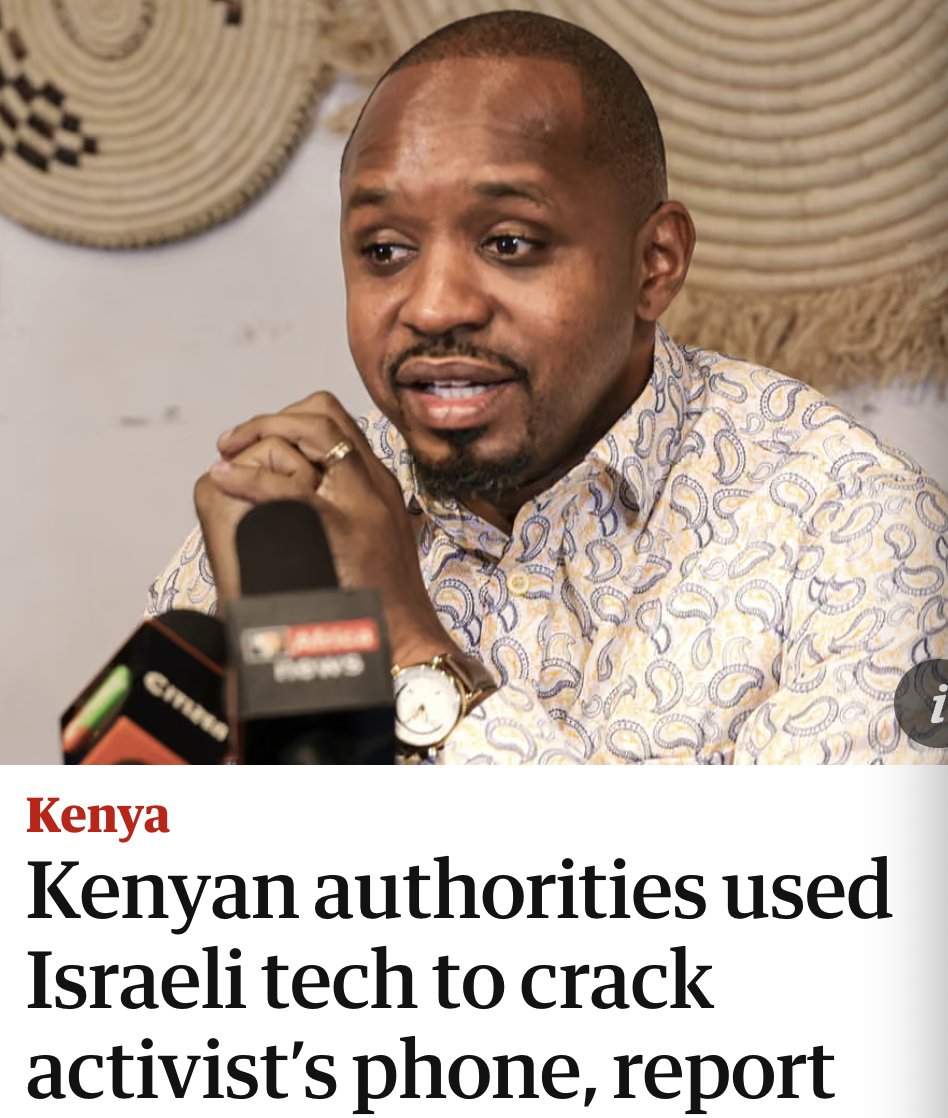
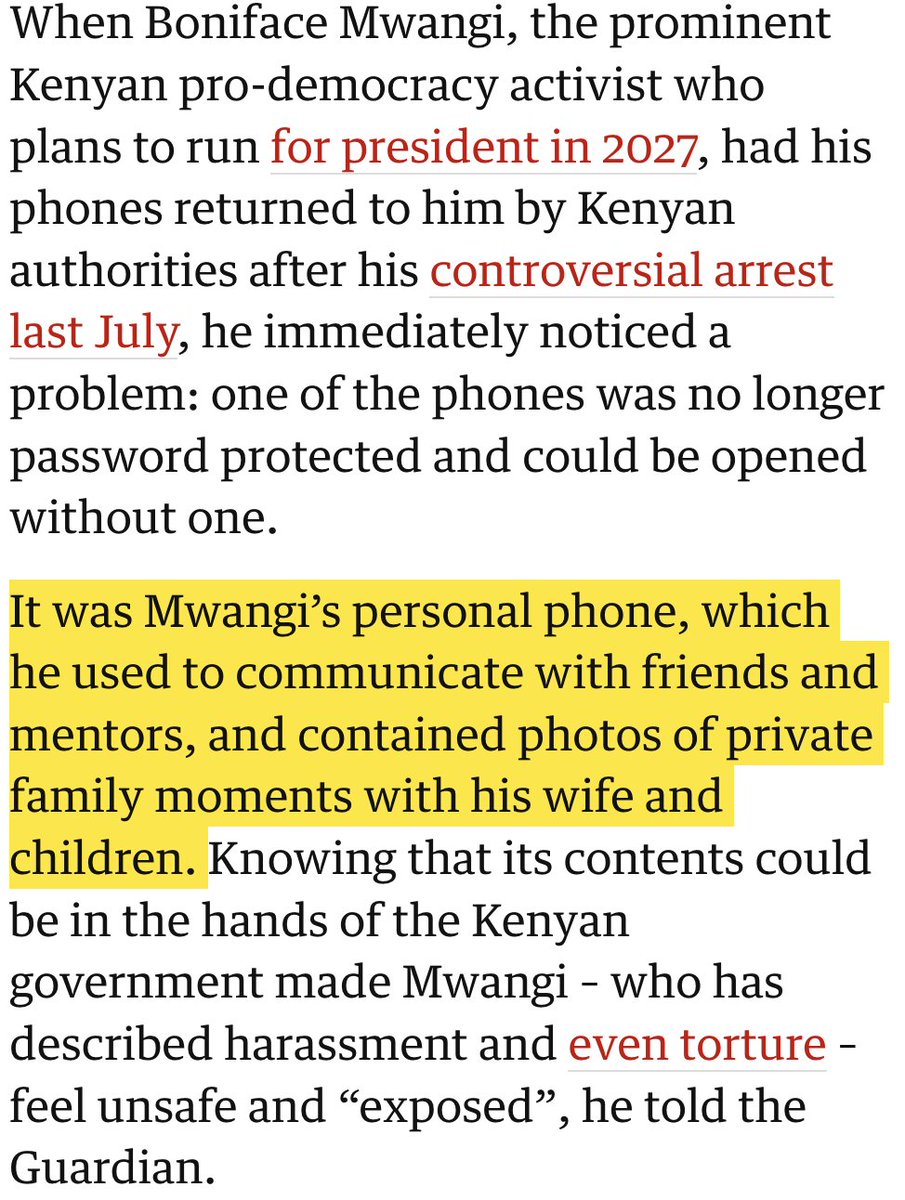
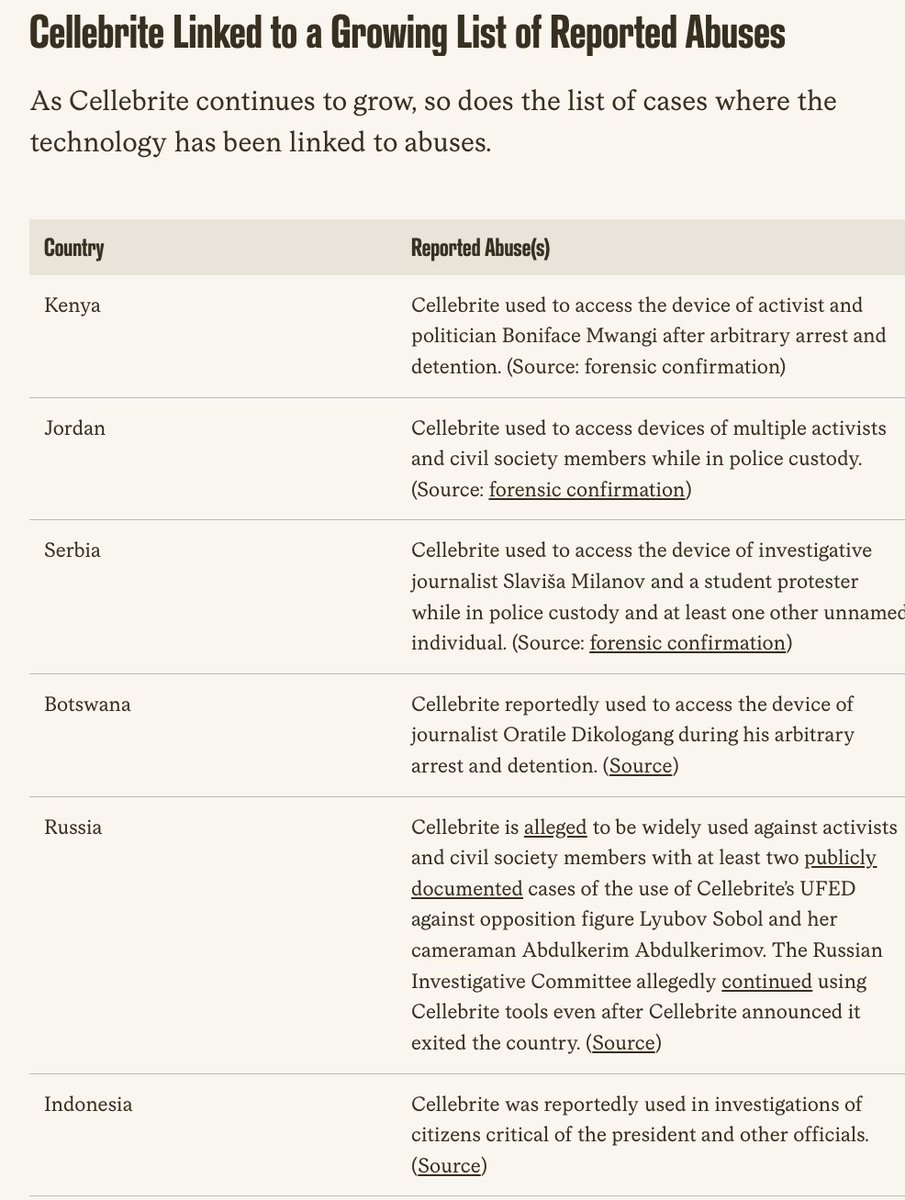
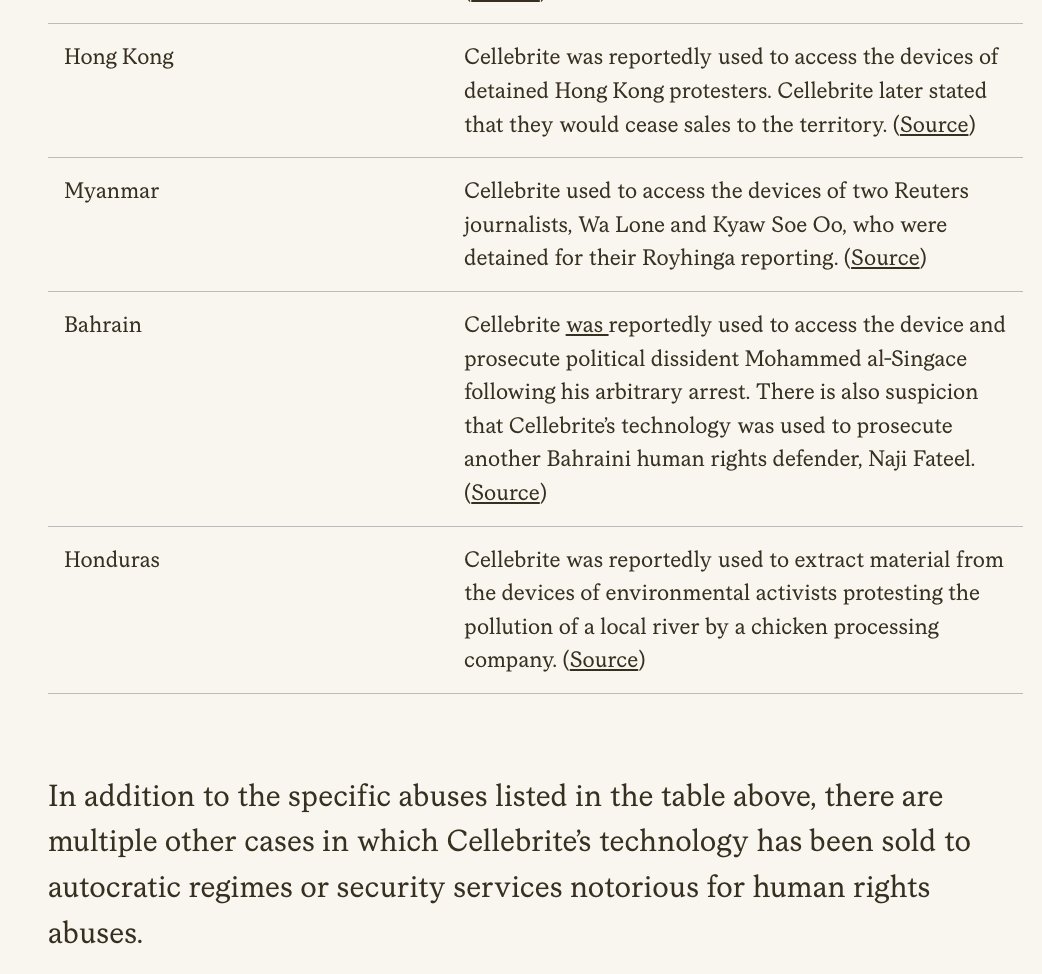
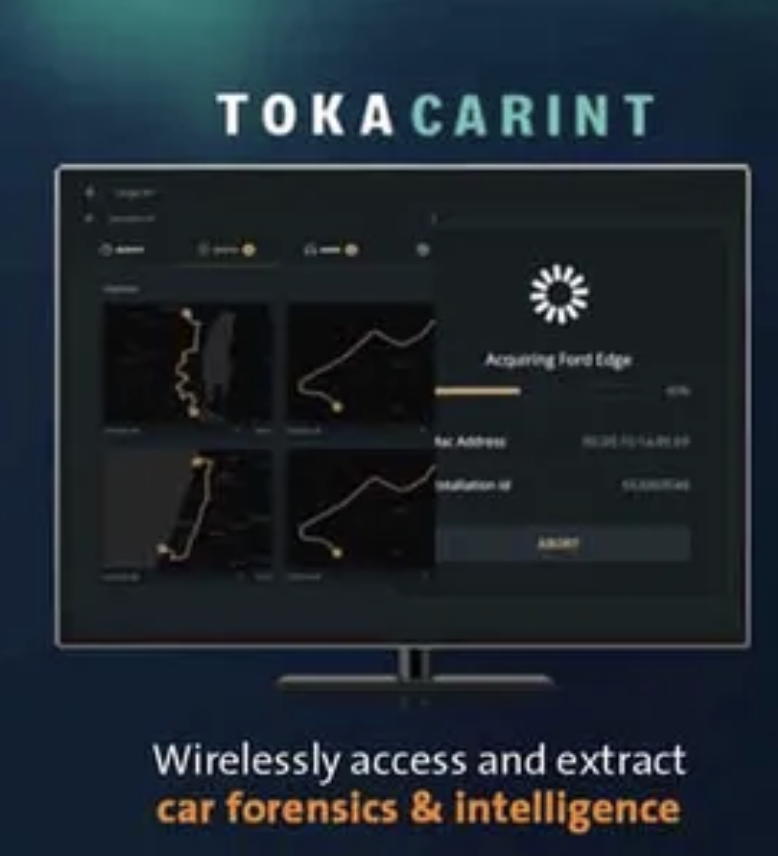
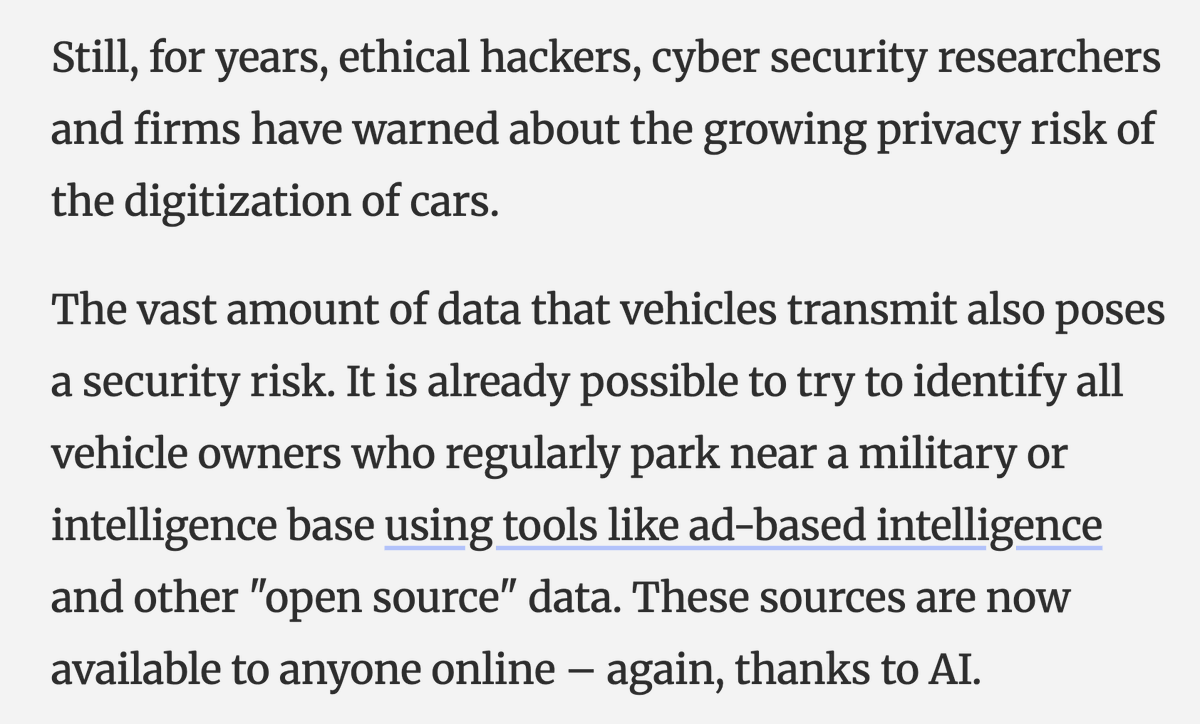
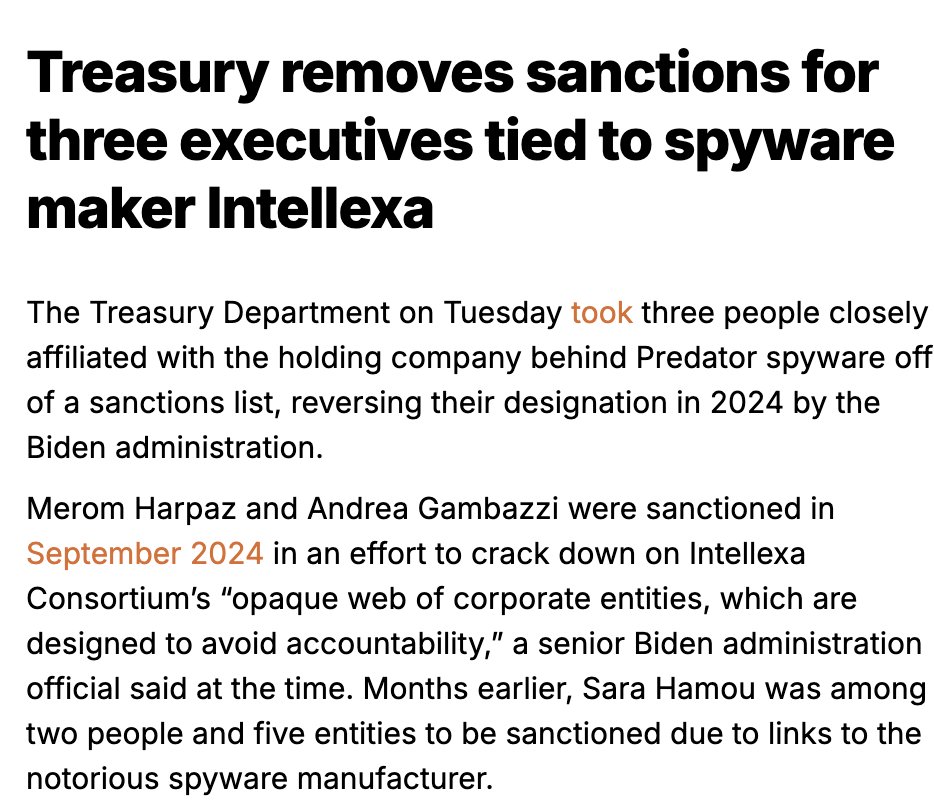
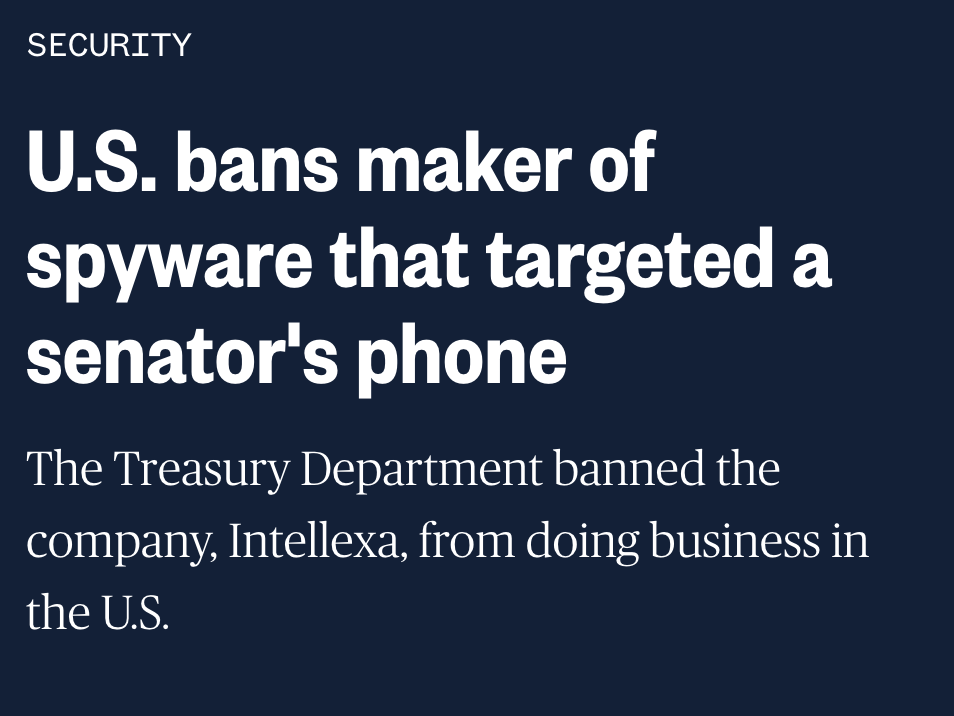
BREAKING NOW: @Apple just filed a major lawsuit against NSO Group.
Apple also notifying some recent targets.
Massive blow to the company notorious for selling spyware to dictators.
And there's more... Explainer THREAD. 1/
apple.com/newsroom/2021/…
Apple also notifying some recent targets.
Massive blow to the company notorious for selling spyware to dictators.
And there's more... Explainer THREAD. 1/
apple.com/newsroom/2021/…

2/ Apple's lawsuit, filed moments ago in Northern California hits NSO hard.
- Seeks to hold NSO & parent accountable for abuses
- ALSO Requests permanent injunction banning NSO from using Apple products.
Directly hits NSO's core development & biz activities.
- Seeks to hold NSO & parent accountable for abuses
- ALSO Requests permanent injunction banning NSO from using Apple products.
Directly hits NSO's core development & biz activities.

3/ NSO poked the hornet's nest for years, and @Apple wasn't satisfied with simply suing the spyware company..
Apple just pledged millions to groups working cyber surveillance... plus any damages that they extract from NSO.
Apple's wrath is poetic.
Apple just pledged millions to groups working cyber surveillance... plus any damages that they extract from NSO.
Apple's wrath is poetic.

4/ Notifying NSO victims is another major step.
After @WhatsApp, Apple is the 2nd major company to do so.
✅Helps victims recognize what's going on
✅puts NSO's government customer base on notice: their abuses might be exposed next.
After @WhatsApp, Apple is the 2nd major company to do so.
✅Helps victims recognize what's going on
✅puts NSO's government customer base on notice: their abuses might be exposed next.

5/ NSO's accelerating tailspin, current status...
In recent weeks:
✅US🇺🇸 sanctioned NSO
✅ Court ruled that @WhatsApp's lawsuit against them could go ahead
✅ Reports that NSO is headed towards possible default.
Now, a massive lawsuit from Apple.
In recent weeks:
✅US🇺🇸 sanctioned NSO
✅ Court ruled that @WhatsApp's lawsuit against them could go ahead
✅ Reports that NSO is headed towards possible default.
Now, a massive lawsuit from Apple.
6/ NSO's profitable spyware is predictably used for repression by many dictators.
This didn't scare off unscrupulous investors.
Other spyware companies are now chasing their lead..
Now, NSO's *crisis* sends a different signal: your fortunes could come crashing down.
This didn't scare off unscrupulous investors.
Other spyware companies are now chasing their lead..
Now, NSO's *crisis* sends a different signal: your fortunes could come crashing down.
7/ NSO's spyware doesn't just harm human rights.
It hurts tech companies.
After years of spending efforts on technical means of control (e.g. patching & securing their products), big platforms have decided it was time to punch back in a different way:
In court.
It hurts tech companies.
After years of spending efforts on technical means of control (e.g. patching & securing their products), big platforms have decided it was time to punch back in a different way:
In court.

8/ I see @Apple's lawsuit as partly triggered by findings & efforts of so many of our @citizenlab peers:
E.g. @AmnestyTech @accessnow @RSF_inter @EFF @pressfreedom @R3Dmx @article19org & many more.
Most importantly though: the victims that bravely came forwards. Here's why...
E.g. @AmnestyTech @accessnow @RSF_inter @EFF @pressfreedom @R3Dmx @article19org & many more.
Most importantly though: the victims that bravely came forwards. Here's why...
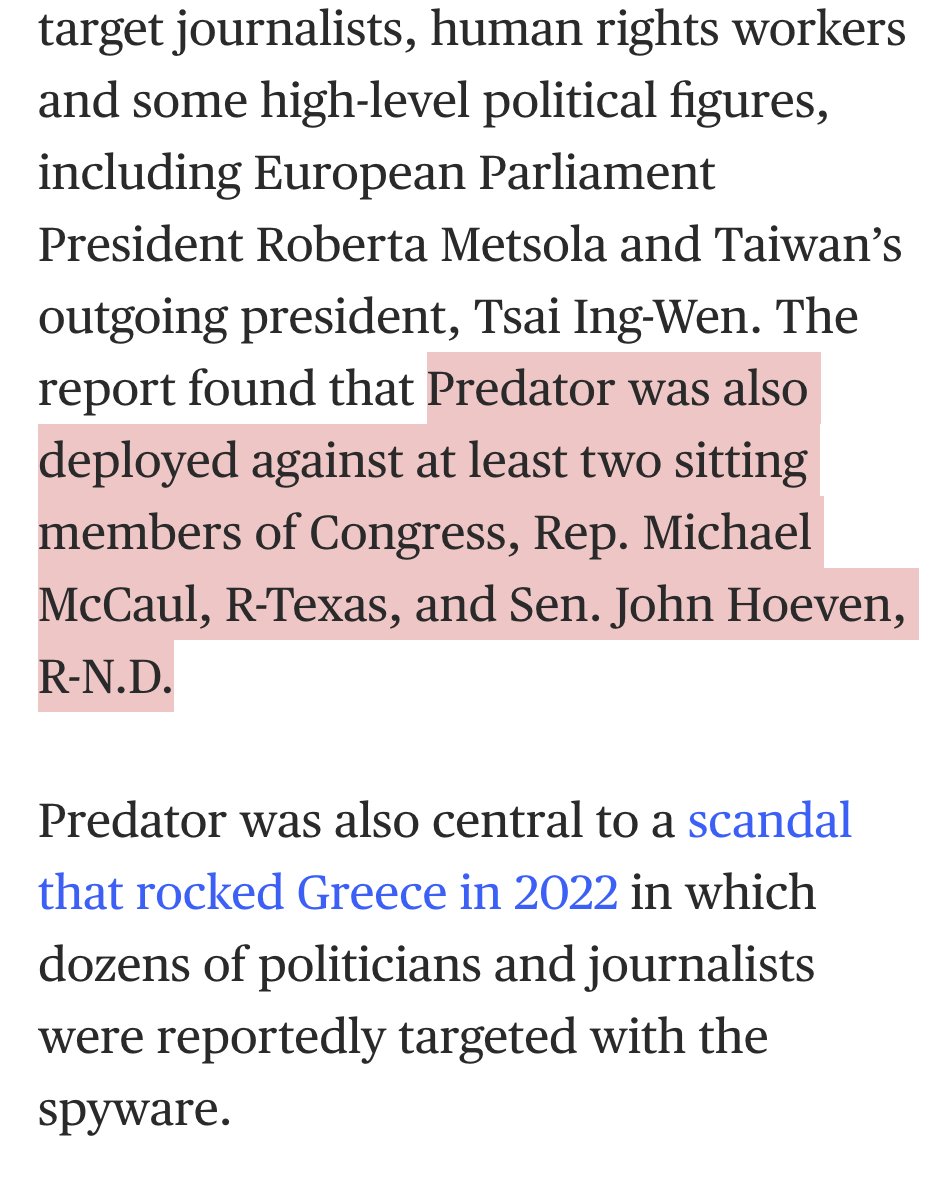
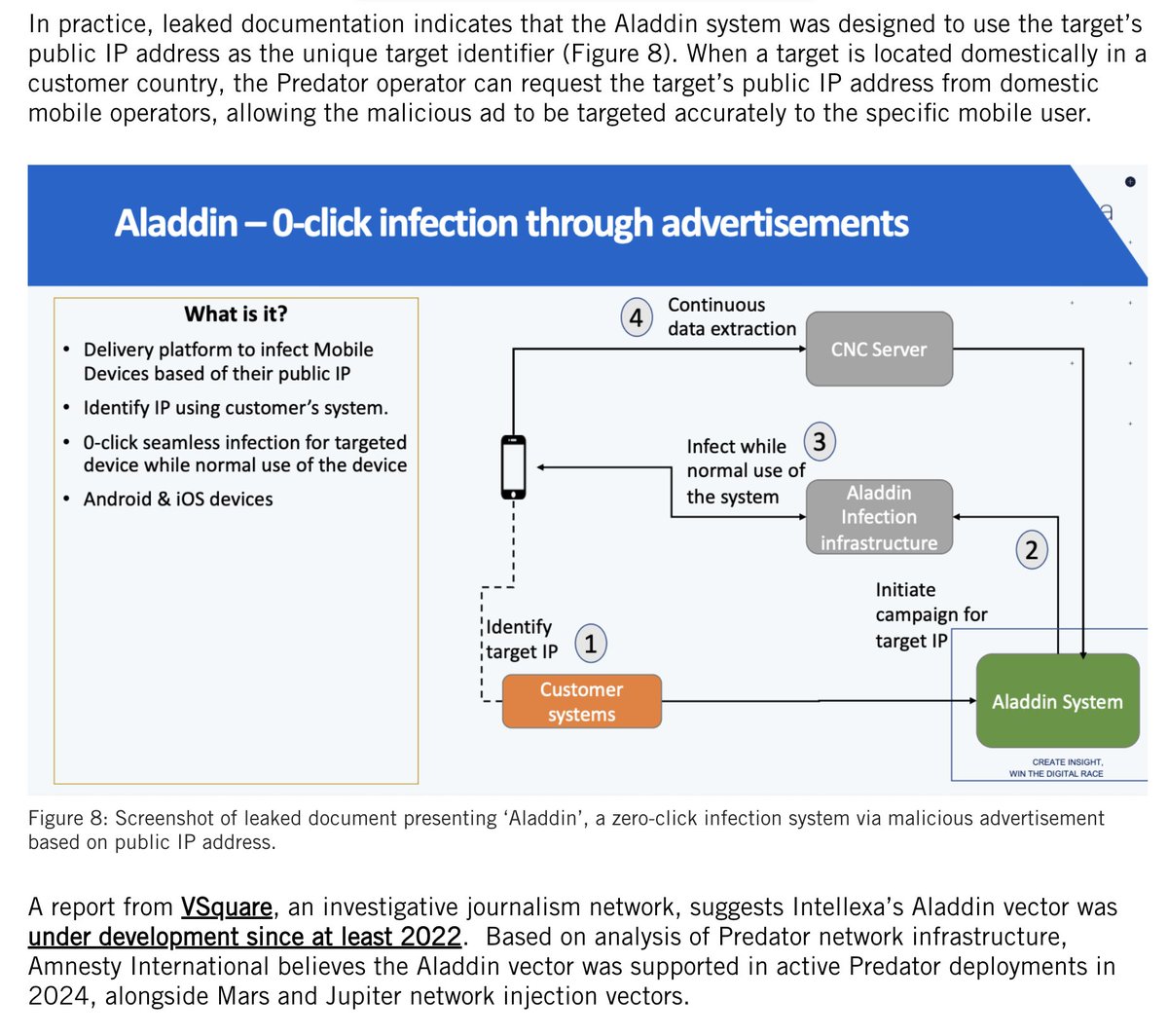
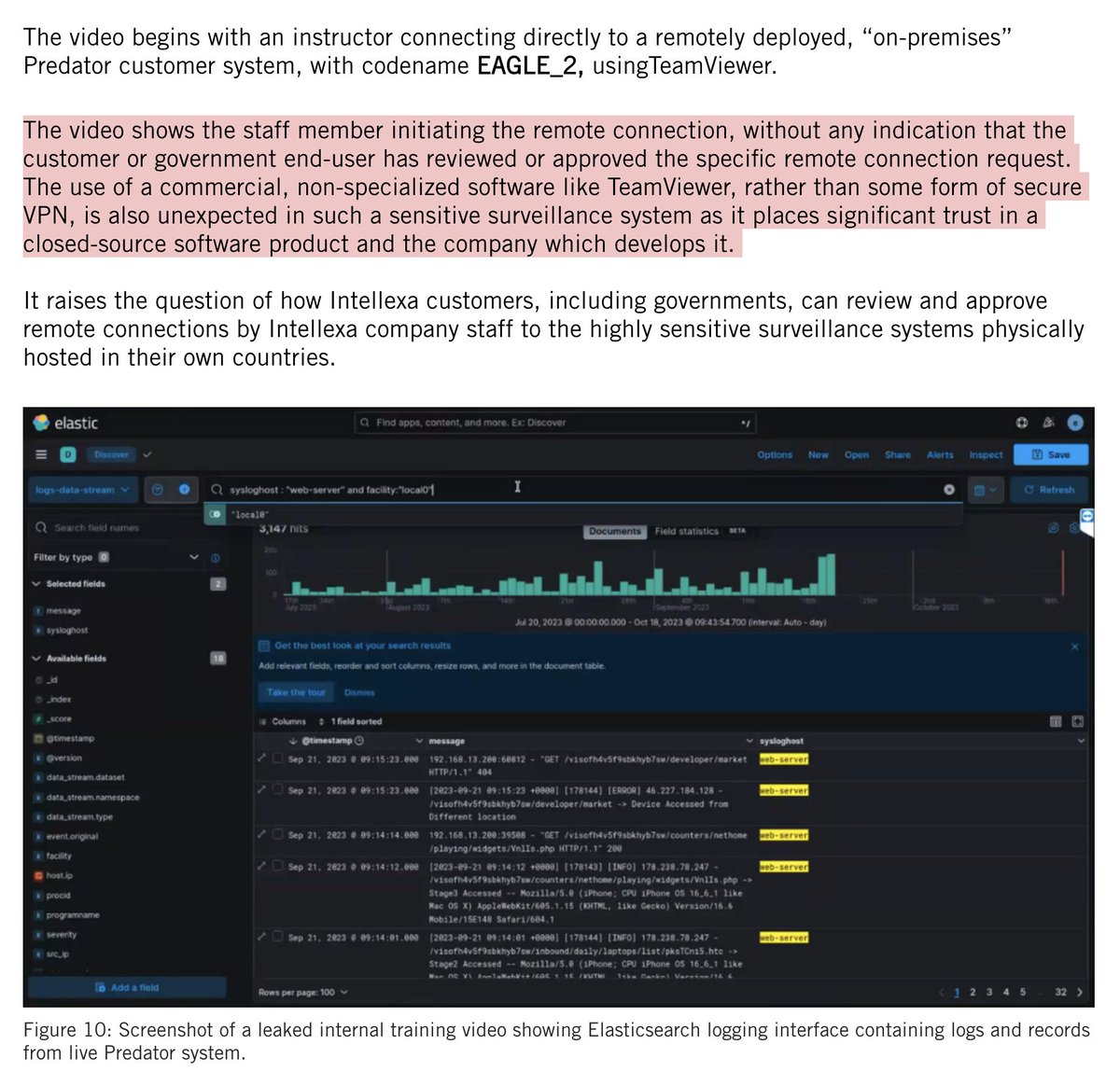
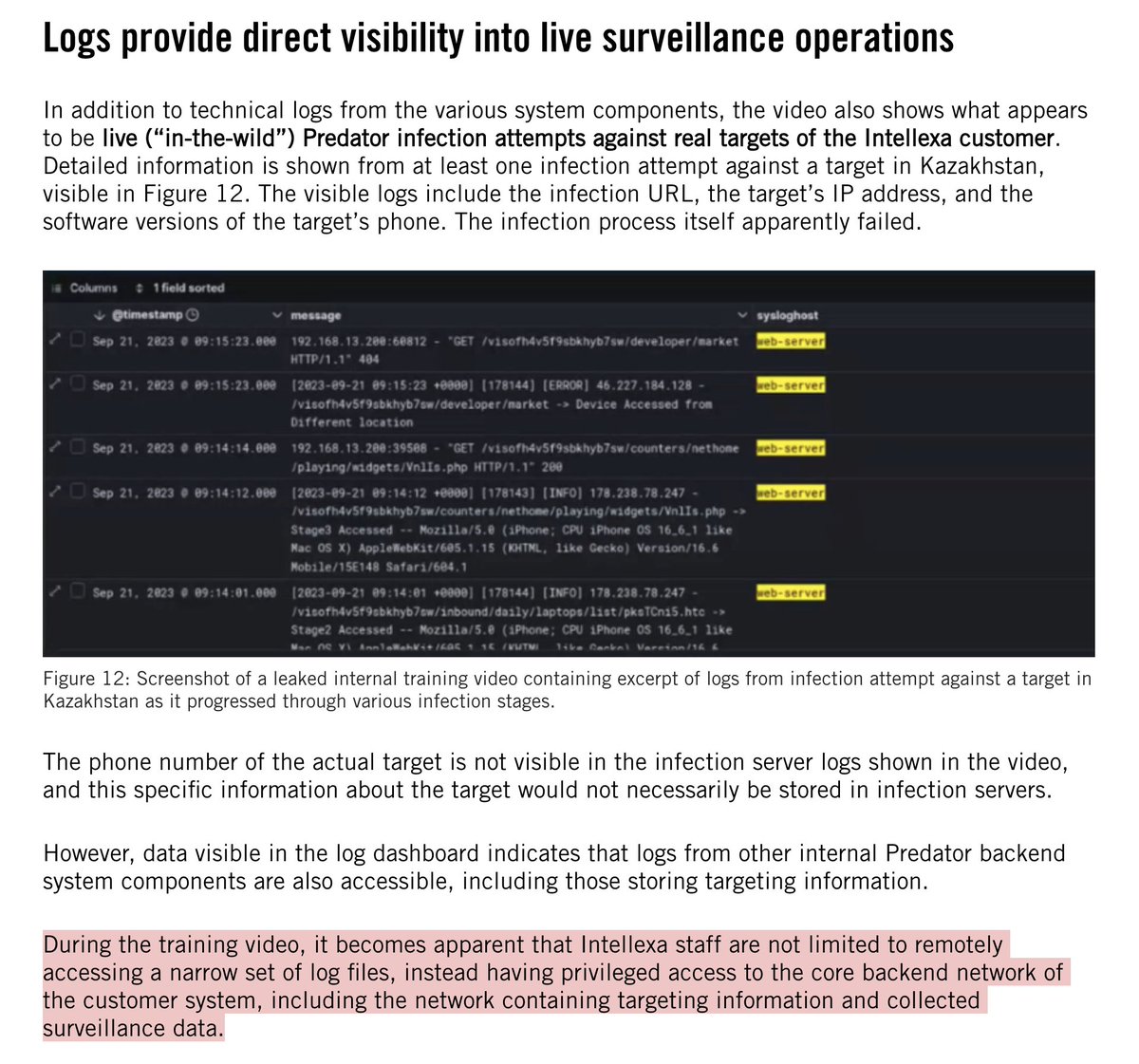
9/ The FORCEDENTRY zero-click exploit is prominently mentioned @apple's lawsuit.
It was discovered when a spyware victim let us check their phone.
This is as it should be: targets of dictatorial surveillance contributing to fighting back & helping protect us all.


It was discovered when a spyware victim let us check their phone.
This is as it should be: targets of dictatorial surveillance contributing to fighting back & helping protect us all.



10/ Immediate effects of @Apple filing suit against NSO:
✅ NSO an even more radioactive investment.
✅ Investors that stuck with NSO look not only amoral, but foolish.
✅ Scares off risk-averse government customers.
✅ Chilling effect on spyware industry.
✅ NSO an even more radioactive investment.
✅ Investors that stuck with NSO look not only amoral, but foolish.
✅ Scares off risk-averse government customers.
✅ Chilling effect on spyware industry.
11/ It would take a huge internal effort for a massive company to undertake any one of these:
✔Lawsuit
✔Victim Notification
✔Attribution
✔Civil society support.
@apple did it all at once.
There are unsung heroes in this story.
Complaint: apple.com/newsroom/pdfs/…
✔Lawsuit
✔Victim Notification
✔Attribution
✔Civil society support.
@apple did it all at once.
There are unsung heroes in this story.
Complaint: apple.com/newsroom/pdfs/…
12/ Addendum to tweet #4: @billyleonard at TAG reminds me that @Google / @android should also be on the list of companies that have notified NSO victims in the past.
Link: android-developers.googleblog.com/2017/04/an-inv…
Link: android-developers.googleblog.com/2017/04/an-inv…

13/ Just 2 weeks ago, the 9th Circuit Court of Appeals rejected NSO's claims to foreign sovereign immunity in @WhatsApp v. NSO.
Here's their CEO weighing in on @Apple's lawsuit.👇
Here's their CEO weighing in on @Apple's lawsuit.👇
https://twitter.com/wcathcart/status/1463214633423048705
• • •
Missing some Tweet in this thread? You can try to
force a refresh