
The #ContiLeaks contained some messages consisting of IP:Username:pass combinations for #Conti infrastructure.
This allows us to connect certain #Trickbot activcity with the #Conti group:
1/x
This allows us to connect certain #Trickbot activcity with the #Conti group:
1/x

The IP's in the image are the following:
117.252.69[.]134
117.252.68[.]15
116.206.153[.]212
103.78.13[.]150
103.47.170[.]131
103.47.170[.]130
118.91.190[.]42
117.197.41[.]36
117.222.63[.]77
117.252.69[.]210
2/x
117.252.69[.]134
117.252.68[.]15
116.206.153[.]212
103.78.13[.]150
103.47.170[.]131
103.47.170[.]130
118.91.190[.]42
117.197.41[.]36
117.222.63[.]77
117.252.69[.]210
2/x
Using @MaltegoHQ together with OTX/Alienvault and
@virustotal integration, we are able to connect several of these IP's to #Trickbot activity:
3/x
@virustotal integration, we are able to connect several of these IP's to #Trickbot activity:
3/x
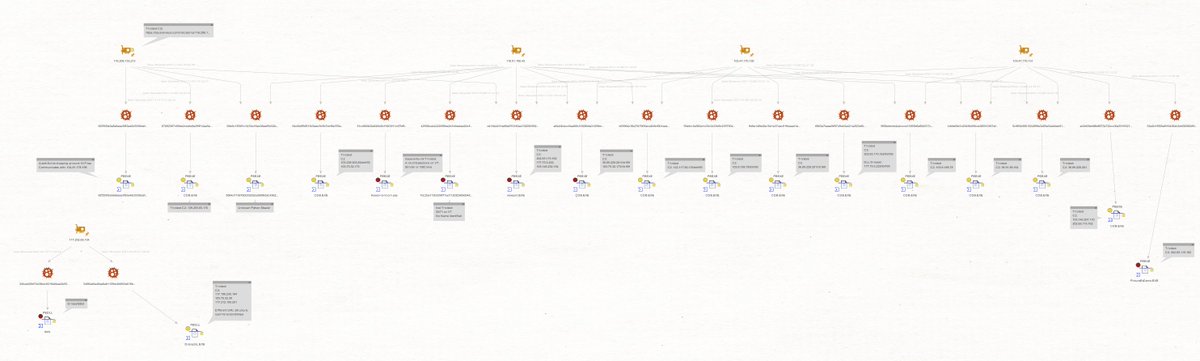
Some interesting observations:
- OTX shows that many of these devices used for spreading Trickbot are running #RouterOS by #Mikrotik
- 5 IPs don't have #malware attribution. These are all based in India. Maybe attack infrastructure ?
4/x
- OTX shows that many of these devices used for spreading Trickbot are running #RouterOS by #Mikrotik
- 5 IPs don't have #malware attribution. These are all based in India. Maybe attack infrastructure ?
4/x
Some other malware can be observed associated:
#Qbot / #Dridex
34fced20fd7d43fb4c8216e0bae2b55b4419f6d68fe4f5248eb4fa196d1d9e50
Unknown python #stealer:
09e5c1f5581c3433a16ec08ee85d32b27e2153aa60e30ca18f13a0e34ba9840a
5/x
#Qbot / #Dridex
34fced20fd7d43fb4c8216e0bae2b55b4419f6d68fe4f5248eb4fa196d1d9e50
Unknown python #stealer:
09e5c1f5581c3433a16ec08ee85d32b27e2153aa60e30ca18f13a0e34ba9840a
5/x
AutoIt Script
82f393fe3a8e6eae3f63e46d3336def02a2d6436e427cdcce3701f296b4176e1
Something called #Strictor or #VBClone:
51cd90f402a646d2b19203f11c87bf63c88bab6a2f623cea1e09d5d8c8a7bcd4
unidentified Malware:
42958ca44222099be2d1bfde4ee20c8a24ac4bcc1c9e29bbfe7b0c5d52c91212
6/x
82f393fe3a8e6eae3f63e46d3336def02a2d6436e427cdcce3701f296b4176e1
Something called #Strictor or #VBClone:
51cd90f402a646d2b19203f11c87bf63c88bab6a2f623cea1e09d5d8c8a7bcd4
unidentified Malware:
42958ca44222099be2d1bfde4ee20c8a24ac4bcc1c9e29bbfe7b0c5d52c91212
6/x
Would love to know if these have any relation to #Conti.
Maybe someone with better RE Skills can have a look ?
@malwrhunterteam @herrcore @aaqeel87 @TheDFIRReport @VK_Intel @executemalware
Maybe someone with better RE Skills can have a look ?
@malwrhunterteam @herrcore @aaqeel87 @TheDFIRReport @VK_Intel @executemalware
Ok, as this Tweet got waaaay more tracktion then I anticipated, I am following it up with an OTX Event to share all connected IoC!
Thanks for everyone viewing, liking and sharing my work ! <3
otx.alienvault.com/pulse/6223cad8…
Thanks for everyone viewing, liking and sharing my work ! <3
otx.alienvault.com/pulse/6223cad8…
• • •
Missing some Tweet in this thread? You can try to
force a refresh



