Financially-motivated cybercriminals are usually staying away from politics, but when politics hit close to home, they strike back. In this thread, we share a quick recap of the most interesting initiatives and discussions about #UkraineRussiaConflict on cybercrime forums. 

A user on CrdClub proposed to organize a fundraiser to support the families and children in Ukraine. The author shared a BTC wallet that was issued by the forum’s admin specifically for this cause. 

A user on Exploit published a post asking Russian citizens to participate in protests against the war. Other users commented that regardless of the forum’s rules, it is highly important to discuss the matter and state such opinions out loud. However, the thread was deleted. 

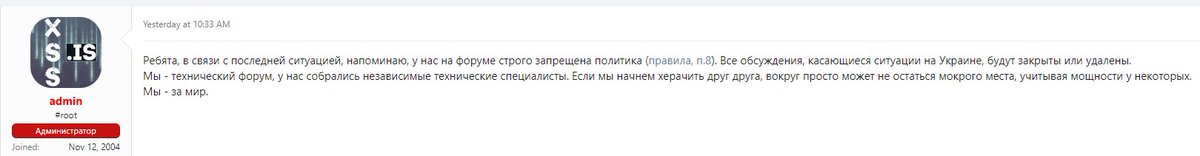
Admin of XSS reminded that politics is prohibited on the forum: “All discussions about the Ukraine situation will be closed or deleted”. He said that if Russian-speaking cybercriminals will start to attack each other, there will be nothing left. 


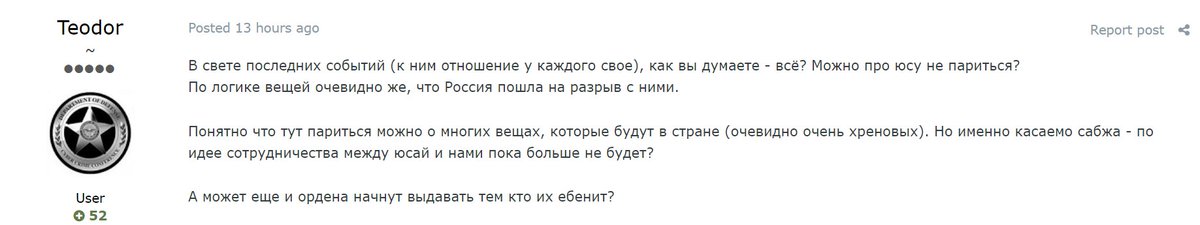
Some users asked if it is possible to safely attack US companies again, referring to recent arrests of Russian-speaking cybercriminals: “Looks like there will be no more collaboration between US and us?” Another user: “Did V/V [Putin] permit us to attack critical infrastructure?” 


The Ukrainian Ministry of Defense allegedly asked the Ukrainian hacker community for help and requested to fill out a Google Docs form. Some users considered it to be a law enforcement operation aimed to gain information on hackers or refused to participate. 



Multiple initiatives were shared on Raidforums (now it is allegedly seized by authorities). The admin claimed any user connected from Russia will be banned, while users suggested making a collection of “attackable Russian IP-ranges” and “IP-ranges that are scanning Ukraine”.
Speaking of #Conti’s statements regarding Russia's support, it did not gain much attention among cybercriminals on forums. KELA continues to monitor sources and welcomes any additions to this thread you might have.
• • •
Missing some Tweet in this thread? You can try to
force a refresh






