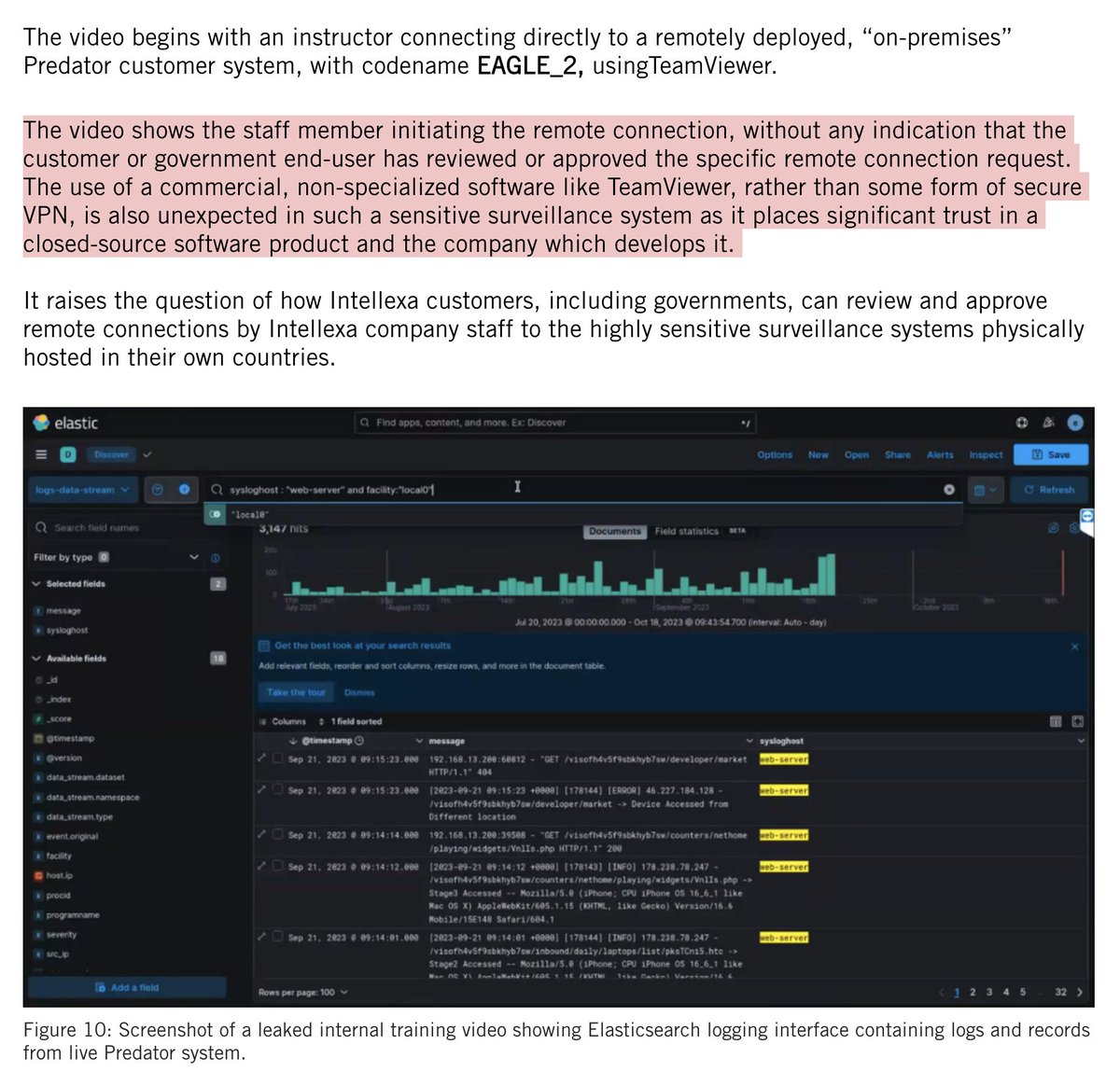
🚨 UPDATE YOUR APPLE DEVICES NOW🚨
We caught a zero-click, zero day iMessage exploit used by NSO Group's #Pegasus spyware.
Target? Saudi activist.
We reported the #FORCEDENTRY exploit to @Apple, which just pushed an emergency update.
THREAD 1/
citizenlab.ca/2021/09/forced…
We caught a zero-click, zero day iMessage exploit used by NSO Group's #Pegasus spyware.
Target? Saudi activist.
We reported the #FORCEDENTRY exploit to @Apple, which just pushed an emergency update.
THREAD 1/
citizenlab.ca/2021/09/forced…

2/ Here's the story of the #FORCEDENTRY exploit:
Back in Mach my colleague @billmarczak was examining the phone of a Saudi activist infected w/#Pegasus spyware. Bill did a backup at the time.
A recent a re-analysis yielded something interesting: weird looking ".gif" files.
Back in Mach my colleague @billmarczak was examining the phone of a Saudi activist infected w/#Pegasus spyware. Bill did a backup at the time.
A recent a re-analysis yielded something interesting: weird looking ".gif" files.
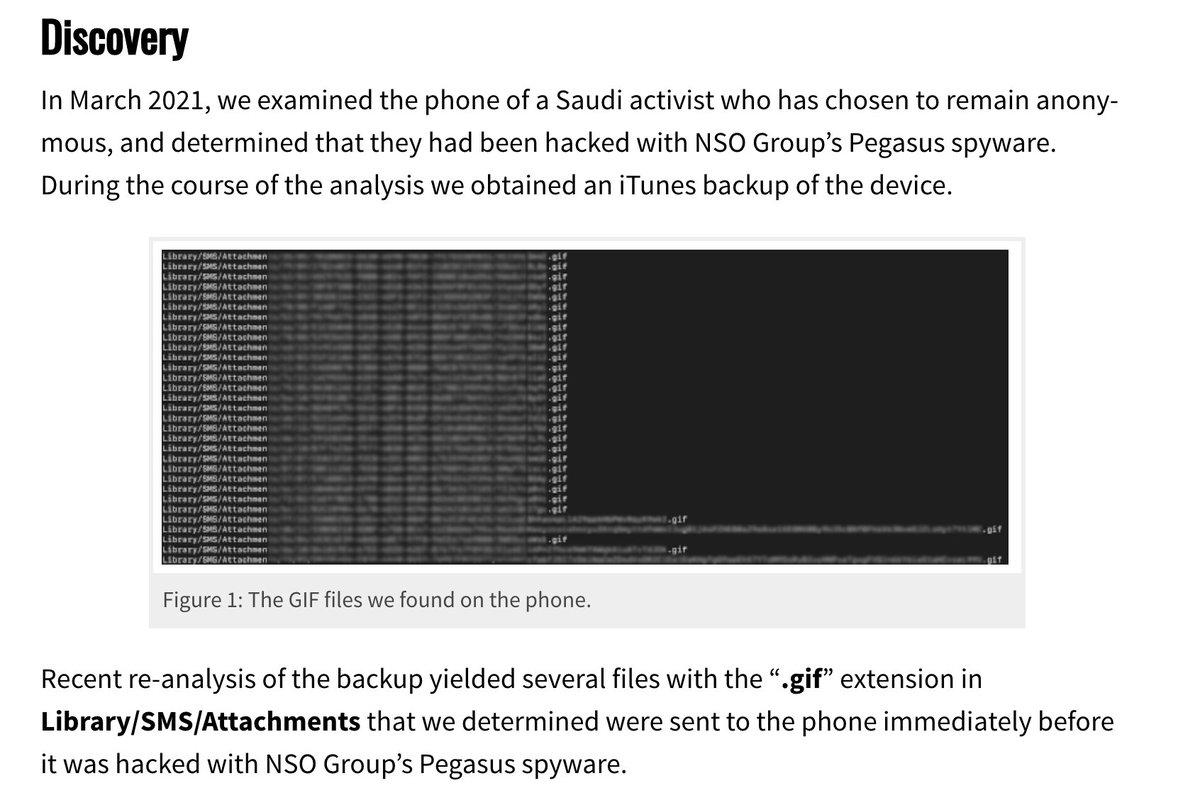
3/ Thing is, the ".gif" files...were actually Adobe PSD & PDF files...and exploited Apple’s image rendering library.
Result? Silent exploit via iMessage.
Victim sees *nothing,* meanwhile #Pegasus is silently installed & their device becomes a spy in their pocket.

Result? Silent exploit via iMessage.
Victim sees *nothing,* meanwhile #Pegasus is silently installed & their device becomes a spy in their pocket.


4/ NSO Group says that their spyware is only for targeting criminals & terrorists.
But here we are... again: their exploits got discovered by us because they were used against an activist.
Thesis: discovery is inevitable byproduct of selling spyware to reckless despots.
But here we are... again: their exploits got discovered by us because they were used against an activist.
Thesis: discovery is inevitable byproduct of selling spyware to reckless despots.

5/ #FORCEDENTRY exploit bigger picture:
Popular chat apps are the soft underbelly of device security.
They are on every device, & some have a needlessly large attack surface.
Their security needs to be a *top* priority.
Popular chat apps are the soft underbelly of device security.
They are on every device, & some have a needlessly large attack surface.
Their security needs to be a *top* priority.

6/Less than a week from notification to patching #FORCEDENTRY.
@Apple can move fast. Great stuff. Herculean effort by teams there.
Company is obviously fed up with NSO & the mercenary spyware industry. Like Google, Facebook, and the rest of the legit tech industry.
@Apple can move fast. Great stuff. Herculean effort by teams there.
Company is obviously fed up with NSO & the mercenary spyware industry. Like Google, Facebook, and the rest of the legit tech industry.
• • •
Missing some Tweet in this thread? You can try to
force a refresh