
Today CERT-UA released two new posts on recent attacks on Ukraine Gov and enterprises.
- UAC-0026 Delivering HeaderTip.
cert.gov.ua/article/38097
- UAC-0088 Attacks with DoubleZero Wiper.
cert.gov.ua/article/38088
Follow along for a quick thread:
🧵1/x
- UAC-0026 Delivering HeaderTip.
cert.gov.ua/article/38097
- UAC-0088 Attacks with DoubleZero Wiper.
cert.gov.ua/article/38088
Follow along for a quick thread:
🧵1/x

@AeonTimeline 2/x: (threads are hard, sorry)
First lets look at UAC-0026:
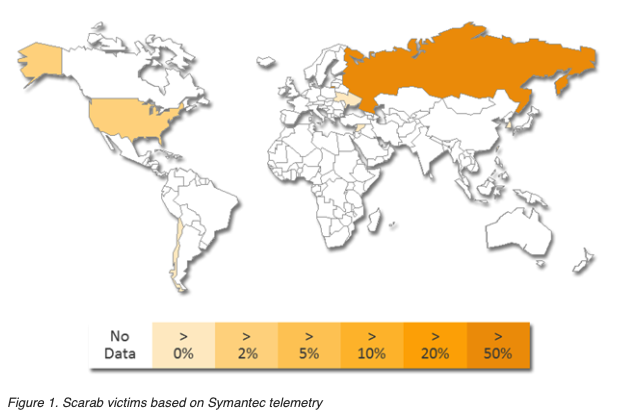
Some (including me at first) are associating this with Symantec 2015's post on "Scarab", who was active since 2012.
At the time they were known to target a very small amount of individuals of interest (see map)
First lets look at UAC-0026:
Some (including me at first) are associating this with Symantec 2015's post on "Scarab", who was active since 2012.
At the time they were known to target a very small amount of individuals of interest (see map)
@AeonTimeline 3/x:
Here is Symantecs old blog: web.archive.org/web/2015012402…
Unfortunately the IOC file is no longer hosted there. Luckily our friends at AT&T (Alienvault OTX) pulled the IOCs back when that blog was posted: otx.alienvault.com/pulse/54c7e1e8…
Here is Symantecs old blog: web.archive.org/web/2015012402…
Unfortunately the IOC file is no longer hosted there. Luckily our friends at AT&T (Alienvault OTX) pulled the IOCs back when that blog was posted: otx.alienvault.com/pulse/54c7e1e8…
@AeonTimeline 4/x:
So what links these two?
First look at IOCs alone is the domain mrbasic[.]com. However thats just dyndns and used by many unrelated actors over the years. mrbasic[.]com subdomains should not be considered related.
So what links these two?
First look at IOCs alone is the domain mrbasic[.]com. However thats just dyndns and used by many unrelated actors over the years. mrbasic[.]com subdomains should not be considered related.
@AeonTimeline 5/x:
So IMO based on infra, UAC-0026 != Scarab APT.
Looking at the samples may yield better linkage, but I'm not quite finding anything confident enough link the two.
Its also noteworthy to point out CERT-UA noted similar in Sept 2020. Hmm anyone got that?
So IMO based on infra, UAC-0026 != Scarab APT.
Looking at the samples may yield better linkage, but I'm not quite finding anything confident enough link the two.
Its also noteworthy to point out CERT-UA noted similar in Sept 2020. Hmm anyone got that?
@AeonTimeline Taking a look at the files from CERT-UA:
1af894a5f23713b557c23078809ed01c
Про збереження відеоматеріалів з фіксацією злочинних дій армії російської федерації.rar
"About preservation of video materials with fixing of criminal actions of army of the Russian Federation.rar"
1af894a5f23713b557c23078809ed01c
Про збереження відеоматеріалів з фіксацією злочинних дій армії російської федерації.rar
"About preservation of video materials with fixing of criminal actions of army of the Russian Federation.rar"
@AeonTimeline 7/x:
That RAR includes an EXE:
13612c99a38b2b07575688c9758b72cc
Ah and here are the pivots to the September 2020 activity..
That RAR includes an EXE:
13612c99a38b2b07575688c9758b72cc
Ah and here are the pivots to the September 2020 activity..
@AeonTimeline 8/x:
So 13612c99a38b2b07575688c9758b72cc (our CERT-UA share) has lots of references to officecleaner.dat as they noted.
However go pivot on:
set objfile=%temp%\httpshelper.dll
and you run into 0e87736d289505407a2c5e467356e72a from late 2021. meh.. but..
So 13612c99a38b2b07575688c9758b72cc (our CERT-UA share) has lots of references to officecleaner.dat as they noted.
However go pivot on:
set objfile=%temp%\httpshelper.dll
and you run into 0e87736d289505407a2c5e467356e72a from late 2021. meh.. but..

@AeonTimeline 9/x:
it makes use of officecleaner.dll -- oh that makes sense. Here we can now pivot with that to our September 2020 activity:
Bin: 6947b8f80551f0ce0ea98687deab18e5
DLL: acd062593f70c00e310c47a3e7873df4
XLS: d25ff61103b6e817f63838e66f177a6b
Joining Instructions IMPC 1.20 .xls
it makes use of officecleaner.dll -- oh that makes sense. Here we can now pivot with that to our September 2020 activity:
Bin: 6947b8f80551f0ce0ea98687deab18e5
DLL: acd062593f70c00e310c47a3e7873df4
XLS: d25ff61103b6e817f63838e66f177a6b
Joining Instructions IMPC 1.20 .xls
@AeonTimeline ebook.port25[.]biz
Ah and here is the sept. 2020 RAR they probably emailed out like our most recent activity:
bcb6387516de9160330c38cb78320958
Joining Instructions IMPC 1.20 .rar
Ah and here is the sept. 2020 RAR they probably emailed out like our most recent activity:
bcb6387516de9160330c38cb78320958
Joining Instructions IMPC 1.20 .rar
12/x:
Okay so looking at httpshelper on both cases, they are very similar. This is HeaderTip according to CERT-UA.
acd062593f70c00e310c47a3e7873df4 (Sept 2020)
1aba36f72685c12e60fb0922b606417c (Mar 2022)
Both are very similar...
Okay so looking at httpshelper on both cases, they are very similar. This is HeaderTip according to CERT-UA.
acd062593f70c00e310c47a3e7873df4 (Sept 2020)
1aba36f72685c12e60fb0922b606417c (Mar 2022)
Both are very similar...
13/x:
That leads us to others similar:
675ea1e99cbb9699dd4434aa54c3504c (June 2021)
8cbff18f49c3ca0a98309070f6533967 (June 2021)
e4c38e8aaea8a1120127031ccfcfe7d6 (March 2021)
BTW these dates are basic on earliest public ver (VT mostly)
That leads us to others similar:
675ea1e99cbb9699dd4434aa54c3504c (June 2021)
8cbff18f49c3ca0a98309070f6533967 (June 2021)
e4c38e8aaea8a1120127031ccfcfe7d6 (March 2021)
BTW these dates are basic on earliest public ver (VT mostly)
So again this is just VT, and well.. your telemetry may tell a different story, but UAC-0026 has been pushing around HeaderTip since at least Sept. 2020, with clues to something happening early-mid 2021 with them too.
What is "IMPC" and why would I want to join it in sept 2020?
What is "IMPC" and why would I want to join it in sept 2020?
15/x:
IDK I'm just guessing here but:
International Mineral Processing Congress?
Anyways here is the C2 from the the other HeaderTip sample above: dynamic.ddns[.]mobi
IDK I'm just guessing here but:
International Mineral Processing Congress?
Anyways here is the C2 from the the other HeaderTip sample above: dynamic.ddns[.]mobi
16/x:
That dynamic.ddns[.]mobi brings us to yet another pivot. This time back to 2018:
b5f2cc8e8580a44a6aefc08f9776516a
Which brings us to Scarab known infra from the Symantec blog at the top of this thread. Didn't expect that!
That dynamic.ddns[.]mobi brings us to yet another pivot. This time back to 2018:
b5f2cc8e8580a44a6aefc08f9776516a
Which brings us to Scarab known infra from the Symantec blog at the top of this thread. Didn't expect that!
17/x:
So TLDR: UAC-0026 is indeed #Scarab APT. Disregard my previous comment on them not being the same.
So TLDR: UAC-0026 is indeed #Scarab APT. Disregard my previous comment on them not being the same.
18/x:
#HeaderTip IOCs:
1aba36f72685c12e60fb0922b606417c, March 2022
675ea1e99cbb9699dd4434aa54c3504c, June 2021
8cbff18f49c3ca0a98309070f6533967, May 2021
e4c38e8aaea8a1120127031ccfcfe7d6, March 2021
acd062593f70c00e310c47a3e7873df4, Sept 2020
#HeaderTip IOCs:
1aba36f72685c12e60fb0922b606417c, March 2022
675ea1e99cbb9699dd4434aa54c3504c, June 2021
8cbff18f49c3ca0a98309070f6533967, May 2021
e4c38e8aaea8a1120127031ccfcfe7d6, March 2021
acd062593f70c00e310c47a3e7873df4, Sept 2020
19/19: Closing remarks:
As expected, CN isn’t far behind on spying in Ukraine.
As expected, CN isn’t far behind on spying in Ukraine.
• • •
Missing some Tweet in this thread? You can try to
force a refresh



