NEW on #Log4Shell...
Horde of miner bots and backdoors leveraged #Log4J to attack VMware Horizon servers
1/14
Horde of miner bots and backdoors leveraged #Log4J to attack VMware Horizon servers
1/14

In the wake of December 2021 exposure of a remote code execution vulnerability (dubbed “Log4Shell”) in the ubiquitous Log4J Java logging library, we tracked widespread attempts to scan for and exploit the weakness—particularly among cryptocurrency mining bots. 2/14
The vulnerability affected hundreds of software products, making it difficult for some organizations to assess their exposure. 3/14
One of the products affected was VMware Horizon, a desktop and application virtualization platform that became part of the solution for some organizations’ work-from-home needs prior to and during office shutdowns over the past two years. 4/14
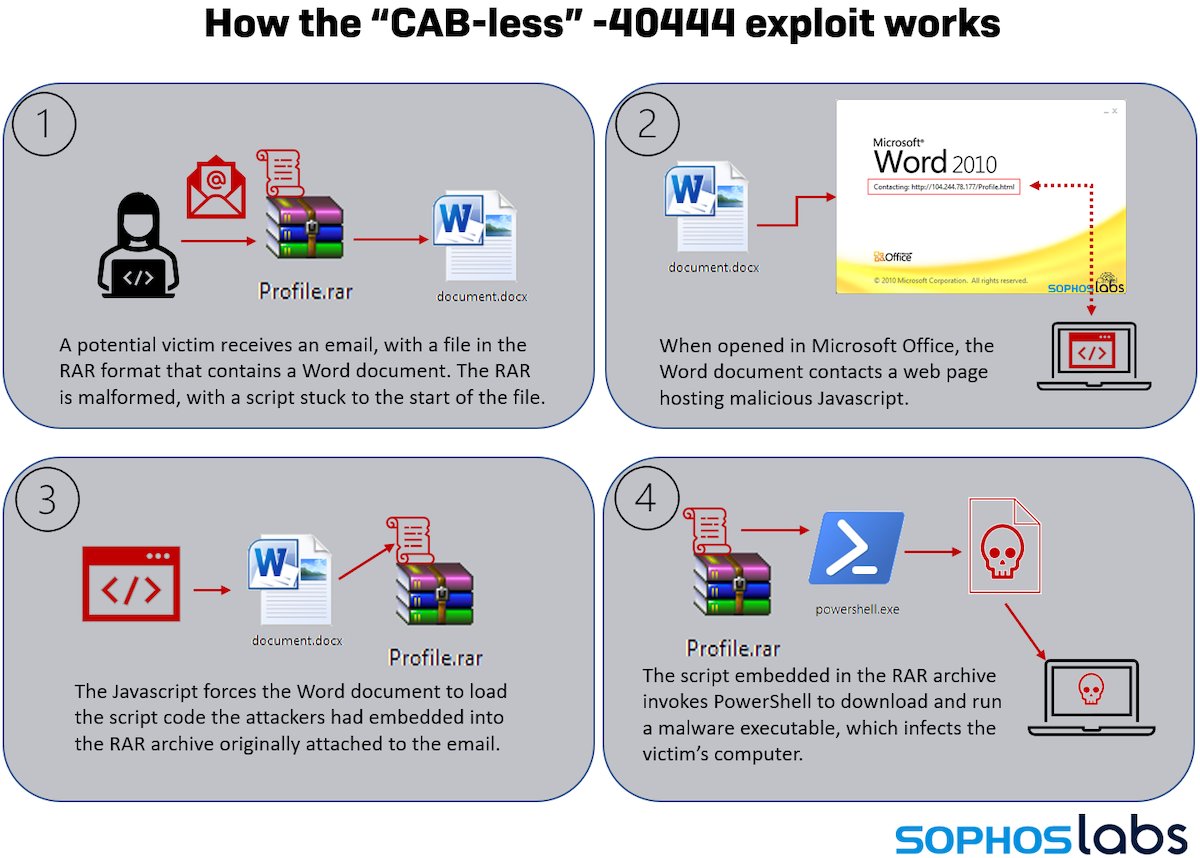
In late December 2021 and in January 2022, there were multiple reports of active exploitation of the Log4Shell vulnerability in VMware Horizon servers. The attack used the Lightweight Directory Access Protocol resource call of Log4J to... 5/14
...retrieve a malicious Java class file that modified existing legitimate Java code, adding a web shell that provided remote access and code execution to the attackers. SophosLabs has observed these attacks in customer telemetry since the beginning of January. 6/14
Attempts to leverage Horizon, which continued throughout January, were frequently associated with attempts to deploy cryptocurrency mining malware; others had less clear motives and may be associated with initial access brokers or ransomware actors. These attacks continue. 7/14
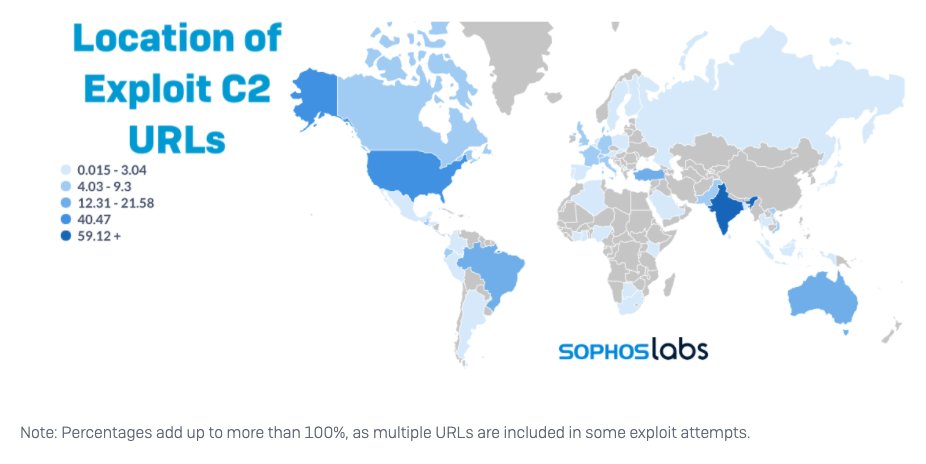
The initial attempts on January 10 came from command and control servers at api[.]rogerscorp[.]org (since sink-holed) and 45[.]32.125.79. The next day, the server was changed to 185.112.83.116; this was kept in use for a larger wave of attacks on January 14. 8/14
Some of these used Cobalt Strike to stage and execute the cryptominer payloads.
The largest wave of Log4J attacks aimed at Horizon that we have detected began January 19, and is still ongoing. 9/14
The largest wave of Log4J attacks aimed at Horizon that we have detected began January 19, and is still ongoing. 9/14
This wave did not rely on Cobalt Strike; instead, the cryptominer installer script is directly executed from the Apache Tomcat component of the Horizon server. The most frequently used server in these campaigns is 80.71.158.96. 10/14
Organizations should thoroughly research their exposure to potential Log4J vulnerabilities, as they may impact commercial, open-source and custom software that in some cases may not have regular security support. 11/14
Organizations should also ensure they have defense in depth in place to detect and block malicious activity of all types on servers and clients. Even after patches are applied, a full assessment of previously vulnerable systems for other potential malware or compromise. 12/14
@Sophos detects the Windows miners listed in this article, as well as the behaviors related to the scripts used as droppers and backdoors.
A full list of indicators of compromise for the Horizon-related malware attacks we have investigated is available on our GitHub page. 13/14
A full list of indicators of compromise for the Horizon-related malware attacks we have investigated is available on our GitHub page. 13/14
See all the details, including the infection process, from @GaborSzappanos and @thepacketrat: news.sophos.com/en-us/2022/03/…
14/14
14/14
• • •
Missing some Tweet in this thread? You can try to
force a refresh