Sometimes you find something so disturbing during an audit, you've gotta check/recheck because you assume that *something* must be broken in the test.
But I'm confident now.
The new @DuckDuckGo browsers for iOS/Android don't block Microsoft data flows, for LinkedIn or Bing.🧵
But I'm confident now.
The new @DuckDuckGo browsers for iOS/Android don't block Microsoft data flows, for LinkedIn or Bing.🧵
DuckDuckGo has browser extensions & their own browsers for iOS / Android @ duckduckgo.com/app
iOS @ apps.apple.com/us/app/duckduc…
Android @ play.google.com/store/apps/det…
Both versions of the DDG browser claims to use tools which
"automatically blocks hidden third-party trackers" 👀


iOS @ apps.apple.com/us/app/duckduc…
Android @ play.google.com/store/apps/det…
Both versions of the DDG browser claims to use tools which
"automatically blocks hidden third-party trackers" 👀



If you download the current version of the DuckDuckGo browser for iOS/Android, & if you hope this browser actually stops data transfers to super common advertising subsidiaries owned by a company like Microsoft... well too bad, the browser has a secret allow data flow list 👀🤡
I don't have the full list of advertising domains that the DuckDuckGo browser is allowing to collect data within their new "private" browser ((anyone have that or parsed it somewhere??) but any list that doesn't include "linkedin[.]com" + "bing[.]com" is *purposefully* broken.
It's public knowledge that DuckDuckGo has been creating exemptions for Microsoft for awhile, which they've been required to explain on a page like @ help.duckduckgo.com/duckduckgo-hel… / DDG openly says they are sending your user IP address & user agent to Microsoft for the DDG ads on-click. 
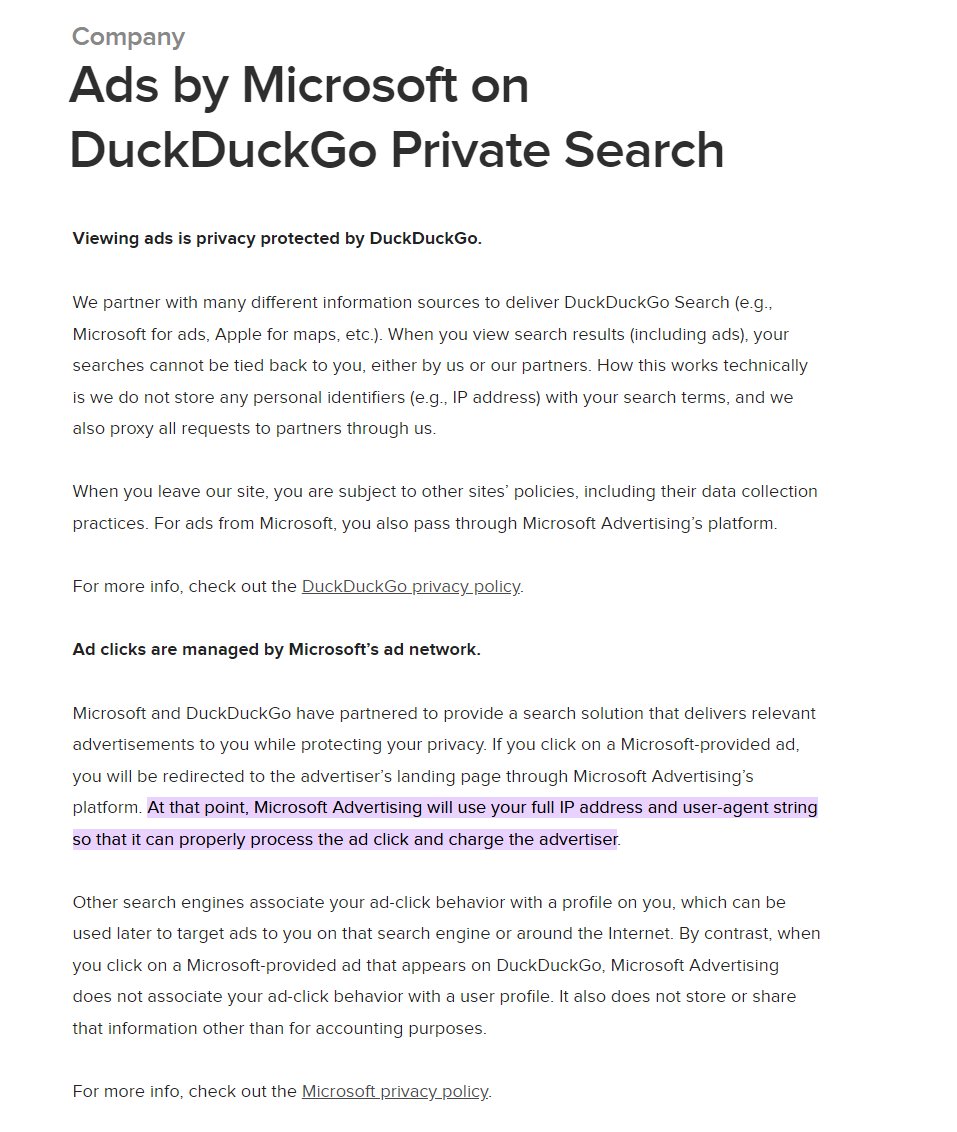
But you won't find any public articles from DuckDuckGo explaining *why* they are not blocking Microsoft-owned 3rd party data flows on websites *not* owned by Microsoft, like on Facebook's Workplace[.]com domain sending data to Bing & Linkedin in the DDG "private" browser. 👀🤡⛈️
I tested the DuckDuckGo so-called private browser for both iOS and Android, yet *neither version* blocked data transfers to Microsoft's Linkedin + Bing ads while viewing Facebook's workplace[.]com homepage.
Look at DDG bragging about stopping Facebook on Workplace, no MSFT..:
Look at DDG bragging about stopping Facebook on Workplace, no MSFT..:
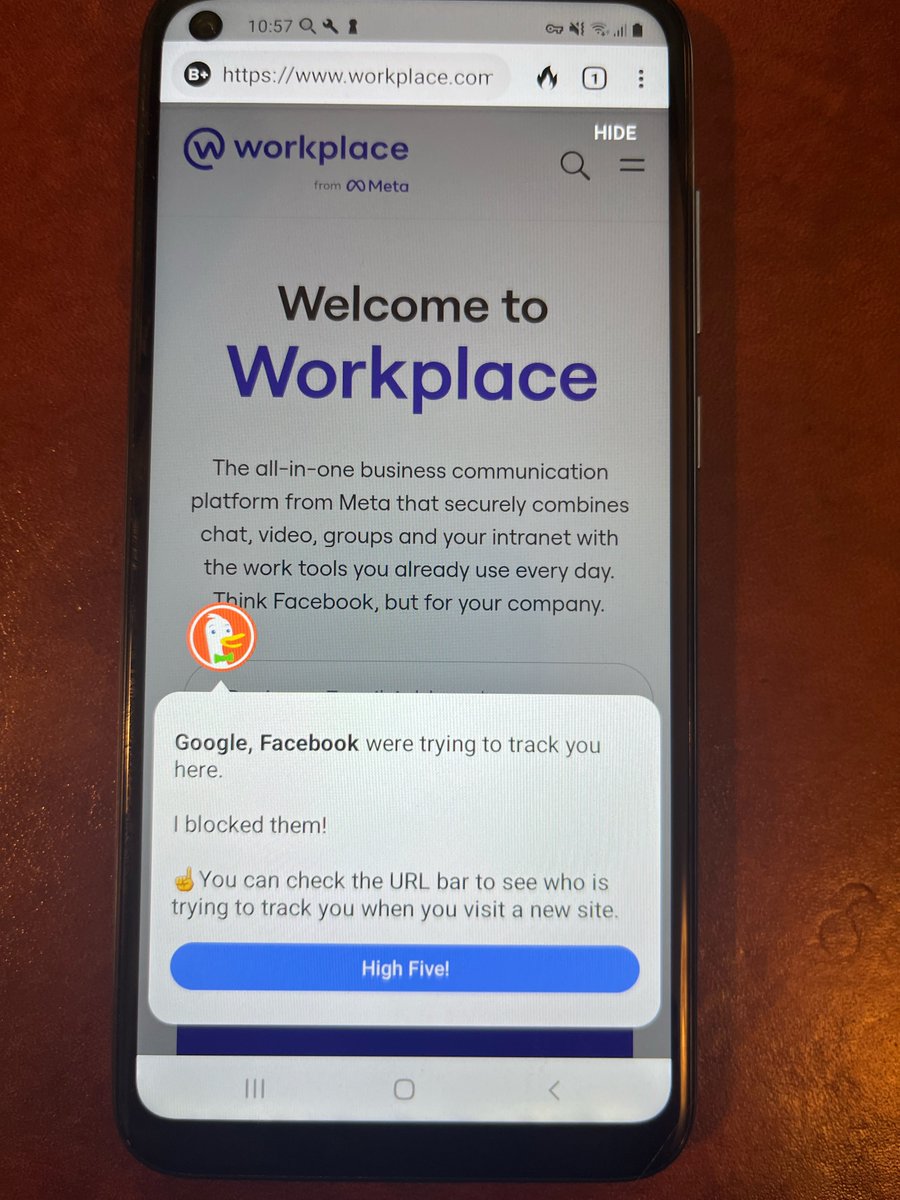
You can capture data within the DuckDuckGo so-called private browser on a website like Facebook's workplace.com and you'll see that DDG does NOT stop data flows to Microsoft's Linkedin domains or their Bing advertising domains.
iOS + Android proof:
👀🫥😮💨🤡⛈️⚖️💸💸💸

iOS + Android proof:
👀🫥😮💨🤡⛈️⚖️💸💸💸
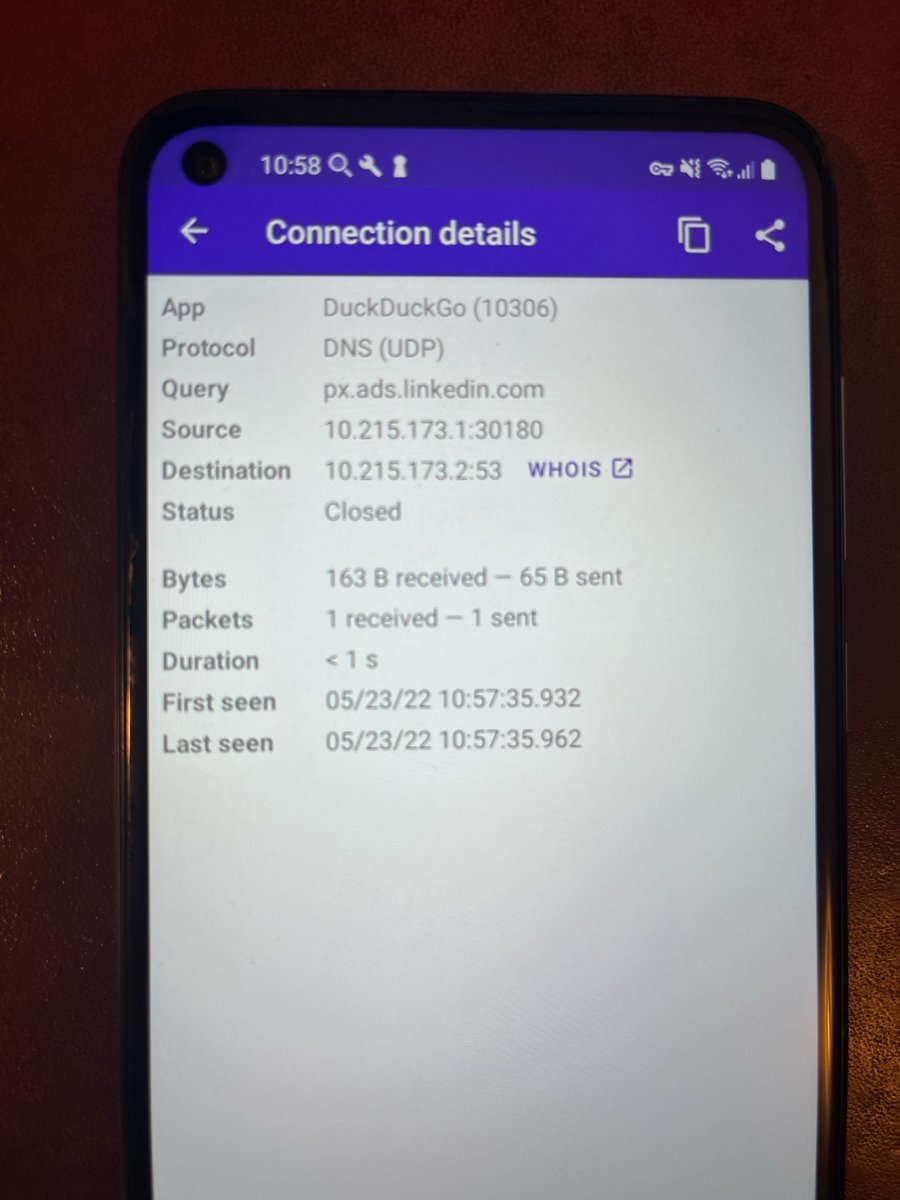
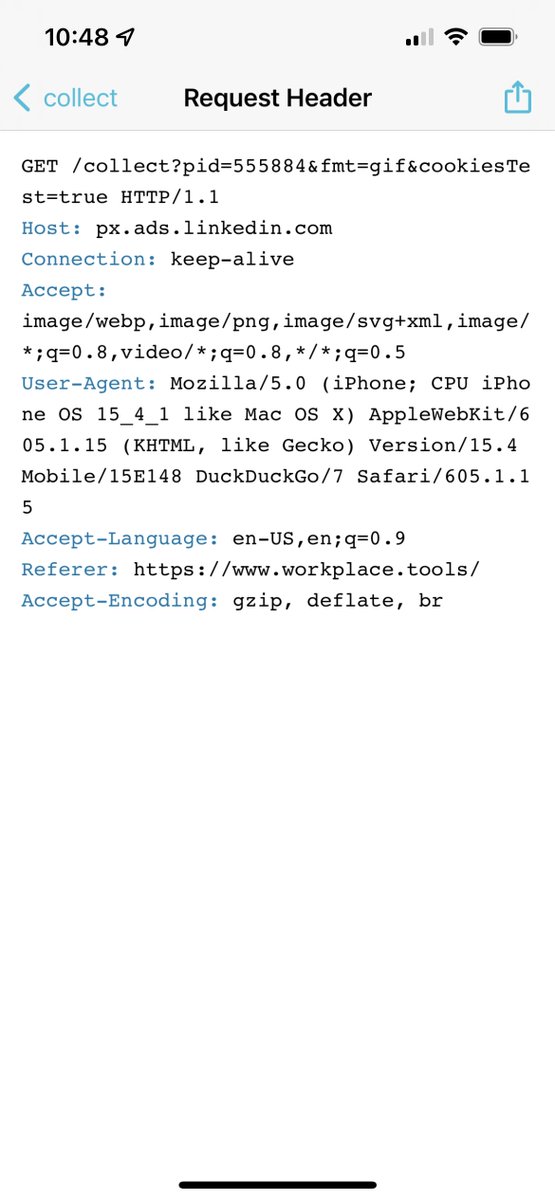
And you can see proof that the DuckDuckGo team *knows* that Microsoft's domains are crossite tracking vectors @ raw.githubusercontent.com/duckduckgo/tra… - that's the DDG feedback loop to help them populate blocklists.
So if DDG's researchers *know* MSFT/Bing/Linkedin=tracking, why exclude them?
So if DDG's researchers *know* MSFT/Bing/Linkedin=tracking, why exclude them?
So another question to ask: if you were a DDG privacy researcher who knew that Microsoft has a variety of domains they use for cross-site tracking to optimize their ads systems, and you already knew that DDG was giving IP address & UA string data to MSFT, did you know this too?👀
And if you are a privacy researcher working at DDG, do you think it's appropriate to push rhetoric about why this is a good browser, knowing that there are global data brokers - your own partners - who you are purposefully not stopping data flows for, on domains they don't own?🆒
Personally, I think that both Google & Apple have an obligation to users within their app marketplaces to remove apps which claim to do X, Y, Z, but do the opposite, merely because it makes the parent company more money.
If you say you block 3rd party data flows, *do that* ...
If you say you block 3rd party data flows, *do that* ...
There are a variety of lists from DuckDuckGo to help parse this, like "Domains which should have cookie protections disabled due to site breakage issues" github.com/duckduckgo/pri… - which includes the bat.]bing.]com domain but does NOT include the Linkedin domain, so 100% unclear:
I don't think there is a public list of *all* the domains that the DuckDuckGo browser is *not* blocking, but they seem to be doing this w/ hardcoded rules. The DDG browser stops data flows from tons of domains.... except DDG's #1 ad tech partner.
Mysterious! 🤡⛈️⚖️📴📴
Mysterious! 🤡⛈️⚖️📴📴
I won't hold my breath that DuckDuckGo will update their own so-called private browser to actually stop data flows to their own ad tech partners, but this is one of those things that makes a privacy auditor ... annoyed? bitter? confrontational?
Does Google / Apple care? </🧵>
Does Google / Apple care? </🧵>
• • •
Missing some Tweet in this thread? You can try to
force a refresh













