Hmm, this is actually much less impressive than I expected as far as inverting PhotoDNA (based only on reading @hackerfactor's blog post) reddit.com/r/MachineLearn… 
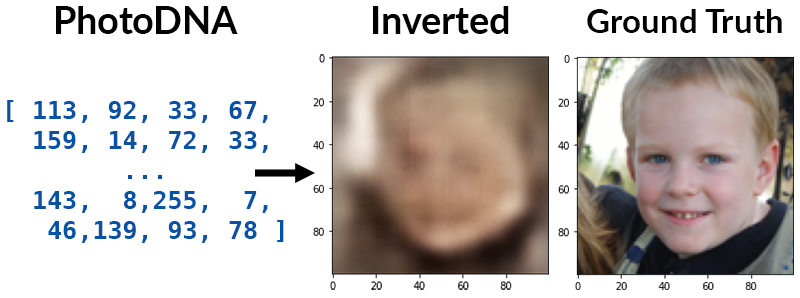
@hackerfactor @matthew_d_green perhaps of interest if you haven't seen it yet and want to take a break from fighting with half of CS twitter about NFTs ;)
Ah, I see, it's taking a pure black box ML approach to try and learn the inverse straight from the hashes. OK, that is pretty impressive!
I had assumed it would use the limitations described here as a starting point, and then use the ML to sharpen/refine/upscale the generated image – but that would require a lot more RE on the PhotoDNA DLL hackerfactor.com/blog/index.php…
And having spent a weekend staring at that DLL's optimized XMM code until my eyes bled last summer, I certainly can't blame @anishathalye for taking the black box approach ;)
• • •
Missing some Tweet in this thread? You can try to
force a refresh