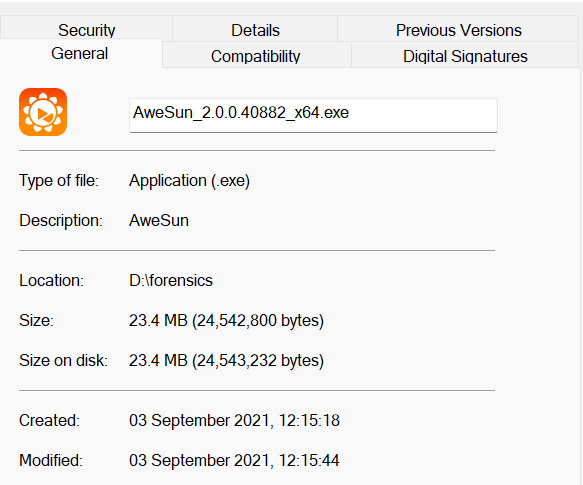
A friend's father had his PC taken over by scammers.... just doing a bit of forensics on it to work out what happened.
First sign is a download of amazon_security.exe which is actually Supremo Remote Desktop. supremocontrol.com

First sign is a download of amazon_security.exe which is actually Supremo Remote Desktop. supremocontrol.com

Anydesk log - interesting name on that incoming session request.
Any "direct scam paid 3" on the connection flags?
Any "direct scam paid 3" on the connection flags?

Log files are a bit all over on Anydesk, but this inbound connection is from 103.220.18.194.
Kolkata, India.
shodan.io/host/103.220.1…
Kolkata, India.
shodan.io/host/103.220.1…

The IP has Sonicwall exposed to the Internet which is a bit odd.
I believe ad.roster.items in user.conf for Anydesk are recent sessions made.
That's a lot of sessions - is this a logged in account that lets us see what the scammers are doing?
That's a lot of sessions - is this a logged in account that lets us see what the scammers are doing?

They do seem to have stored a couple of passwords in Edge's password safe. Not sure how to trivially access that from an image, might need to boot from an image.
Deeply tempted to spin this up on a danktop with a keylogger installed and grab all the passwords they are using.
The Anydesk session appears to allow switch_sides and filetransfer both ways. High risk for them?
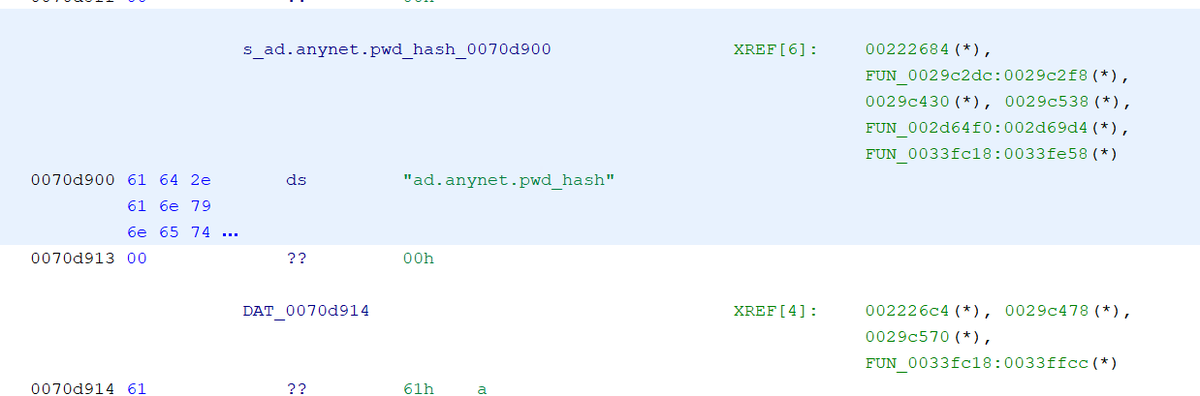
Jesus, Anydesk is just a massive monolithic binary in Windows... going to be a real pain to reverse that hash algorithm.
cheesedog123 gives this hash. Salt changes each time.
ad.anynet.pwd_hash=c81e58dc07bfb2dc42e5bffd47f25d7d17d870e673895bee99b36d6c28bd3960
ad.anynet.pwd_salt=2170a3c5bfd1728bb098f4fdcabfd6ea
ad.anynet.pwd_hash=c81e58dc07bfb2dc42e5bffd47f25d7d17d870e673895bee99b36d6c28bd3960
ad.anynet.pwd_salt=2170a3c5bfd1728bb098f4fdcabfd6ea
Surprised no one else has looked into this before.
Annoying that it's a monotlithic binary, some imports would make this much easier.
Annoying that it's a monotlithic binary, some imports would make this much easier.

Thanks to @LennertWo and a memory dump into this function from Frida and we have the hash function worked out.
It's sha256(password + null + salt)
I thought I tried that but must have made a mistake.
It's sha256(password + null + salt)
I thought I tried that but must have made a mistake.

I think we can coerce hashcat into doing this by putting a null at the beginning of the salt...
One moment please.
One moment please.
Ok - parallel to this, I've pulled the passwords from Edge. They are the same and of the form Word123.
They used the user's email address on several money transfer platforms.
The pass works.
They used the user's email address on several money transfer platforms.
The pass works.
I now have the Anydesk password as well.
longerword123
This is falling apart quite quickly.
longerword123
This is falling apart quite quickly.
I have a train to catch, back later!
• • •
Missing some Tweet in this thread? You can try to
force a refresh