1/n
If you are wondering if there will be anybody at Mike Lindell's cybersymposium who can confirm or refute his "packet captures", well, there's going to be me. I'm a well-known expert on packet captures, and somewhat knowledgeable about election systems.
m.washingtontimes.com/news/2021/aug/…
If you are wondering if there will be anybody at Mike Lindell's cybersymposium who can confirm or refute his "packet captures", well, there's going to be me. I'm a well-known expert on packet captures, and somewhat knowledgeable about election systems.
m.washingtontimes.com/news/2021/aug/…
2/
I've done a bunch of other techie fact checking, such as confirming that Hunter Biden email was authentic, and debunking that conspiracy-theory of suspicious DNS logs showing secret communication between Russia's Alfa Bank and Trump Tower.
I've done a bunch of other techie fact checking, such as confirming that Hunter Biden email was authentic, and debunking that conspiracy-theory of suspicious DNS logs showing secret communication between Russia's Alfa Bank and Trump Tower.
3/
I don't know what Lindell's packet captures contain, but whatever it is, I'll write up a description within a few days after the event. I'll be extending this twitter thread over the next couple days just live tweeting the process.
I don't know what Lindell's packet captures contain, but whatever it is, I'll write up a description within a few days after the event. I'll be extending this twitter thread over the next couple days just live tweeting the process.
4/ FYI: nobody is going to win the $5 million. It's impossible to disprove election fraud. It's only possible to demonstrate that claimed evidence fails to prove it.
https://twitter.com/ArtByAlida/status/1424879778323214336
5/ BTW, what kind of expert am I? Well, if you capture packets on the public Internet for more than a few minutes, you'll capture some that I created. Since you've been reading this thread, your home router has gotten hit by my packets.
6/ For those who know me, you might want to pile onto this thread, but only BEFORE I write up my conclusions later this week, before you know what the conclusions will be. Afterwards, it looks insecure, just agreeing with the conclusions you want.
https://twitter.com/0xmchow/status/1424936018202046473
8/ Here’s a pic looking backwards. Btw, I’ll be the guy wearing a mask, because as you know I’m an internet troll and this is the sort of thing I do. 

9/ Before this week, the things Mike Lindell posted were not recognizable as "packet-captures". This is what they normally look like. It's not required to look like this, but it's the level of detail I'll be getting into. 
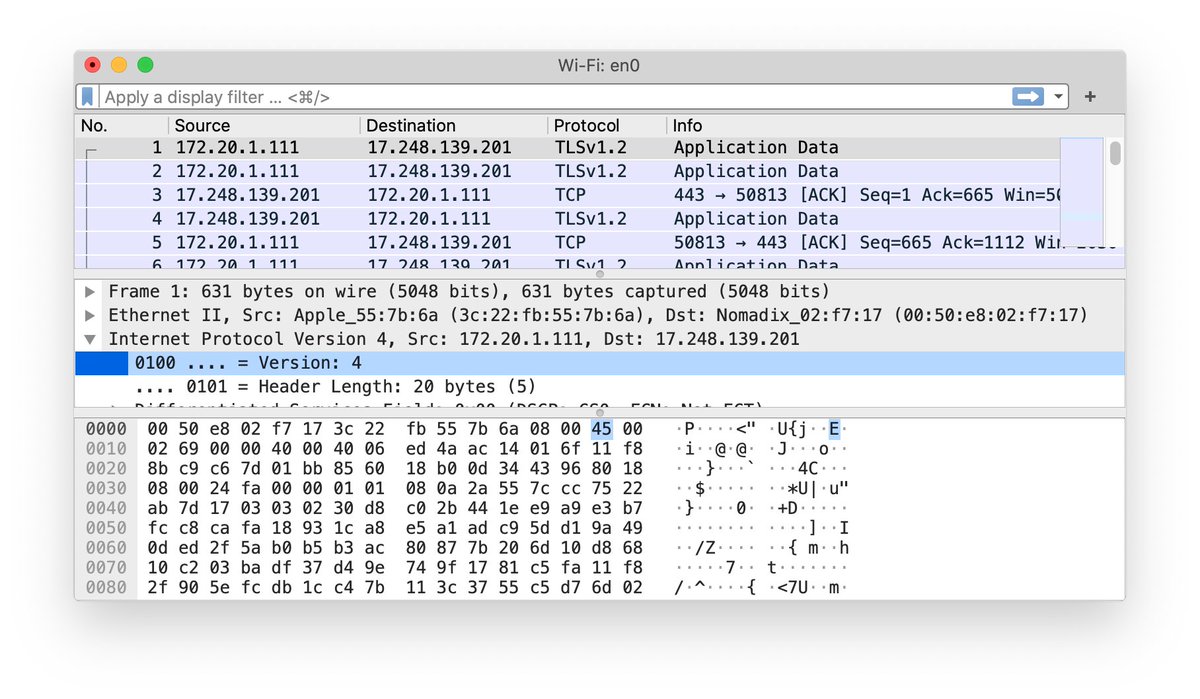
10/ ok, I was wrong about the contest rules. They are much better than I thought: simply proving its not election data. However, the data supplied before this week seems to have been already public registration data and not votes. 

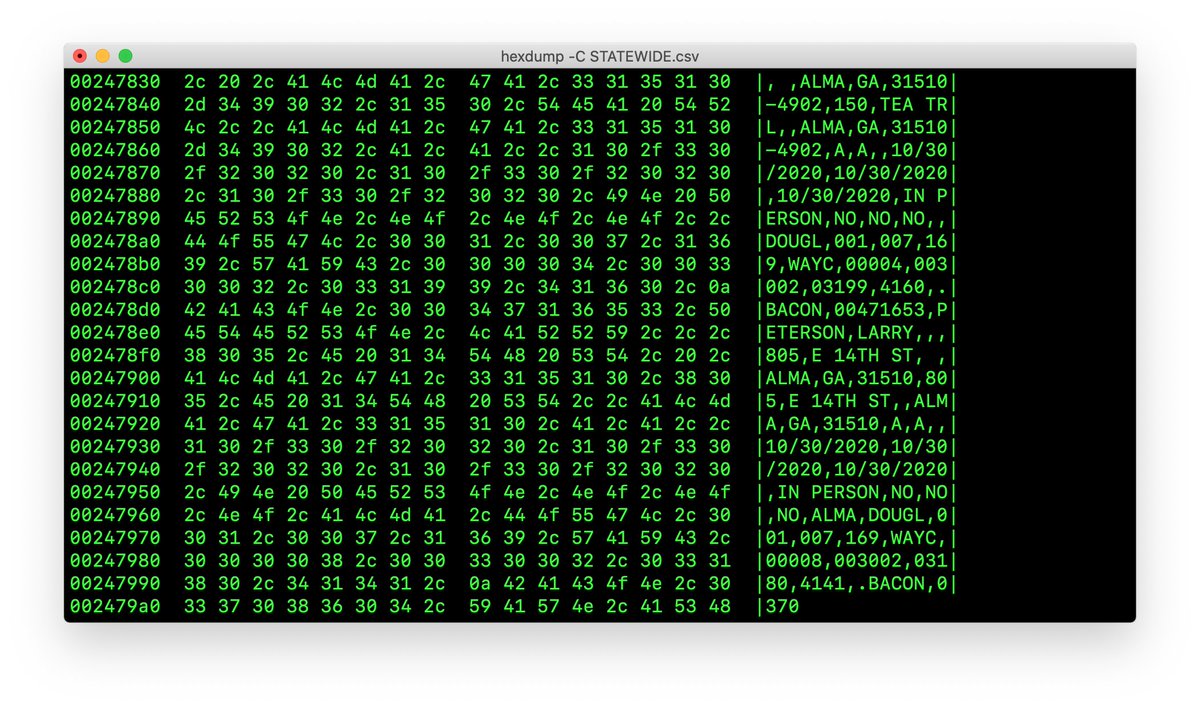
11/ For example, here is data that I got from the State of Georgia, a hexdump of early voting records. It's public, anybody can download it from the net.
So I don't care if it's "election data", I got that already. I'll be looking for hard evidence proving election fraud.
So I don't care if it's "election data", I got that already. I'll be looking for hard evidence proving election fraud.
12/ Everyone is friendly and nice. Which is what I expected. We like to demonize our opponents, but really, they are almost always reasonable, kind hearted people -- even if in our own opinion they are wrong. On both sides.
https://twitter.com/Hogosec/status/1425091607230046214
13/ For a specific list of questions that I'll be trying to answer, I'll start with this, and then have additional questions depending upon the data.
Either way, I'll write things up and EXPLAIN in simple terms what the data shows.
leadstories.com/analysis/2021/…
Either way, I'll write things up and EXPLAIN in simple terms what the data shows.
leadstories.com/analysis/2021/…
14/ I go to a lot of cyber security conferences and have a ton of old badges hanging from the wall in my closet - I’ll just add this one to the pile. 

15/ This is an excellent question. I'm starting on the skeptic side because, so far, he hasn't published any good data. I don't understand why he hasn't simply dumped the raw data for everyone to see.
https://twitter.com/JosephApartmen5/status/1425098686351171587
16/ “I invited the Fakebook fact checkers” — Lindell
Also statements about inviting fake media like CNN. When he mentioned Fox News the crowd booed.
Also statements about inviting fake media like CNN. When he mentioned Fox News the crowd booed.
17/ they have scrolling hexdumps. For one thing they scroll too fast to read, and for another, they are too blurry to read, and lastly, even experts can’t generally read hexdumps without decoders. 



18/ The reason why the question “what’s the source of data” is so important is because we know that media reports of vote tallies where highly inaccurate, the media made lots of accidental mistakes. 



19/ We know the flaws of the NYTime live election night data feed, how it didn't accurately reflect the official counts, why it appeared to show flipped votes and jumps on one side or the other.
The question is whether such things exist in the raw data.
The question is whether such things exist in the raw data.
20/ "they work for LeadStories? fact checkers? shame on them!!! .... they are the enemies of the people"
That's me!!! That's me!!!!
I'm not feeling ashamed, though.
That's me!!! That's me!!!!
I'm not feeling ashamed, though.
21/ "We are going to do a mock election... we'll show you how the routers work ... we'll show packet captures in real time".
I'm actually looking forward to this. Dominion machines can be networked, but DEF CON Voting Village didn't have networked machines to play with.
I'm actually looking forward to this. Dominion machines can be networked, but DEF CON Voting Village didn't have networked machines to play with.
22/ "I saw Hari Hursti is here" (and some criticism of Hari).
He brings voting machines to the DEF CON hacking conference for hackers to play with, confirming they are easily hackable -- but they don't like him because he still rejects the idea that the 2020 election was hacked.
He brings voting machines to the DEF CON hacking conference for hackers to play with, confirming they are easily hackable -- but they don't like him because he still rejects the idea that the 2020 election was hacked.
23/ The evidence that I'm here to validate is showing that it was hacked -- not that it could've been hacked. I know it could've been hacked, by either side. I'm hoping to see the raw details showing it was indeed hacked or manipulated or fraud happened.
24/ Yes, the schedule is for later today, to have breakout sessions, where (I think) I'll get to sit down and personally look at raw data -- and hopefully, get to post to the Internet for experts like Laura Chappell to see as well.
https://twitter.com/LauraChappell/status/1425126573628301312
25/ Phil Waldron kicked off the breakout session. He wasn't involved in collecting the packet-captures, so didn't have clear answers. But he suggested:
1. the packet-captures come from a Chinese network
2. they are in a proprietary BLX/PLX format
But he didn't seem sure.
1. the packet-captures come from a Chinese network
2. they are in a proprietary BLX/PLX format
But he didn't seem sure.
26/ ...but we haven't got the actual data yet, but soon. We are still dealing with lunch.
27/ They've given us access to a server on the local WiFi network that has the "data" that we are supposed to be analyzing.
We are struggling to figure out what this data contains. I've put the smaller files up on github:
github.com/robertdavidgra…
We are struggling to figure out what this data contains. I've put the smaller files up on github:
github.com/robertdavidgra…
28/ So what they gave us were these "HEX.txt" files, which when decoded (`xxd -r -p filename`) produces .rtf files. One of the RTF files contains a table of IP address, the others contain something in an unknown character set.
29/ Here's the current status: nothing.
They've given us a drop of data that makes no sense that they can't explain.
They promise: just wait until later tonight, that's the "real" data.
They've given us a drop of data that makes no sense that they can't explain.
They promise: just wait until later tonight, that's the "real" data.
30/ I mean: they've given us a bunch of confusing stuff they can't explain, but have not given us the "real" stuff yet. They promise the "real" stuff is coming tonight or tomorrow for us to look at.
31/ The delay is explained by a bunch of things going wrong, such as the guy who was a source of data getting a stroke.
https://twitter.com/DenisRno/status/1425181697612603399
32/ So I had the list of questions I sought to answer this morning at the top of this thread. Current progress = 0%
33/ This is incredibly frustrating. Lindell invited "cyber experts" and "fact checkers" to come and confirm the "packet captures" -- and has yet to provide us any packet captures and it's 4pm already. #ReleaseThePacketCaptures
34/ So I got some straight answers from Spider:
1. the data comes from Dennis Montgomery
2. it's the data shown in those Lindell videos
3. it's the hexdumps that have been scrolling in his videos and kiosk
4. we cyber experts will not be given opportunity to verify it
1. the data comes from Dennis Montgomery
2. it's the data shown in those Lindell videos
3. it's the hexdumps that have been scrolling in his videos and kiosk
4. we cyber experts will not be given opportunity to verify it

35/ Please don't interpret that as being disproven. This would be the WRONG conclusion. Instead, it means it's simply not confirmed. Montgomery is in the hospital and unable to come, and unable to help us, because it's in a proprietary format.
36/ The vague answers to this question is that it was retrieved with custom tools on the China side of things, as they targeted election systems via the Internet, not collected on the side of the election systems.
https://twitter.com/jojo2020/status/1425217903452884992
37/ For all that Mike Lindell attacks critics, do remember that he invited critics to come to the event, which is something I respect. On the other hand, failure to give the critics the data they were promised, well, I'm frustrated by that. I'm a pcap guy who loves pcaps.
38/ Later they will be showing pcaps from Mike Lindell's own people, that are here, that will stand behind them and explain them. I look forward to reading them.
https://twitter.com/TheDublinDon/status/1425223838187524100
39/ Wait, what? I'll come on stage and defend my findings. It's just that we techies are sitting in breakout rooms in the back and I wasn't aware of the live feed. I'm out front now. Let's go!
https://twitter.com/RayRedacted/status/1425221061264691201
40/ Sigh. I'm here near the stage, ready to stand up and defend my claims in this thread. Just call me up on stage and let's talk. #ReleaseThePacketCaptures
41/ Many are suggesting I bum rush the stage.
Can't. They have muscled security goons that would stop me.
And it would be rude. He's doing a bit, I don't want to interrupt, I'm sure he'll invite me after.
#ReleaseThePacketCaptures
Can't. They have muscled security goons that would stop me.
And it would be rude. He's doing a bit, I don't want to interrupt, I'm sure he'll invite me after.
#ReleaseThePacketCaptures
41/ By the way, this is the data they are NOT giving us, they are not allowing pcap experts to analyze this data. Showing it as a video stream like this is unreadable.
https://twitter.com/rx13/status/1425235019384033280
41/ Ah, man, he ended the segment and didn't invite me on stage like he'd promise. He's setting up for the "big reveal" at 7pm, which I think is member of Bolsinaro's team, the current president of Brazil who's claiming that the upcoming election is going to be hacked.
43/ Come on, Mike, you challenged me to come on stage to debate why you haven't released the packet-captures you promised. Let's do this thing! I'm around all three days! I'm ready any time, just have one of your people DM me!
I'll go back to the breakout room now.
I'll go back to the breakout room now.
44/ BTW, the source of the "packet-captures" is important, because it appears to be this "Dennis Montgomery" guy, as LeadStories describes:
leadstories.com/analysis/2021/…
leadstories.com/analysis/2021/…
45/ the picture from this morning was empty of people because I arrived early. There are at a couple hundred people here. 

46/ The guy speaking on stage mentioned the packet-captures they got Jan 7, and they mentioned that while it was hard over the weekend getting them ready, that they got them ready.
BUT THEY HAVEN'T RELEASED THE PACKET-CAPTURES TO US
#ReleaseThePacketCaptures
BUT THEY HAVEN'T RELEASED THE PACKET-CAPTURES TO US
#ReleaseThePacketCaptures
49/ he called me a coward claiming I ran away — I’ve been sitting here in front the entire time waiting for him to call me onstage to discuss the packet captures
50/ I'm done for the day (Tuesday). I go back tomorrow.
One guy already got kicked for sharing too much, so I guess I won't be able to share much until Thursday -- general conference related things, yes, but data related things, not until after the conference.
One guy already got kicked for sharing too much, so I guess I won't be able to share much until Thursday -- general conference related things, yes, but data related things, not until after the conference.
51/ To be clear: he gave us experts NOTHING today, except random garbage that wastes our time (e.g. a CSV needlessly encoded as RTF needlessly encoded as hex).
https://twitter.com/lgbtciabossbabe/status/1425262180501426180
52/ Also be clear: all the people I've been dealing with are good people, trying to do their best in a chaotic and difficult situation. The only thing lacking for me is the one thing I'm here for: the packet captures promised before the conference.
54/ So I had a bunch of private conversations last night where people helped clarify things. One thing they mentioned was that there's confusion about "hex", that they think we techies like to see things in hex, so that's why it was given to us this way.
55/ the Matrix does much to foster the impression that nerds prefer to see things that way — that it’s cool.
We don’t — we hate hex, it’s just sometimes it’s the only alternative.
We don’t — we hate hex, it’s just sometimes it’s the only alternative.

56/ F***! That last tweet came out wrong, so I deleted.
Last night talking privately to friends, they stressed to me how it important it was that I'm just an observer, and that participation in things like pledges/prayer would be counter to my mission.
Last night talking privately to friends, they stressed to me how it important it was that I'm just an observer, and that participation in things like pledges/prayer would be counter to my mission.
https://twitter.com/mubix/status/1425462480537587712
57/ So CodeMonkeyZ presenting Dominion source code. That looks like a lot of fun -- by fun, I mean, a lot of people are going to just wig out on the fact he's the 8chan guy. 

56a/ All day Mike Lindell has been on stage saying the cyber experts are happily working on packet captures.
We are not. We haven't been given the packet captures we were promised.
We are not. We haven't been given the packet captures we were promised.
56b/ I mentioned this because some of his PR guys came by looking to take video of cyber experts working on packet captures. They seem confused by the fact that theres no cyber experts who have seen the promised packet captures.
56c/ I mean, I can turn on Wireshark, capture some new packets right now, and show me working on them, but that's not quite the same thing. It's a pcap, not the pcap. 

57/ To be fair, the "cyber experts" are indeed working on NEW data, like the system images shown on stage. So they are working.
It's just that no "cyber expert" at the conference is working on the OLD pcaps or proof from his Absolute Proof video.
It's just that no "cyber expert" at the conference is working on the OLD pcaps or proof from his Absolute Proof video.
60+/ I forked this thread, because I'm stupid. Here's the other branch:
https://twitter.com/ErrataRob/status/1425472300015517701
61/ Well, this is confirmation of this thread, we haven't gotten the Absolute Proof packet captures, and it's likely we won't.
Note: the guy quoted, Joshua, has been straight forward with us this entire, I'm impressed by his integrity
https://twitter.com/sboger/status/1425614795940585475
Note: the guy quoted, Joshua, has been straight forward with us this entire, I'm impressed by his integrity
62/ So the day has ended. Got to play with a bunch of new election data, like system images of election management machines, which I've been curious about.
But sadly, no packet captures.
But sadly, no packet captures.
63/ Good morning twitters for the third and last day (Thursday) of Mike Lindell’s Cybersymposium. Cyber expert here, hoping to get my hands on the cyber pcaps containing Absolute Proof. 

64/ people ask me how the food is — it’s good solid three square meals a day, nothing fancy, but I’d say above average for such things 

65/ This "poison pill" thing pass by so fast that I didn't quite catch what it meant. Was it about these new pieces of evidence since the start of the symposium? Or is it why they can't give us the old pcaps that were promised?
66/ FYI: if there are Antifa agitators here, I haven't seen anything like that. The outside is empty of anybody that isn't part of the conference.
https://twitter.com/rattanwarrior/status/1425871444026683392
67/ Sadly, at the last minute, I chickened out and didn't wear my Wall of Sheep (@wallofsheep) T-shirt (nobody else is wearing T-shirts, it's a very suits-and-tie affair).
Because having login packets in a capture file is not a "poison pill".
Because having login packets in a capture file is not a "poison pill".
68/ If we receive packet captures with embedded captured logins, no, we are not committing a crime and trafficking in passwords. I mean, contact your lawyer, but I do so on the time, including live on stage at DEF CON.
69/ @kjhiggins is still annoyed with me for having captured and displayed her password on stage at a conference. Indeed, I've been caught by @hdmoore doing the same to me (very embarassing), displaying my password.
70/ I'm here to make jokes and take evidence. I'm long past caring about those who'll deliberately take jokes out of context. Someone willingly misreading jokes condemns themselves.
https://twitter.com/vikphatak/status/1425879347676786691
71/ Main conference still seems full, but cyber-experts have been slowly leaving, having flights to catch. I've got about 3 more hours, then gotta run to catch my flight.
72/ So they had one of the "cyber experts" go on stage and describe the conclusion of the group. I didn't hear precisely what was said, but my conclusion is simply: we didn't get the Absolute Proof packet captures that show the flipped votes that Mike Lindell promised.
73/ Maybe these packet captures will appear in the future. Then I'll take a look. But of course, I'm not spending another $1000 to look at them -- I'll just download them from the Internet.
74/ If this is the message you heard, "we need more time", then that's wrong.
The issue is we weren't given the data promised, it's not about time.
The issue is we weren't given the data promised, it's not about time.
https://twitter.com/WatchAllTheTV/status/1425897053624758274
75/ Instead of giving us the data we were promised, the Absolute Proof of votes being flipped, Lindell dumped a bunch of new data on us, like Mesa county disk images they got yesterday. Yes, of course, that needs a lot time to search for things and analyze.
76/ But he didn't ask us here to do forensics/analysis on NEW data to find possible new evidence (which takes time) -- he invited us here to confirm the analysis that he claimed to have already performed on OLD data (which doesn't take much time).
77/ The initial analysis takes time, it's a lot of effort searching haystacks for needles. But once you find a needle, it doesn't take much time at all to confirm you've found one. Had we been given the packet captures, we could've confirmed it in a day.
79/
Final verdict of this "cyber expert":
Number of "packet captures" or "cyber pcaps" seen = 0
Amount of "Absolute Proof" seen = 0
Amount of any evidence seen = 0
Final verdict of this "cyber expert":
Number of "packet captures" or "cyber pcaps" seen = 0
Amount of "Absolute Proof" seen = 0
Amount of any evidence seen = 0
80/ Some comments on the last tweet claim that while there were no packet-captures, that they saw other pieces of evidence presented on stage. If I missed something, please correct me and point to the specific thing that I missed.
81/ Well, yes, technically, packet captures were seen. If you scroll up in my thread, you'll see some packet captures I created during the symposium.
I was clearer in the other tweets: none of the packet captures THAT WE WERE PROMISED
I was clearer in the other tweets: none of the packet captures THAT WE WERE PROMISED
https://twitter.com/GailGolec/status/1425932515508776960
82/ They did give us some additional packet captures, captured after the election, which don't seem to be related to elections at all. So yes, "pcaps" but not the election pcaps showing vote flipping that we were promised.
83/ As for "intentional weakening of security", it's meaningless. It's what we call "conspiracy theories" where you go searching through something you don't understand looking for suspicious looking things that confirm your theory. 

84/ I know how that image looks suspicious. But it's your job to create a coherent story about how this suspicious looking thing is actually malicious, not a techy's job to explain how registries, SQL, SSL, and voting machines work.
85/ If something is evidence, explain what the evidence means. Start with "I understand exactly what's going on here and here's how it's evidence", not "I don't understand what's going on and my only explanation is the theory".
86/ Remember that's what we are trying to sift through: a world of things we don't understand that look suspicious as hell, and the world of things that we do understand that we can pin down exactly what happened.
87/ it’s wrong to describe Lindells followers as gullible or other insults. Only half were impervious to the fact he didn’t deliver, another half were upset and felt it was a problem.
88/ it’s the worst half you see on Twitter, arguing their case, but they aren’t the entirety
• • •
Missing some Tweet in this thread? You can try to
force a refresh









