1️⃣ Search for secret API keys publicly exposed on websites :
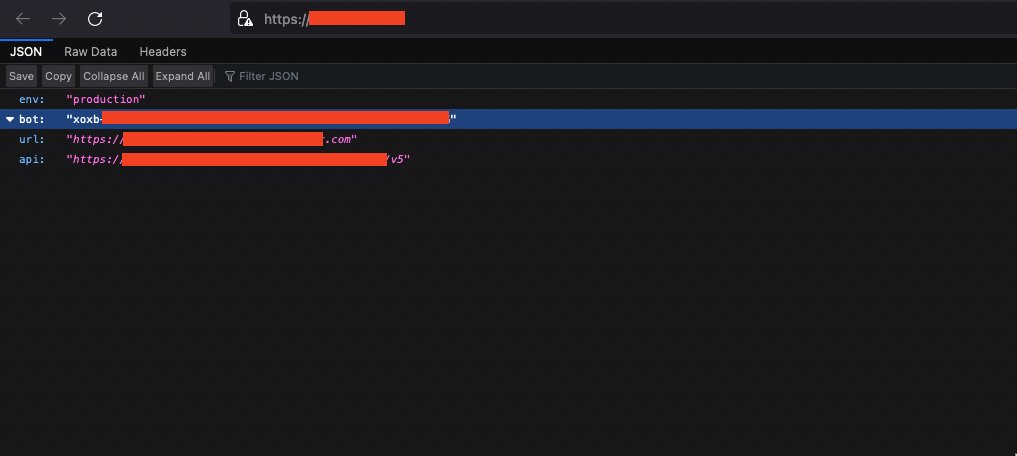
ex : Searching for slack API token on all the scanned websites
http.html:"xoxb-"

ex : Searching for slack API token on all the scanned websites
http.html:"xoxb-"

2️⃣ Search using 'favicon' hash :
- One of the most accurate way of finding services
ex- Find all jenkins server : http.favicon.hash:81586312
A list of favicon hashes : github.com/sansatart/scra…
shodan.io/search?query=h…

- One of the most accurate way of finding services
ex- Find all jenkins server : http.favicon.hash:81586312
A list of favicon hashes : github.com/sansatart/scra…
shodan.io/search?query=h…


4️⃣ Search services vulnerable to a particular CVE :
ex - Search all machines vulnerable to 'eternal blue'. vuln:ms17-010
or
Search a particular CVE :
ex - Services that are vulnerable to Heartbleed
vuln:CVE-2014-0160
Note:This is only available to users of higher API plan
ex - Search all machines vulnerable to 'eternal blue'. vuln:ms17-010
or
Search a particular CVE :
ex - Services that are vulnerable to Heartbleed
vuln:CVE-2014-0160
Note:This is only available to users of higher API plan

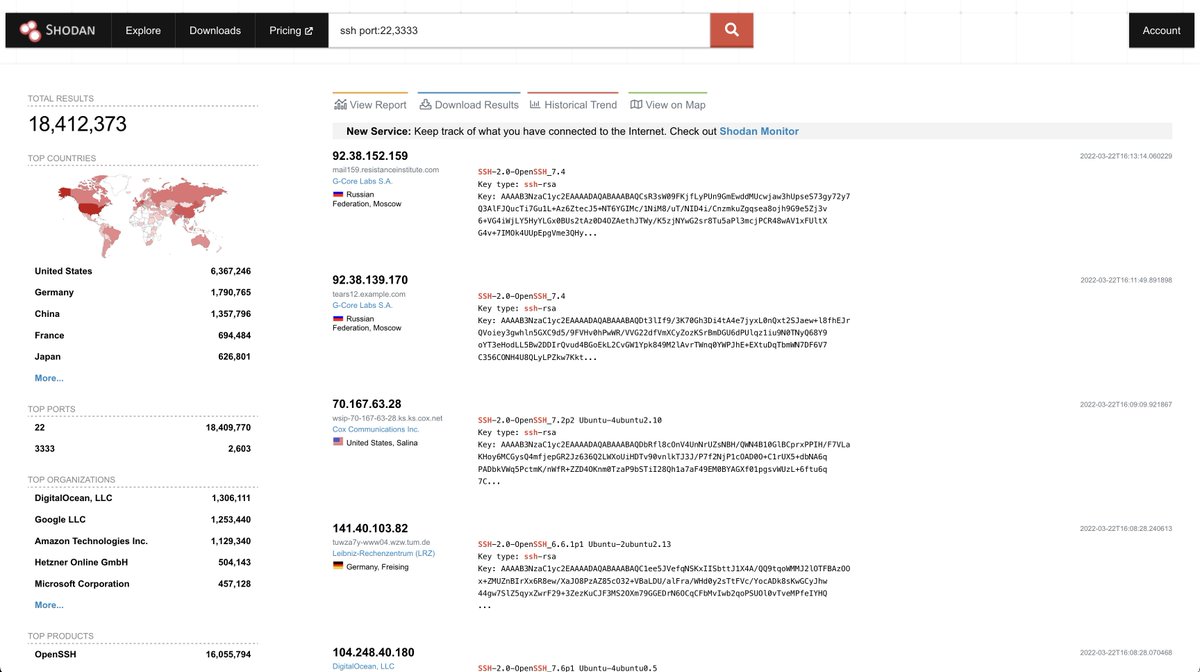
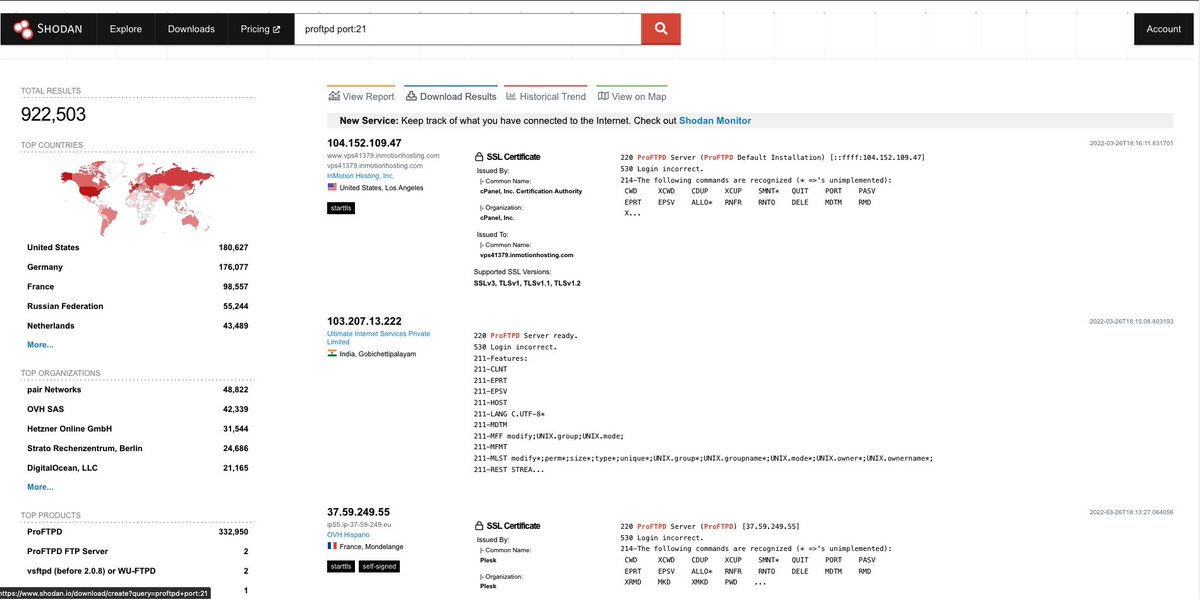
5️⃣ Search for a particular port + service :
ex - SSH on port 22 or 3333
ssh port:22,3333
or
proftpd port:21
You can use this to find services on non-standard port.
Like : ssh -port:22
ssh which is not on port 22


ex - SSH on port 22 or 3333
ssh port:22,3333
or
proftpd port:21
You can use this to find services on non-standard port.
Like : ssh -port:22
ssh which is not on port 22

6️⃣ Search for a particular OS :
e.g. Checking for vulnerable win 10 home version
os:"Windows 10 Home 19041"
e.g. Checking for vulnerable win 10 home version
os:"Windows 10 Home 19041"

7️⃣ Combine filters to generate more targeted results
e.g. All windows 7 machines in India
country:"IN" os:"windows 7"
e.g. All windows 7 machines in India
country:"IN" os:"windows 7"

• • •
Missing some Tweet in this thread? You can try to
force a refresh