7 Things To Get Started With Android Pentesting :
A Thread 🧵👇
A Thread 🧵👇
1️⃣ Get the APK
Download from :
➡ apkpure.com
➡ apkmirror.com
➡ aptoide.en.aptoide.com
➡ en.uptodown.com/android
➡ apps.evozi.com/apk-downloader/ (Downloads from PlayStore)
Note: These are 3rd party sites, hence, install only on your testing device/emulator.
Download from :
➡ apkpure.com
➡ apkmirror.com
➡ aptoide.en.aptoide.com
➡ en.uptodown.com/android
➡ apps.evozi.com/apk-downloader/ (Downloads from PlayStore)
Note: These are 3rd party sites, hence, install only on your testing device/emulator.
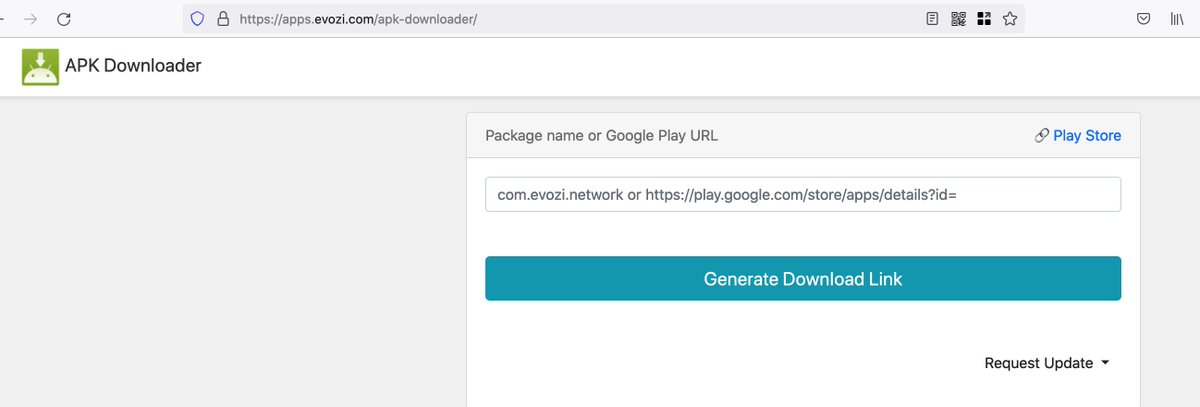
↪ Get apk from your own device using android adb :
Find app in PlayStore using a 'browser'. URL of the app contains the package name.
1. Connect your device to your laptop.
2. Enable 'USB debugging' on your device
Run the commands : stackoverflow.com/a/18003462

Find app in PlayStore using a 'browser'. URL of the app contains the package name.
1. Connect your device to your laptop.
2. Enable 'USB debugging' on your device
Run the commands : stackoverflow.com/a/18003462


2️⃣ Decompile the APK
Use the following tools :
1. apktool - ibotpeaches.github.io/Apktool/instal…
Command : apktool d app.apk
Decompiles to folder.
2. jadx - github.com/skylot/jadx
Command : jadx-gui app.apk
Decompiles in GUI

Use the following tools :
1. apktool - ibotpeaches.github.io/Apktool/instal…
Command : apktool d app.apk
Decompiles to folder.
2. jadx - github.com/skylot/jadx
Command : jadx-gui app.apk
Decompiles in GUI


3️⃣ Setup Emulator/Device
1. Rooted device - Use Magisk with it's modules for awesome features like hide root status from other apps, specially financial apps github.com/topjohnwu/Magi…
2. Genymotion - Smoothest emulator
blog.yeswehack.com/yeswerhackers/…
1. Rooted device - Use Magisk with it's modules for awesome features like hide root status from other apps, specially financial apps github.com/topjohnwu/Magi…
2. Genymotion - Smoothest emulator
blog.yeswehack.com/yeswerhackers/…
4️⃣ Static Analysis of the app
2. mobileAudit - github.com/mpast/mobileAu…
3. Deobfuscating Apps :
- apk-deguard.com
- github.com/Gyoonus/deoptf…
1. MobSF - github.com/MobSF/Mobile-S…
2. mobileAudit - github.com/mpast/mobileAu…
3. Deobfuscating Apps :
- apk-deguard.com
- github.com/Gyoonus/deoptf…
1. MobSF - github.com/MobSF/Mobile-S…
5️⃣ Dynamic Analysis of app
1. MobSF - github.com/MobSF/Mobile-S…
2. qark - github.com/linkedin/qark
3. frida - frida.re ⬅ Very crucial in complex android app testing, decrypting strings, in-memory strings etc
4. Objection - github.com/sensepost/obje… ⬅ SSL Unpinning
1. MobSF - github.com/MobSF/Mobile-S…
2. qark - github.com/linkedin/qark
3. frida - frida.re ⬅ Very crucial in complex android app testing, decrypting strings, in-memory strings etc
4. Objection - github.com/sensepost/obje… ⬅ SSL Unpinning
6️⃣ Getting started resources :
1. Detailed blog : infosecwriteups.com/android-app-se…
2. Mobile App Pentesting Series : youtube.com/playlist?list=…
3. github.com/B3nac/Android-…
4. Infosec android writeups - infosecwriteups.com/tagged/android
5. h1 android writeups - infosecwriteups.com/hacker101-ctf-…
1. Detailed blog : infosecwriteups.com/android-app-se…
2. Mobile App Pentesting Series : youtube.com/playlist?list=…
3. github.com/B3nac/Android-…
4. Infosec android writeups - infosecwriteups.com/tagged/android
5. h1 android writeups - infosecwriteups.com/hacker101-ctf-…
7️⃣ Vulnerable android application for testing :
1. github.com/optiv/Insecure…
2. Kotlin app - ctf.hpandro.raviramesh.info
3. rewanthtammana.com/damn-vulnerabl…
4. github.com/satishpatnayak…
5. Flutter app - github.com/B3nac/InjuredA…
6. github.com/oversecured/ov…
7. OWASP MSTG - github.com/OWASP/MSTG-Hac…
1. github.com/optiv/Insecure…
2. Kotlin app - ctf.hpandro.raviramesh.info
3. rewanthtammana.com/damn-vulnerabl…
4. github.com/satishpatnayak…
5. Flutter app - github.com/B3nac/InjuredA…
6. github.com/oversecured/ov…
7. OWASP MSTG - github.com/OWASP/MSTG-Hac…
• • •
Missing some Tweet in this thread? You can try to
force a refresh