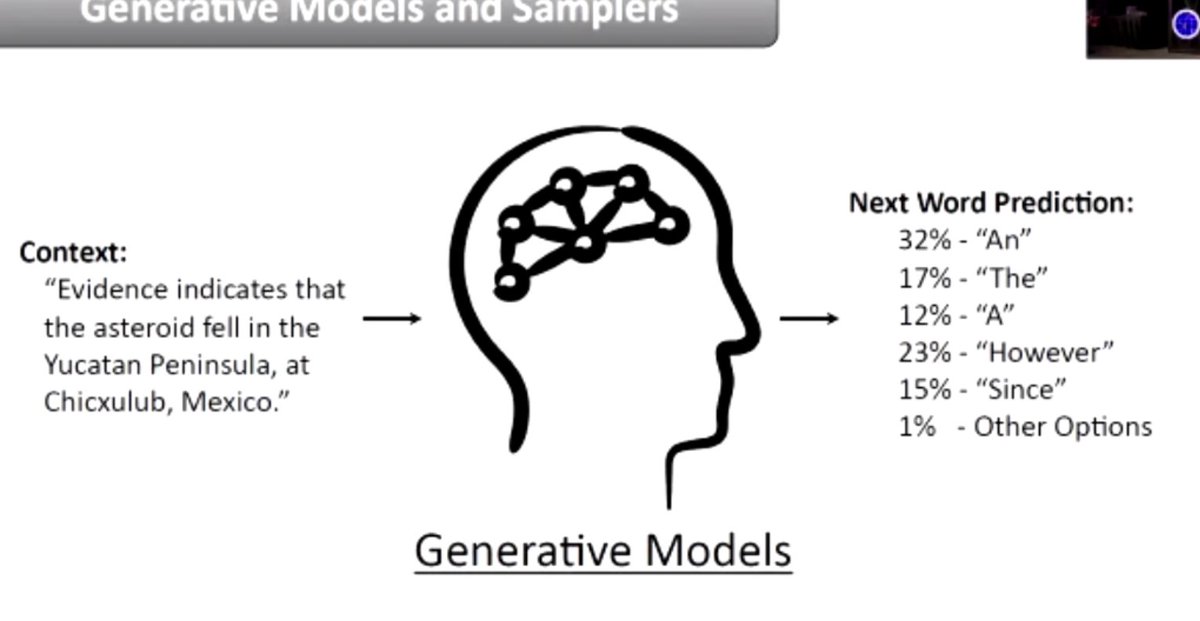
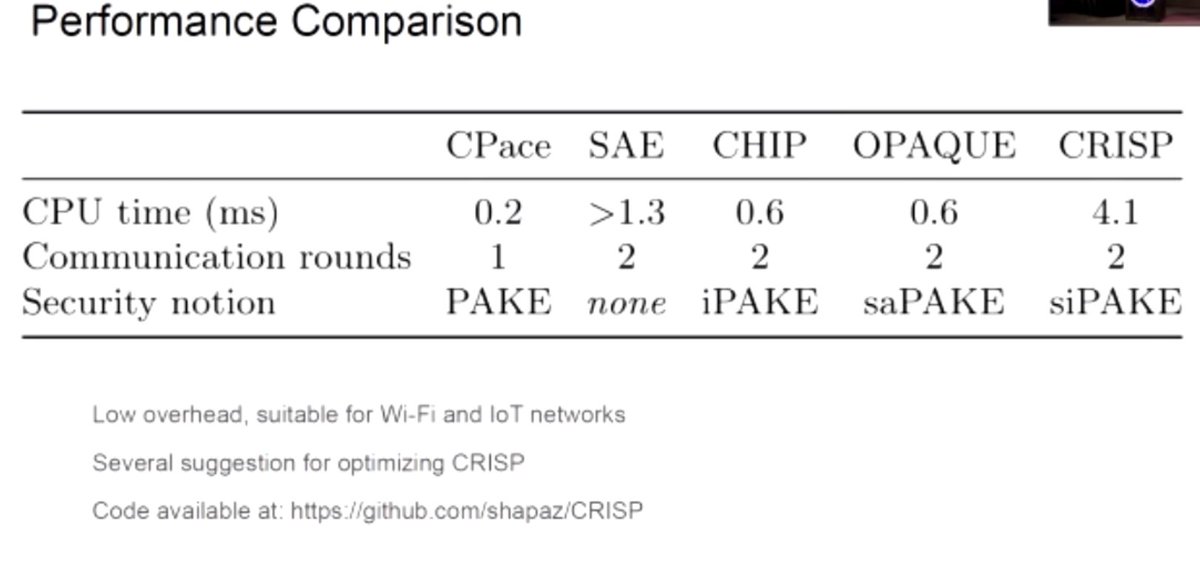
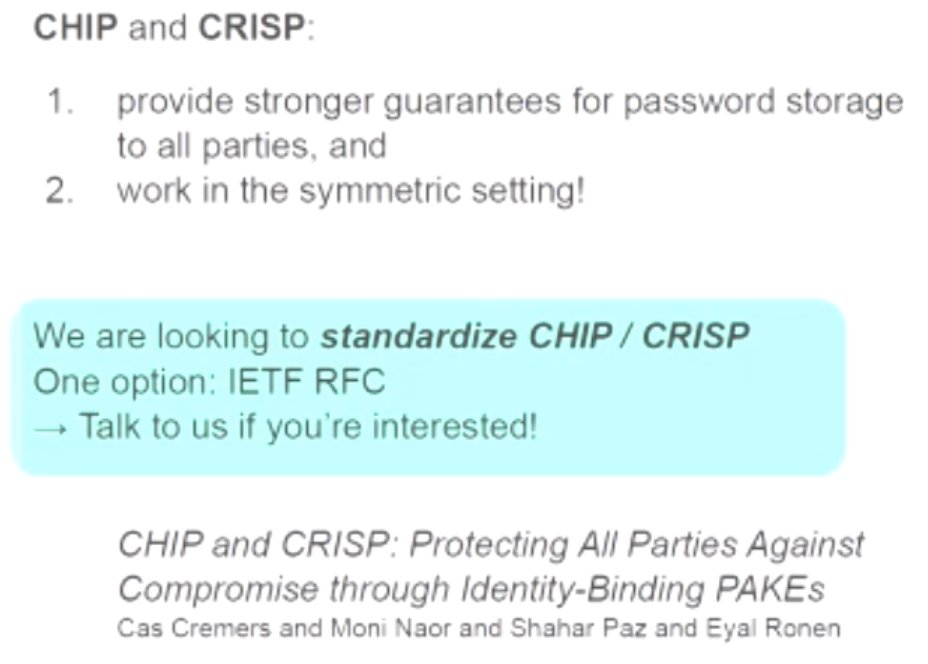
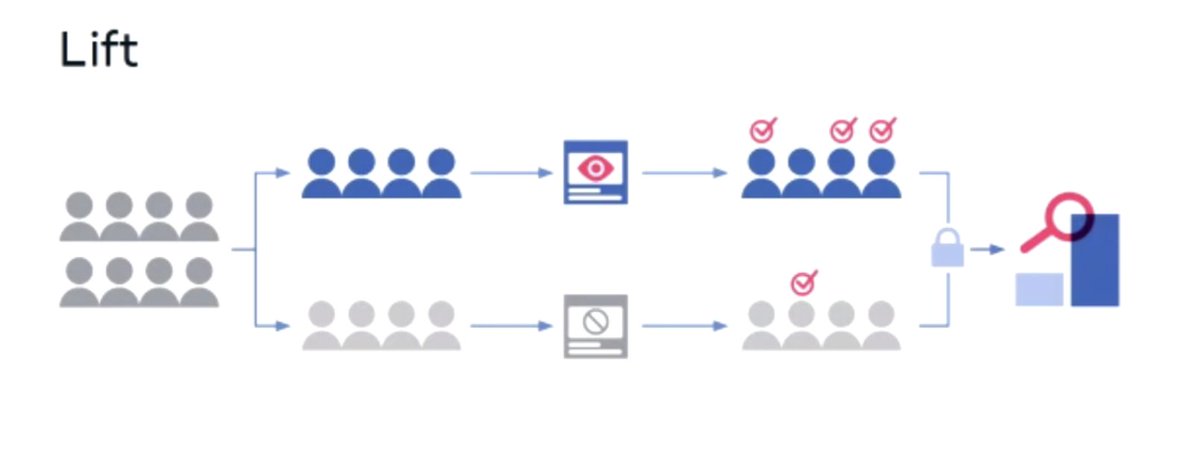
LIVE, IN THE FLESH, FROM AMSTERDAM, IT'S #REALWORLDCRYPTO!
@cryptojedi kicking off with logistics 

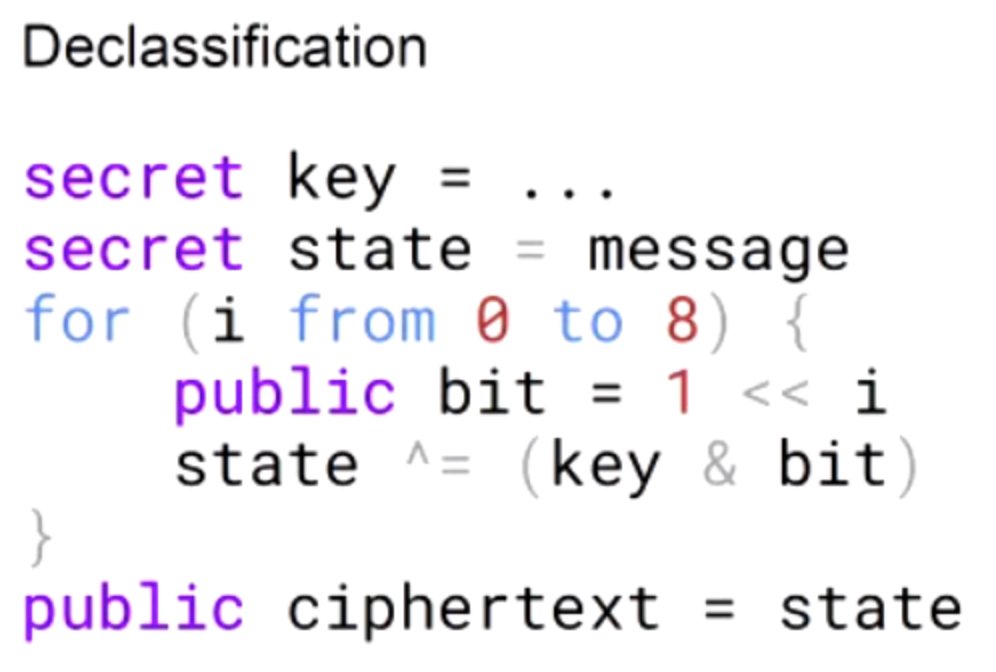
Kicking off with in fact, side channels: Spectre Declassified
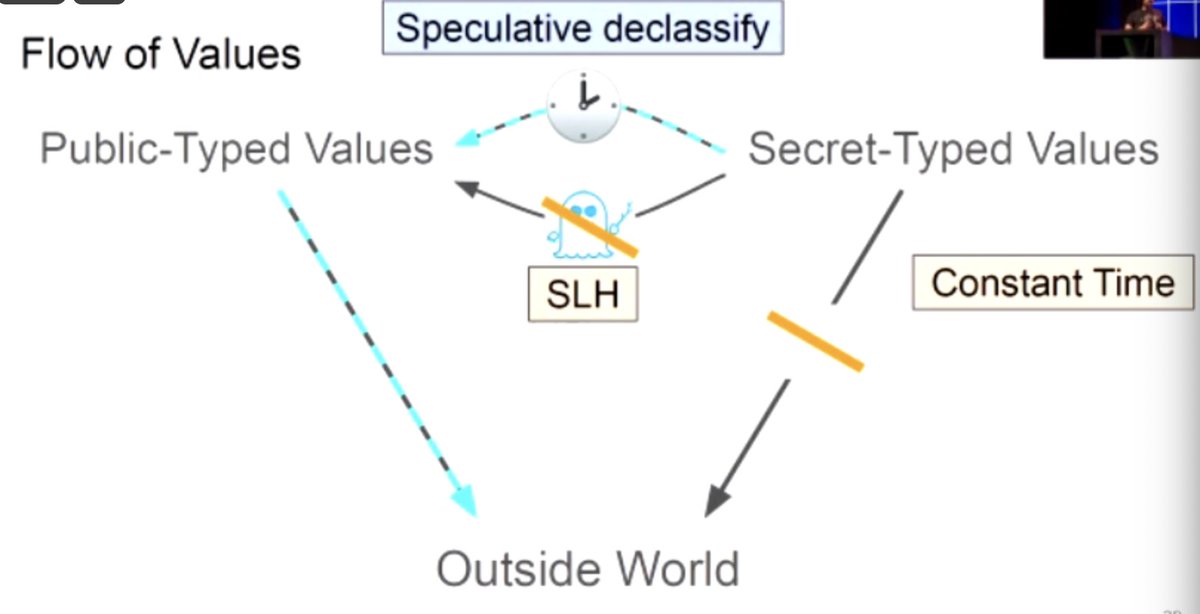
Spectre can smuggle a private-typed value into the public domain. Some mitigations, incl. speculative load hardening
#realworldcrypto
#realworldcrypto

Q: Declassify does a lot, what if a function used once is safe, but again is not (like involving a nonce), can this be enforced with the type system?
A: Declassifier would check somewhat but that's getting beyond our classifier type system
#realworldcrypto
A: Declassifier would check somewhat but that's getting beyond our classifier type system
#realworldcrypto
Q: Ensure instructions before the fence are correctly executed?
A: lfence() ensures the instructions before MUST be executed before the lfence
#realworldcrypto
A: lfence() ensures the instructions before MUST be executed before the lfence
#realworldcrypto
Q: All these attacks and mitigations feel like a cat and mouse game, should this be handled at the hardware level? Feels fragile on a micro/architectural change
A: Yesss? Need cooperation with vendors
#realworldcrypto
A: Yesss? Need cooperation with vendors
#realworldcrypto
Attacks that abuse timing leaks, but can be algorithmic, not hardware: branches / accesses that vary based on secret values
#realworldcrypto
#realworldcrypto
Often you have to ✨hope✨ that the compiler doesn't optimize away your constant time mitigations, tools can help check that they persist to machine code
#realworldcrypto
#realworldcrypto

@RustCryptoOrg Constant time algorithms, and kinda just, hoping, the compiler doesn't mess them up
#realworldcrypto
#realworldcrypto

Crypto competitions (like NIST PQC) should require / standardize constant-time code
#realworldcrypto
#realworldcrypto

Custom tools, but also custom languages, which devs don't like because of integration issues/effort
Big divide between compiler authors and crypto devs re side channels
#realworldcrypto
Big divide between compiler authors and crypto devs re side channels
#realworldcrypto
Q: Which of these tools are actively maintained and 'industry ready'?
A: *chuckle* a few; 5 actively maintained; some tools are used in CIs of crypto libraries of big libs like AWS S2N (// @colmmacc )
#realworldcrypto
A: *chuckle* a few; 5 actively maintained; some tools are used in CIs of crypto libraries of big libs like AWS S2N (// @colmmacc )
#realworldcrypto
Q: Which tools would fit the trusted execution environment?
A: Depends if you have access to the code, or the binary, 'most' should work
#realworldcrypto
A: Depends if you have access to the code, or the binary, 'most' should work
#realworldcrypto
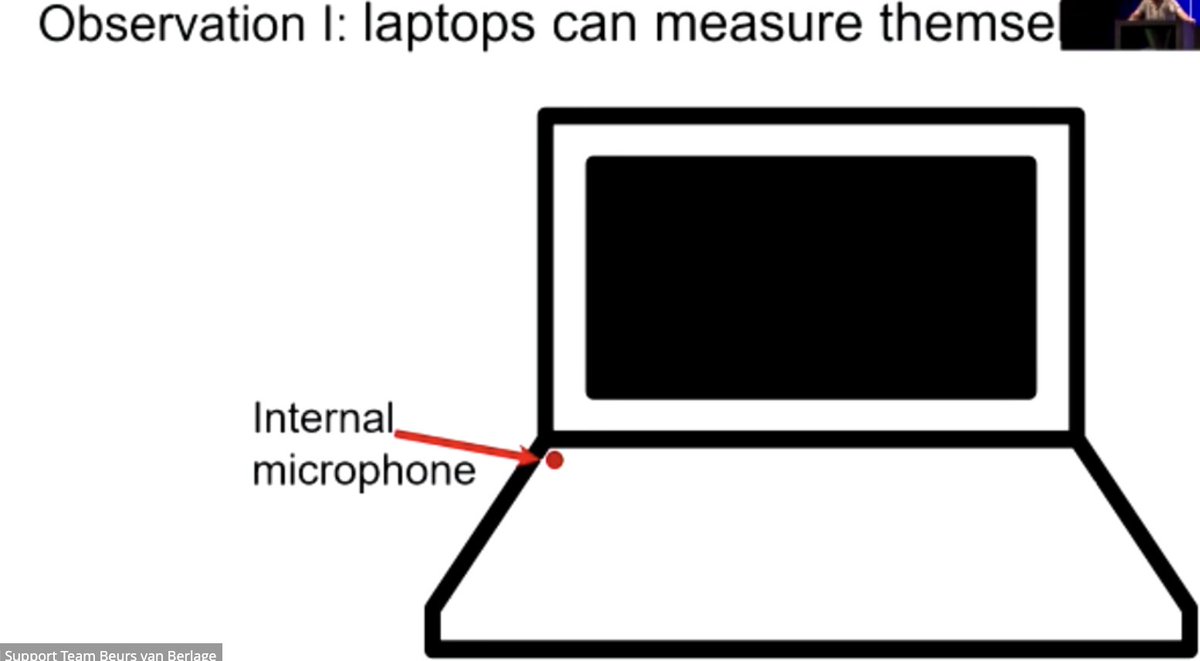
Next up, "Lend Me Your Ear: Passive Remote Physical Side Channels on PCs ", presented by Daniel Genkin and Roei Schuster
#realworldcrypto
#realworldcrypto

Building on Elie's work, using DNN's trained on power analyses to classify new traces and save humans lots of work
#realworldcrypto
#realworldcrypto
"This is the first example of a physical attack running across the internet, without the target running attack code." YEAH.
#realworldcrypto
#realworldcrypto
Q: Did you find adding noise makes it hard for the DNN to detect?
A: Possible, did an experiment with interference, really trying to introduce truly random noise (not human white noise) can help ,attack is only 94%, can lower accuracy
#realworldcrypto
A: Possible, did an experiment with interference, really trying to introduce truly random noise (not human white noise) can help ,attack is only 94%, can lower accuracy
#realworldcrypto
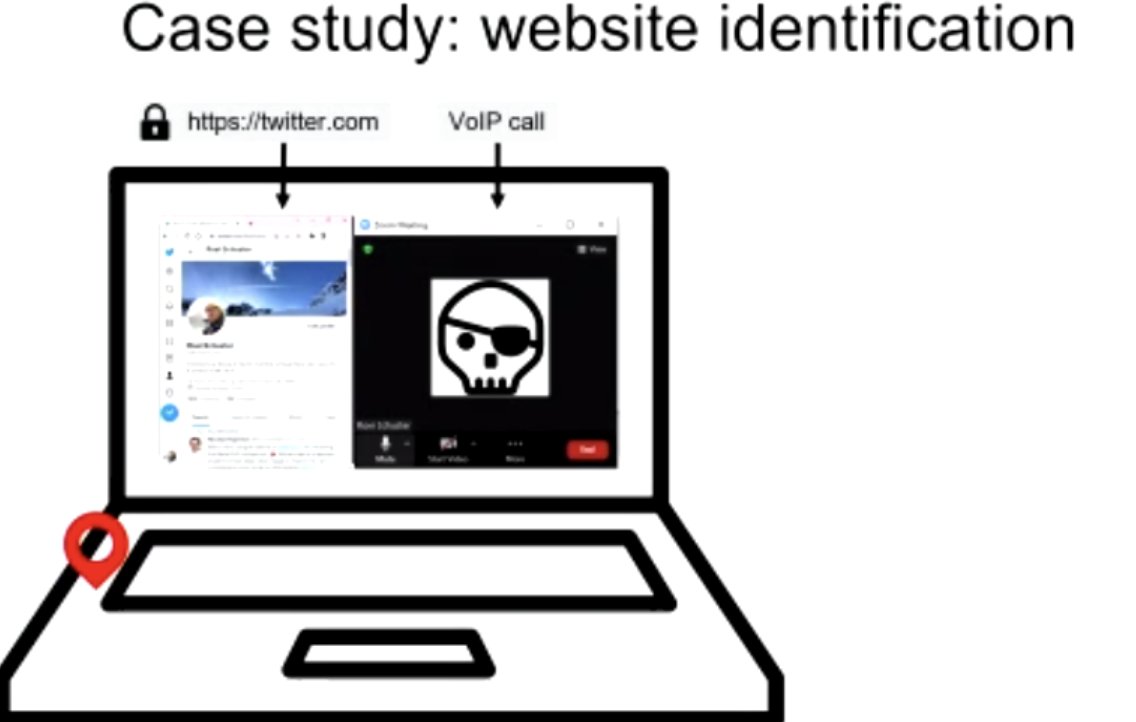
Q: Are any particular codecs vulnerable?
A: 'Most of them?' Also depends on how close the microphone is
#realworldcrypto
A: 'Most of them?' Also depends on how close the microphone is
#realworldcrypto

Coffee break!
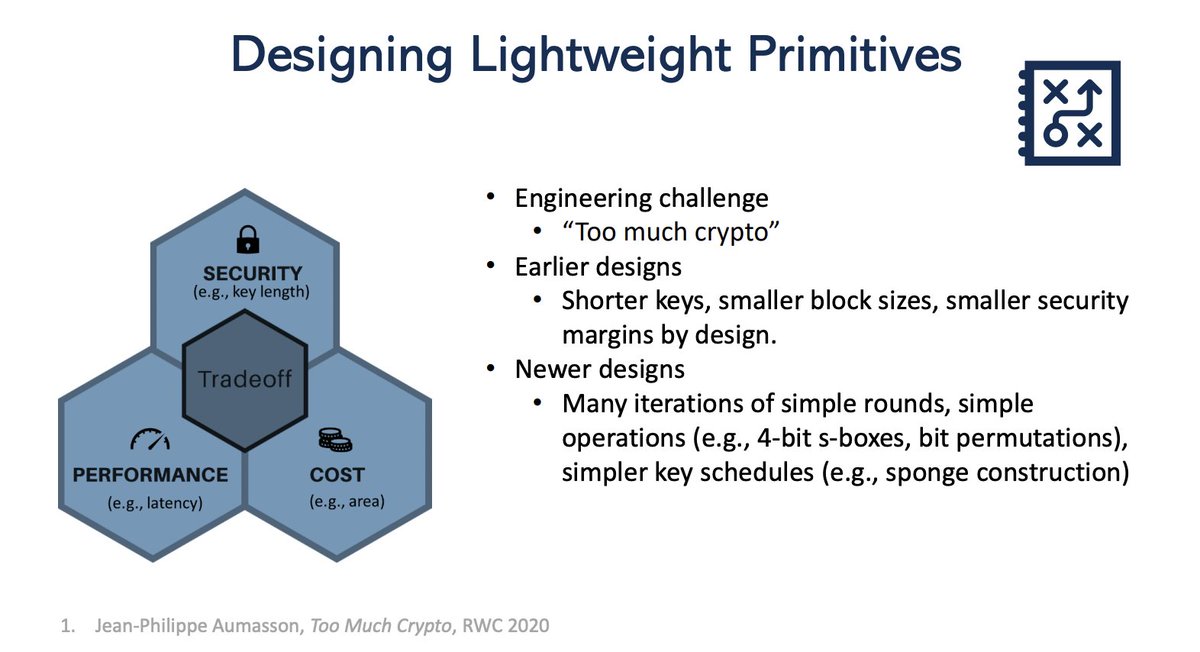
Back! Next up, "Heavyweight Security via Lightweight Cryptography", presented by Meltem Sonmez Turan
#realworldcrypto
#realworldcrypto

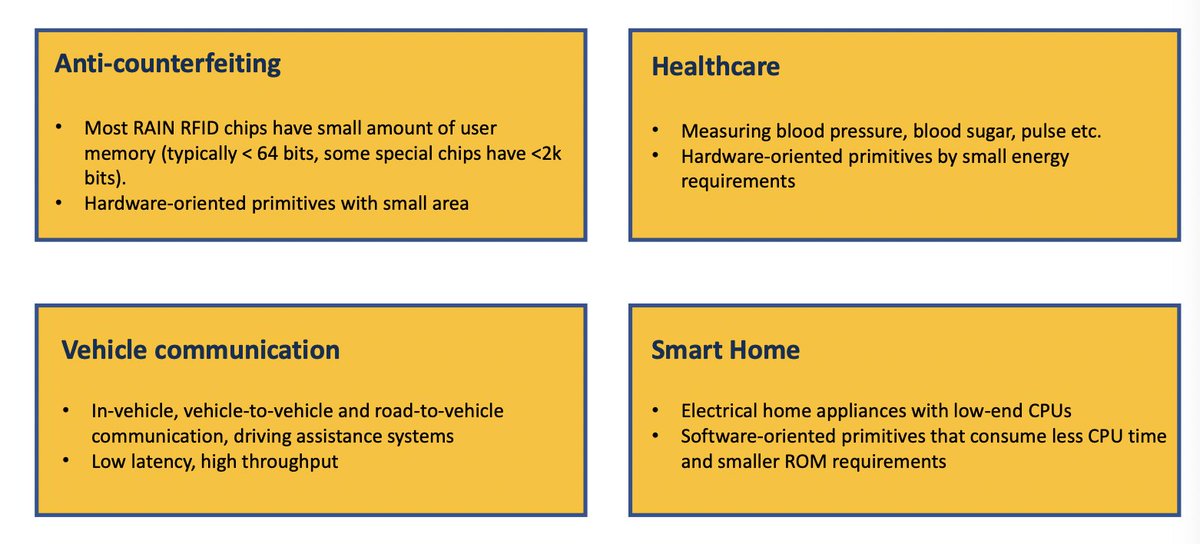
Multi-round competition to develop new guidelines, recommendations and standards optimized for constrained devices
#realworldcrypto
#realworldcrypto
Didn't realize that the PQC competition was very popular, compared to other NIST competitions!
#realworldcrypto
#realworldcrypto

Round 1: lots of things based on block ciphers, tweakable block ciphers, and hashes based on sponge constructions
#realworldcrypto
#realworldcrypto

Don't let the name fool you, "lightweight" doesn't mean "weak", rather they are optimized to perform well and securely on constrained devices. Follow here: csrc.nist.gov/Projects/light…
#realworldcrypto
#realworldcrypto
Q: After some of these lightweight primitives are finalized, does it make sense to use AES at all after?
A: They will not be very efficient as AES in servers / PCs where AES-NI instructions are available
#realworldcrypto
A: They will not be very efficient as AES in servers / PCs where AES-NI instructions are available
#realworldcrypto
Next up, "Rugged Pseudorandom Permutations and Their Applications", presented by Jean Paul Degabriele
#realworldcrypto
#realworldcrypto

Looks nice for order-resilient channels like QUIC, DTLS; need to handle out-of-order delivery of packets/records
#realworldcrypto
#realworldcrypto

Q: This looks to help so much with protocol design, were you looking at things like QUIC when designing?
A: Yeah Tor, and some QUIC
#realworldcrypto
A: Yeah Tor, and some QUIC
#realworldcrypto
"IBM allowed me to work on things of my own taste, including signatures, discrete log; I was able to dabble with authentication schemes and public key schemes." Sounds like a lovely research environment 🥰
#realworldcrypto
#realworldcrypto
"If you submitted a paper to CRYPTO/EUROCRYPT in the early 90s, and your paper was rejected because of a 'devastating attack', that was me." [applause]
#realworldcrypto
#realworldcrypto
We absolutely have moved the internet on deployment of TLS because in huge part of Let's Encrypt's work
#realworldcrypto
#realworldcrypto

"It felt frustrating that [creating a new CA from scratch] was what had to happen, it's a lot of work." Support them! letsencrypt.org/donate/
#realworldcrypto
#realworldcrypto
[ Cheap plug: it's hard to be a certificate authority! …tycryptographywhatever.buzzsprout.com/1822302/914639… ]
#realworldcrypto
#realworldcrypto
Resiliency is really important in the PKI ecosystem, automated revocation is work that will make this even better
#realworldcrypto
#realworldcrypto
Lunchtime!
Compelled decryption and lawful intercept are system changes, it's not just about a single ciphertext
#realworldcrypto
#realworldcrypto
Bangladesh: "criminals are using e2ee services to plan [offline] crimes!" Motivates the ask for 'traceability'
#realworldcrypto
#realworldcrypto

Ethiopia: after a workshop on how to do PGP-encrypted email, organizers arrested on allegations of being "spies" (!)
#realworldcrypto
#realworldcrypto

Zimbabwe: gov claimed they could read E2EE'd WhatsApp messages, scared people enough to chill activity; if gov can't stop usage enough, they just block WhatsApp completely
#realworldcrypto
#realworldcrypto

US: EARN-IT act
EU: Child Safety Act
Would embolden govs/actors around the world to also feel entitled to similar access
#realworldcrypto
EU: Child Safety Act
Would embolden govs/actors around the world to also feel entitled to similar access
#realworldcrypto
Offer alternative narratives, watch alternative policies, don't forget civil liberties implications of things like compelled decryption, client-side scanning
#realworldcrypto
#realworldcrypto

Need clear definitions of what End to End Encryption is, or others try to erode the definition while claiming to still be E2EE'd
#realworldcrypto
#realworldcrypto
Q: Intellectual property law threats to encryption?
A:Proposed in the past, largely unpopular, in contrast to the client-side scanning, CSAM matching approaches
#realworldcrypto
A:Proposed in the past, largely unpopular, in contrast to the client-side scanning, CSAM matching approaches
#realworldcrypto
Q: Web3, circumvent censorship?
A: In the EU there things that get taken down, and the inability to ever take something down (like on a blockchain) presents problems
#realworldcrypto
A: In the EU there things that get taken down, and the inability to ever take something down (like on a blockchain) presents problems
#realworldcrypto
Q: end-running E2EE via escrow, thresholds?
A: Eval'd a bunch of proposals, found most are unsatisfactory; NCMEC hash databases maintained by trusted parties and humans, the promise of confidentiality is gone (Apple too). User reporting is good, but see above
#realworldcrypto
A: Eval'd a bunch of proposals, found most are unsatisfactory; NCMEC hash databases maintained by trusted parties and humans, the promise of confidentiality is gone (Apple too). User reporting is good, but see above
#realworldcrypto
Q: What if the democratic will wants to crack down on encryption?
A: In our offline lives, we have the right to whisper: allowing this online includes encryption; taking breaking encryption off the table may help us come up with better societal solutions
#realworldcrypto
A: In our offline lives, we have the right to whisper: allowing this online includes encryption; taking breaking encryption off the table may help us come up with better societal solutions
#realworldcrypto
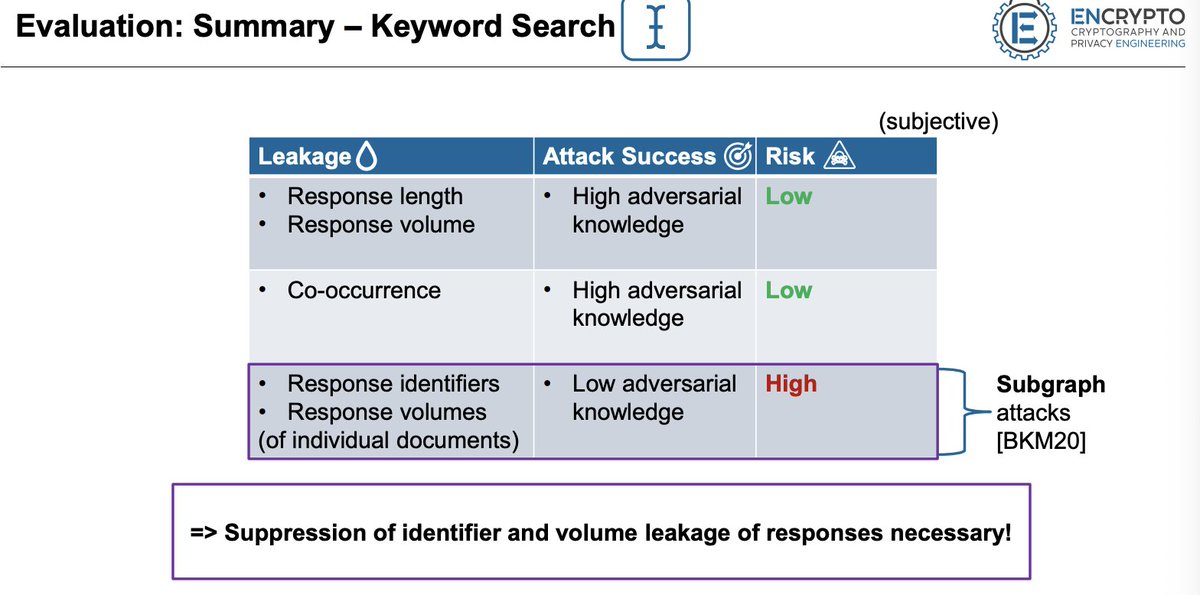
Next up, "All about that Data: Towards a Practical Assessment of Attacks on Encrypted Search", presented by Amos Treiber
#realworldcrypto
#realworldcrypto

Tool: LEAKER, implementation of 17 major attacks in python ➛ github.com/encryptogroup/…
#realworldcrypto
#realworldcrypto

#realworldcrypto
https://twitter.com/crypto_doodles/status/1514215138412437507?t=JVVNCbxzerzMjb2YtT_q1Q&s=19
Q: Factoring in weighted risk of occurrence?
A: No numerical analysis, intuition as to what level of revealing is 'bad'
#realworldcrypto
A: No numerical analysis, intuition as to what level of revealing is 'bad'
#realworldcrypto
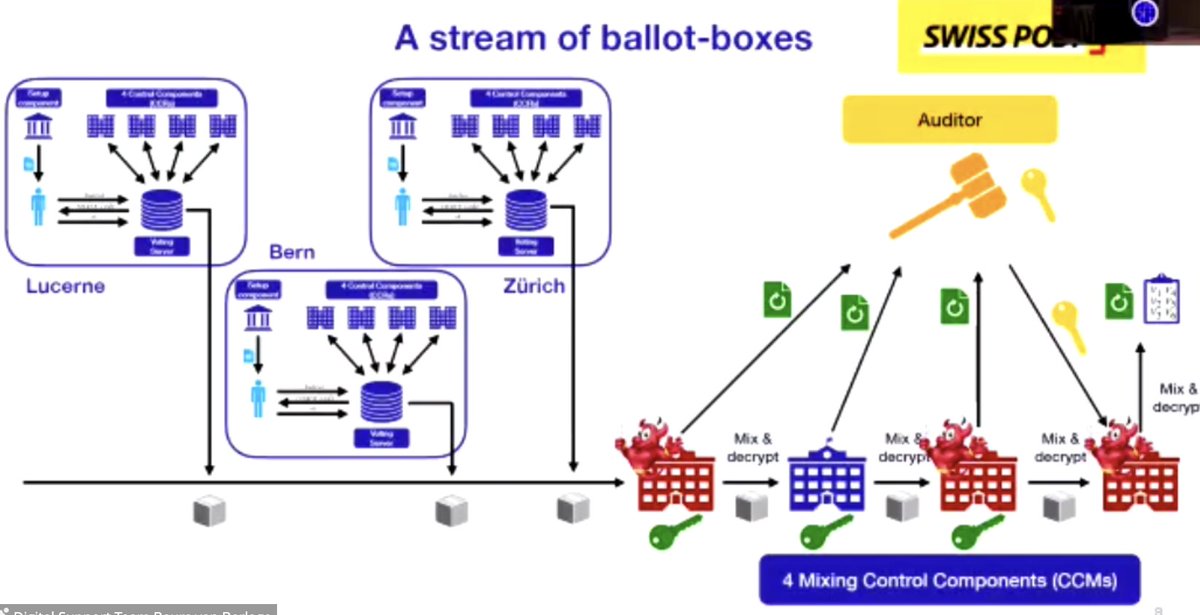
Next up, "A privacy attack on the SwissPost e-voting system", presented by Alexandre Debant
#realworldcrypto
#realworldcrypto
#realworldcrypto
https://twitter.com/MalloryKnodel/status/1514217823005986819?t=C-3IW9WrBSOIukZzaO7KAw&s=19
it is important to model _all the specificities of the system_ when doing formal proofs
#realworldcrypto
#realworldcrypto
New requirement, made a mess of the security properties established up to this point
#realworldcrypto
#realworldcrypto

Q: Methodology to find the attack?
A: Started symbolic proof w/ ProVerif very naïvely, and found an attack for a different one; did same for SwissPost; quite easy to detect
#realworldcrypto
A: Started symbolic proof w/ ProVerif very naïvely, and found an attack for a different one; did same for SwissPost; quite easy to detect
#realworldcrypto
Break time!
Next up, "Exposure Notifications Private Analytics", by Tim Geoghegan, Mariana Raykova Frederic Jacobs
#realworldcrypto
#realworldcrypto
[Thought: do any health authorities support a curated at-home rapid test as input to their EN systems?]
#realworldcrypto
#realworldcrypto
How can we tune the system to be useful to epidemiologists and health authorities, while upholding privacy principles?
#realworldcrypto
#realworldcrypto

Paper: covid19-static.cdn-apple.com/applications/c…
Uses Prio (eprint.iacr.org/2019/188)
#realworldcrypto
Uses Prio (eprint.iacr.org/2019/188)
#realworldcrypto
Each client adds a small amount of noise, aggregation amplifies this noise, providing differential privacy
#realworldcrypto
#realworldcrypto
An aggregator is operated by ISRG (the org behind @letsencrypt ), and by NCI at NIH; running on k8s on different cloud hosts
#realworldcrypto
#realworldcrypto

Ingestion servers to authenticate and attest to data and devices before their inputs get aggregated
#realworldcrypto
#realworldcrypto

Deployed since December 2020, 15 US states and 4 Mexican states; 9 metrics collected; servers process millions of contributions daily
Used to estimate that dozens of lives were saved in Olympia Washington by Covid Exposure Notifications in that area
#realworldcrypto
Used to estimate that dozens of lives were saved in Olympia Washington by Covid Exposure Notifications in that area
#realworldcrypto
["Instantiating PKIs for <specific thing> is harder than it looks, ask @sleevi_ , @letsencrypt ]
#realworldcrypto
#realworldcrypto
To get a cred that lets you do something, you need 4 different cred exchanges 🥴
To get it to work, you need a /lot/ of config that is easy to mess up 😒
#realworldcrypto
To get it to work, you need a /lot/ of config that is easy to mess up 😒
#realworldcrypto

Drive tests from a seed for repeatability, prep for integrating with servers outside your VPN, custom builds, needs close communication with teams that aren't on your team Slack
#realworldcrypto
#realworldcrypto

CTA: user and adopter education, standardization (datatracker.ietf.org/doc/bofreq-pri…, which is the next talk!)
#realworldcrypto
#realworldcrypto
Next up, "Standardizing MPC for Privacy-preserving Measurement" presented by Chris Patton
#realworldcrypto
#realworldcrypto

ENPA was designed specifically for aggregating bitvectors - what about other types of stats? Other papers' goals tend to vary. A roadmap: IETF working group on privacy-preserving measurement:
datatracker.ietf.org/doc/bofreq-pri…
#realworldcrypto
datatracker.ietf.org/doc/bofreq-pri…
#realworldcrypto
Incremental distributed point function (IDPF), allows counting the number of strings beginning with a given prefix
#realworldcrypto
#realworldcrypto
Filter out some below a threshold, and get the ones that occur at least as many times as our threshold
#realworldcrypto
#realworldcrypto
Not all solutions will have the same shape, but hopefully similar enough to build applications around them: Verifiable Distributed Aggregation Functions (VDAFs)
datatracker.ietf.org/doc/draft-patt…
#realworldcrypto
datatracker.ietf.org/doc/draft-patt…
#realworldcrypto
Q: Failure modes - identification of cheaters, after aggregation?
A: Whole bag of worms, let's talk offline 🐛
#realworldcrypto
A: Whole bag of worms, let's talk offline 🐛
#realworldcrypto
Q: Crypto seems to be a small part of making the whole system work, does a standard help?
A: Useful to abstract away the cloud primitives, something agnostic.
#realworldcrypto
A: Useful to abstract away the cloud primitives, something agnostic.
#realworldcrypto
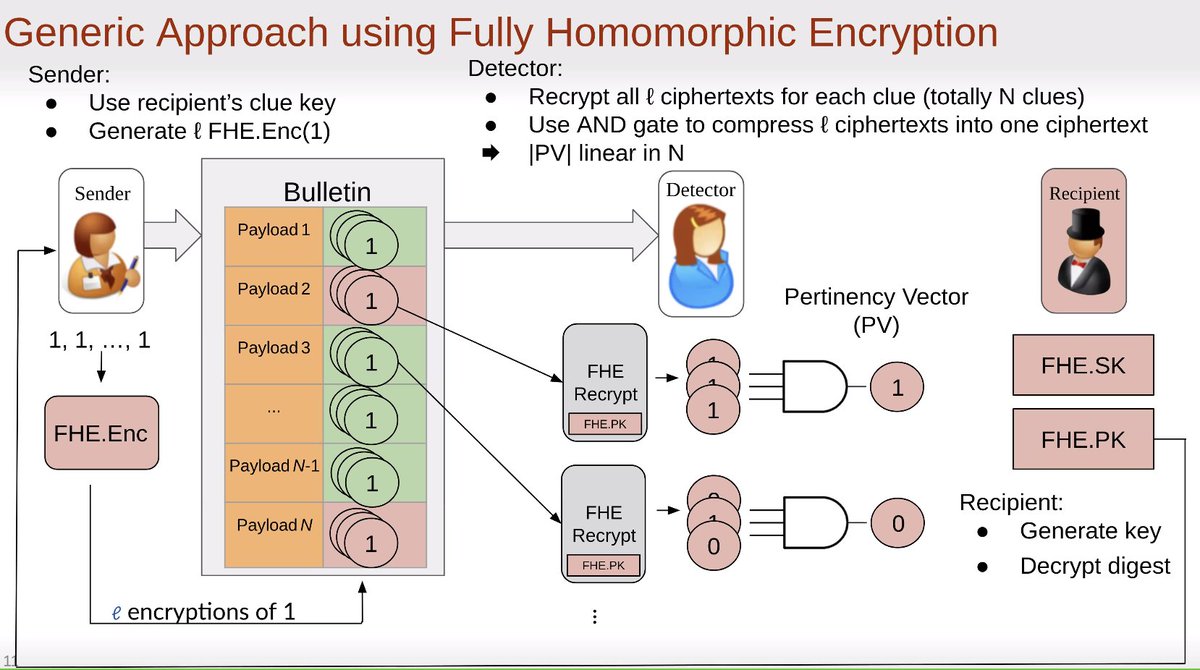
Last talk of the day, "Oblivious Message Retrieval", by Zeyu Liu and Eran Tromer
eprint.iacr.org/2021/1256
#realworldcrypto
eprint.iacr.org/2021/1256
#realworldcrypto

FMD: using decoys in the trial decryption, gives weak privacy, needs honest senders and receivers
#realworldcrypto
#realworldcrypto
Private Signaling needs trusted hardware (🔥)
V2 needs two communicating, non-colluding server, a strong assumption
#realworldcrypto
V2 needs two communicating, non-colluding server, a strong assumption
#realworldcrypto
You can give your encrypted viewing key to a server, server does an FHE'd query using that encrypted key, gives you results, and the server doesn't need to be within your trust boundary 🎉
#realworldcrypto
#realworldcrypto
PVW encryption, based on LWE (lattice) assumptions, much smaller and more efficient
#realworldcrypto
#realworldcrypto

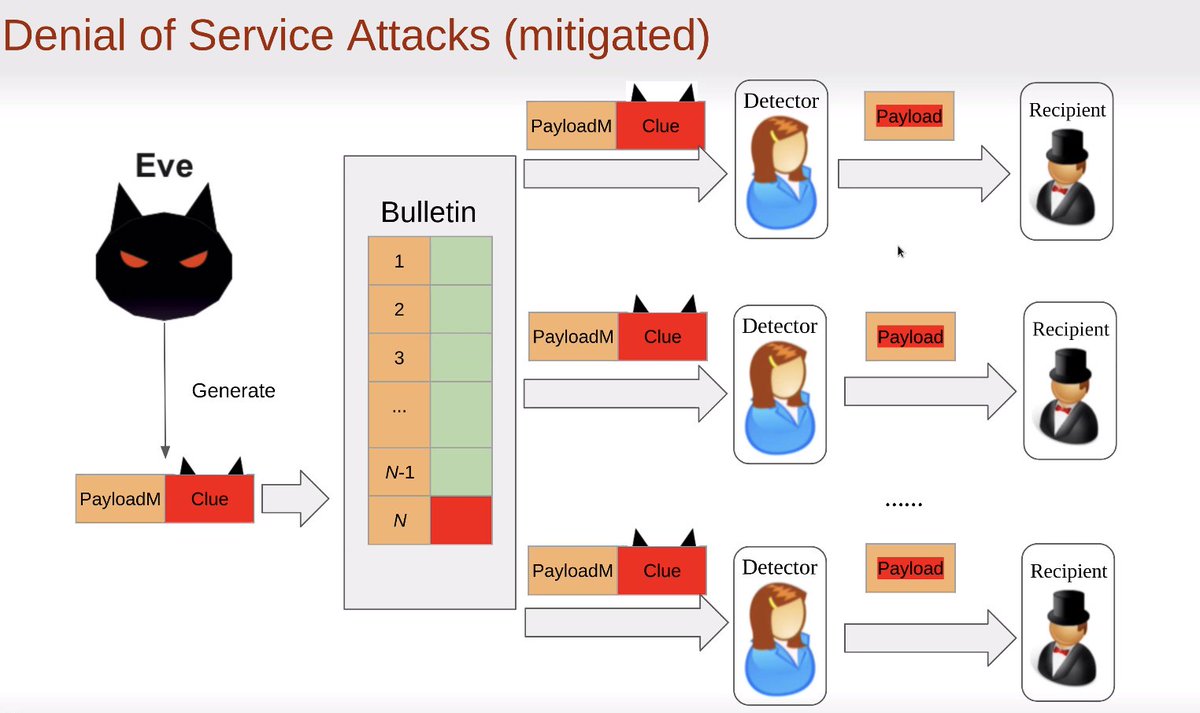
Earlier schemes assume some level of honesty; OMR mitigates malicious clues sent from dishonest clients
#realworldcrypto
#realworldcrypto
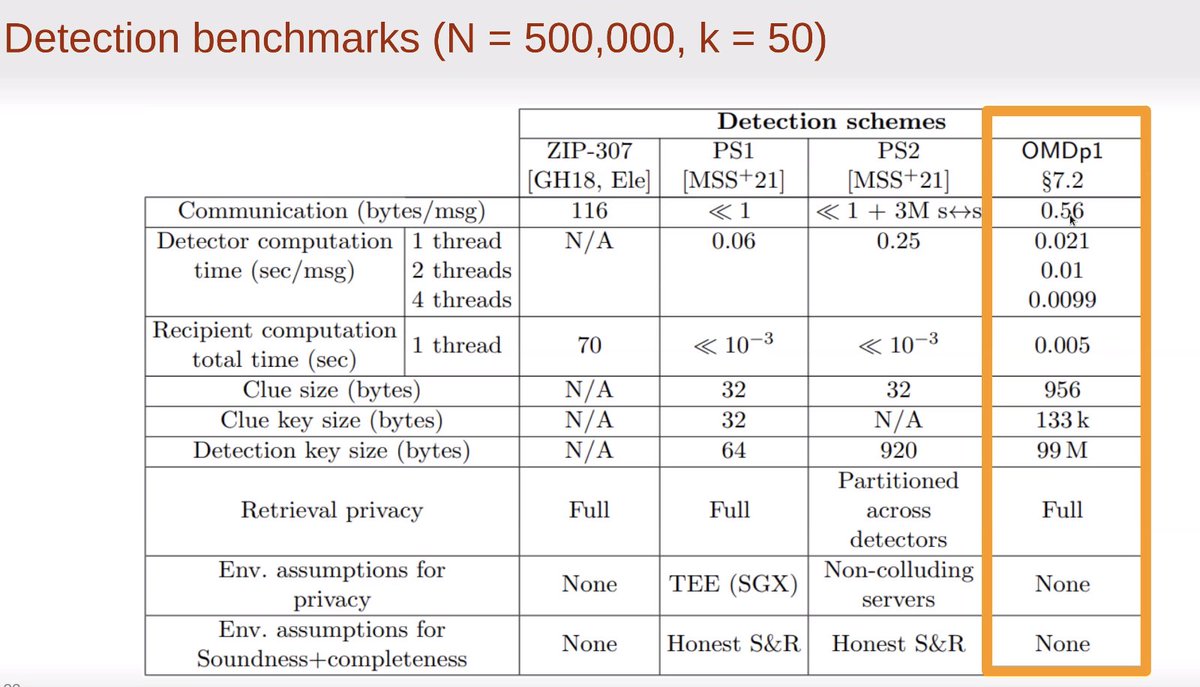
Less than a byte per message 😻
~5ms
Clue size is < 1KB
Detection keys are about 100MB (😬)
Strongest notions of privacy and honesty of parties
#realworldcrypto
~5ms
Clue size is < 1KB
Detection keys are about 100MB (😬)
Strongest notions of privacy and honesty of parties
#realworldcrypto
Q: Should we actually worry about quantum computers?
A: Yes; Sure it keeps mathematicians employed; gives cryptographers opportunity to dev new schemes
#realworldcrypto
A: Yes; Sure it keeps mathematicians employed; gives cryptographers opportunity to dev new schemes
#realworldcrypto
Yuval says Mike Hamburg suggested looking at exploiting speculative execution to break attack crypto schemes (๑•́ ヮ •̀๑)
#realworldcrypto
#realworldcrypto
Q: Advice for younger-career members of RWC community?
A: Do what you like; get a taste of research in different contexts, see who's going to use the results of your research
#realworldcrypto
A: Do what you like; get a taste of research in different contexts, see who's going to use the results of your research
#realworldcrypto
Q: what do you think will ultimately happen with cryptocurrencies?
A: Some really cool cryptography is going to come out of it [😉]
#realworldcrypto
A: Some really cool cryptography is going to come out of it [😉]
#realworldcrypto
Q: besides tricky names, what's the secret to strong cryptography?
A: For AES, we were working on it for years before the competition started; for SHA3, we invested a lot of time, open research, no pressure to publish papers really helped
#realworldcrypto
A: For AES, we were working on it for years before the competition started; for SHA3, we invested a lot of time, open research, no pressure to publish papers really helped
#realworldcrypto
Q: what do you think will be the future of Intel SGX?
Yuval: Intel has stopped producing SGX for the end user, if you have physical access to a machine holding secrets you will eventually break it, SGX cloud-only can become a defense-in-depth layer
#realworldcrypto
Yuval: Intel has stopped producing SGX for the end user, if you have physical access to a machine holding secrets you will eventually break it, SGX cloud-only can become a defense-in-depth layer
#realworldcrypto
Q: is the gap between theory and practice in cryptography narrowing?
A: There's a large spread, the gap is narrowing, companies are investing more; much better than 20 years ago
#realworldcrypto
A: There's a large spread, the gap is narrowing, companies are investing more; much better than 20 years ago
#realworldcrypto
Me: Are paper reviewers responsible for bugs in my implementation of a crypto protocol that gets deployed to prod? [NB: not necessarily the protocol, but implementation]
A: Science is about building on others; you would think reviewers would check the proof
#realworldcrypto
A: Science is about building on others; you would think reviewers would check the proof
#realworldcrypto
Q: Who should roll their own crypto?
A: Don't do it alone, bring a friend!
[Cheap plug: …tycryptographywhatever.buzzsprout.com/1822302/895384…]
#realworldcrypto
A: Don't do it alone, bring a friend!
[Cheap plug: …tycryptographywhatever.buzzsprout.com/1822302/895384…]
#realworldcrypto
End of day 1!
Day 2 of #realworldcrypto ! Kicking off with the TLS session, "Justifying Standard Parameters in the TLS 1.3 Handshake", presented by Hannah Davis
The reduction to diffie-hellman isn't tight, giving a tighter bound, quadratic loss -> constant loss
#realworldcrypto
#realworldcrypto
A reduction to DH has to simulate all these sessions at once; a random factor for picking a session and for a server leads to the tightness loss
#realworldcrypto
#realworldcrypto
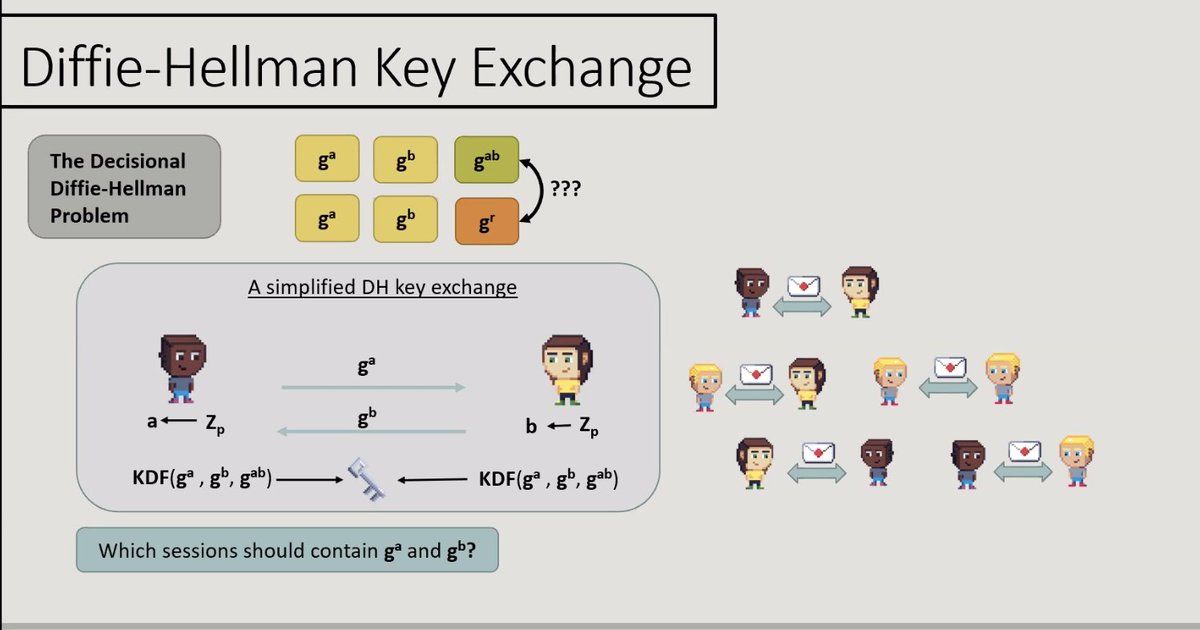
Only one hash function, so not more than one random oracle - proof has to model only the one random oracle
#realworldcrypto
#realworldcrypto

Q: If you could, how would you redesign TLS 1.3?
A: No perfect answer, starting from scratch would incl. redesigning HMAC to separate; incl. suffix padding to each of HMAC & KDF
#realworldcrypto
A: No perfect answer, starting from scratch would incl. redesigning HMAC to separate; incl. suffix padding to each of HMAC & KDF
#realworldcrypto
Q: KEM instead of DH?
A: Relies on re-randomization properties of DH, if possible we could try them in this technique
#realworldcrypto
A: Relies on re-randomization properties of DH, if possible we could try them in this technique
#realworldcrypto
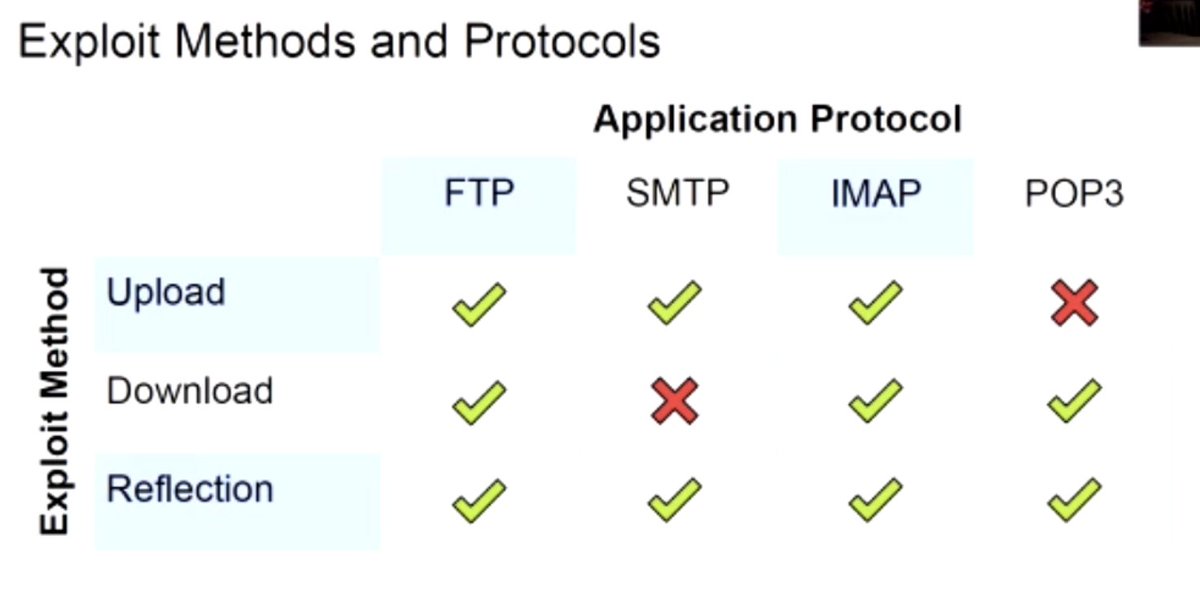
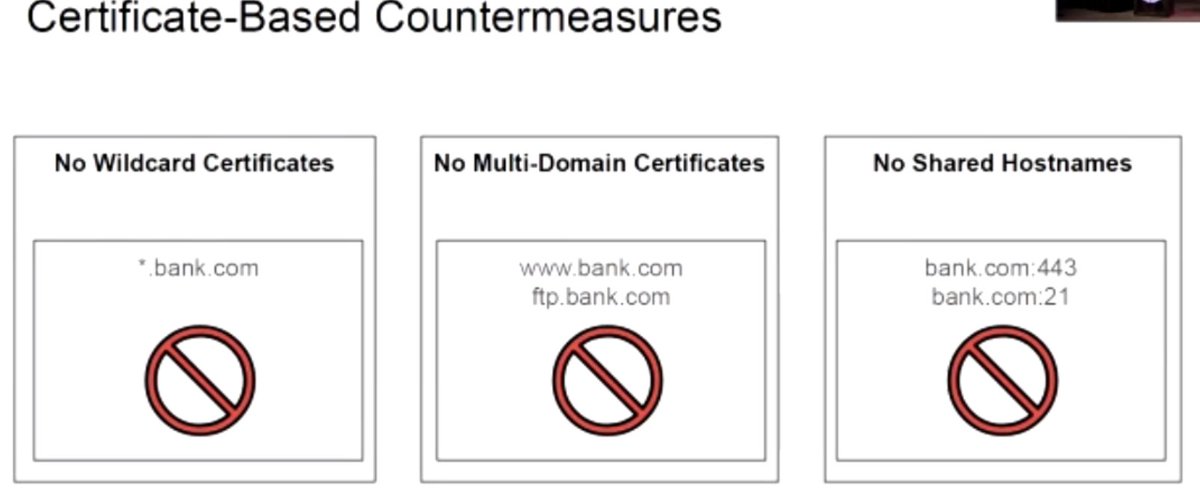
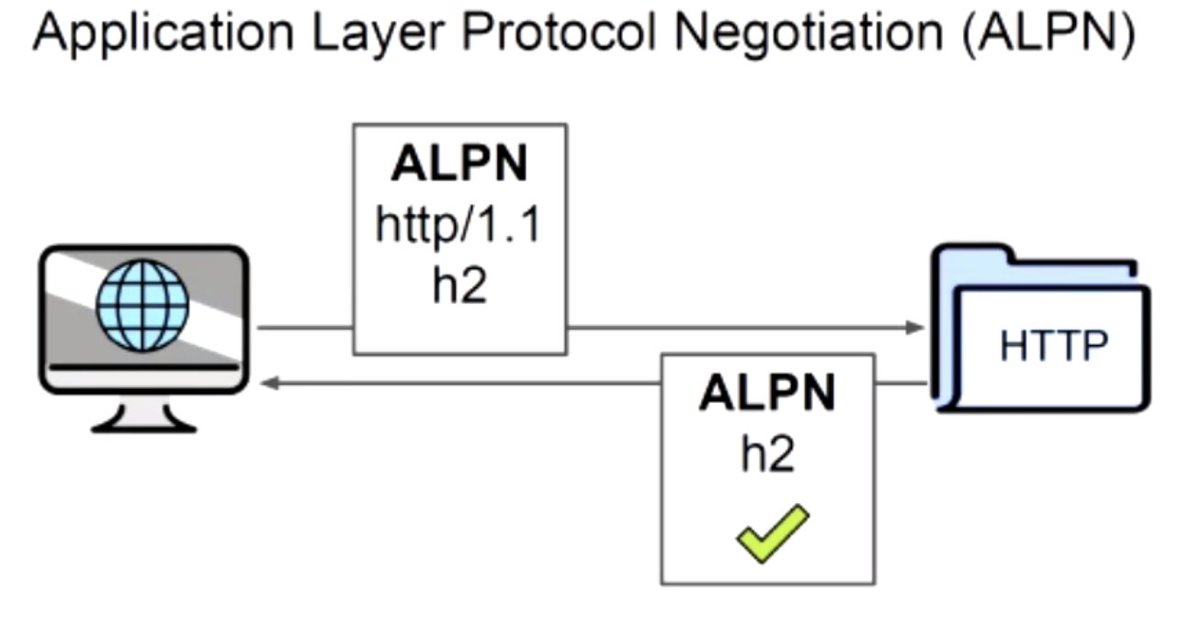
Next up, "ALPACA: Application Layer Protocol Confusion - Analyzing and Mitigating Cracks in TLS Authentication", presented by Marcus Brinkmann
#realworldcrypto
#realworldcrypto

Can extract the cookie and impersonate user to the web site, such as your bank (or crypto exchange?)
#realworldcrypto
#realworldcrypto
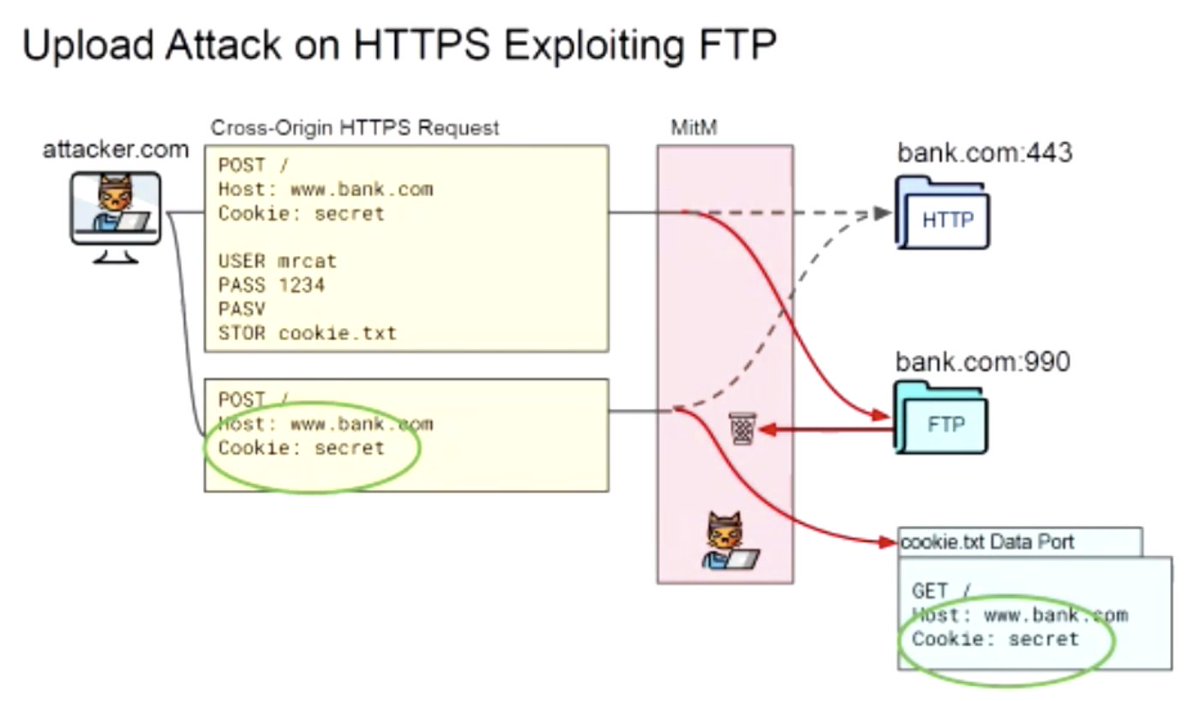
Detect, "limit syntax errors", avoid reflection, to mitigate in the application layer
#realworldcrypto
#realworldcrypto

Q: Is the attack limited by CORS policies?
A: There are some 'CORS-safe' requests that are kept for compat, that always seem to go through cross-origin; can be mitigated, doesn't work in a scenarios, more in paper, depends on cookie policies
#realworldcrypto
A: There are some 'CORS-safe' requests that are kept for compat, that always seem to go through cross-origin; can be mitigated, doesn't work in a scenarios, more in paper, depends on cookie policies
#realworldcrypto
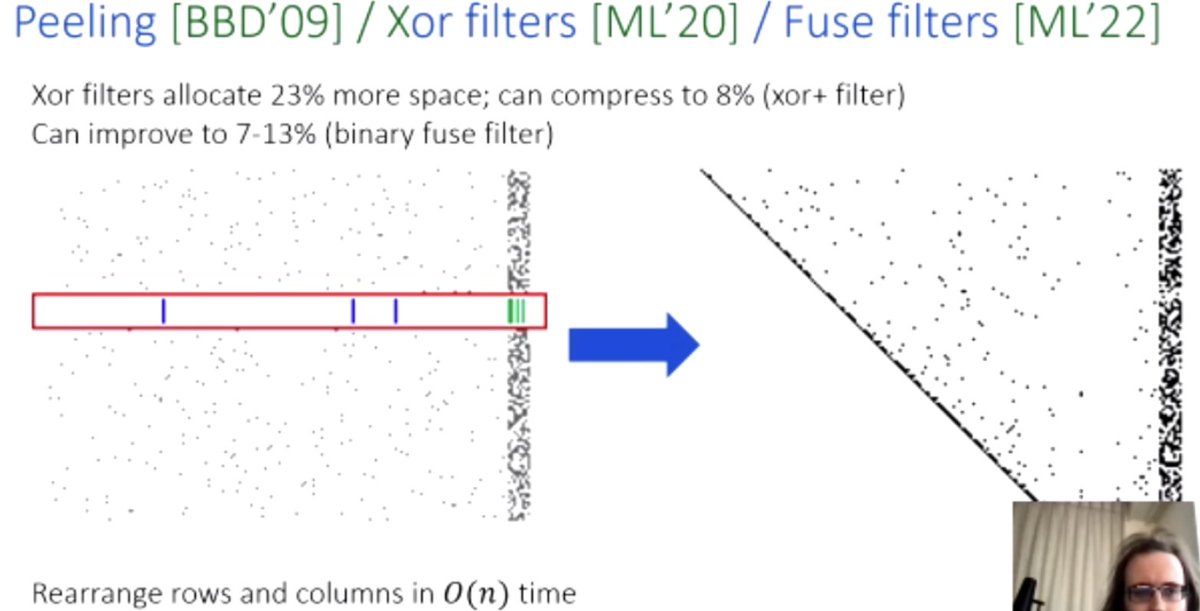
Next up, "Improved CRL compression with structured linear functions", by Mike Hamburg
#realworldcrypto
#realworldcrypto
Compress, only need to query some certs, only need to build a function that is correct on a finite domain
#realworldcrypto
#realworldcrypto

Ooo, solve the matrix with gaussian elimination, but this takes O(n³) time, O(n^2.8) memory
#realworldcrypto
#realworldcrypto

Efficient in time and memory, but there is a chance there will not be a solution, so you can make the matrix larger to lower this chance
#realworldcrypto
#realworldcrypto

Q: What were the causes for variance between query times of different approaches?
A: Rust is better for safety, when optimizing to compare cross-platform, Rust's siphasher crate was slower on Intel vs M1; Some had more than one frayed ribbon filter
#realworldcrypto
A: Rust is better for safety, when optimizing to compare cross-platform, Rust's siphasher crate was slower on Intel vs M1; Some had more than one frayed ribbon filter
#realworldcrypto
Break!
Next up, "Commit Acts of Steganography — Before It's Too Late", presented by Gabriel Kaptchuk
#realworldcrypto
#realworldcrypto

Q: Do we have to work so hard to make covertext look like natural language? Needle in a high stack?
A: We're shooting higher, usually in a high-risk environment
#realworldcrypto
A: We're shooting higher, usually in a high-risk environment
#realworldcrypto
Q: How resilient is this to adversary that malleates?
A: This is CPA secure, CCA/ integrity is future work
#realworldcrypto
A: This is CPA secure, CCA/ integrity is future work
#realworldcrypto
(// @SoatokDhole )
(//@swodinsky )
Q: Separating between advertisers & meta, how are you doing the secret sharing?
A: Paper coming
#realworldcrypto
A: Paper coming
#realworldcrypto
Q: To systems people, MPC may not be hard to abstract, what's hard about the crypto to systems people?
A: Because there are more constraints, that operating in the clear, different paradigm
#realworldcrypto
A: Because there are more constraints, that operating in the clear, different paradigm
#realworldcrypto
Q: How does this affect the opacity of the ads ecosystem for /users/?
A: it's hard enough to explain to developers, let alone users, similar with regulators
#realworldcrypto
A: it's hard enough to explain to developers, let alone users, similar with regulators
#realworldcrypto
Q: Can you show ads on clients such that Meta doesn't know which clients saw which ads?
A: Federated analytics [this is not the same]
#realworldcrypto
A: Federated analytics [this is not the same]
#realworldcrypto
.@FiloSottile on supporting open source software 🎉
words.filippo.io/pay-maintainer…
#realworldcrypto
words.filippo.io/pay-maintainer…
#realworldcrypto
Props to RWC for providing childcare, allows people to attend who otherwise couldn't!
#realworldcrypto
#realworldcrypto
Cheslea Komlo previewing a paper on proving properties re: threshold signatures, proving lack of participation
#realworldcrypto
#realworldcrypto
cryptography.rs ! It has a vetted curation of good Rust cryptography implementations
#realworldcrypto
#realworldcrypto
Lunchtime!
Next up, "Secure Messaging Authentication against Active Man-in-the-Middle Attacks", presented by Britta Hale
#realworldcrypto
#realworldcrypto
Comparing Signal public keys is not directly checking anything about the encryption between those two parties
#realworldcrypto
#realworldcrypto
Q: When a device is compromised, can't the ratchet keys be influenced? Does adding the authentication key affect deniability?
A: Using a designated verifier sig preserves deniability
#realworldcrypto
A: Using a designated verifier sig preserves deniability
#realworldcrypto
Next up, "An evaluation of the risks of client-side scanning", presented by @matthew_d_green
#realworldcrypto
#realworldcrypto
Rather than occasional targeted exceptional access, law enforcement started asking to delay E2E encryption deployment in general
#realworldcrypto
#realworldcrypto
"Is it possible to build systems to scan for content without breaking end to end encryption and violating privacy?"
#realworldcrypto
#realworldcrypto
CSAM scanning on the server side when the service has access to plaintext: PhotoDNA or other perceptual hashes, checking against a known db of hashes
#realworldcrypto
#realworldcrypto

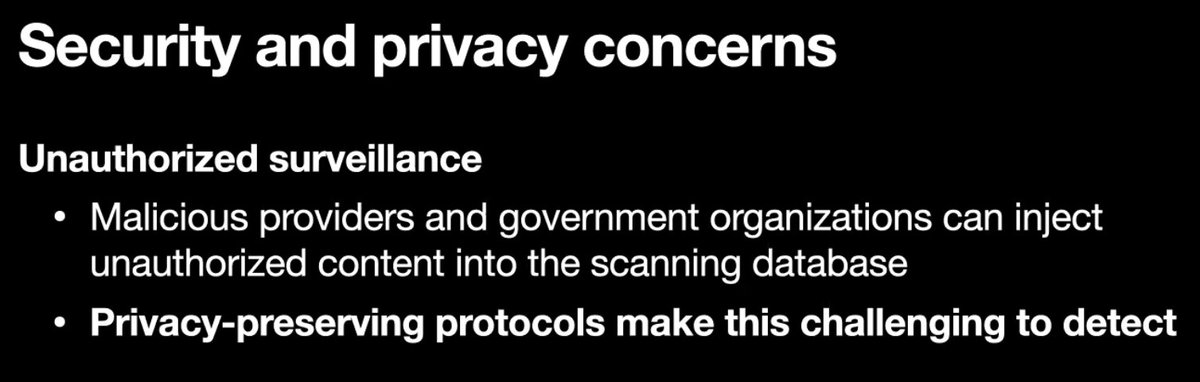
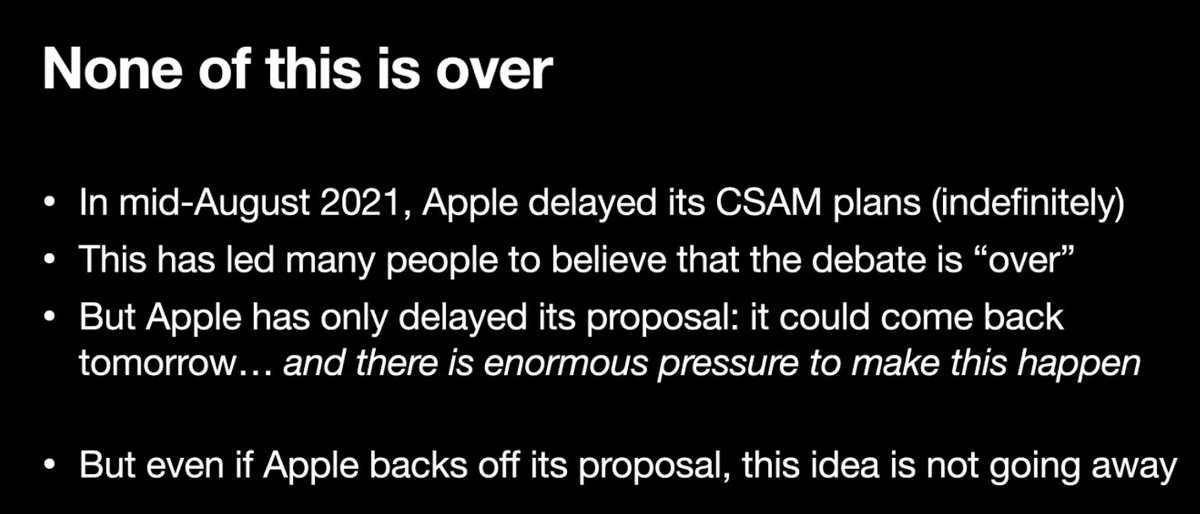
This research became very real when Apple announced it was going to deploy a system like this with iOS 15, now delayed indefinitely
#realworldcrypto
#realworldcrypto

[ We did an episode on this at the time w/ @matthew_d_green that goes into detail about the crypto in Apple's system: …tycryptographywhatever.buzzsprout.com/1822302/909977… ]
#realworldcrypto
#realworldcrypto
'Not just a theoretical concern': terrorist content, 'foreign adversaries attempts to undermine democratic values' have also been floated as in-scope for client-side scanning
#realworldcrypto
#realworldcrypto
Easy to game these NN hashes (NeuralHash) but also PhotoDNA to produce false collisions against the CSAM hash set:
#realworldcrypto
#realworldcrypto

Even if we deploy systems like this, we MUST figure out how to make them auditable and abuse-resistant.
#realworldcrypto
#realworldcrypto

Sometimes we produce technology and deploy it before we understand how to audit it and handle abuse of it
#realworldcrypto
#realworldcrypto
Q: The adversarial model that LEO has?
A: They are not very robust to even mild adversarial behavior; 97% of reports to NCMEC aren't prosecuted, are outside of the US
#realworldcrypto
A: They are not very robust to even mild adversarial behavior; 97% of reports to NCMEC aren't prosecuted, are outside of the US
#realworldcrypto
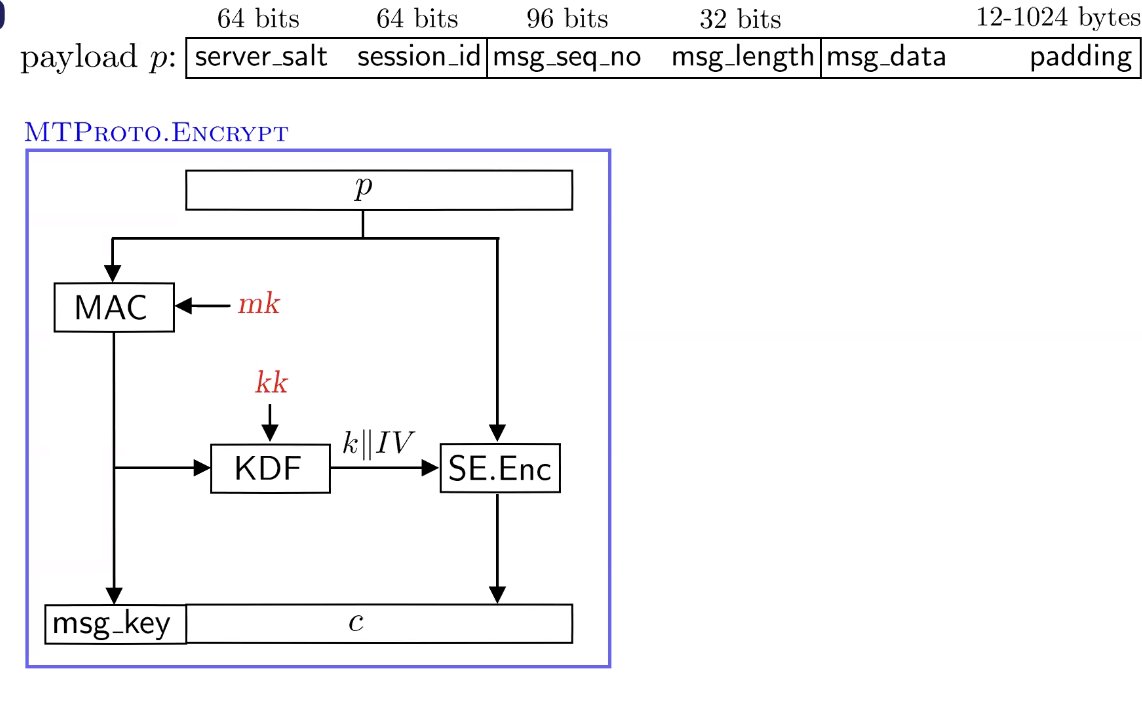
#REALWORLDCRYPTO chat: 'Non-technical evaluation: MTProto is *weird*'
- IND-CPA attack - in theory
- Message reordering - trivial, easy to exploit
- Tiiming side channel on clients - plaintext recovery, practically infeasible
- Timing side channel on server - MITM the kex, practically infeasible
#realworldcrypto
- Message reordering - trivial, easy to exploit
- Tiiming side channel on clients - plaintext recovery, practically infeasible
- Timing side channel on server - MITM the kex, practically infeasible
#realworldcrypto

@durov claimed the server code will not be released because some government wanted their server code, to stand up a telegram clone?
#realworldcrypto
#realworldcrypto
@durov No time for questions, next up, "Making Signal Post-quantum Secure: Post-quantum Asynchronous Deniable Key Exchange from Key Encapsulation and Designated Verifier Signatures", presented by Rune Fiedler
#realworldcrypto
#realworldcrypto

Deniable authentication via designated verifier signatures (heard about in the earlier Signal talk)
#realworldcrypto
#realworldcrypto
DVS can only be verified by Bob, who already know it's you, so that gives you transcript deniability
#realworldcrypto
#realworldcrypto

Break time!
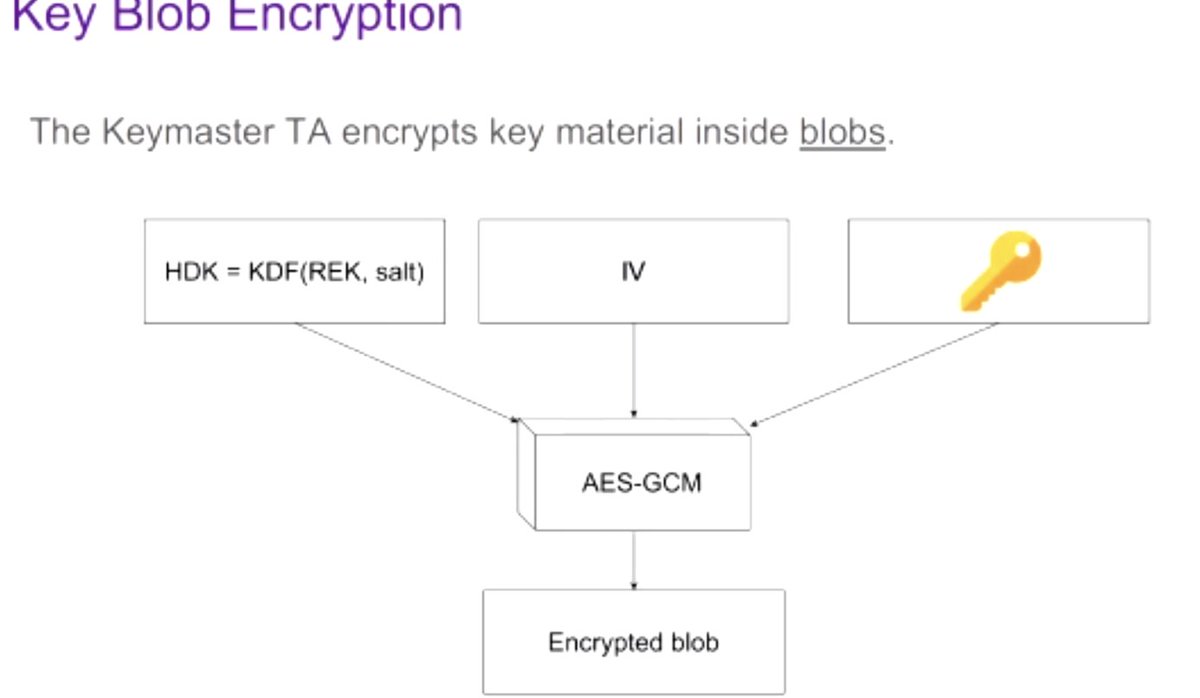
next up, "Trust Dies in Darkness: Shedding Light on Samsung’s TrustZone Cryptographic Design", presented by Alon Shakevsky
#realworldcrypto
#realworldcrypto

Q: What would you recommend to replace AES-GCM?
A: SIV mode, maybe a different block cipher, or use the cipher with the recommended usage
#realworldcrypto
A: SIV mode, maybe a different block cipher, or use the cipher with the recommended usage
#realworldcrypto
Q: Test WebAuthN against first-party services (re: counter)?
A: Cloning from devices is tricky, you have to update the counter, even without the user's knowledge
#realworldcrypto
A: Cloning from devices is tricky, you have to update the counter, even without the user's knowledge
#realworldcrypto
@luca_defeo Under-specified cryptostandards give you room to hammer your fingers...
#realworldcrypto
#realworldcrypto

@luca_defeo What does it mean to use ElGamal, or RSA? :points at some books, some edition:
#realworldcrypto
#realworldcrypto

@luca_defeo "Don't look at that algorithm, it's terrible, you will never be able to implement it"
#realworldcrypto
#realworldcrypto

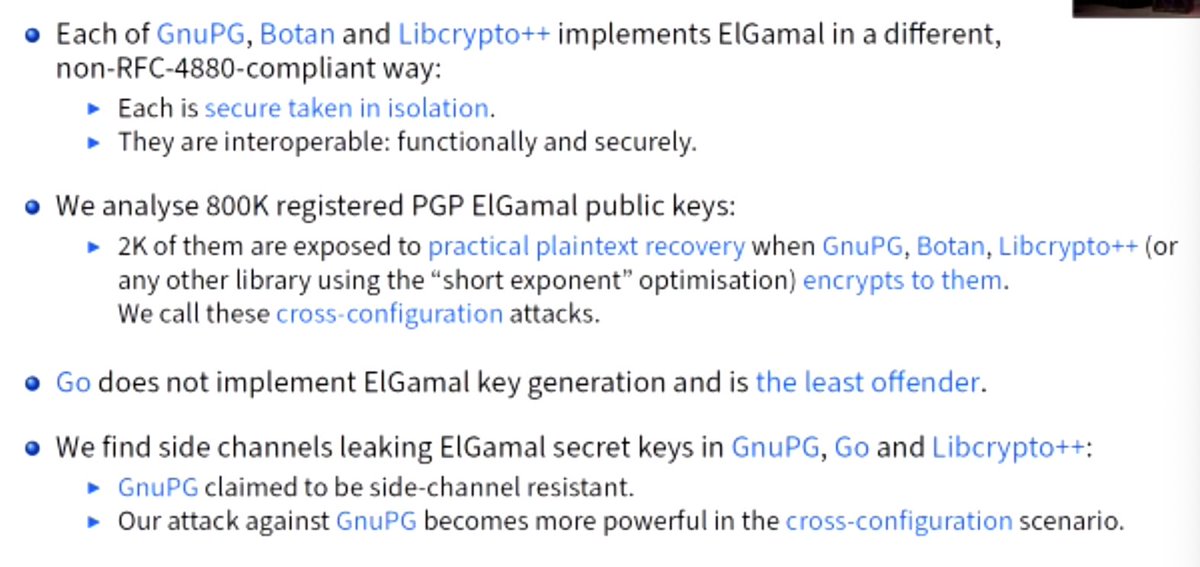
Cross-configuration attacks: different impls do slightly different things when doing ElGamal encryption
#realworldcrypto
#realworldcrypto
of 800k ElGamal OpenPGP keys, most use primes from a 'standard' set. Some use Schnorr-style primes, Lim-Lee/GnuPG
#realworldcrypto
#realworldcrypto

Q: This is a basically key validation?
A: the ECC is better because they use the RFC, which specifies, ElGamal was not sufficiently specified to include validation
#realworldcrypto
A: the ECC is better because they use the RFC, which specifies, ElGamal was not sufficiently specified to include validation
#realworldcrypto
Q: Symantec?
A: We didn't look, we couldn't find the software [apparently it's widely used in corp. contexts]
#realworldcrypto
A: We didn't look, we couldn't find the software [apparently it's widely used in corp. contexts]
#realworldcrypto
Next up, "Don't Break the Web: APIs for Chrome's Privacy Sandbox", presented by Michael Kleber
#realworldcrypto
#realworldcrypto
heh, google.com would not suffer that kind of loss, because https://t.co/cNC9CnF9bM does not need cookies to target users, they just target queries typed in by untracked users
#realworldcrypto
#realworldcrypto

All these JS functions are isolated [ I'm guessing all the work on Site Isolation has enabled this ]
#realworldcrypto
#realworldcrypto
Bidding functions /do/ need some real-time information, not just pre-loaded data on the device
#realworldcrypto
#realworldcrypto
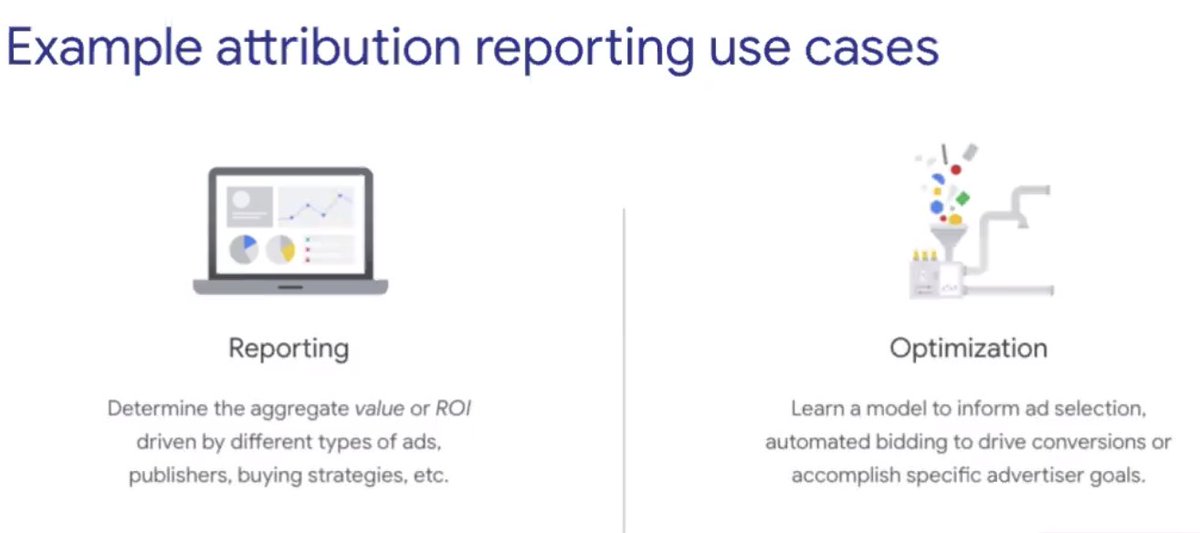
What they really want to know is the /aggregate/ ROI driven by different ads, publishers, etc
#realworldcrypto
#realworldcrypto
Q: Fraud prevention? [ a real issue in the current ad ecosystem ]
A: PRIVACY PASS WOO [ emphasis mine ]
#realworldcrypto
A: PRIVACY PASS WOO [ emphasis mine ]
#realworldcrypto
A: Other blind signatures. There is not an end-to-end solution for this problem, turns out there is a lot of overlap with solutions for fraud prevention
#realworldcrypto
#realworldcrypto
Q: users explicitly specifying their ad preferences?
A: Some proposals ('Topics' from Chrome), all need good privacy properties
#realworldcrypto
A: Some proposals ('Topics' from Chrome), all need good privacy properties
#realworldcrypto
A: Privacy is contextually-dependent; some people think contextual distinctions exist and some think other ones exist, it's tricky
#realworldcrypto
#realworldcrypto
New Journal should be free/open access, fast turnaround time (3 months), all crypto areas, scaling, reduce load on reviewers, can publish without travel to conferences, complement but not replace other confs, and
#realworldcrypto

#realworldcrypto


Q: If people still submit to the main confs, are they unchanged?
A: Unchanged, adding a new publication, takes /some/ papers out of the queue for the other confs, relieving the burden of the conf reviewers
#realworldcrypto
A: Unchanged, adding a new publication, takes /some/ papers out of the queue for the other confs, relieving the burden of the conf reviewers
#realworldcrypto
A: We have a lot of people who can't travel for many diverse reasons to confs, so many more people in the community than before, a journal like this scales much better so that many people can get published that otherwise wouldn't because of travel requirements
#realworldcrypto
#realworldcrypto
Q: What about code, artifacts?
A: TCHES has artifacts that are reviewed, we should look at it
#REALWORLDCRYPTO
A: TCHES has artifacts that are reviewed, we should look at it
#REALWORLDCRYPTO
@BearSSLnews : if the new journal happens, I will probably submit there and only there ʕ·͡ᴥ·ʔ
#realworldcrypto
#realworldcrypto
Q: What if conf-accepted papers aren't required to challenge?
A: That does have benefits, but this was proposed in 2011 and did not get much community support, but we can also try that again, while also trying the new journal
#realworldcrypto
A: That does have benefits, but this was proposed in 2011 and did not get much community support, but we can also try that again, while also trying the new journal
#realworldcrypto
A: Easier to do something new that changing something that exists that people have a vested interest in
#realworldcrypto
#realworldcrypto
Q: What about Reviewer #2?
A: We propose mechanisms to handle this, rebuttal etc, why 2 accept and 1 reject?
#realworldcrypto
A: We propose mechanisms to handle this, rebuttal etc, why 2 accept and 1 reject?
#realworldcrypto
OH it costs _IACR_ $100/paper, _not_ the paper submitter. No cost to the submitter.
#realworldcrypto
#realworldcrypto
Done for day 2!
https://twitter.com/SchmiegSophie/status/1514608663364718608?t=19mHhk8kCtRnBr3xYj1r5w&s=19
#realworldcrypto
Day 3 of #realworldcrypto!
Catching up the Post Quantum session, with "Quantum-Resistant Security for Software Updates on Low-power Networked embedded Devices", by Benjamin Smith
#realworldcrypto
#realworldcrypto
What is the practical cost of transitioning from classical cryptosystems
(ECDSA/P256 or Ed25519) to post-quantum alternatives on RIOT, say?
#realworldcrypto
(ECDSA/P256 or Ed25519) to post-quantum alternatives on RIOT, say?
#realworldcrypto
PQ signing benchmarks on an ARM Cortex-M4 (not including dyn Dilithium which doesn't fit on the stack on the Sipeed Nano board)
#realworldcrypto
#realworldcrypto

"For larger updates, the network transfer costs overwhelm the other factors." [ looks at SIDH ]
#realworldcrypto
#realworldcrypto
Next up in the threshold crypto session, "A threshold ECDSA protocol: its design
and implementation", by Victor Shoup
#realworldcrypto
and implementation", by Victor Shoup
#realworldcrypto
[ If you want a Schnorr threshold sig protocol instead of ECDSA, can I interest you in FROST? ]
ietf.org/id/draft-irtf-…
#realworldcrypto
ietf.org/id/draft-irtf-…
#realworldcrypto
"The Internet computer", a distributed platform for secure execution of smart contracts, by DFINITY
#realworldcrypto
#realworldcrypto
Doing a preprocessing round allows the latency of a signature to just be one communication round between the parties
#realworldcrypto
#realworldcrypto
If there are thousands of signing keys, it will be hard to efficiently maintain them when there are updates, reshares, etc
#realworldcrypto
#realworldcrypto
ECDSA proven secure in Generic Group Model (GGM) assuming hash is
collision resistant and random preimage resistant (Brown02)
#realworldcrypto
collision resistant and random preimage resistant (Brown02)
#realworldcrypto
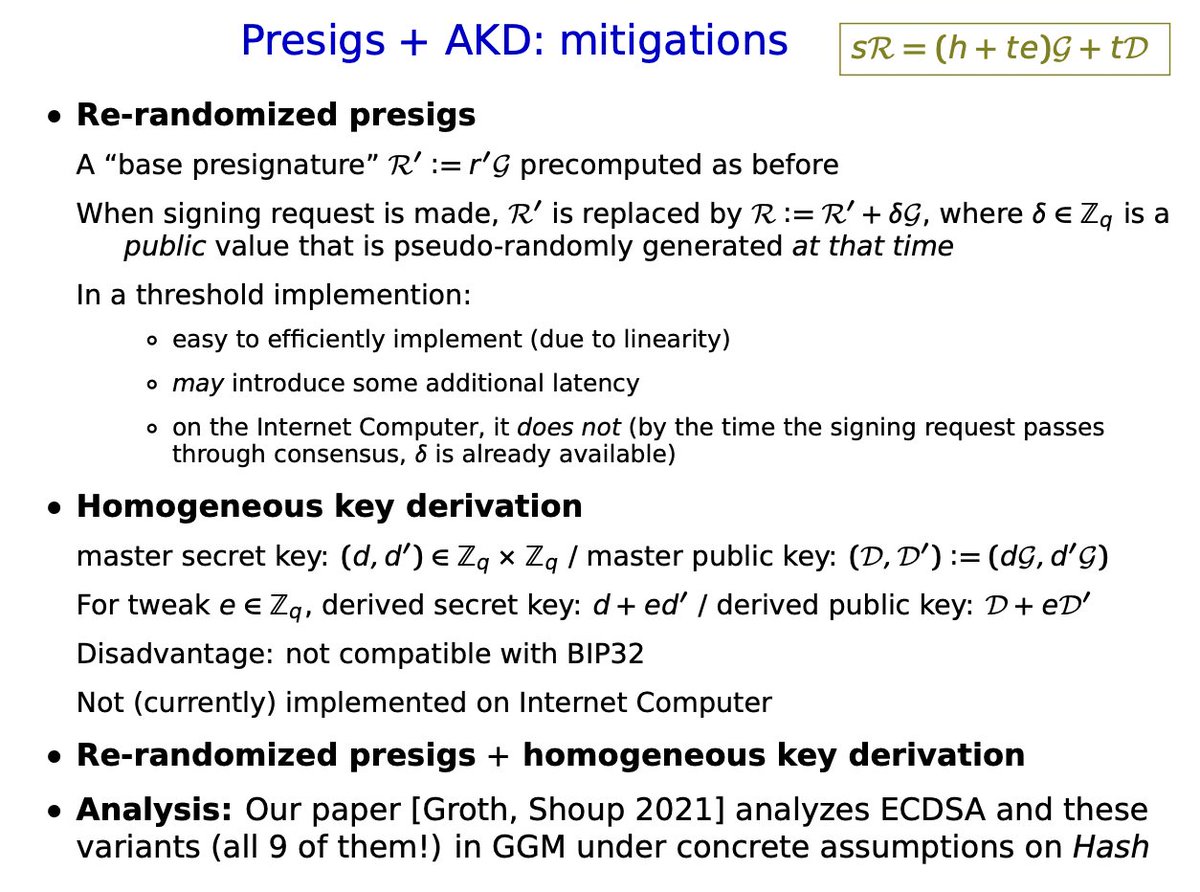
ECDSA w/ additive key derivation: no general security proof results
ECDSA w/ presigs & additive key derivation: no results, despite the desire for it
#realworldcrypto
ECDSA w/ presigs & additive key derivation: no results, despite the desire for it
#realworldcrypto
Works async, byzantine corruptions, guaranteed output delivery, NI online signing, BIP32- style additive key derivation
#realworldcrypto
#realworldcrypto

"• It relies on the Internet Computer’s “Random Beacon” to implement
re-randomized presigs" [ oh.]
#realworldcrypto
re-randomized presigs" [ oh.]
#realworldcrypto
Dedicated servers: many servers, many secrets, each server runs existing protocols many times, slow
#realworldcrypto
#realworldcrypto
For ad-hoc servers, nicer for big systems when sharing between millions of parties, where compute is N²
#realworldcrypto
#realworldcrypto

@kaplannie: if you are reviewing/auditing crypto professionally, meetup in Amsterdam upstairs
#realworldcrypto
#realworldcrypto
"Just a quick plug for the EU Commssions Chat Controls legislative debate and Open Letter to the EU Commissioners, which is online and available @ ChatControlsv2.EU"
#realworldcrypto
#realworldcrypto
For "Drive (Quantum) Safe! --Towards Post-Quantum Security for Vehicle-to-Vehicle Communications", presented by Nina Bindel:
#realworldcrypto
#realworldcrypto

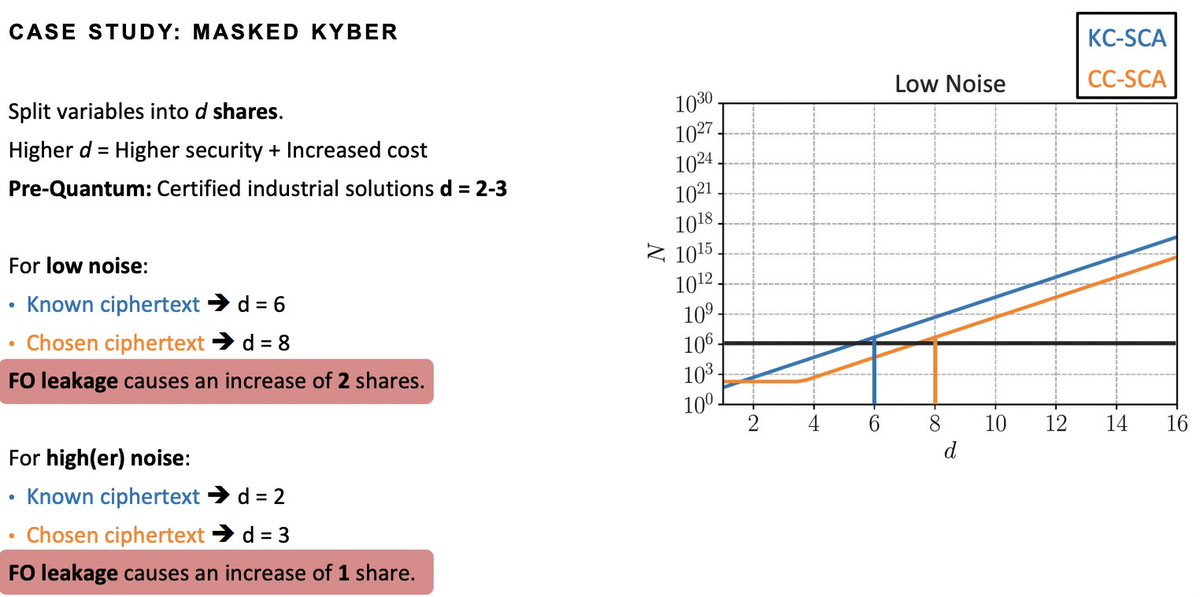
For "Surviving the FO-calypse: Securing PQC Implementations in Practice", presented by Tobias Schneider 👀
#realworldcrypto
#realworldcrypto

The Fujisaki-Okamoto (FO) transformation (or slight variants) underlies the IND-CCA security of many KEMs
#realworldcrypto
#realworldcrypto
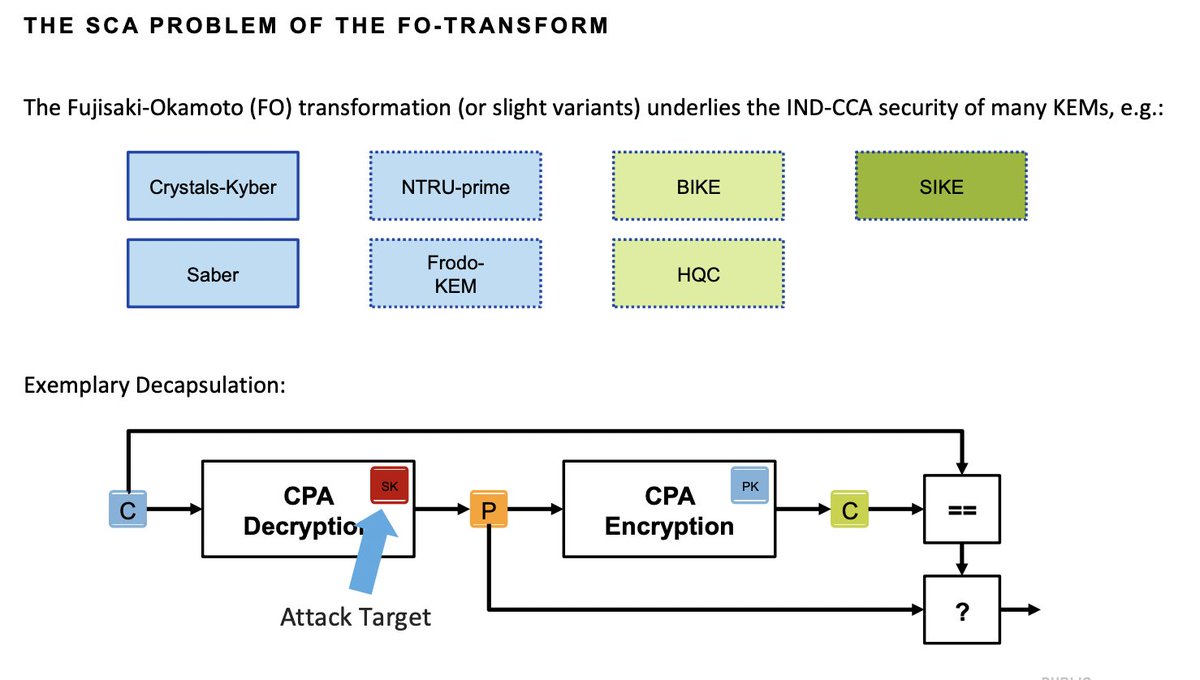
[ I may have to rewind the tape later to capture the pq agility talk ]
Lunch!
[ Is anyone looking at 'better' FO transforms right now? ]
#realworldcrypto
https://twitter.com/durumcrustulum/status/1514907920957378564?t=mW0FzH6KD6yW4s4KKSCI7w&s=19
#realworldcrypto
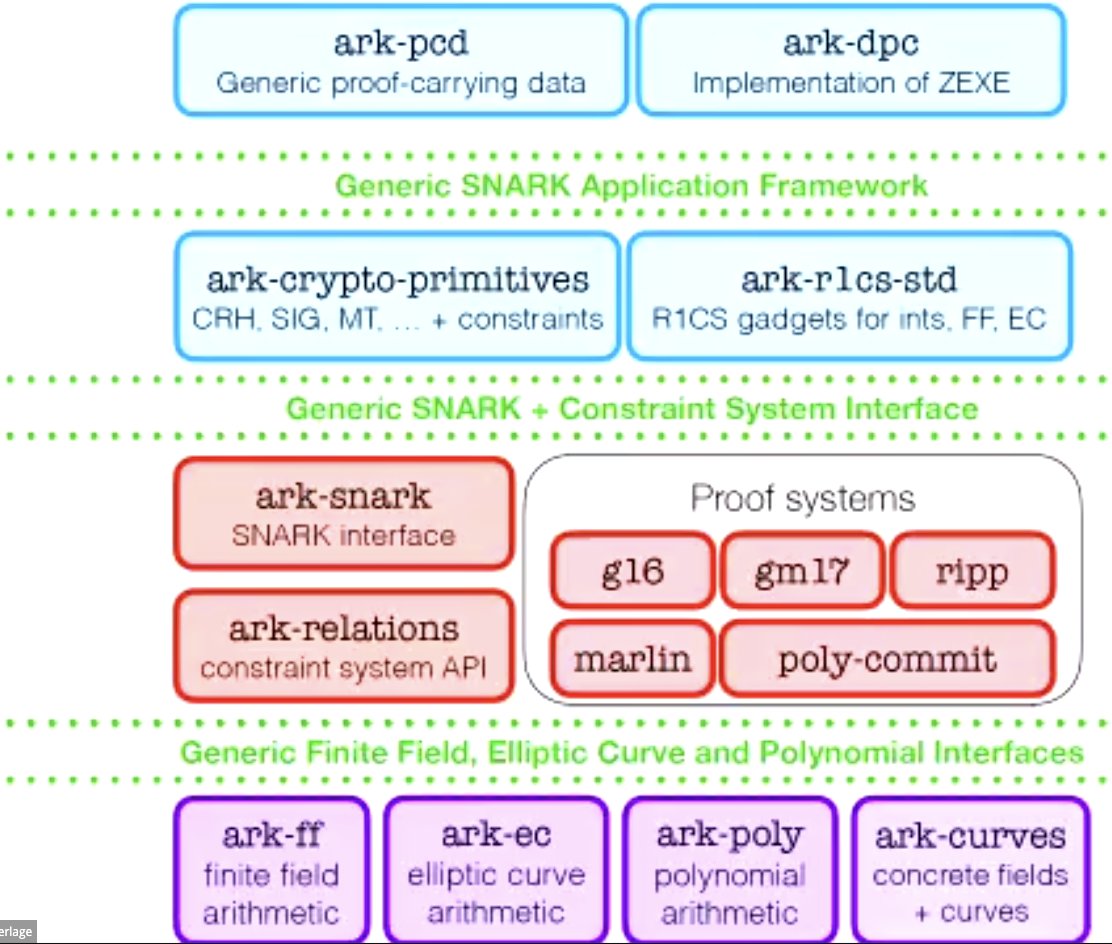
Expressing your zkSNARK is not super easy, there are now many languages and frameworks to express your computation and then compile it down to a constraint system
#realworldcrypto
#realworldcrypto

But:
- tons of duplicate, wasted effort
- optimizations are scatted across libraries
- upgrading becomes hard
- auditing and bugfixes are split
#realworldcrypto
- tons of duplicate, wasted effort
- optimizations are scatted across libraries
- upgrading becomes hard
- auditing and bugfixes are split
#realworldcrypto
@ElectricCoinCo Yes, this does allow higher level proving systems to swap out 'pretty easily'
#realworldcrypto
#realworldcrypto

When the real generally lines up with the pseudocode, this really helps with auditability
#realworldcrypto
#realworldcrypto

Directly programming algebraic constraints is painful 😫
Want to achieve safety, ergonomics, without sacrificing efficiency
#realworldcrypto
Want to achieve safety, ergonomics, without sacrificing efficiency
#realworldcrypto
Q: Language features that would help even more?
A: Const functions, more useful const generics, would allow getting rid of some macros, const expressions aren't on stable yet
#realworldcrypto
A: Const functions, more useful const generics, would allow getting rid of some macros, const expressions aren't on stable yet
#realworldcrypto
Q: How can you help prevent mixing and matching in insecure ways?
A: Only so much you can do, but, curve interfaces only let you construct prime order group elements, but also depends
#realworldcrypto
A: Only so much you can do, but, curve interfaces only let you construct prime order group elements, but also depends
#realworldcrypto
Q: Audited? Projects using arkworks been audited?
A: Various of those have been audited, latest codebase will be getting audited after some refactors, stabilization
#realworldcrypto
A: Various of those have been audited, latest codebase will be getting audited after some refactors, stabilization
#realworldcrypto
Q: Plonk?
A: 3 external ones relying on arkworks to impl Plonk, arkworks doesn't have its own Plonk impl yet
#realworldcrypto
A: 3 external ones relying on arkworks to impl Plonk, arkworks doesn't have its own Plonk impl yet
#realworldcrypto
Q: Governance model of arkworks?
A: Definitely, we're just starting to think about that, now that we're big enough
#realworldcrypto
A: Definitely, we're just starting to think about that, now that we're big enough
#realworldcrypto
Q: Why new curve params?
A: We needed recursion, and Twisted Edwards are very efficient for circuits
#realworldcrypto
A: We needed recursion, and Twisted Edwards are very efficient for circuits
#realworldcrypto
Q: Moving to the record model, does this affect access patterns and impact privacy?
A: Not functional privacy but data privacy, can see which applications are popular, the parties using them and the data used are not revealed 👀
#realworldcrypto
A: Not functional privacy but data privacy, can see which applications are popular, the parties using them and the data used are not revealed 👀
#realworldcrypto
Leo language helps write code to compile to assembly then R1CS to make it even easier for developers: github.com/AleoHQ/leo
#realworldcrypto
#realworldcrypto
Expressing complex logic is often too slow and hard to do on-chain, so to do it off-chain, with a transparency log, helps achieve that
#realworldcrypto
#realworldcrypto
Coffee time!
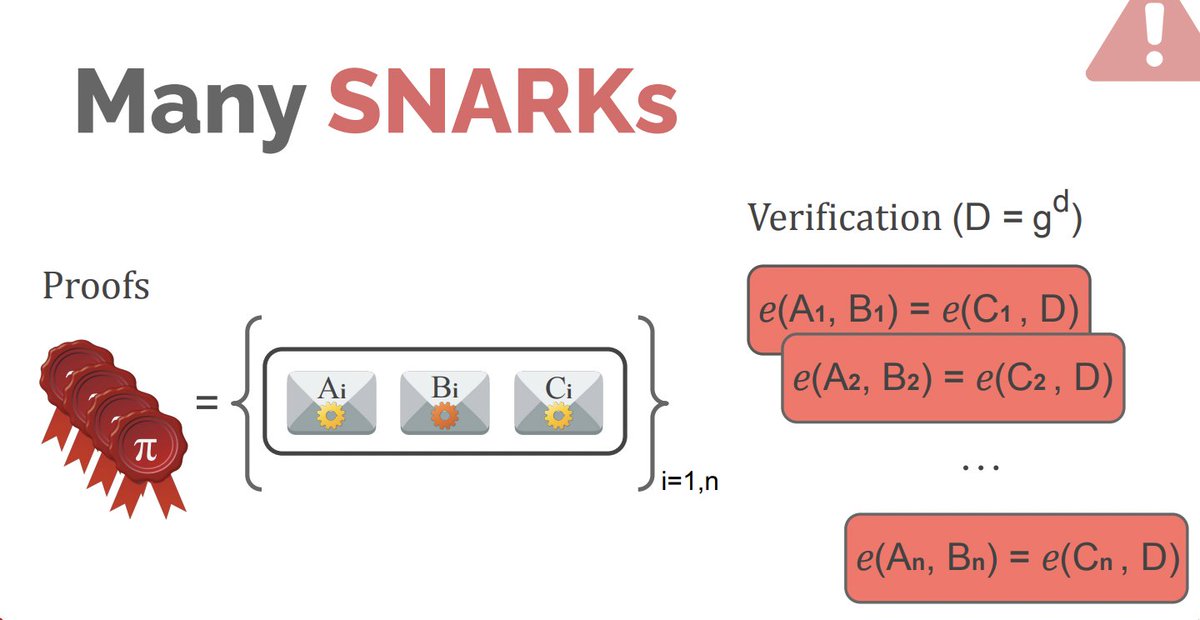
[ If you need fast batch verification of Groth16 proofs, I upstreamed an implementation to the bellman library: github.com/zkcrypto/bellm… ]
#realworldcrypto
#realworldcrypto
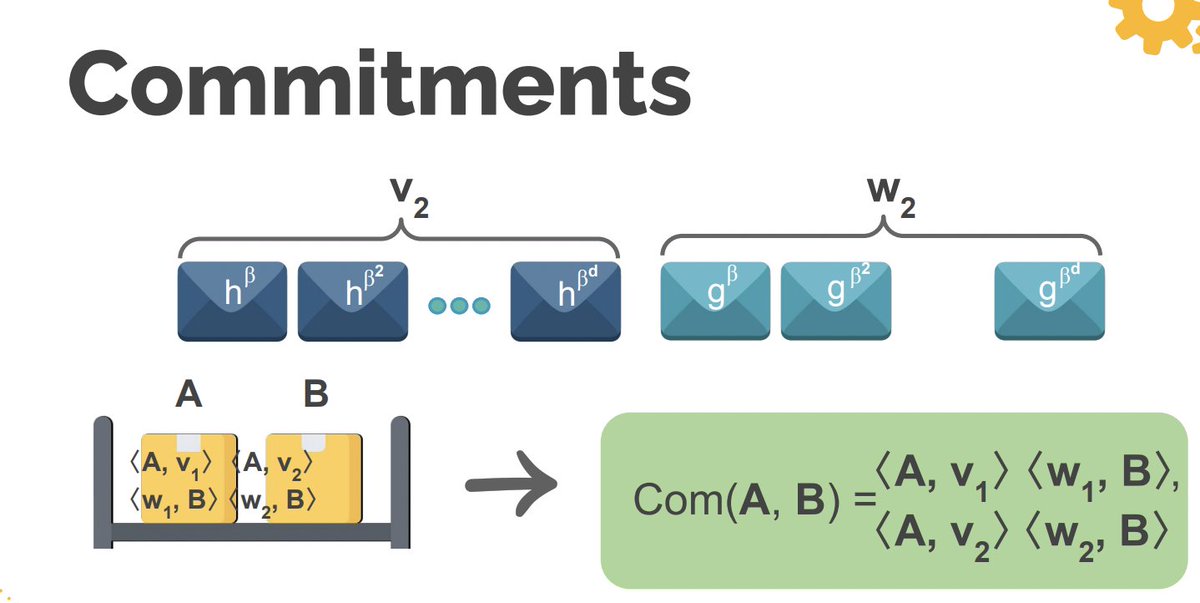
Instead of pushing this math to the verifier, the prover will do a lot of it themselves:
#realworldcrypto
#realworldcrypto
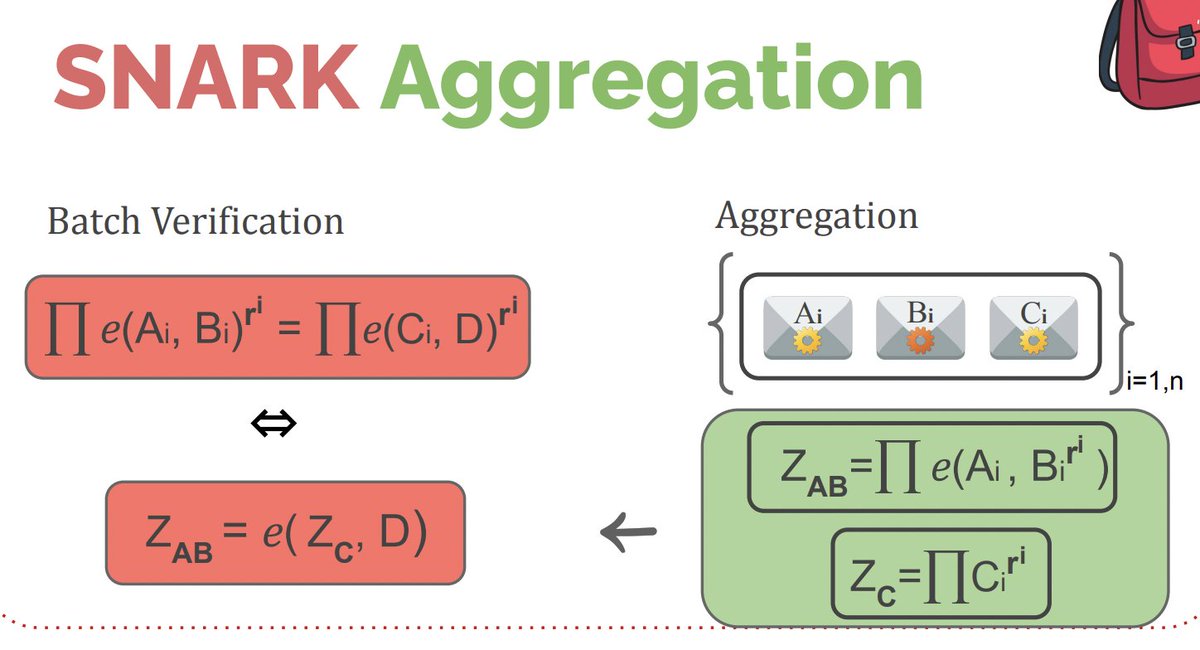
- bootstraps from existing trusted setup CRS's
- transparent aggregation
- optimized
- Could we extend this to other pairing-based schemes, besides Groth16?
#realworldcrypto
- transparent aggregation
- optimized
- Could we extend this to other pairing-based schemes, besides Groth16?
#realworldcrypto
Requirements:
- Don't weaken encryption
- Able to enforce policies as before
- No server changes
#realworldcrypto
- Don't weaken encryption
- Able to enforce policies as before
- No server changes
#realworldcrypto
eg, only 51% of TLS servers are providing TLS 1.3, whereas 80+% of Chrome clients are speaking it
#realworldcrypto
#realworldcrypto
"We don't want to prevent circumvention by advanced users", which could be misused for censorship
#realworldcrypto
#realworldcrypto
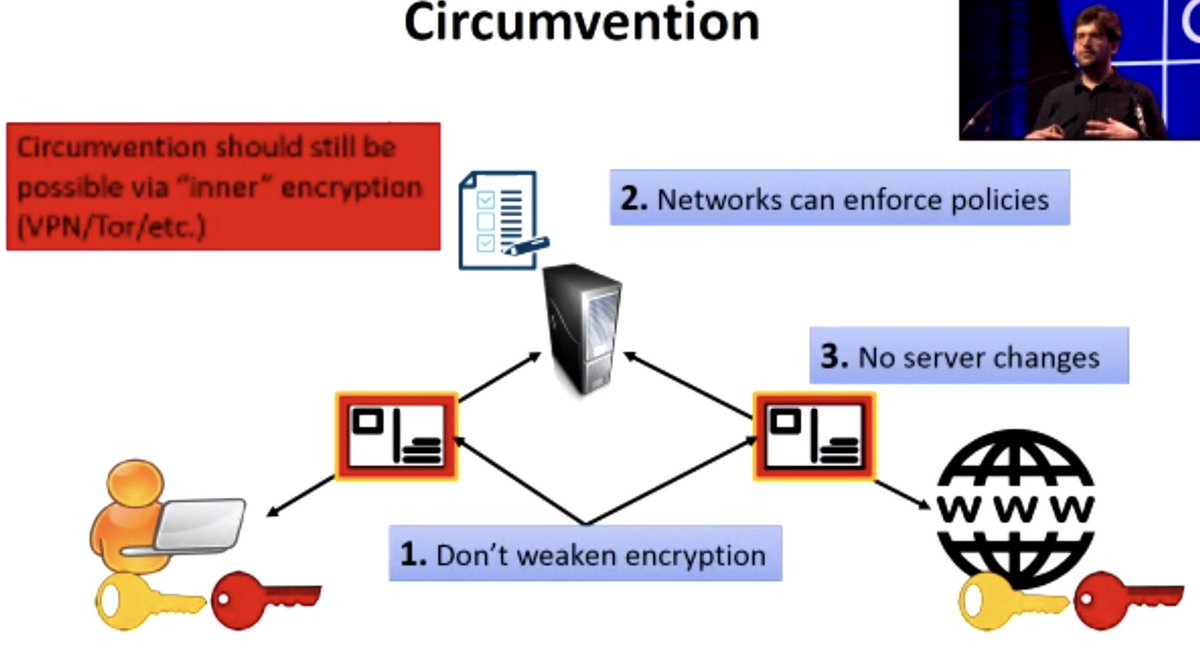
Proof prevents the client from lying, and middlebox strips out the proofs when it forwards on the traffic to the server
#realworldcrypto
#realworldcrypto
Output the plaintext is the AEAD decryption succeeds, but the TLS 1.3 AEADs are not _binding_, ciphertexts can have multiple correct decryptions
#realworldcrypto
#realworldcrypto
Re-run the key derivation inside the circuit - the handshake 'commits to' the intermediate steps of key derivation, check these instead to shortcut key derivation
#realworldcrypto
#realworldcrypto
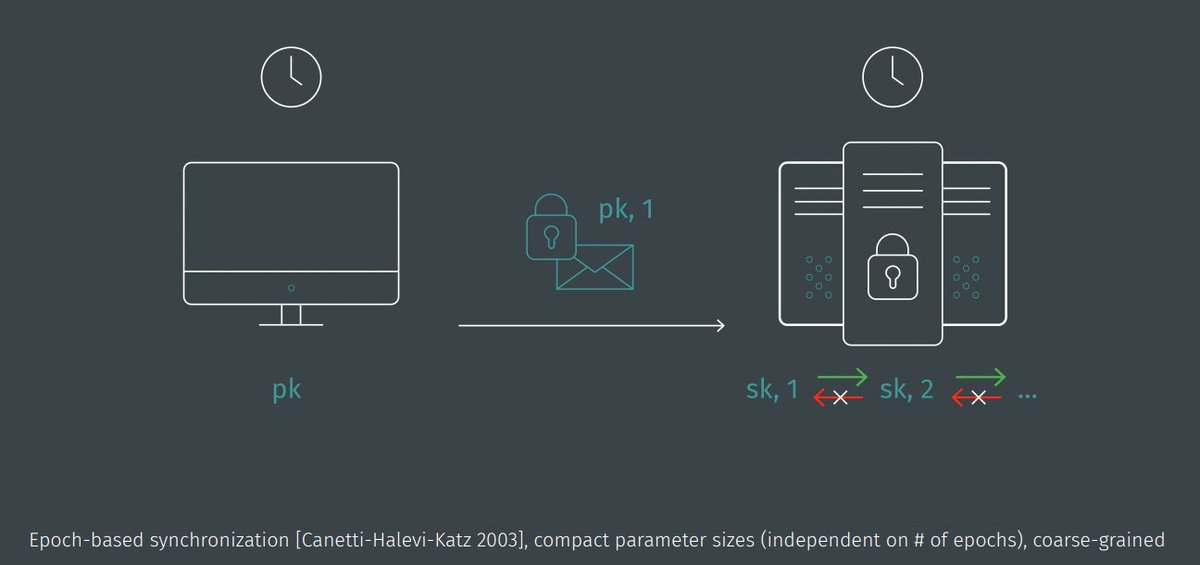
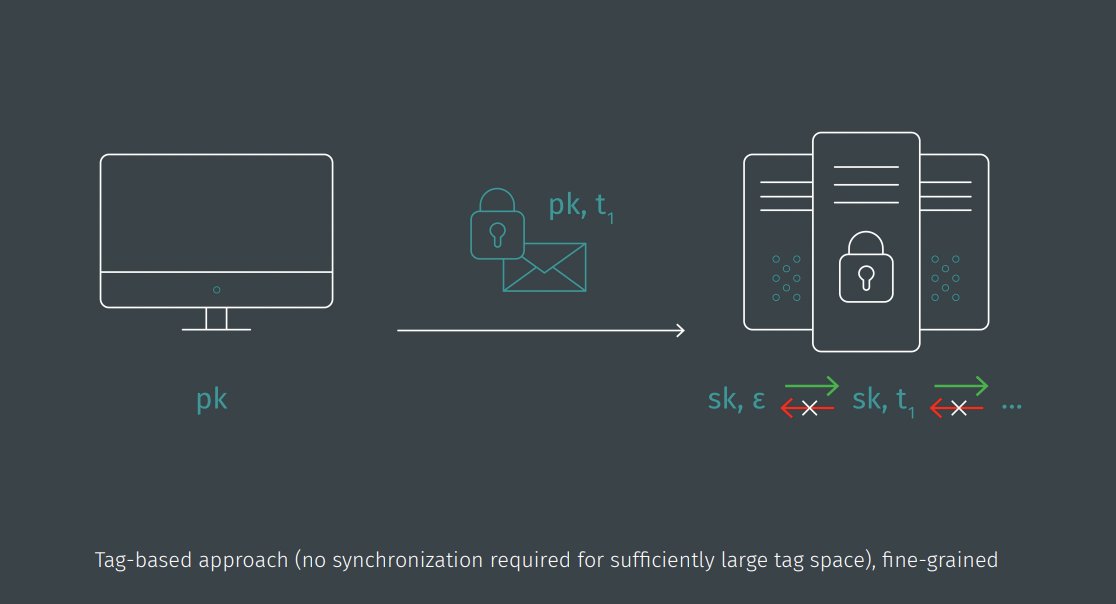
Next up, "Puncturable Encryption – A Fine-Grained Approach to Forward-Secure Encryption and More", presented by Christoph Striecks
#REALWORLDCRYPTO
#REALWORLDCRYPTO
#REALWORLDCRYPTO 2023 will be in Japan! March 27-29
And we're done! 👋
</fin>
</fin>
#realworldcrypto
https://twitter.com/matthew_d_green/status/1514999138227732486?t=M7TGjraUCfK21oTDPUfSqA&s=19
• • •
Missing some Tweet in this thread? You can try to
force a refresh