#ContiLeak 🧵! This time, management/developpers documentation 📄
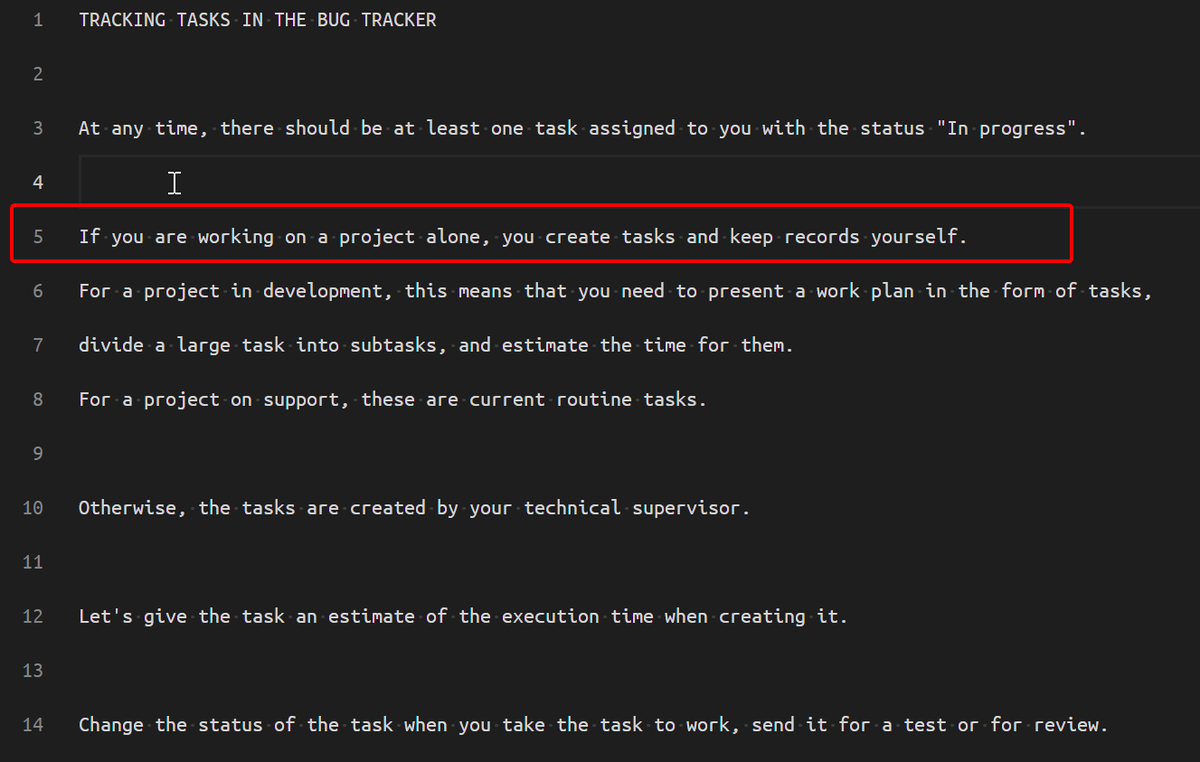
CODING PRINCIPLES
Those are surprisingly good principles. "The wrong choice will grow in the code forever!" ✅✅✅✅✅ FACTS


Those are surprisingly good principles. "The wrong choice will grow in the code forever!" ✅✅✅✅✅ FACTS



GIT POLICY
Like all of us, they use git for all the good reasons :) Perhaps the most interesting thing is that they actually track issues in an "accounting system" with ticket numbers (3rd image). JIRA USERS REJOICE, IF CRIMINALS DO IT IT MUST BE USEFUL🎉🎉🎉🎉



Like all of us, they use git for all the good reasons :) Perhaps the most interesting thing is that they actually track issues in an "accounting system" with ticket numbers (3rd image). JIRA USERS REJOICE, IF CRIMINALS DO IT IT MUST BE USEFUL🎉🎉🎉🎉



ISSUE TRACKING AND PROJECT DEVELOPMENT
This text was written by every project manager and scrum master who has ever lived 😂 You can litteraly give this piece of text to any software development business and it applies to them

This text was written by every project manager and scrum master who has ever lived 😂 You can litteraly give this piece of text to any software development business and it applies to them


INSTRUCTION TO THE TECHNICAL MANAGER
The technical manager manages HR, half of this documentation is how to deal with humans👨👨👦👦But they have a lot of responsabilities, like code review and managing hires



The technical manager manages HR, half of this documentation is how to deal with humans👨👨👦👦But they have a lot of responsabilities, like code review and managing hires




BUG REPORTING RULES
Ransomware groups, like all of us, HATE IT when they receive reports that their program has bugs but without the needed context to fix it 😤😤
Ransomware groups, like all of us, HATE IT when they receive reports that their program has bugs but without the needed context to fix it 😤😤

SAFETY PRECAUTIONS
Opsec tips from hackers! There are 12 bullet points, and they all aim at reducing the amount of information that can be linked to the real "you". I didn't know about whoer.net, interesting website!


Opsec tips from hackers! There are 12 bullet points, and they all aim at reducing the amount of information that can be linked to the real "you". I didn't know about whoer.net, interesting website!


Yes Conti, ALWAYS check unknown files on @virustotal , ESPECIALLY the ones you're compiling from source please 🙏🙏 





TRACKING TASKS IN THE BUG TRACKER
This is a heavy process (see 3rd image), and why would I create jira tickets for a solo project?? YOU'RE SLOWING DOWN INNOVATION CONTI 😡


This is a heavy process (see 3rd image), and why would I create jira tickets for a solo project?? YOU'RE SLOWING DOWN INNOVATION CONTI 😡


I'll end this 🧵 here, there are a lot more docs detailling more technical things, like their RDP scanner/ bruteforcer, website/sql vulnerability scanner, vpn module, OWA creds stuffing for top 50 000 alexa websites, and more. I might look into it later, but rn im exhausted :)
• • •
Missing some Tweet in this thread? You can try to
force a refresh









