
Ok... It's the time of year I treasure. @VZDBIR reading at a coffee shop. This is going to be a live thread of love for DBIR, folks like @alexcpsec and @gdbassett, footnotes, and exciting uses of data visualization. 1/x 

First: @VZDBIR predictions pre-reading
- Ransomware up! Thus making intrusions up! (Shocker,Malware that tells you you are infected makes for better detection)
- Increased threat to OT (colonial)
- BEC is actually the real threat
- APTs reduced in volume but higher in impact 2/x
- Ransomware up! Thus making intrusions up! (Shocker,Malware that tells you you are infected makes for better detection)
- Increased threat to OT (colonial)
- BEC is actually the real threat
- APTs reduced in volume but higher in impact 2/x
Ahhh right off the bat. Can we just do this to begin every ppt, whitepaper, blog and conference talk? Then add definitions of Risk, Vulnerability, and Threat? Would be nice to educate.folks 3/x 

A whole section explaining Viz used is huge! The viz used in DBIR is always top notch and is multivariate. I don't expect I'll see a stupid 🥧 chart at all. Only quibble? The use of green/yellow may be hard on folks with deutan color vision deficiency. Aka color blind 4/x 

Summary is clean and crisp.
- creds&phishing top method of access (no surprise and prolly have causation/correlation)
- ransomware up up up!
- supply chain up! How much of that is active/required #log4shell reporting tho
- humans are bad at security
- misconfigured cloud bad 5/x
- creds&phishing top method of access (no surprise and prolly have causation/correlation)
- ransomware up up up!
- supply chain up! How much of that is active/required #log4shell reporting tho
- humans are bad at security
- misconfigured cloud bad 5/x

There (imo) is a HUGE over rotation to insider vs external. I've always had that anecdotal feeling but DBIR brings the data bar charts. Lots of defensive overlap on both but I feel like the need for insider threat detection is often emotionally motivated not data. 6/x 

Saying that, insider is MUCH harder to detect imo due to being already inside perimeter and lack of defense-in-depth/crown jewel at most orgs. DBIR alludes to this as well. 7/x
Saying that, apparently the number of records stolen by insiders is 10x vs external! Makes sense. Insiders have more access by default and may just grab "everything" rather than being precise. But then again, if all you need is patents.docx, 1 file is as valuable as 375k 8/x 

A wild @alexcpsec appears and points out the wrong screenshot. Its now... Worse? 9/x 

I often have folks ask where they should start/prioritize their defenses. I tell them to look at the last 5 years of incidents in their own organization. If you don't have that, use someone else's data:
- web apps
- spear phishing
- stolen creds
Are great places to start
10/x

- web apps
- spear phishing
- stolen creds
Are great places to start
10/x


Favorite footnote so far? I'm hoping for an @alexcpsec Pinto Principle later... 11/x 

Hmm looks like one of my predictions will fall flat due to lack of data. Although... Flip that frown upside down?
BREAKING FOX NEWS: VZDBIR REPORTS A 200% YoY INCREASE IN OT BREACHES. @RobertMLee UNAVAILABLE FOR COMMENT DUE TO PREVIOUS @Davos COMMITMENT 12/X
BREAKING FOX NEWS: VZDBIR REPORTS A 200% YoY INCREASE IN OT BREACHES. @RobertMLee UNAVAILABLE FOR COMMENT DUE TO PREVIOUS @Davos COMMITMENT 12/X

This shows how powerful modern viz is! I love seeing how parent card data has dropped but creds increase. .
As someone once said: You don't hack the cloud, you log into it.
C. reds
R. ule
E. verything
A. round
M. e
13/x
As someone once said: You don't hack the cloud, you log into it.
C. reds
R. ule
E. verything
A. round
M. e
13/x

70% of reported malware in breaches with ransomware. Once again, it's just not surprising to me because Ransomware tells you that it's on your system. The whole goal of APT malware is to stay hidden. Saying that, quantity has a quality all to it's own 14/x 

This live 🧵 paused as I cycle home. I'll wave to cyber pros @sroberts and @pseudohvr as I cruise their neighborhoods 

Ok. Live thread back on with my office supervisor. @ajohnsocyber knows what this is all about #cyberdoglife 

Ok. This is my favorite page in the report so far. I believe it clearly illustrates my feelings about ransomware disclosures skewing data to look better than it is. Also that Event Chain data is 👨🍳😘. Review work by @CERTNZ wrt that data and ransomware for more goodness 15?/x 

This is also one of the most useful pages but probably the hardest for non advanced shops to action. Harkening back to LM cyber kill chain (25¢ for you @killchain) increasing cost (time/effort/$) of attack to adversary is the only way imo to long term reduce targeting. 16/x 

Hmmm interesting though for threat hunters who are looking for ways to group their hunts. @DavidJBianco thoughts of bucketizing by @VZDBIR prioritizes incident classifications? 17/x 

I too can use markers @gdbassett 18/x 😘 

Back at it. I can't emphasize enuff how useful this data can be for strategic planning. Either as a "this is a great place to start" or "this doesn't match with our data". The @VZDBIR does a great job of calling out "Partner" as being a possible outlier due to "PolarShins" 19/x 

Can you rip apart an office doc? Do you have advanced integrated malware tools in your email pipeline? Calling @DidierStevens and tools like #laikaboss and #stoQ
Oh...and Ransomware. @splunk knows a little.a out that don't we @DrShannon2000 / @d1vious 20/x
Oh...and Ransomware. @splunk knows a little.a out that don't we @DrShannon2000 / @d1vious 20/x

That footnote tho... "With the median organization receiving over 75% of its malware via email." I have to say if you're only depending on your email provider or software to protect you... You are just going to have a bad day 21/x
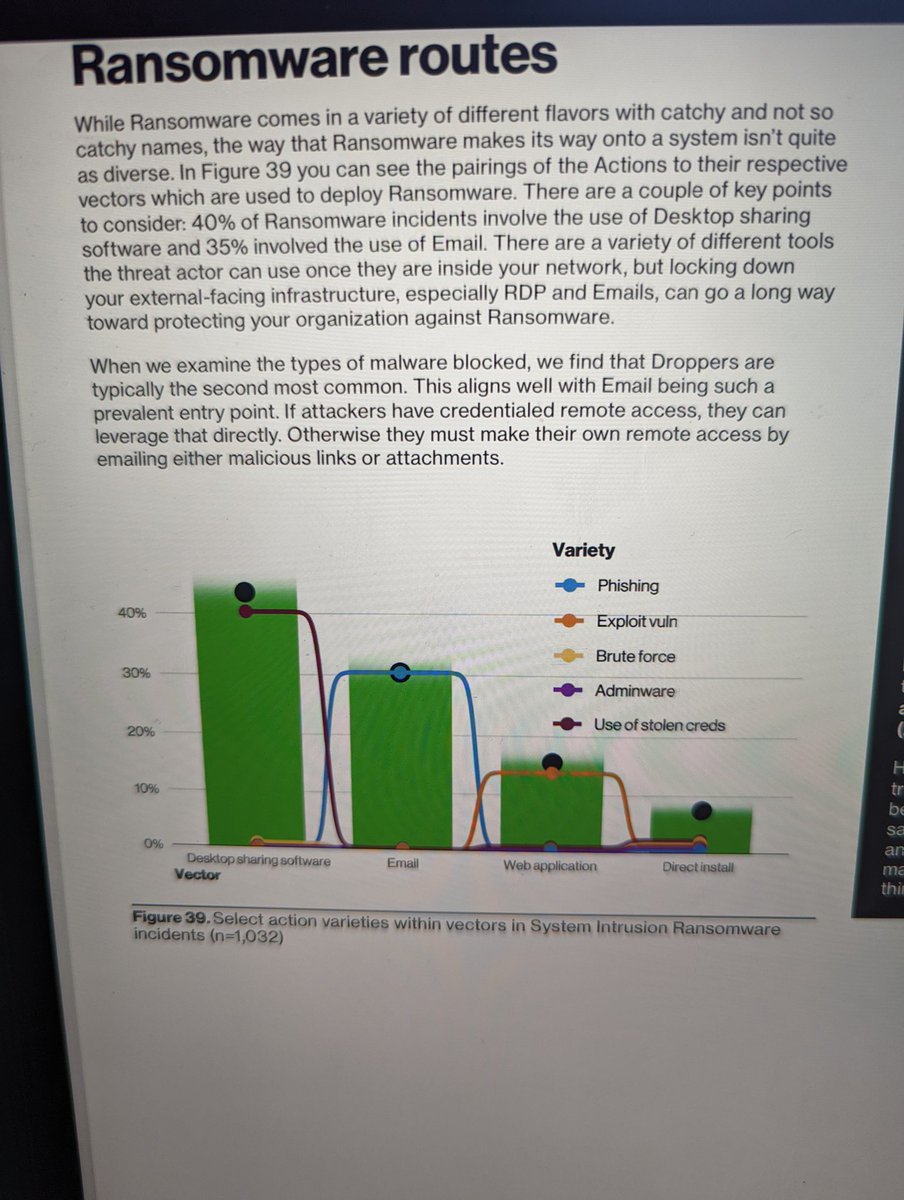
100% this. If you are still thinking of ransomware as just something that self-propagates and is used in isolation you could not be more wrong. That ransomware binary has to go on the system somehow and apparently it's mostly RDP or email. Again @CERTNZ / @DrShannon2000 ftw 22/x 
OK. Final meeting of the day is done. Now I can finish this off. One thing I like doing for VZDBIR is "reoccurring thingies" (a technikal Kovarian term). Big thingie this year? CREDS CREDS CREDS
C. reds
R. ule
E. verything
A. round
D. BIR
23/x
C. reds
R. ule
E. verything
A. round
D. BIR
23/x

Another great footnote.
"12 And by average, we mean median because statistics isn’t hard enough already. Mode."
I wonder how many people realize my Twitter handle is a stats joke?
24/x
"12 And by average, we mean median because statistics isn’t hard enough already. Mode."
I wonder how many people realize my Twitter handle is a stats joke?
24/x
As the world of attacks is more financially motivational there absolutely needs to be more consideration for the interdisciplinary study of TTPs. We already say that RAAS acts like biz, time to start using models & lessons learned from places like business and marketing. 25/x 

Interesting work on the value of IOCs. Hashes a higher value than I would've thought. IPs if you block them fast can have high value but gotta be fast. Also are these citations or footnotes! Either way shoutout to @DavidJBianco. Also, do I smell some tiq-test @alexcpsec? 26/x 



For those who aren't aware, this tiq-test was some great work on measuring the speedy efficacy of IP threat data. Great work by Alex and @kylemaxwell. Take a peek! media.defcon.org/DEF%20CON%2022… 27/ 

The human element continues to be a key driver of 82% of breaches and this pattern captures a large percentage of those breaches.
Key take away here? Get rid of your users. 28/x
Key take away here? Get rid of your users. 28/x
Hey CREDS and BEC! My DBIR bingo card is filling up. As @iHeartMalware has been testifying for years, BEC is the silent killer of businesses around the world. 100k here, 100k there, suddenly we are talking a reverse engineer's salary worth of financial loss to a company! 29/x 

Training is a key tool for reducing the attack surfaces of an org. I did a whole Masters' thesis on this at @UniWestminster. But its time to value is fleeting and has to be done often. Also, 99 emails were reported but 1 was opened by a domain admin? I still believe tho 30/x 

@UniWestminster Heyyy Web app attacks. #1 action variety?
C. reds
R. ule
E. verything
A. round
M. e
Sorry I love that joke. @VZDBIR I give you permission to use it in footnotes or text of VZDBIR2023.
31/x
C. reds
R. ule
E. verything
A. round
M. e
Sorry I love that joke. @VZDBIR I give you permission to use it in footnotes or text of VZDBIR2023.
31/x

If you are only focusing on patching and not watching password spray, brute force, low/slow... you are gonna have a bad day. Also great use of viz... once again.
32/x
32/x

Since I am live-tweeting I'm not looking at data but I _assume_ that the breaches of email servers referenced here are not inclusive of o365/gmail/geocitymail but rather on-prem. Real value adds moving to those sort of hosted platforms, especially post #hafnium. 33/x 

Buuut, lots of orgs have buried SMTP servers that are automating forgotten processes or MNA exchange servers floating around. Just cause you _think_ you are a corporate cloud email provider doesn't mean your users aren't hiding from you. Please refer to tweet 28/x above. 34/x
Anecdotally this jives with me. Feels like for a couple years S3 buckets were dropping every minute. We did a #BossoftheSOC and halfway through @awscloud just solved the problem and started stopping our fun. Seems like this has dropped off a fair bit and data shows it 35/x 

I used to ask people in interviews "how would you block DDOS in your environment?" The only acceptable (IMO) answer (unless you work at a CSP) is "pay more money to your CDN or call your ISP to move IPs." Doesn't seem like that's changed TBH 36/x 

We are well into the flyover country of the DBIR but I love this graph. A perfect example of how context matters. The DBIR team calls this out in text, but can anyone guess why... stolen or lost assets kind of went weird in 2021? Hmm. 37/x 

Attacks on Mobile devices happen but I go back to the data again, if you are spending your time/money focusing on mobile threats & ignoring streamlining your email malware detections (which would help your mobile problem) you are probably(?) better off reassessing your focus.38/x 

I'm going to gloss over the "industries" section of the report, but it's important to point out... this is how you share data. You provide the data, you show your biases, and you explain how you got your conclusions. @VZDBIR sets the industry standard for this IMO 39/x 

@VZDBIR The biggest takeaway for me when I talk to folks about DBIR around industries? Orgs that are willing and capable to report back to Verizon are already probably a step above the majority of the world. The reality is (IMO) the real world is much worse than what DBIR exposes. 40/x
@VZDBIR By themselves, these visualizations don't help me much, but when you can compare two major industries the multivariate data pops. Look at Financials vs Arts/Entertainment. Arts all over the place, Fi very grouped... My guess? Compliance MUCH tighter in Financials 41/x 



@VZDBIR That compliance is going to group those breaches into smaller buckets (is my hypothesis at least). Or maybe the Arts are all over the place because they like more colors. who knows. 42/x
@VZDBIR Cyber Politician TIP O'Neil once said "All Cyber is local" or something. I think it is vital that #CISO teams look at data like this and crunch it. Regionalities matter. What works for the Japan org may not work for the Monaco branch. I go back to, look at tickets and react 43/x 

OK, almost done! The wrap-up is great and read the @SecretService essay. Cool stuff. But I'm digging Appendix E. Ties to what I said earlier. Ransomware is a business and it's a numbers game. You can increase the cost to your adversary and ruin their profit margin 44/x 

OK All done. How did I do on my predictions?
- Ransomware was everywhere
- OT threat is up 200%!!! (looks away quickly)
- BEC is huge
- NOt really possible to judge
I give myself 2.5/4... OT did to up 200%... but only 1 -> 3% of data. 45/x
- Ransomware was everywhere
- OT threat is up 200%!!! (looks away quickly)
- BEC is huge
- NOt really possible to judge
I give myself 2.5/4... OT did to up 200%... but only 1 -> 3% of data. 45/x

Just a huge thanks to the authors of @VZDBIR: @idavehy @langloisSec @alexcpsec @SuzanneWidup. I'm a huge fan (obvs) and I love the data driven quasiAcademic nature of this report. It changes the industry for the better and I hope you and alumni like @wadebaker are proud! 44/44
• • •
Missing some Tweet in this thread? You can try to
force a refresh



