If you're looking for network indicators of #log4j exploitation - this thread is for you. Every detection in this thread is freely available for use RIGHT NOW.
#snort #suricata #CVE202144228
#snort #suricata #CVE202144228
We have tons of inbound rules that'll hit on scanners and we've tried to cover ITW obfuscation methods, but let's be real, there are more ways to obfuscate these attacks than we can cover. 



For outbound traffic (generated by a successful "landing" of the attack strings) there are some good rules now.
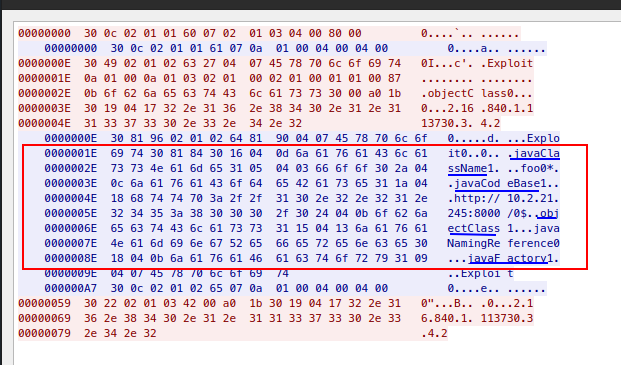
1) 2014474 and 2014475
These existing sigs alert on java (as determined by the UA) downloading a class file. Today we tweaked flowbits (2013035) for better coverage.

1) 2014474 and 2014475
These existing sigs alert on java (as determined by the UA) downloading a class file. Today we tweaked flowbits (2013035) for better coverage.


2) Outbound LDAP, LDAPS and RMI
These sigs are looking for outbound request for ldap, ldaps and RMI. LDAP and LDAPS requests set flowbits so we can see when the session got a response. Enable these rules at the perimeter & correctly set the $HOME_NET and $EXTERNAL_NET variables!

These sigs are looking for outbound request for ldap, ldaps and RMI. LDAP and LDAPS requests set flowbits so we can see when the session got a response. Enable these rules at the perimeter & correctly set the $HOME_NET and $EXTERNAL_NET variables!


4) Commonly observed domains
2034669 - ET POLICY dnslog .cn Observed in DNS Query
2034670 - ET ATTACK_RESPONSE DNS Query for Observed CVE-2121-44228 Payload Domain
These alert on DNS Lookups for domains being seen within the attack string (dnslog[.]cn and .bingsearchlib [.]com)
2034669 - ET POLICY dnslog .cn Observed in DNS Query
2034670 - ET ATTACK_RESPONSE DNS Query for Observed CVE-2121-44228 Payload Domain
These alert on DNS Lookups for domains being seen within the attack string (dnslog[.]cn and .bingsearchlib [.]com)
HUGE thanks to @_JohnHammond @RealTryHackMe for the "solar" room which allowed for a quick and easy replication environment and @SLASH30Miata for providing pcaps.
Speaking of PCAPS - We want more! Please submit #log4j exploit attempts to us via feedback.emergingthreats.net/feedback
Speaking of PCAPS - We want more! Please submit #log4j exploit attempts to us via feedback.emergingthreats.net/feedback
• • •
Missing some Tweet in this thread? You can try to
force a refresh