So, Conti chat logs were leaked, I got my hand on a google-translated version of it, I'll document what I found interesting 🧵
March 2021: They tried to get ahold of a @vmw_carbonblack license, detailing their roadblocks and options: 

Conti "employees" are in fact employees and request days off and maintain non-profesionnal (or, to the very least, friendly) relationships with colleagues 



Driver is *not* happy with specter's performance 😔 They even need to explain what "+=" means. Not the most experienced dev there is, it seems 😂 



Wait did they actually successfully bought a @vmw_carbonblack license? 👀 I'll look it up 

At last, my cyrillic knowledge got useful! The translation said they bought "sonicwolves", but when reading the original, "соникволы" reads "so-nik-voll" and could understand that they meant they bought the @SonicWall Next-Gen Firewall 



Still don't know if they successfully bought Carbon Black, but they do know the best free translator is Google Translate 😂 

Last useful mention of @vmw_carbonblack there is is 3-4 months later, they mention that they indeed bought it successfully but don't seem to have deployed it or done something useful with it: 

So Stern messaged every account in feb 2021 asking who could make a scanner for the @SonicWall vulnerability (idk what CVE). He messaged... 83 accounts 🤯 That is a lot of people 

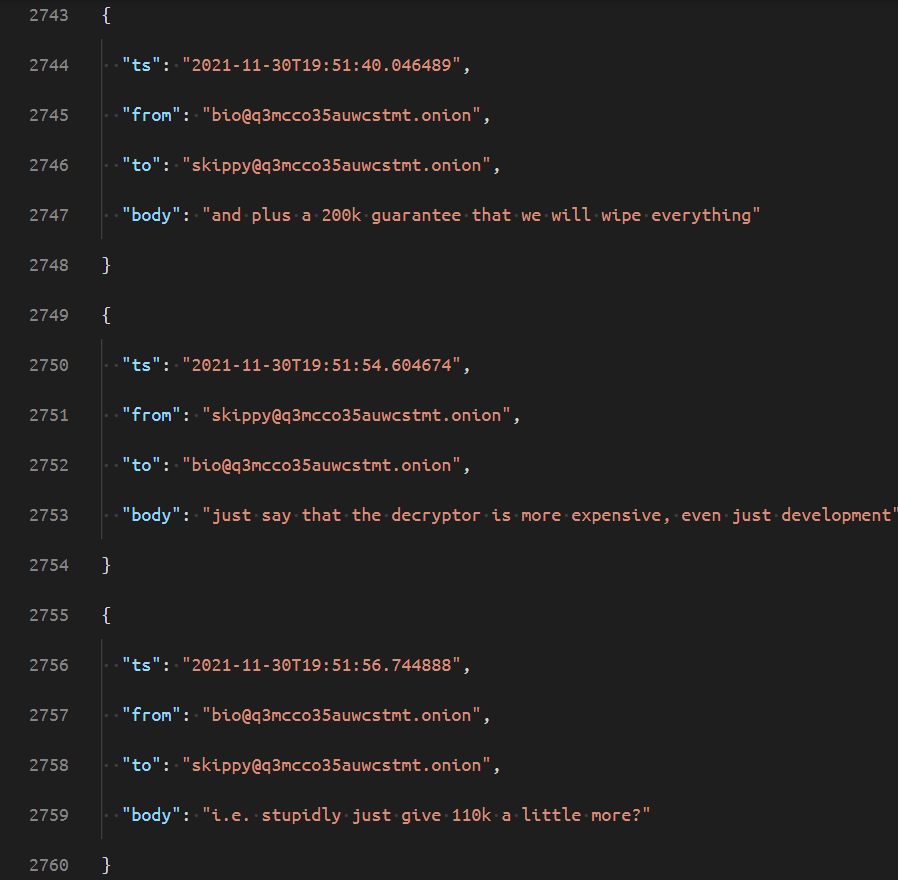
June 2021: A very interesting message from Mango to Stern where they basically say their pre-encryption processes are shit among other things: 

They have a @shodanhq license for their "OSINT Department" 😂😂 BUT they also have a signalhire license as well (most likely to find contacts for their victims and give them harassment phone calls) and they want a ZoomInfo license :o Sent by same user from the previous message 



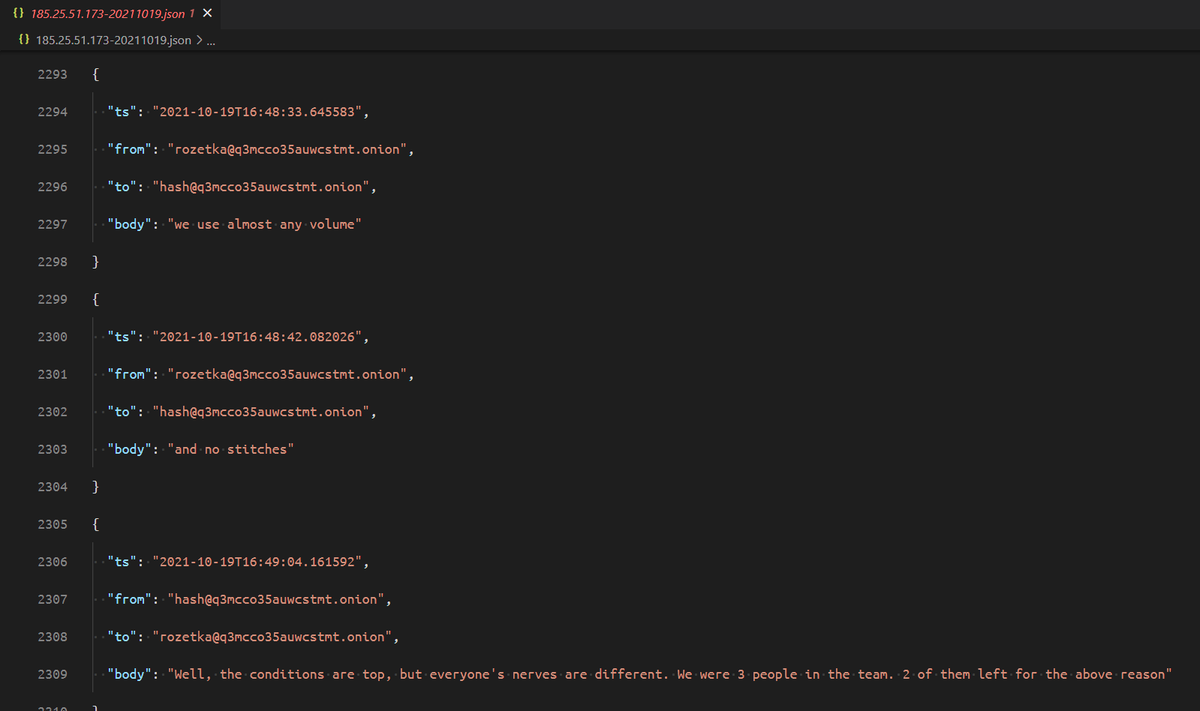
An interesting conversation between bio and skippy, where bio is trying to negociate a payment for a big company, but the data they exfilled was mostly worthless. Lot of discussion and they seem to take the company's claims rather seriously: 







Derek pitches a new way to gather victims to stern. Get a database of business with IT people's phones, call them automatically. When someone answers, a real operator talk the low-level IT person into believing they missed an update (1/?) 

but instead of making the admin install something, they cleverly say they're gonna call their boss, leaving the time for the low-level IT person to tell their boss to expect a call from a third party, making the scheme way more believable. Then, they trick the IT boss (2/3)
into installing malware, and tell them it didn't work, and schedule an in-person fix later in time, making the IT person think they're going to come fix it and that everything is normal, but leaving a lot of time for conti to prepare an attack (3/3)
I think I misread a small detail: They don't call the IT boss, they call the client the IT firm manages (I think)? The rest seems good
There are a *lot* of mentions of attacked companies that were not public. Obviously won't name them here, but it shows a lot of companies pay and never disclose their breach
I mentionned earlier they wanted a @ZoomInfo license, well they got it, I saw customers-only zoominfo links in their chats 

Stern seems very focused on blockchain. There are a lot of mentions of them looking for "blockchain gurus" and they want to build their own blockchain it seems? 

Elvira is a new recruit from june 2021, and they needed to prove their worth by... completing a bring-at-home test. Gratz Elvira, it took you six hours to... count the # of files by extensions in a given directory?😂If you ever think you're not good enough, bookmark this tweet 



Holy shit, 2020 logs, and many many other things, just leaked. Source codes for many of their tools, I'll look into it. CONTI USES @laravelphp my favourite Web Framework😍 

The leak contains very very long screenshots (probably taken using chrome devtools or something) of BazarLoader bots IPs and full information 😲 

Its only 9 pages worth of screenshots though. There is also the JS code showing how they could run commands on the bots: 

There are 36 pages where the HTML is available which could be used to parse the data, but it's not all the available data, since the last page shows that there are at least 51 pages (most likely many more) 



Worth noting that even though I load the HTML files offline the links point to their onion domain, perhaps indicating that the domain is hardcoded (in Bazars code, not contis). Onion domain is still up (I get a cert error), but there seem to be another step to access the service 

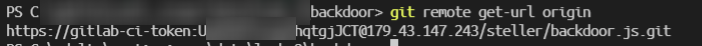
Now looking into the backdoor.js leaked archive. It's a .git file, so rename to .git --> git init --> git reset --hard and you get the files. First thing i notice is they use Python2 😭😭😭 

In the git, there are saved creds for their clearweb gitlab instance but it says SSL error when I try to connect using HTTPS. Using HTTP, there is a dummy (?) Website 

Back to backdoor.js.git: Here are the forbidden locale (if your IP comes from these countries, don't run the backdoor) 

There are a lot of IOCs in the code (and obviously in the chat logs), Threat Intelligence vendors and intelligence agencies will have a lot of fun going through those 

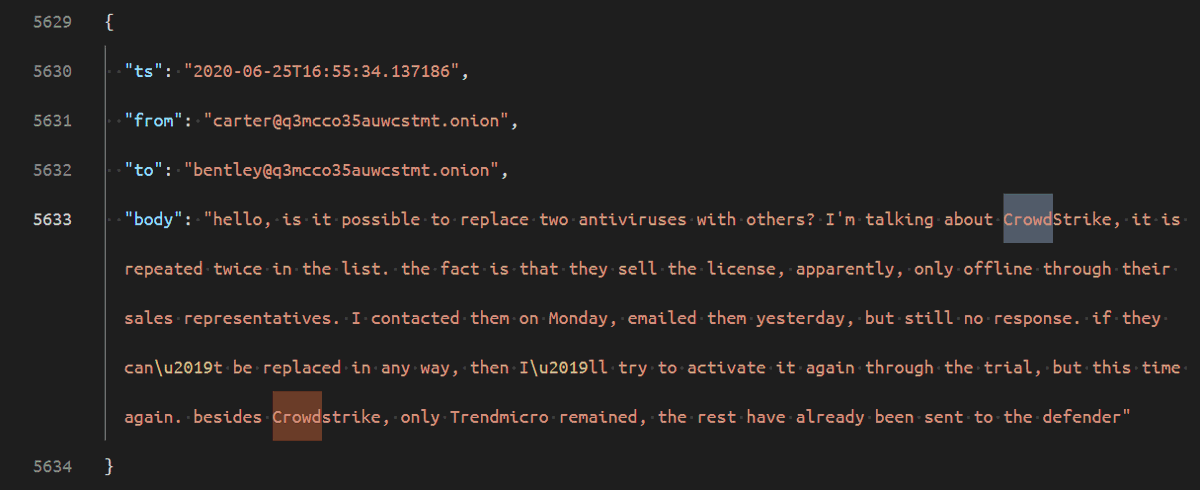
Taking a break from the code, back to the chat logs! @CrowdStrike is mentionned often in the chats in 2020, where they wanted to get a license for it but, like @vmw_carbonblack , it's only sold by h u m a n s. See 3rd image, they test with a lot of AV vendors :o 




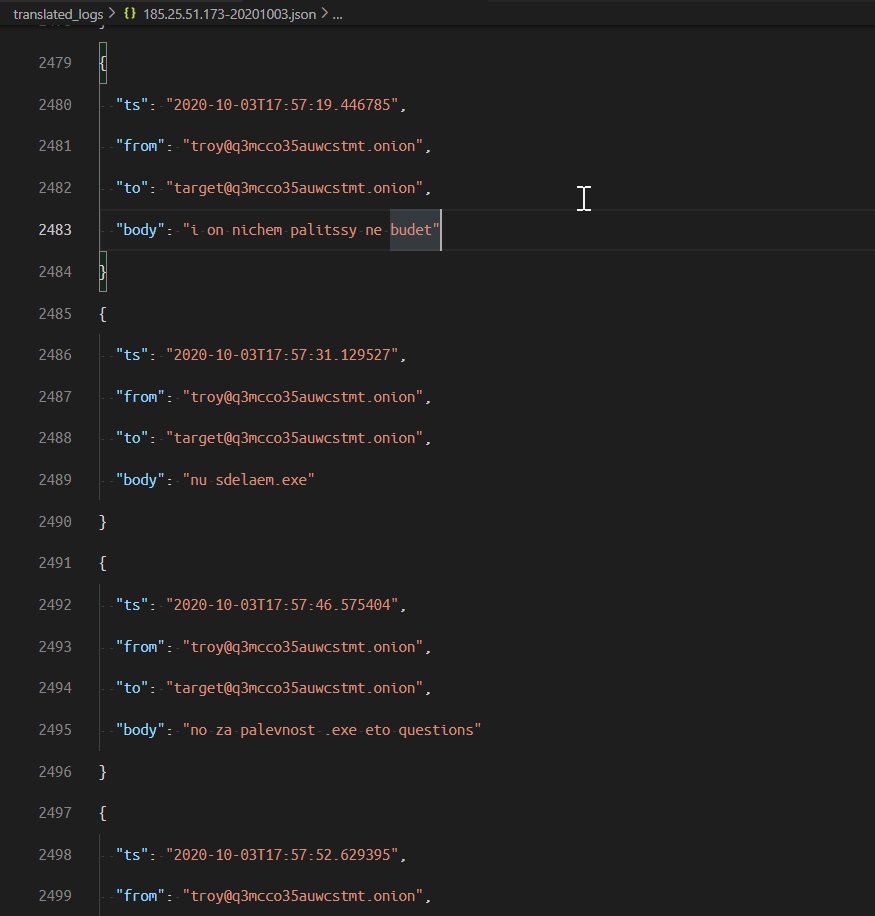
Troy is an interesting member. They write in russian, but using the latin alphabet, not cyrillic. Must be a foreigner that learned russian but didn't bother to learn the keyboard layout of cyrillic. Funfact: Google translate still manages to translate that to english from russian 
Wow. Target is NOT happy with a mistake bentley made. From my understanding, bentley ran a command on MANY hosts that displayed a visual error to the users. Oof. (this goes on for many more messages, but you get the idea LOL) 





There are a lot of talks about opening an office in Moscow and existing offices (going to the office). I don't think this is a translation error. офис actually means "office" (thanks, duolingo) 





I don't know how I missed it but the actual locker + decryptor source code was leaked as well, but it's password-protected. We can see the file names, but not the content. The source of the leak said that they'll share only with trusted people to avoid more damage. 



Back at it! So the source code of the Conti decryptor was leaked, but not the locker (still password-protected). I won't go into details of the code in this thread as many people are way better at this than me :) 

⚠ Right after sending this tweet, I was given the full source code including the locker. Expect the full locker source code to leak soon, if not already leaked. I will *not* be sharing the source, please do not ask :)
This one is pretty good. If I understand correctly, bloodrush is having an emotional talk with best where they say that it really sucks for them to constantly be detected and cleaned up (destruction) by their victim :( 


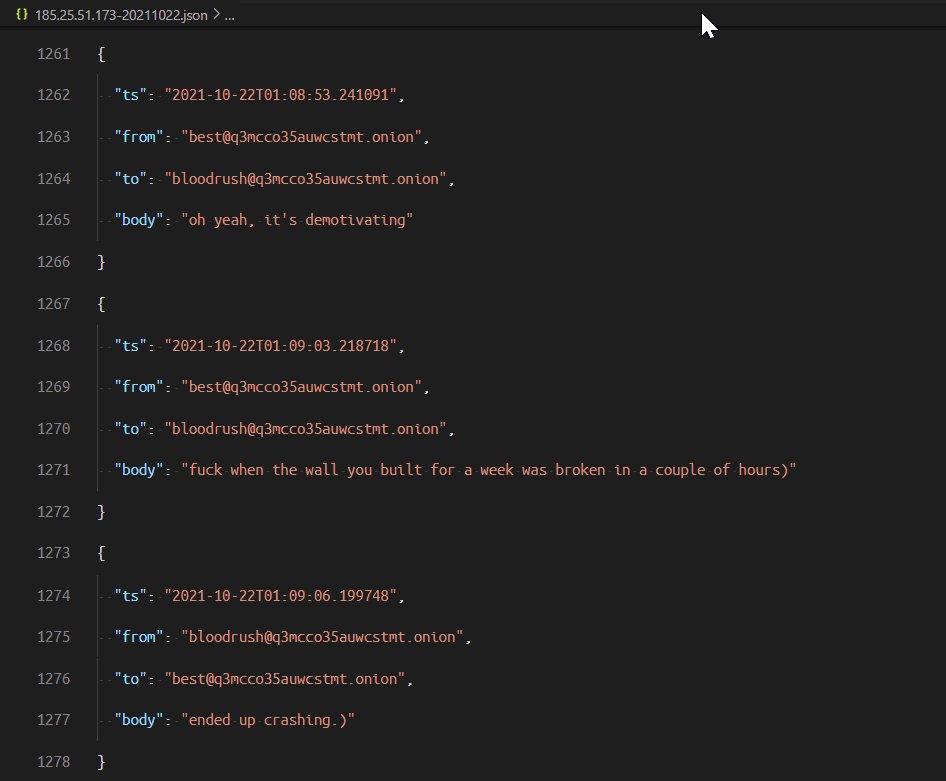
Oct. 22 2021: Chatter about attacking 500-800 targets. Important to note, this date matches a public statement from conti where they reacted to REvil being hacked and forced offline. I don't remember seeing an attack of this scale. Did it fail? 



It's a bit hard to understand, but I think they're cooperating with TrickBot and BazarLoader to hit big on monday Oct 25 2021 and hit big companies with revenues from 50mil ruble to 90bil ruble. 




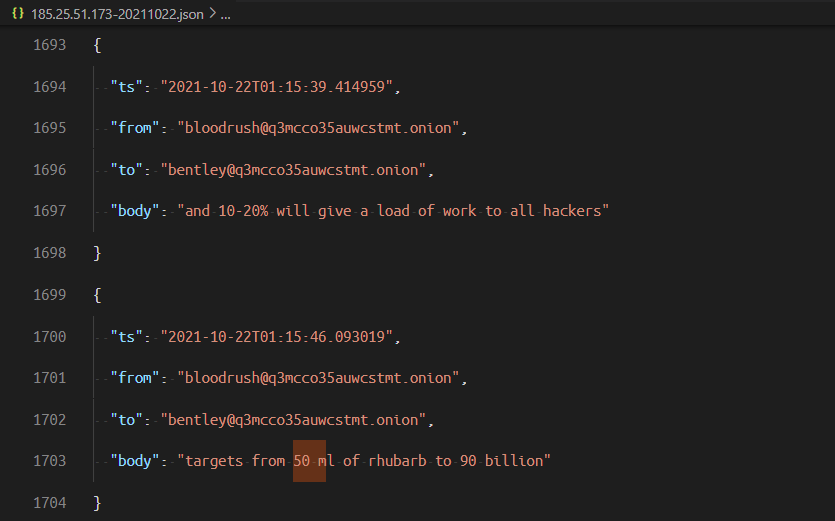
Earlier, I mentionned that they had access to @ZoomInfo to gather intel of their victim.Well they also have access to @crunchbase , which seems like a similar tool. Still going through the oct. 22- oct 25 logs, they were working all weekend to gather as much victims before monday 


Nothing on oct 25, 26 or 27. Maybe they have another chat platform where they coordonated that.
Oh god, in the latest leak, there are many other chat leaks from "rocket-chat". Its formatted in proper json this time, but I'll need to code something to read the messages, there is too much noise. The logs date back 2020-08-22 at the earliest. 

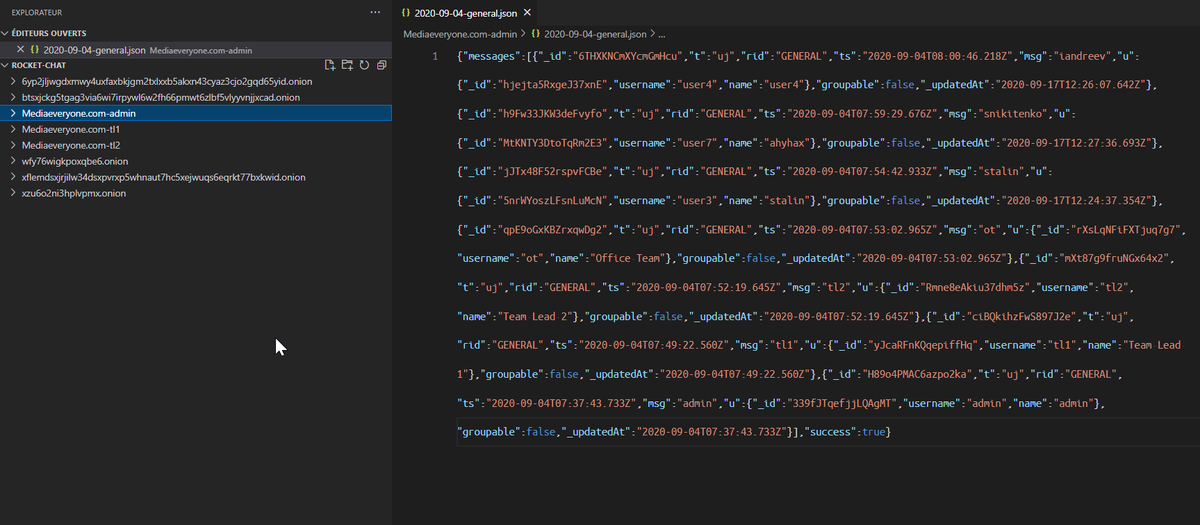

YES I successfully imported one small set of logs in my own rocketchat instance, so I'll be able to easily navigate, search and translate their chats 

So it seems the "no politics at job" does not apply to Conti, they even homophobically insult Biden in the #announcements channel LOL 
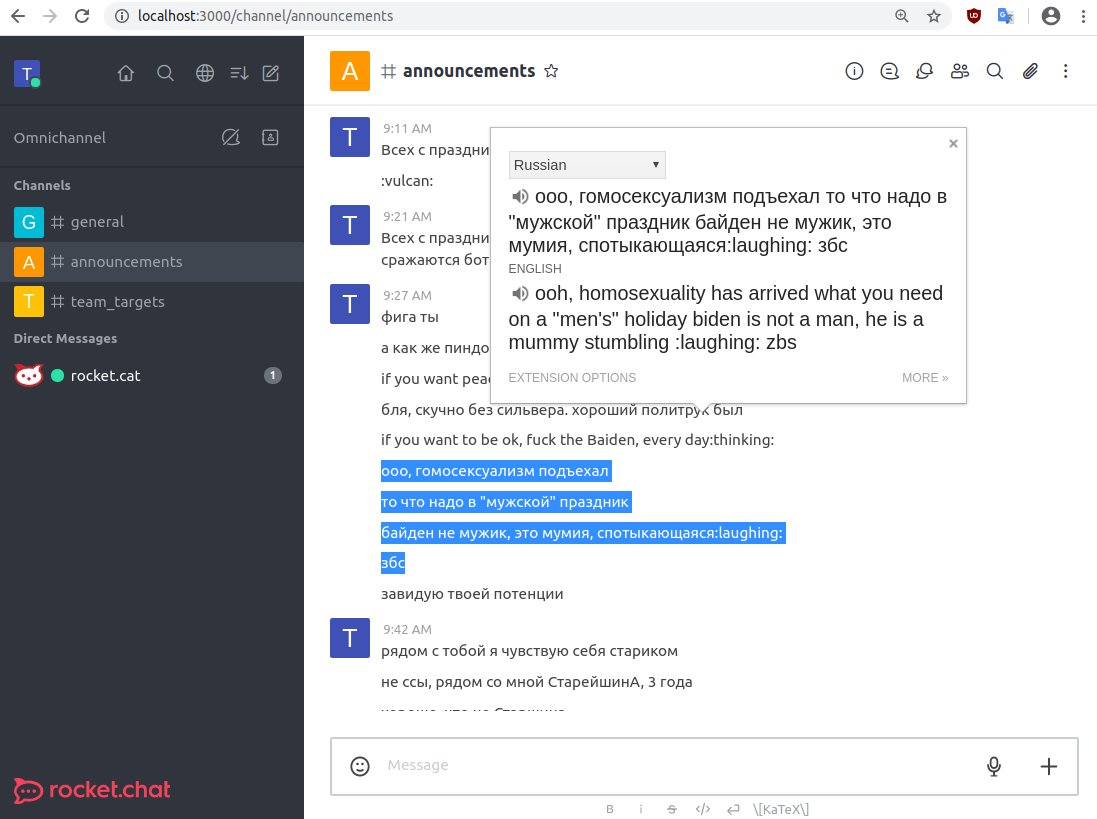
Another gem. Tarrant, what a weird subject to be chatting about in #general 😬😬😬 

IT'S NOT EVEN A SECRET LOL
"What does your daddy do at work?"
"Daddy negociates with americans who enable macros on untrusted documents. He's my hero 😍😍"
"What does your daddy do at work?"
"Daddy negociates with americans who enable macros on untrusted documents. He's my hero 😍😍"

At least they have the decency of not showing PHP to their son 🤠(both messages are from Oct. 1st 2021) 

If you want insights in a more structured manner, @briankrebs did a fantastic article conti chat logs, and more is to come :) krebsonsecurity.com/2022/03/conti-…
hey @TrendMicro you seem to have quite a reputation in the conti group, you should be proud! 😍 

So one interesting thing in one of their rocketchat instances is they create one channel per victim to coordonate the operation, from initial access to impact on objective. The channel name is usually <number>-<status>-<company-domain>. If you have been breached by conti 1/2 

hit me up I'll give you a complete transcript of their operation in your network if I have access. 2/2 In this screenshot, tl1 stands for "Team Lead 1", this name is not translated it was in the leak directly 

Additional translations because google translate has problems with a lot of russian/tech terms
https://twitter.com/seadev3/status/1498783071969099777?s=20&t=3zFs-Vi5IonHNZXrg77V4w
I found an interview! Silver interviews biggie. They have work hours. Their "company" creates "software for pentesters" 



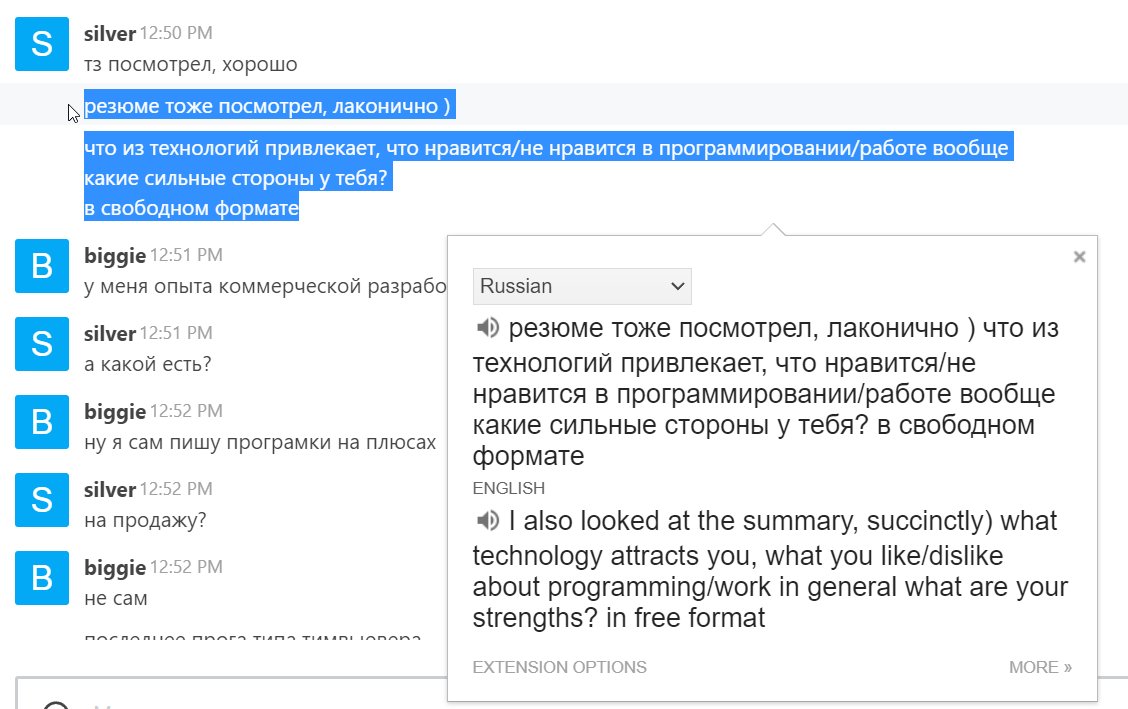


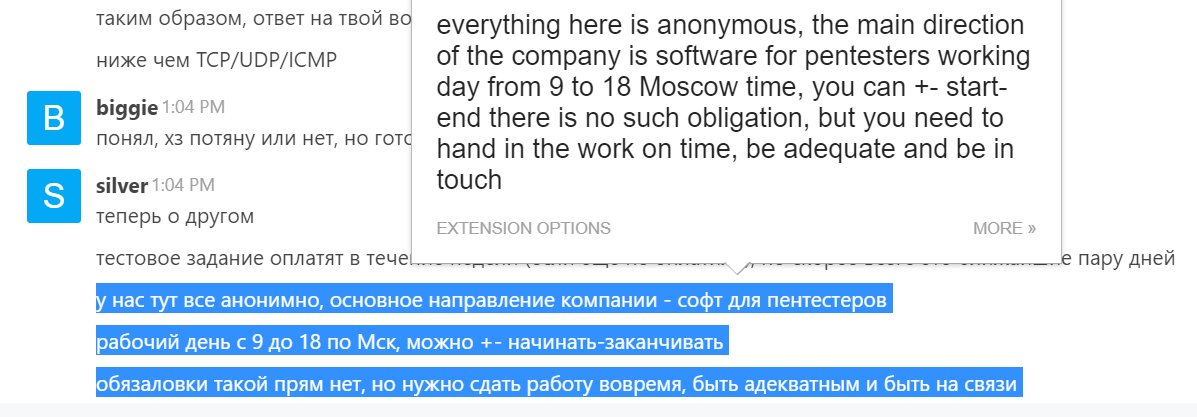
They pay candidates to do their bring-at-home test?? If we should learn one thing from them, let it be this 👀 

If you're interested in the technical procedures they give their operators, have a read!
https://twitter.com/res260/status/1499249425138475014
• • •
Missing some Tweet in this thread? You can try to
force a refresh