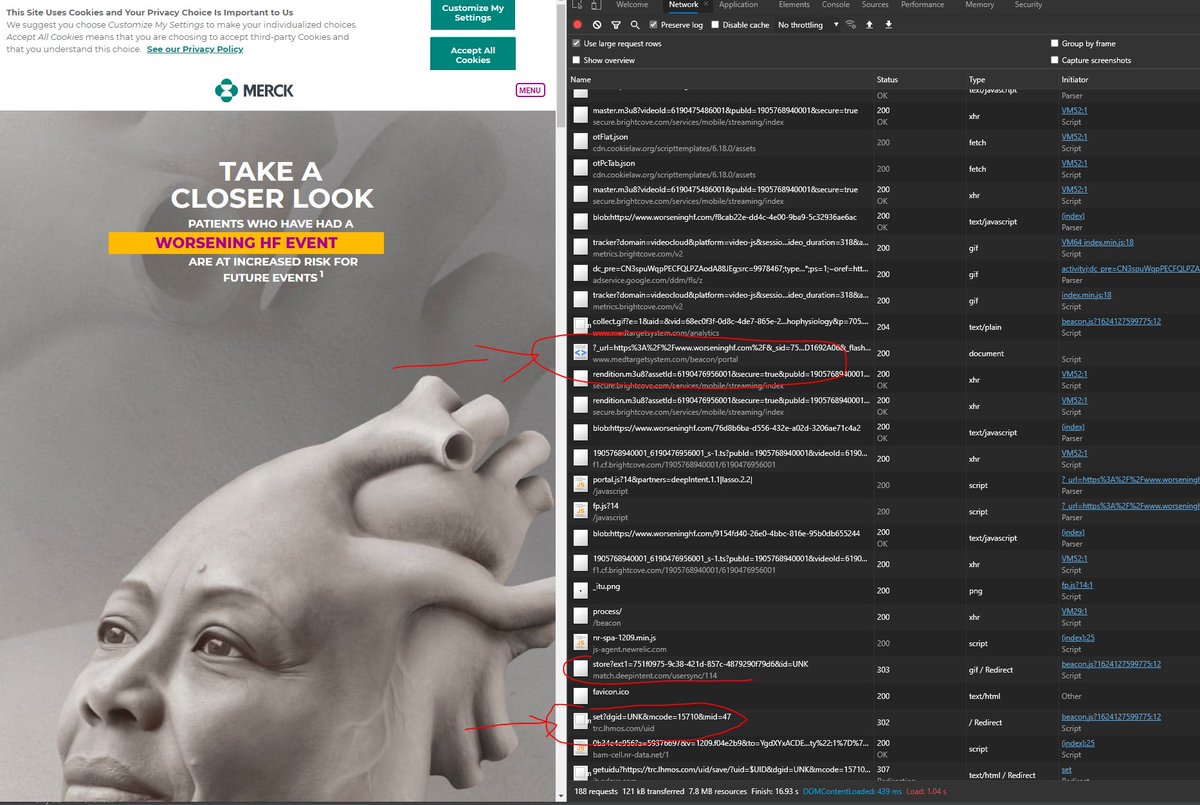
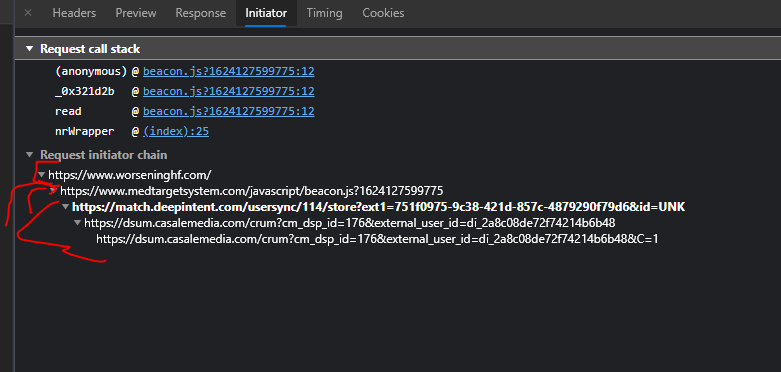
You may notice that there is a 301 location redirect, the backbone of non-compliant triangle user data syncs - the MedTargetSystem JS sends data to Pharma's "trc.lhmos.)com" then a sync to the Ad ID consortium @ "ib.adnxs.)com" reverse proxy shenanigans are transparent here ⛈️💸 
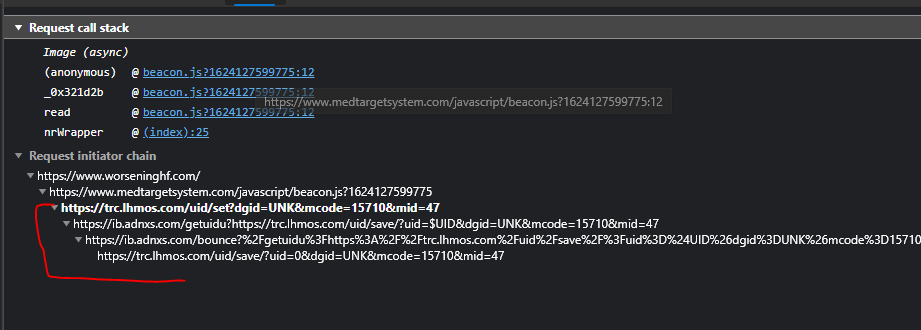
The Ad ID consortium are the kings of reverse proxies - they break consentful data flows & cookie blocks as a course of common practice. Their "ib.adnxs.)com" subdomain is tied to tons of "cookieless data syncs" across the biggest sites in the world. Tons & tons of custom flows. 
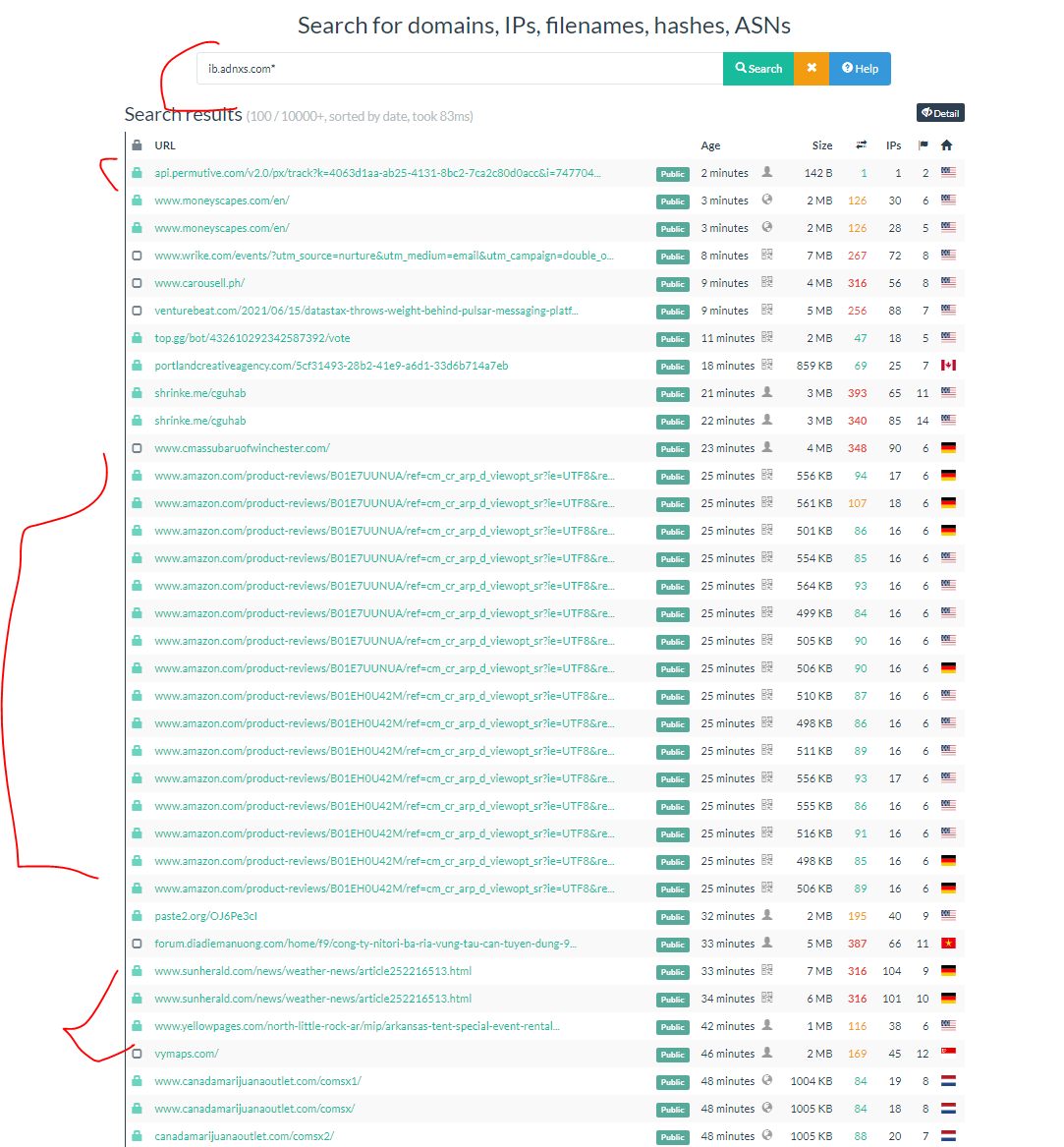
The AD-ID-C domain ties together their cookieless syncing with A records connected to specific IP addresses & tied to domains of their clients. Explore them here @ securitytrails.com/domain/p.updat… // A couple thousand of the biggest domains = biggest data co-op data breach on earth 


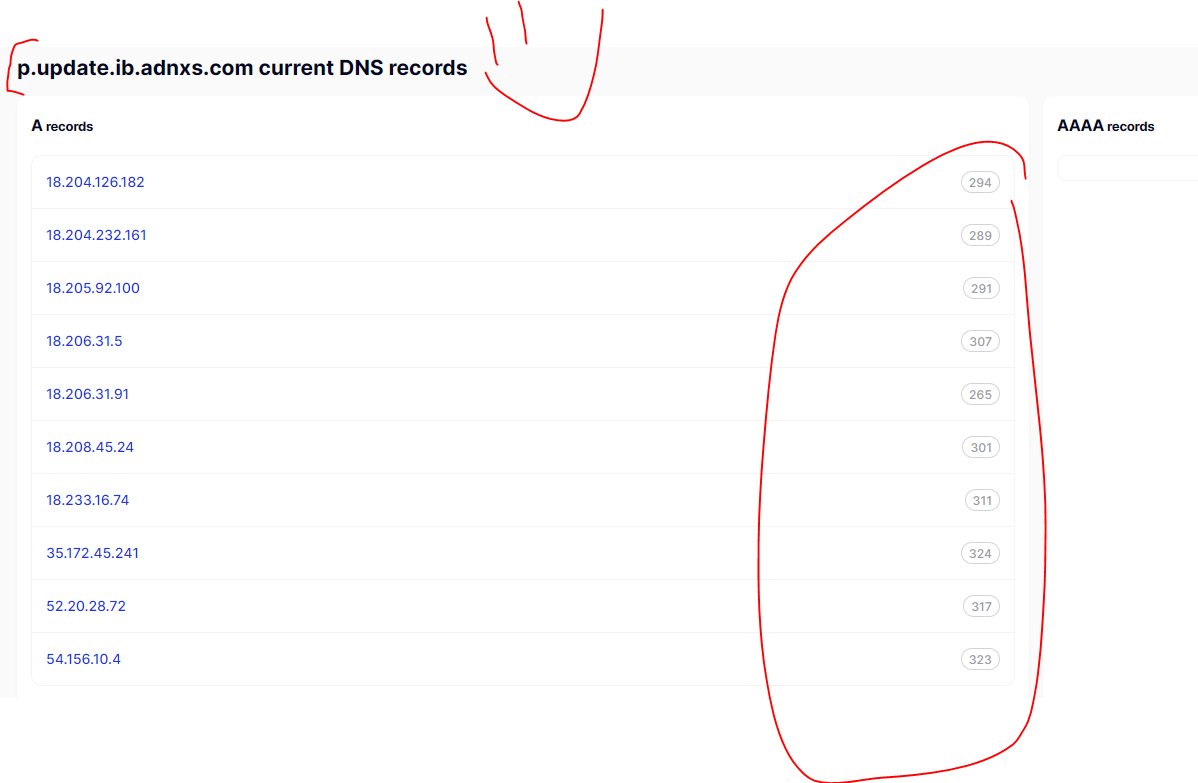
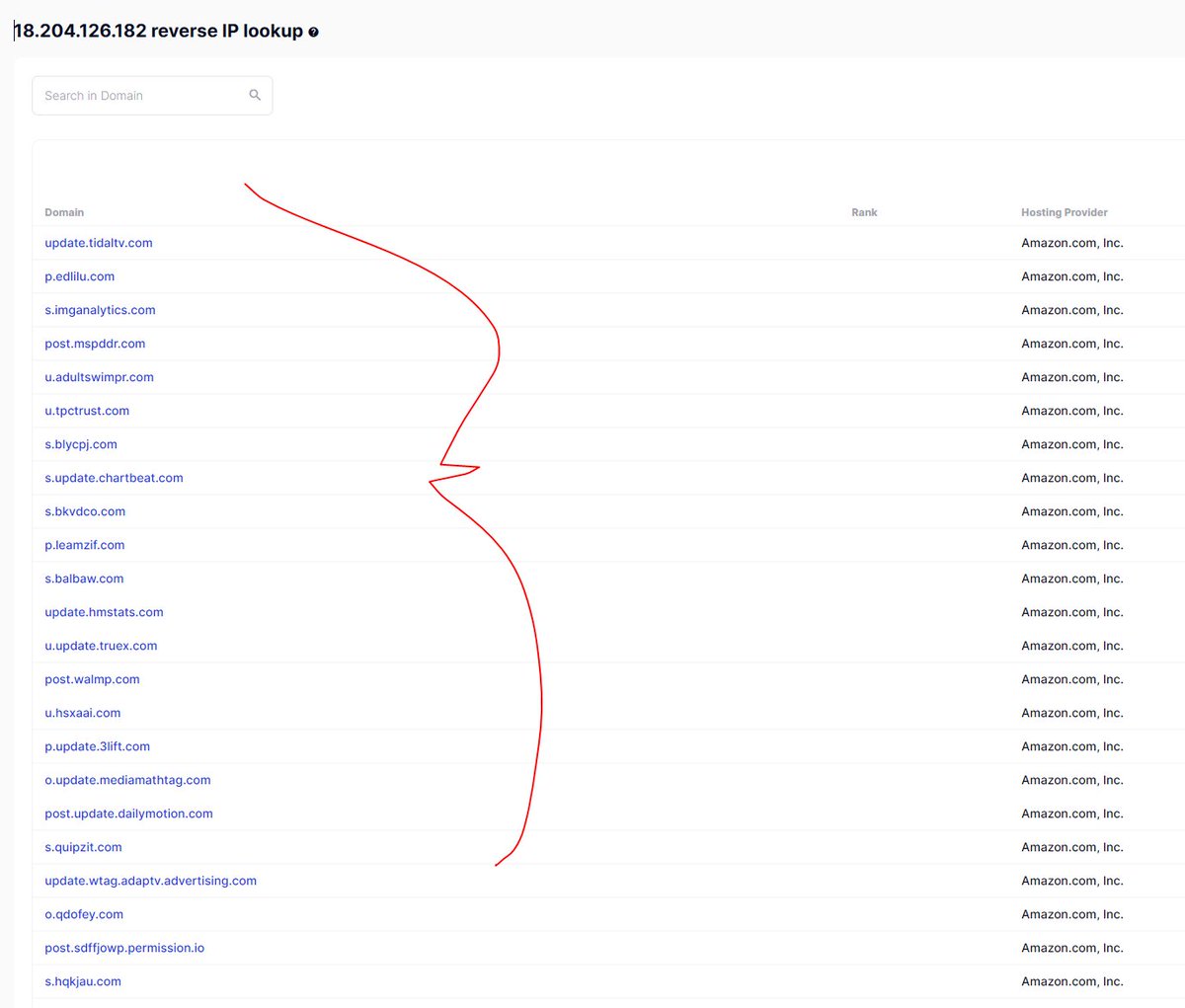
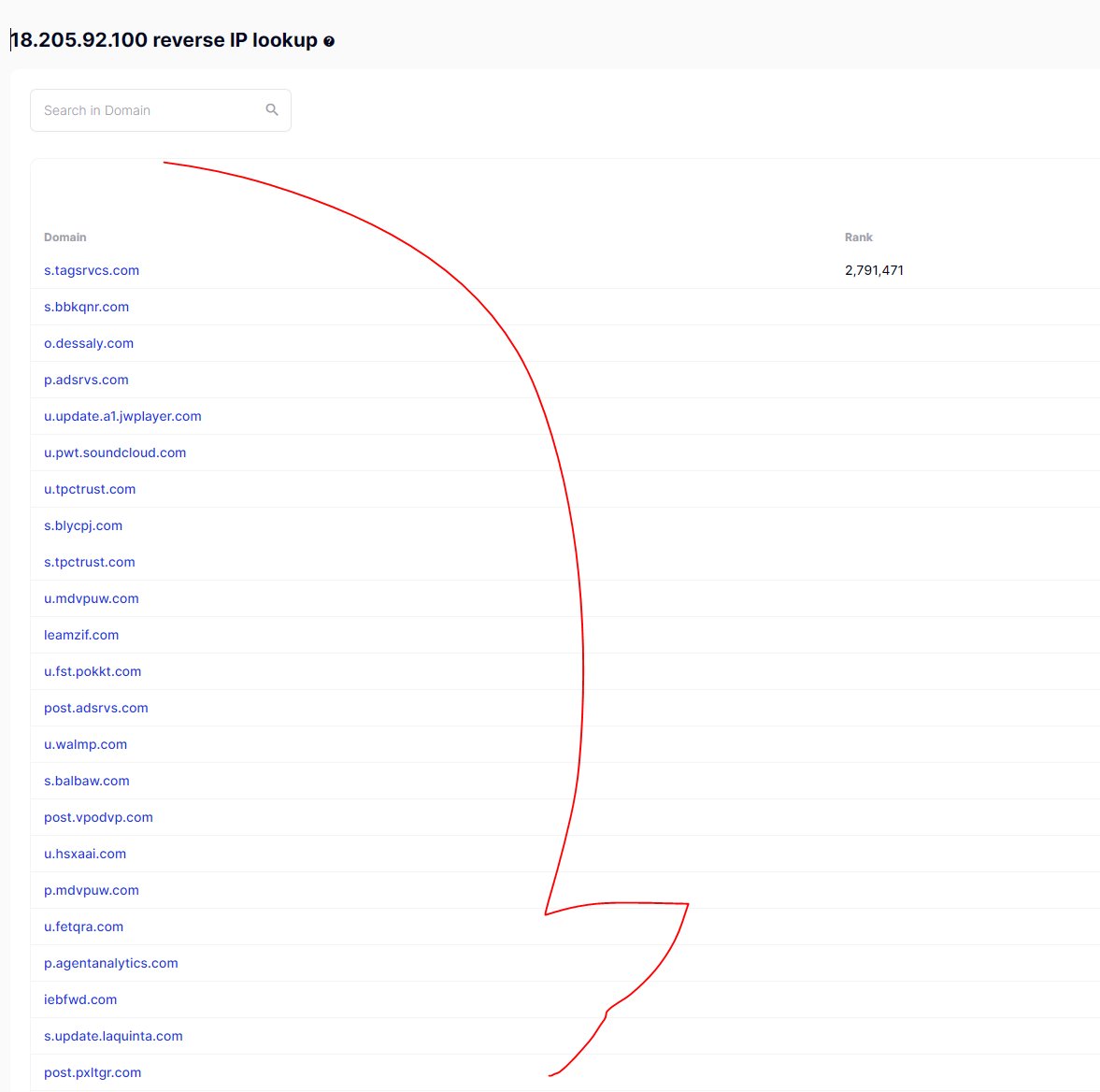
All of these tricks, where huge ad tech co-ops spin up random domains constantly, using "unknown ad tech domains" and fancy DNS tricks / location redirects, to share userIDs across companies, creates huge data co-ops across companies. It works. It's huge business.
And if you load Keytruda in Safari, you can still see how this is happening *(other examples here from MSFT Edge).
The same "medtargetsystem" domain fires in Safari w/ the appnexus reverse proxy domain array ready to push fingerprints & IDs across orgs.
The same "medtargetsystem" domain fires in Safari w/ the appnexus reverse proxy domain array ready to push fingerprints & IDs across orgs.
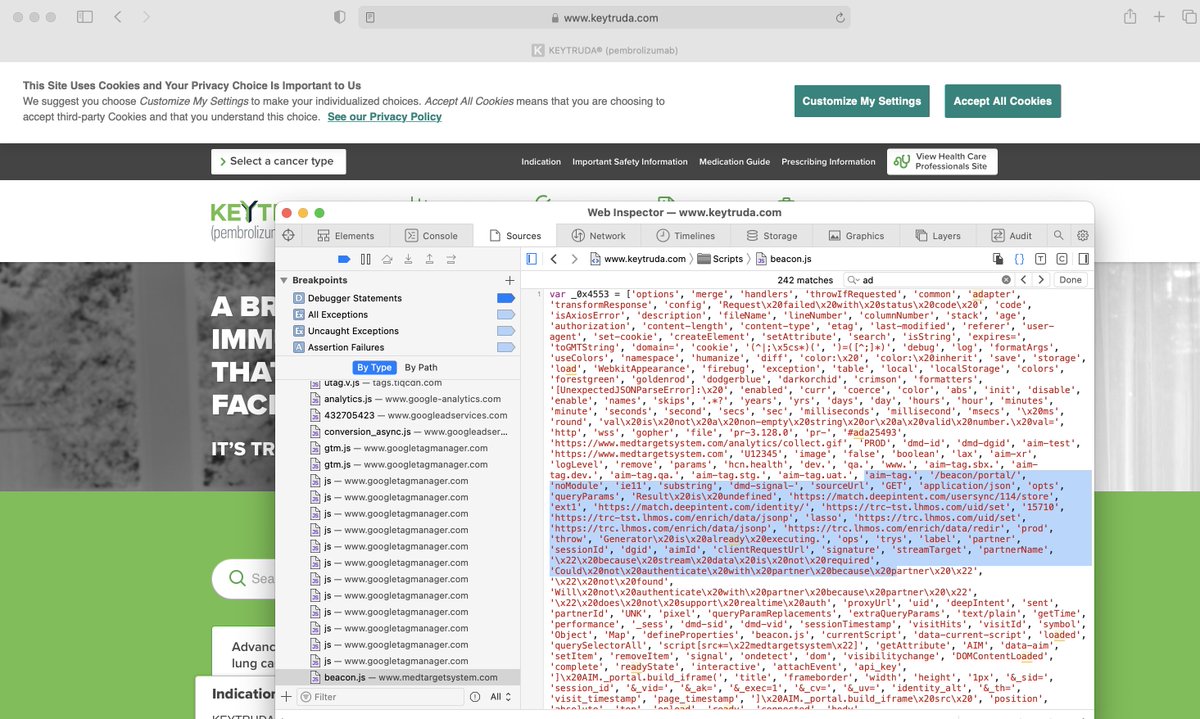
You can see in the Safari syncs how a cookie isn't needed to sync data across a reverse proxy - merely pass the userID in a querystring, have both domains fingerprint the user in the same way, and then you've got a matching fingerprint + join key for future auctions/sharing 
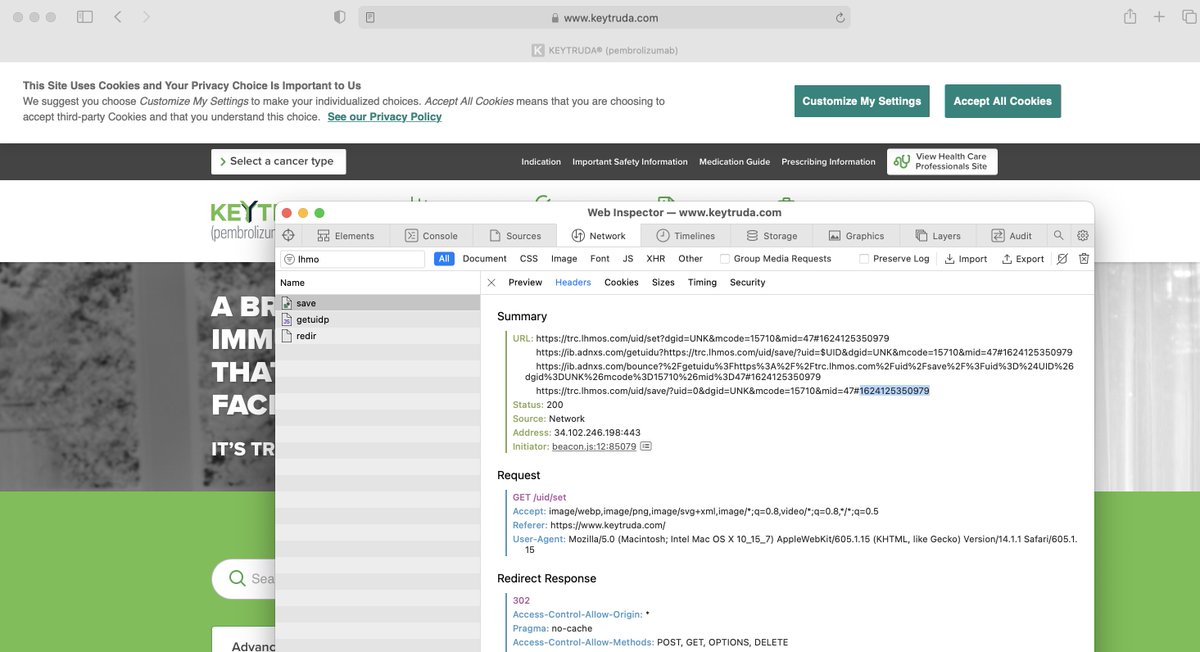
The userID being shared across domains in the Ad ID consortium is also associated with a "liveRampSessionID" dropped in a 1st party context in Safari on "keytruda.)com" - you can see that below. This sync violates the intent of ITP in Safari, should be blocked in the future. 


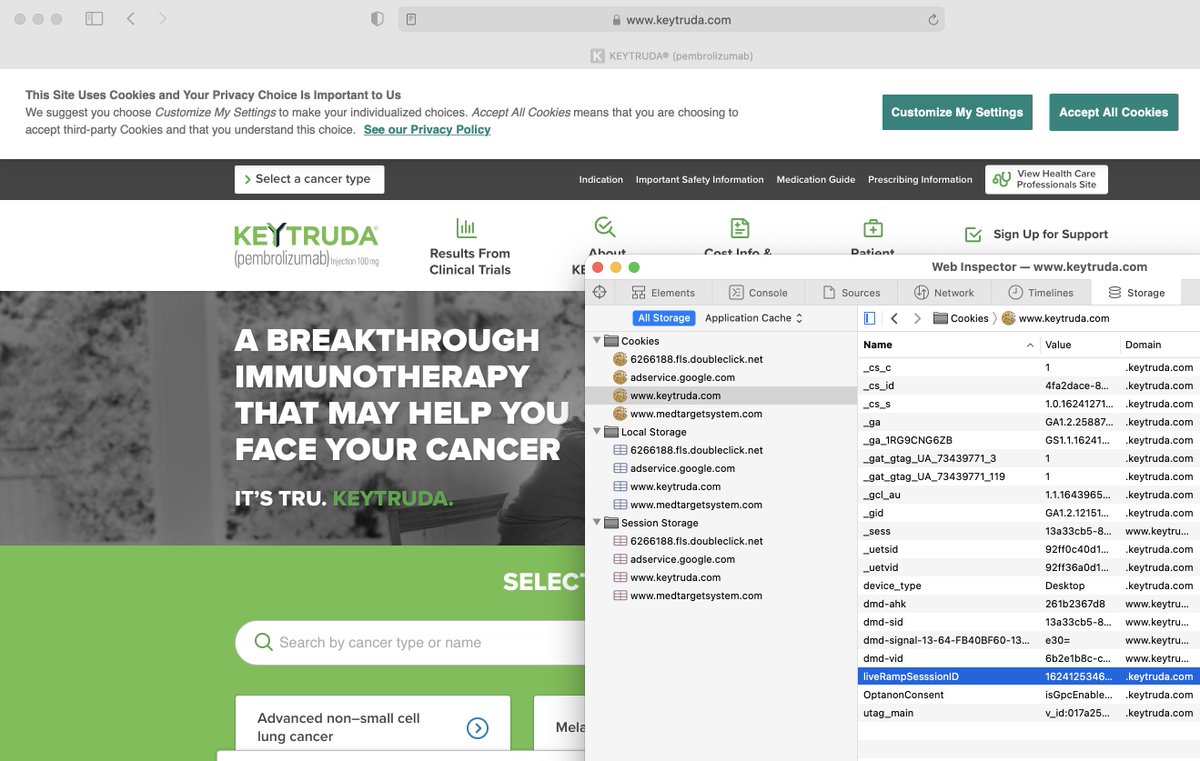
The AD ID Consortium makes the Adobe Data Co-op look quaint, and it was so bad that AT&T said "nahh, that shit is a garbage fire of unethical data flows, we are outta here!" Yet, now here we are.
A C-corp not registered as a data broker is monetizing cancer data on Twitter.
A C-corp not registered as a data broker is monetizing cancer data on Twitter.
There are countless orgs looking for loopholes to current data flow restrictions. This is generally a bad idea. You are creating $$ bubbles & legal exposure for your org. All data supply chains must be mapped -- don't partner with unregistered C-Corp Data Brokers. </🧵>⛈️💸⛈️⚖️
• • •
Missing some Tweet in this thread? You can try to
force a refresh













