
SNARKS FOR NON-CRYPTOGRAPHERS
ZK tech is looking like the holy grail for Ethereum scalability and privacy.
But how does it actually work? What kinds of things are provable?
And if it’s working, what’s the barrier to full zkEVMs?
I spent the past few weeks diving in… (1/n)
ZK tech is looking like the holy grail for Ethereum scalability and privacy.
But how does it actually work? What kinds of things are provable?
And if it’s working, what’s the barrier to full zkEVMs?
I spent the past few weeks diving in… (1/n)
At this point, it’s clear that Ethereum can’t scale without L2s.
While optimistic rollups (like @arbitrum) and side chains (like @0xPolygon PoS chain) are incredible advances, it seems clear that the optimal mix of security and scalability will come from ZK rollups.
While optimistic rollups (like @arbitrum) and side chains (like @0xPolygon PoS chain) are incredible advances, it seems clear that the optimal mix of security and scalability will come from ZK rollups.
“In the medium to long term ZK rollups will win out in all use cases as ZK-SNARK technology improves.” — @vitalik
I’m not going to rehash this here. If you want to learn more, read this post from Vitalik (vitalik.ca/general/2021/0…) and follow @epolynya.
I’m not going to rehash this here. If you want to learn more, read this post from Vitalik (vitalik.ca/general/2021/0…) and follow @epolynya.
BUT WHAT DO ZK ROLLUPS ACTUALLY DO?
The 10k foot view is clear: Zero Knowledge Proofs allow you to prove something without disclosing the details of the thing.
How is that even possible? Here’s a non technical example…
The 10k foot view is clear: Zero Knowledge Proofs allow you to prove something without disclosing the details of the thing.
How is that even possible? Here’s a non technical example…
Imagine you’re colorblind and you don’t believe that I can see color.
So we devise an experiment:
- Start with two different colored balls behind your back.
- Show me one ball and return it behind your back
- Mix them up, and then show me another ball.
“Is it the same one?”
So we devise an experiment:
- Start with two different colored balls behind your back.
- Show me one ball and return it behind your back
- Mix them up, and then show me another ball.
“Is it the same one?”
By answering that question correctly enough times, I can prove to you that clearly I can distinguish between the two balls, without ever telling you the color of either ball.
The challenge with this kind of proof is that it’s interactive: We need to go back and forth.
The challenge with this kind of proof is that it’s interactive: We need to go back and forth.
Through cryptography, zkSNARKs allow us to do the same thing, non-interactively (this is the N in sNark). I can generate the proof once and you confirm it any time.
LET'S GET INTO THE CODE
Okay, this all makes sense conceptually, but how the hell did one even go about creating a SNARK?
The core idea is that you design circuits in a language called circom, which is similar to the HDLs used to write physical chips.
Okay, this all makes sense conceptually, but how the hell did one even go about creating a SNARK?
The core idea is that you design circuits in a language called circom, which is similar to the HDLs used to write physical chips.
The circom language outputs two things:
1) Code that allows you to plug in any input values, and outputs the results (including all intermediate results) of running the function. This output is called the witness.
2) Constraints that must be true if the code ran successfully.
1) Code that allows you to plug in any input values, and outputs the results (including all intermediate results) of running the function. This output is called the witness.
2) Constraints that must be true if the code ran successfully.
Conceptually, you can think of the constraints as taking in the witness values and confirming different pre-defined relationships between them (ie. input1 * input2 - output = 0).
If you can successfully plug in all the witness values, this confirms you ran the computation.
If you can successfully plug in all the witness values, this confirms you ran the computation.
I promised I wouldn’t get into the cryptography here, but if you’re interested, this blog series was what finally got it to click for me: zeroknowledgeblog.com
Notice you aren’t proving that something happened. All you’re able to prove is that you know the inputs that lead to some outputs.
Fortunately, if inputs include a signed transaction by a private key, proving you have the inputs can be enough to prove a transaction “happened”.
Fortunately, if inputs include a signed transaction by a private key, proving you have the inputs can be enough to prove a transaction “happened”.
So once we have the outputs of our circom circuit, what do we do?
snarkjs is another library (from @identhree, the same team that created circom — they are amazing) that helps facilitate the rest of the process. Here’s a visual overview.
snarkjs is another library (from @identhree, the same team that created circom — they are amazing) that helps facilitate the rest of the process. Here’s a visual overview.
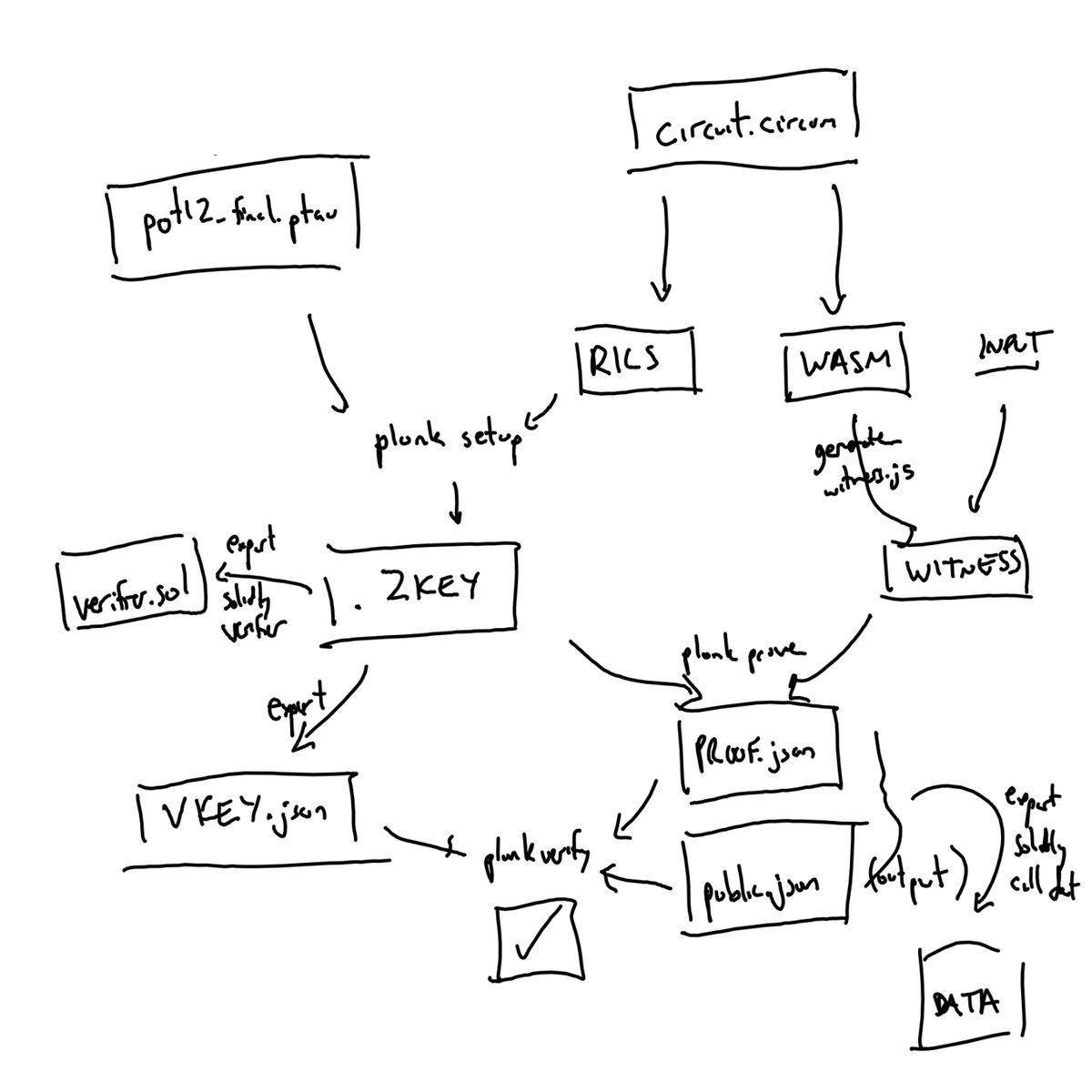
STEP 1: CREATE ZKEY
The constraints above would give us a valid proof, but not a zero knowledge one.
For that to be possible, we need to precompute a set of values from a random input, and then discard that random input (“toxic waste”).
The constraints above would give us a valid proof, but not a zero knowledge one.
For that to be possible, we need to precompute a set of values from a random input, and then discard that random input (“toxic waste”).
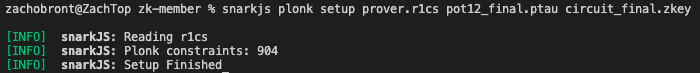
Enter the Powers of Tau ceremony. You can download the results from @0xPolygonHermez: hermez.s3-eu-west-1.amazonaws.com/powersOfTau28_…
This output is combined with your constraints file to create a zkey that holds all the cryptographic setup necessary to create proofs for your specific circuit.
This output is combined with your constraints file to create a zkey that holds all the cryptographic setup necessary to create proofs for your specific circuit.
STEP 2: CALCULATE WITNESS
On the other side of things, we also have to calculate the witness (all the intermediate values of running the function).
snarkjs makes this very easy to do in one command. They have wasm code for smaller files, or efficient C++ code for larger ones.
On the other side of things, we also have to calculate the witness (all the intermediate values of running the function).
snarkjs makes this very easy to do in one command. They have wasm code for smaller files, or efficient C++ code for larger ones.
STEP 3: CREATE THE PROOF
Now, with the combination of the witness and the zkey, we’re able to create the proof.
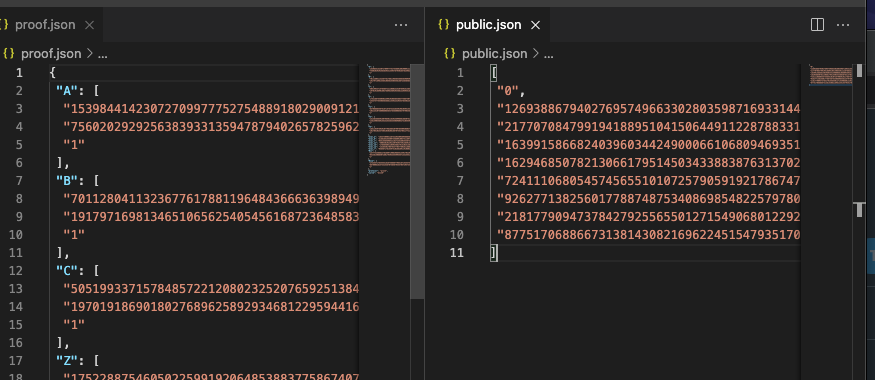
We plug them both into snarkjs and it outputs a proof.json (the numbers constituting the proof) and public.json (the public inputs to confirm).
Now, with the combination of the witness and the zkey, we’re able to create the proof.
We plug them both into snarkjs and it outputs a proof.json (the numbers constituting the proof) and public.json (the public inputs to confirm).
STEP 4: VERIFY
Finally, we can export a verification key from the zkey and pass that to anyone, along with our proof and public files, to verify our proof.
(You can even run one command to export the verification key as a Solidity file, so proofs can be verified on chain.)
Finally, we can export a verification key from the zkey and pass that to anyone, along with our proof and public files, to verify our proof.
(You can even run one command to export the verification key as a Solidity file, so proofs can be verified on chain.)

USE CASES
Beyond rollups, the possibilities for ZK proofs open the door to a lot of ideas.
A question to ask:
What things true, but are currently hard to prove because it'd require disclosing sensitive information?
Beyond rollups, the possibilities for ZK proofs open the door to a lot of ideas.
A question to ask:
What things true, but are currently hard to prove because it'd require disclosing sensitive information?
- What if you could provide a proof that X members of Congress support an idea, without them disclosing who they are?
- What if you could share facts from your medical records without showing them?
- What if you could share facts from your medical records without showing them?
- What if you could provide the proofs you need to get a mortgage without turning over all your financial information to the bank?
- What if you could have blockchain transactions stay secret while in the mempool to avoid MEV and only get revealed once blocks were created?
- What if you could have blockchain transactions stay secret while in the mempool to avoid MEV and only get revealed once blocks were created?
CHALLENGES
Getting into the weeds gave me a better sense of the challenges with this tech:
1) Translation: Translating code into circom’s language (which only allows multiplication and addition) is really tough, especially for complex programs.
Getting into the weeds gave me a better sense of the challenges with this tech:
1) Translation: Translating code into circom’s language (which only allows multiplication and addition) is really tough, especially for complex programs.
I can only imagine how hard creating a general purpose EVM would be.
That said, circuit design languages like circom are well suited for creating small building blocks and then abstracting them as we build more complex things. We’ll get there.
That said, circuit design languages like circom are well suited for creating small building blocks and then abstracting them as we build more complex things. We’ll get there.
2) Signature Schemes: ECDSA signatures are usually efficient, but they use a lot of binary, which is inefficient for SNARKs.
Alternate hash functions (like MiMC) that work better, but the incompatibility between these two formats makes a lot of fun use cases more challenging.
Alternate hash functions (like MiMC) that work better, but the incompatibility between these two formats makes a lot of fun use cases more challenging.
3) Efficiency: A lot of these schemes are still incredibly computationally difficult.
This is an extra problem when proofs are expected to be created on the front end.
This is an extra problem when proofs are expected to be created on the front end.
https://twitter.com/0xB07DAD/status/1493336351453765638
I’ll wrap it up there. This is just the tip of the iceberg, but I’m definitely hooked.
If you’re interested in this stuff, shoot me a message. I’m planning to keep going deeper and try to build something useful with this tech in the coming weeks.
If you’re interested in this stuff, shoot me a message. I’m planning to keep going deeper and try to build something useful with this tech in the coming weeks.
• • •
Missing some Tweet in this thread? You can try to
force a refresh



