
4/8/22 #bugbountydiary #bugbountytips
Everyone is sick in the house but I had some running scans I needed to check up on.
I found a SQL injection bug on a blog.
Here's how I did it, so you can learn...
👇
🚨Like, retweet, & follow for more hacker tips!🚨
1/x
Everyone is sick in the house but I had some running scans I needed to check up on.
I found a SQL injection bug on a blog.
Here's how I did it, so you can learn...
👇
🚨Like, retweet, & follow for more hacker tips!🚨
1/x
Firstly, I ran reconFTW on a set of domains related to the target. I had the main domain, and several acquisition domains running too. The acquisitions were gathered from CrunchBase and Wikipedia.
This gave me a pretty good list of targets.
2/x
github.com/six2dez/reconf…
This gave me a pretty good list of targets.
2/x
github.com/six2dez/reconf…
ReconFTW runs screenshotting on all web-resolvable domains and subdomains.
I opened that folder and saw what looked to be a marketing campaign site that was super old for a product the company no longer supported. To further confirm the Copyright footer was from 2016
3/x
I opened that folder and saw what looked to be a marketing campaign site that was super old for a product the company no longer supported. To further confirm the Copyright footer was from 2016
3/x
This means the site hasn't seen much love in a while.
I browsed the site and immediately saw paths that were WordPress.
When hacking WordPress, the defacto is using a tool called WPScan (@_WPScan_ ).
4/x
I browsed the site and immediately saw paths that were WordPress.
When hacking WordPress, the defacto is using a tool called WPScan (@_WPScan_ ).
4/x
WPScan identified some, but not all, of the plugins.
ReconFTW (by @Six2dez1 ) also runs all spidered URLs through pattern matching.
They use gf by @TomNomNom to do this matching.
github.com/tomnomnom/gf
6/x
ReconFTW (by @Six2dez1 ) also runs all spidered URLs through pattern matching.
They use gf by @TomNomNom to do this matching.
github.com/tomnomnom/gf
6/x
The patterns fed to gf are from a talk I did at @defcon called "Hunt: Data Driven Web Hacking & Manual Testing"
This project statistically identified the most susceptible parameters to certain types of security vulns. You can watch the talk here:
7/x
This project statistically identified the most susceptible parameters to certain types of security vulns. You can watch the talk here:
7/x
The output of gf and the patterns (tied together by ReconFTW) showed me several path/parameters for a plugin that WPScan *didn't* identify.
Several of the parameters had the nomenclature "id" in them.
8/x
Several of the parameters had the nomenclature "id" in them.
8/x
I always test "ID" parameters because I associate them with database interaction. The same with any of these:
github.com/1ndianl33t/Gf-…
Sure enough, inserting a:
'
into one caused an error and inserting two ' did not.
A classic old-school SQL injection sign.
9/x
github.com/1ndianl33t/Gf-…
Sure enough, inserting a:
'
into one caused an error and inserting two ' did not.
A classic old-school SQL injection sign.
9/x
I'd like to say that I did the rest of the injection to prove impact manually, but I didn't.
I used @sqlmap , which is the best-in-breed tool for testing SQL Injection. You can learn more about it here:
github.com/sqlmapproject/…
10/x
I used @sqlmap , which is the best-in-breed tool for testing SQL Injection. You can learn more about it here:
github.com/sqlmapproject/…
10/x
I also wanted to give a complete picture as to what parameters (there were a lot) were injectable.
I passed the URLs as a file to sqlmap with something like this, which found a couple more params vulnerable.
11/x
I passed the URLs as a file to sqlmap with something like this, which found a couple more params vulnerable.
11/x
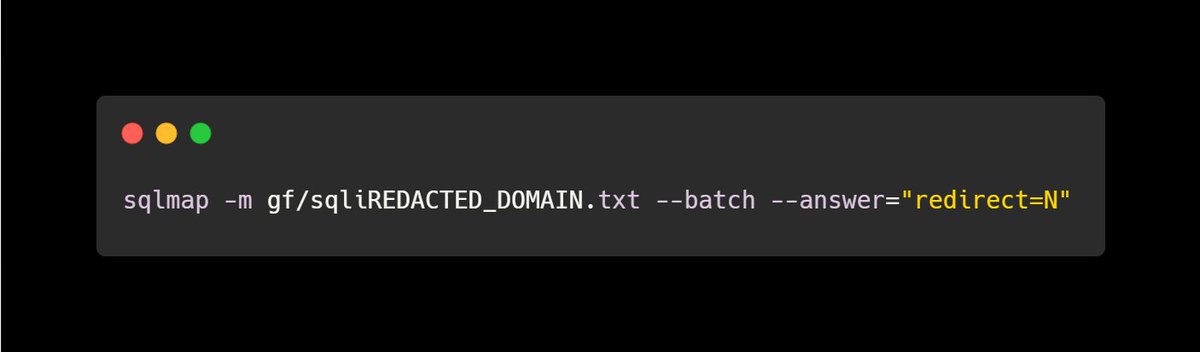
Blog or not, this is my general strategy for finding SQL Injection bugs.
Hopefully, it's not a duplicate 🤞
🚨Like, retweet, & follow for more hacker tips!🚨
12/x
Hopefully, it's not a duplicate 🤞
🚨Like, retweet, & follow for more hacker tips!🚨
12/x
• • •
Missing some Tweet in this thread? You can try to
force a refresh




