A thread on the (suspected) Okta compromise from an incident response perspective 🧵
#okta #LAPSUS$ #dfir #incidentresponse
#okta #LAPSUS$ #dfir #incidentresponse
1. Collect and preserve all Okta logs, focus on the Okta System Log as it's the main audit trail for Okta activities
Need more info on this log check (developer.okta.com/docs/reference…)
Need more info on this log check (developer.okta.com/docs/reference…)
2. Search your audit log for suspicious activity focus on your superuser/admin Okta accounts as they pose the largest risk
3. Rotate passwords for high-privileged accounts, at this stage it might be a bit early to rotate passwords for all users
4. If you outsource (parts) of your Okta deployment check in with your vendor and make sure what 3rd party admin accounts are used and ask them for support
5. Check if you currently have Okta support access enabled, you might want to disable that for the time being more info (help.okta.com/oie/en-us/Cont…)
6. Check for (privileged) accounts created around the time of the suspected breach - 21 January 2022
7. The CEO of Okta, just posted the following statement related to the alleged breach:
https://twitter.com/toddmckinnon/status/1506184721922859010
Check out some SIEM rules by @blueteamblog that you can use to search for Okta behavior
https://twitter.com/blueteamblog/status/1506176104985411587thanks for sharing!=
10. Piece by @josephfcox from Vice on the hack vice.com/en/article/jgm… in short screenshots in Telegram most likely related to 3rd party breach from January 2022 which was already investigated and resolved 👀
12. - "no evidence to date".. are they still investigating? Will there be updates later..
13. No further update at this moment in time, we are awaiting further information from Okta or other parties involved.
14. Some overlap with the earlier shared sigma/elastic security rules, but this is a nice repository with Okta security events for your hunting/log analysis by @hevnsnt thanks for sharing!
https://twitter.com/hevnsnt/status/1506309932735475714
15. Updated statement by Okta see: okta.com/blog/2022/03/u…
16. Looking at the positive side, this might all be less serious. This is a strong statement to make. 

17. However it can also be interpreted as contradictory with the bottom half of the statement as their might be impact for some customers. Our advice stay vigilant and keep an eye on the updates coming out of the Okta investigation. 

19. Statement is from their Telegram group t.me/minsaudebr
20. Without inside knowledge we cannot really comment on the statement of LAPSUS$ itself. LAPSUS$ also recommends Okta hiring @Mandiant which is excellent advice, if they're too busy please let us know 😉
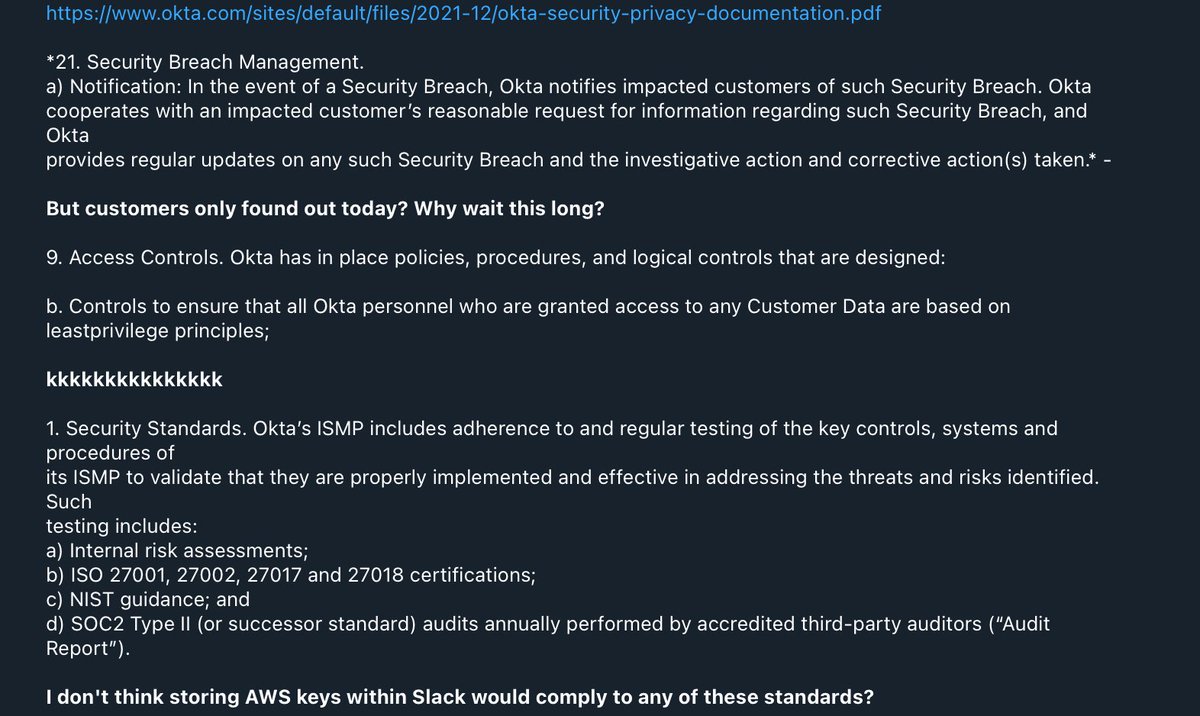
21. Okta has provided additional details in their statement (okta.com/blog/2022/03/u…) Most important from the statement in our opinion:
- 2,5% of clients impacted they are already contacted
- There will be a webinar by Okta's CSO on the incident, link to register in post.
- 2,5% of clients impacted they are already contacted
- There will be a webinar by Okta's CSO on the incident, link to register in post.

• • •
Missing some Tweet in this thread? You can try to
force a refresh