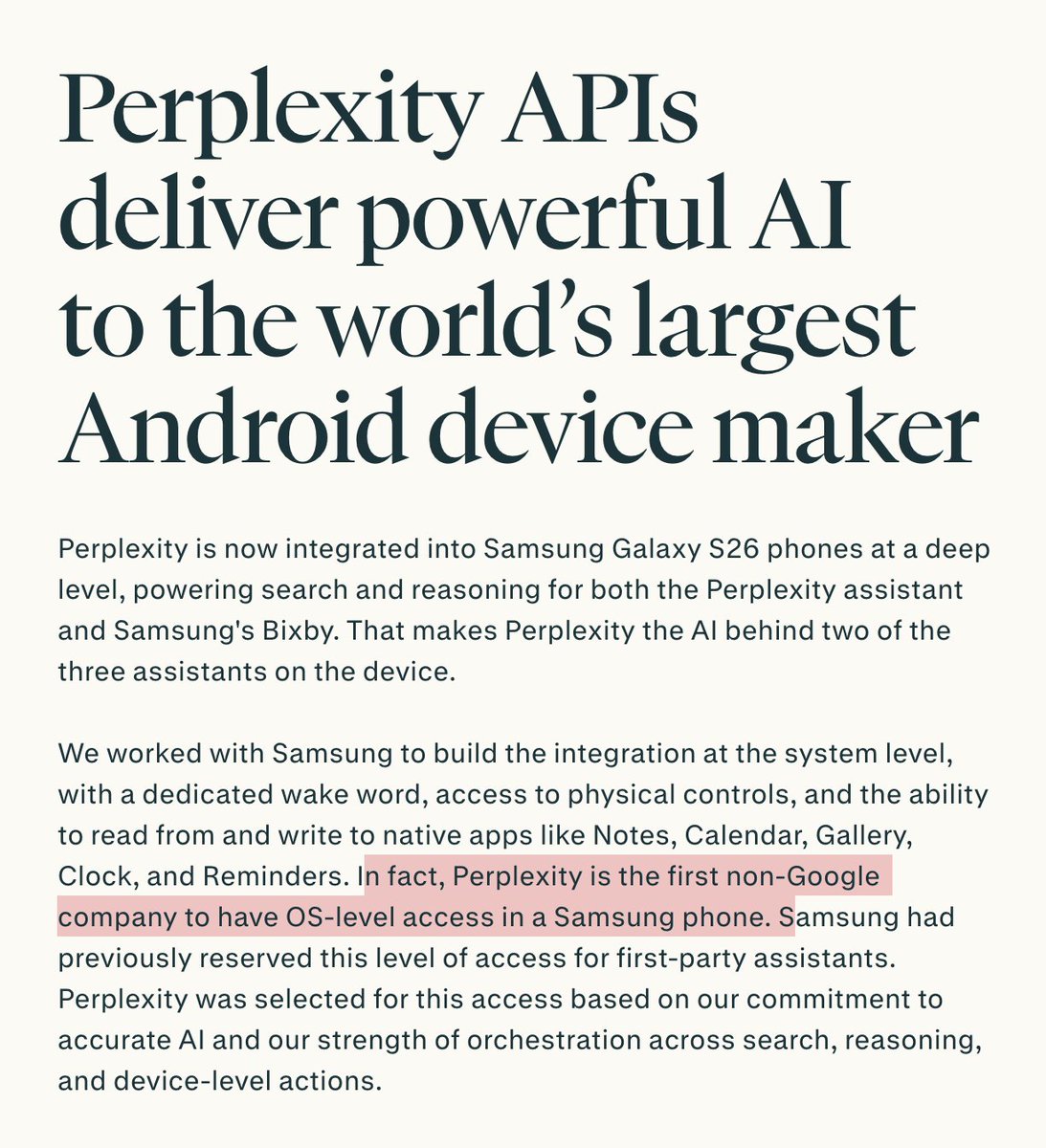
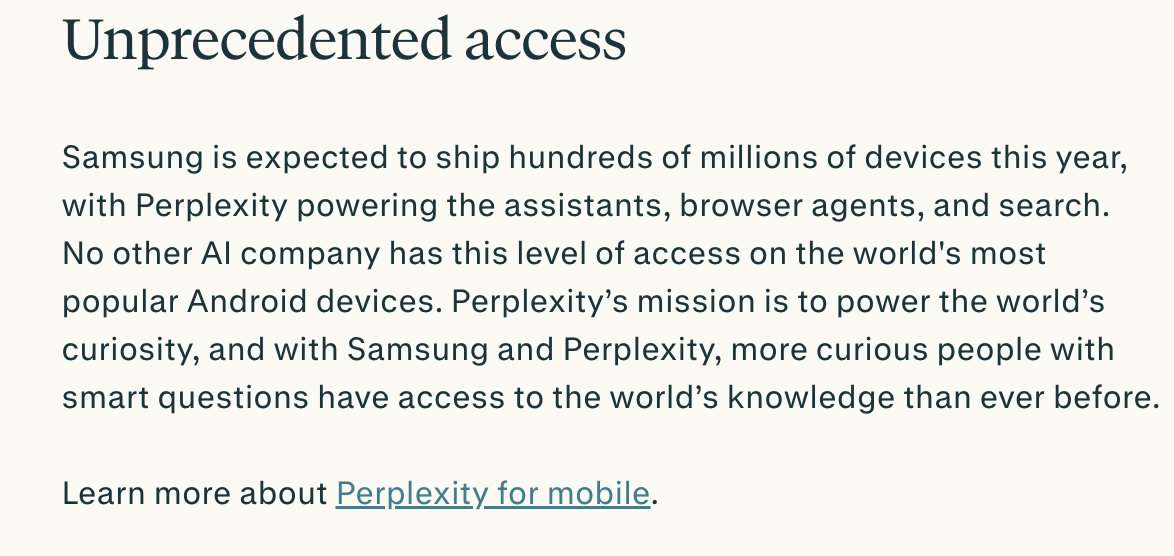
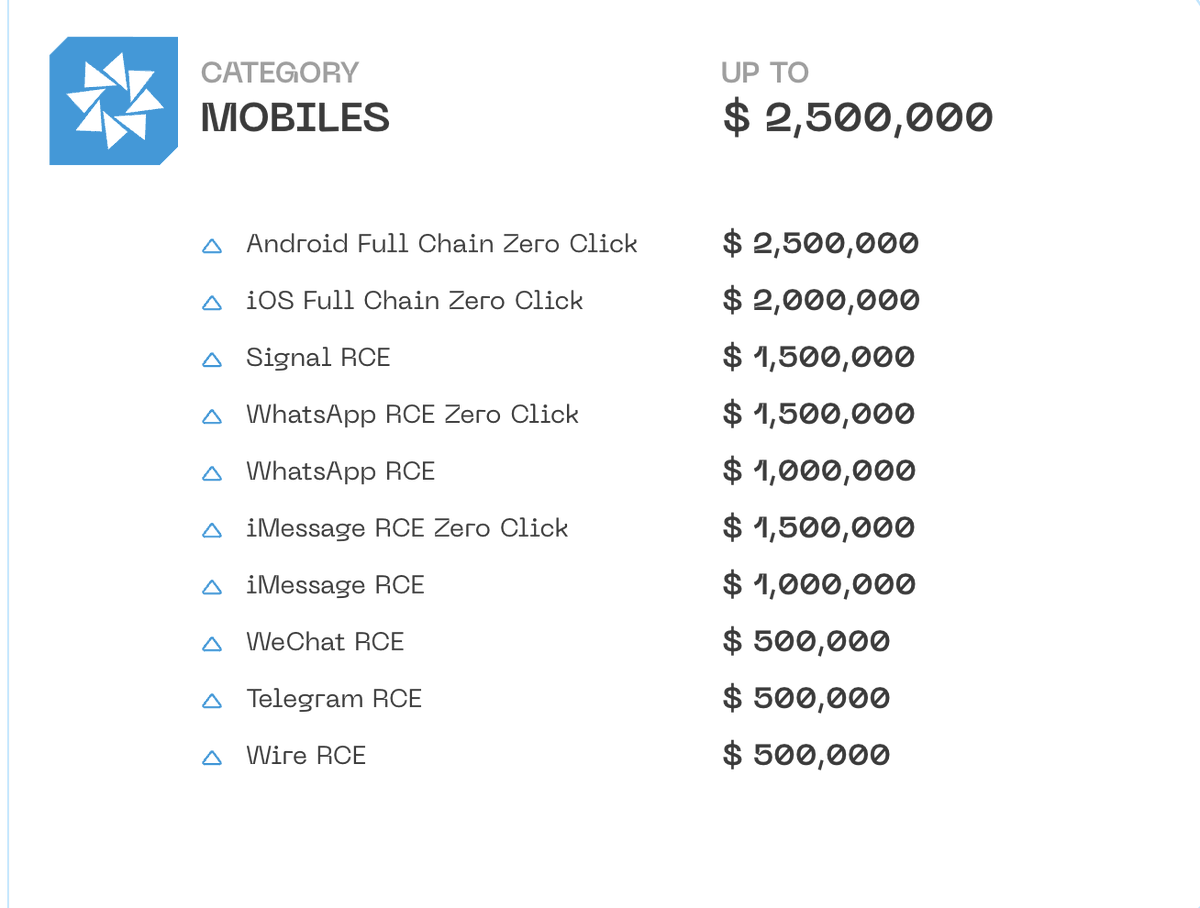
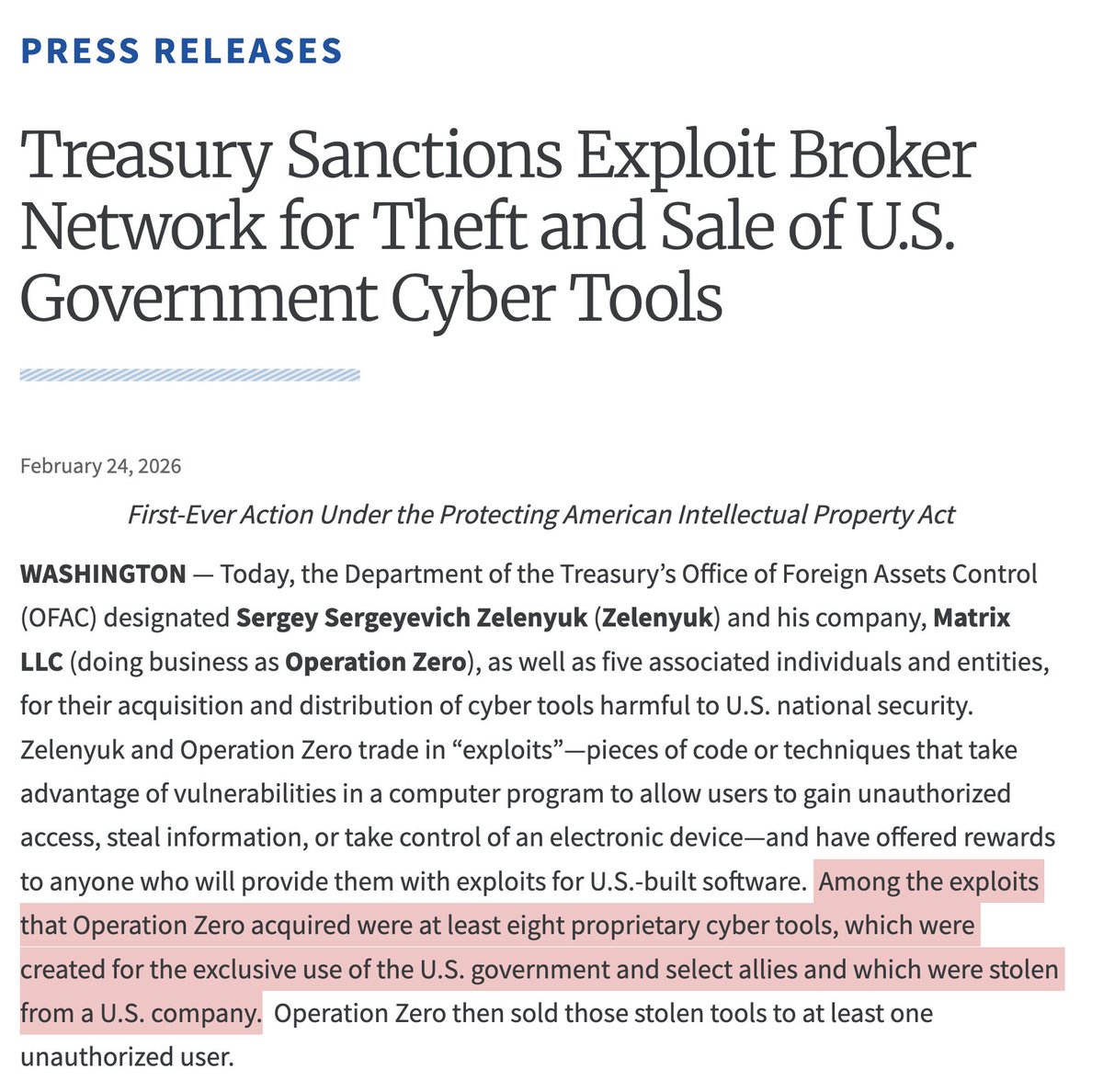
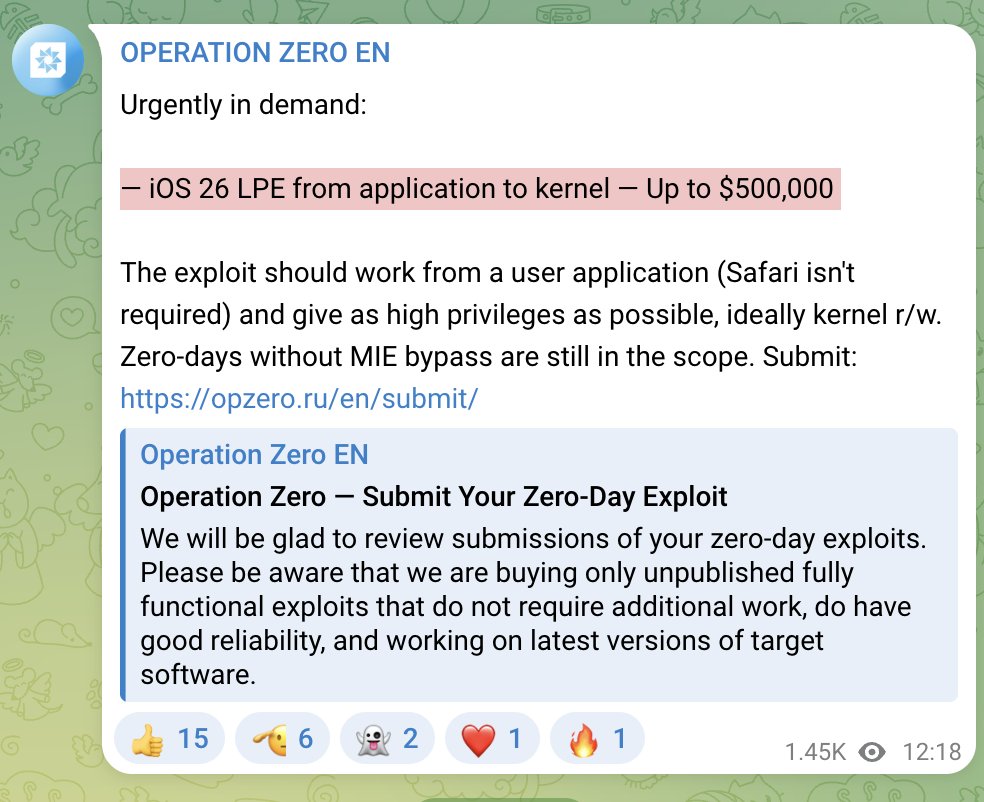
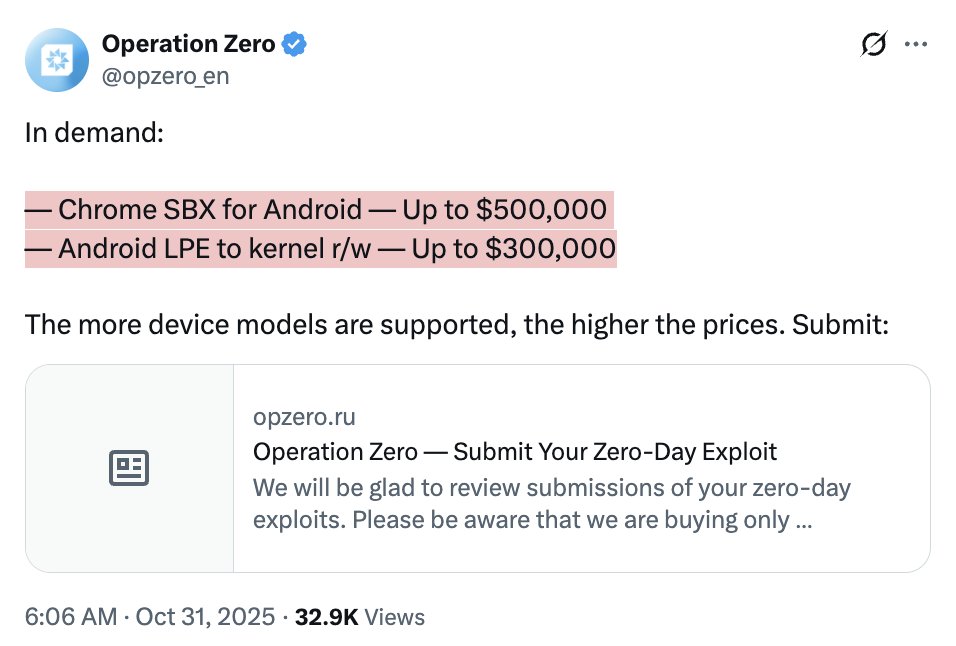
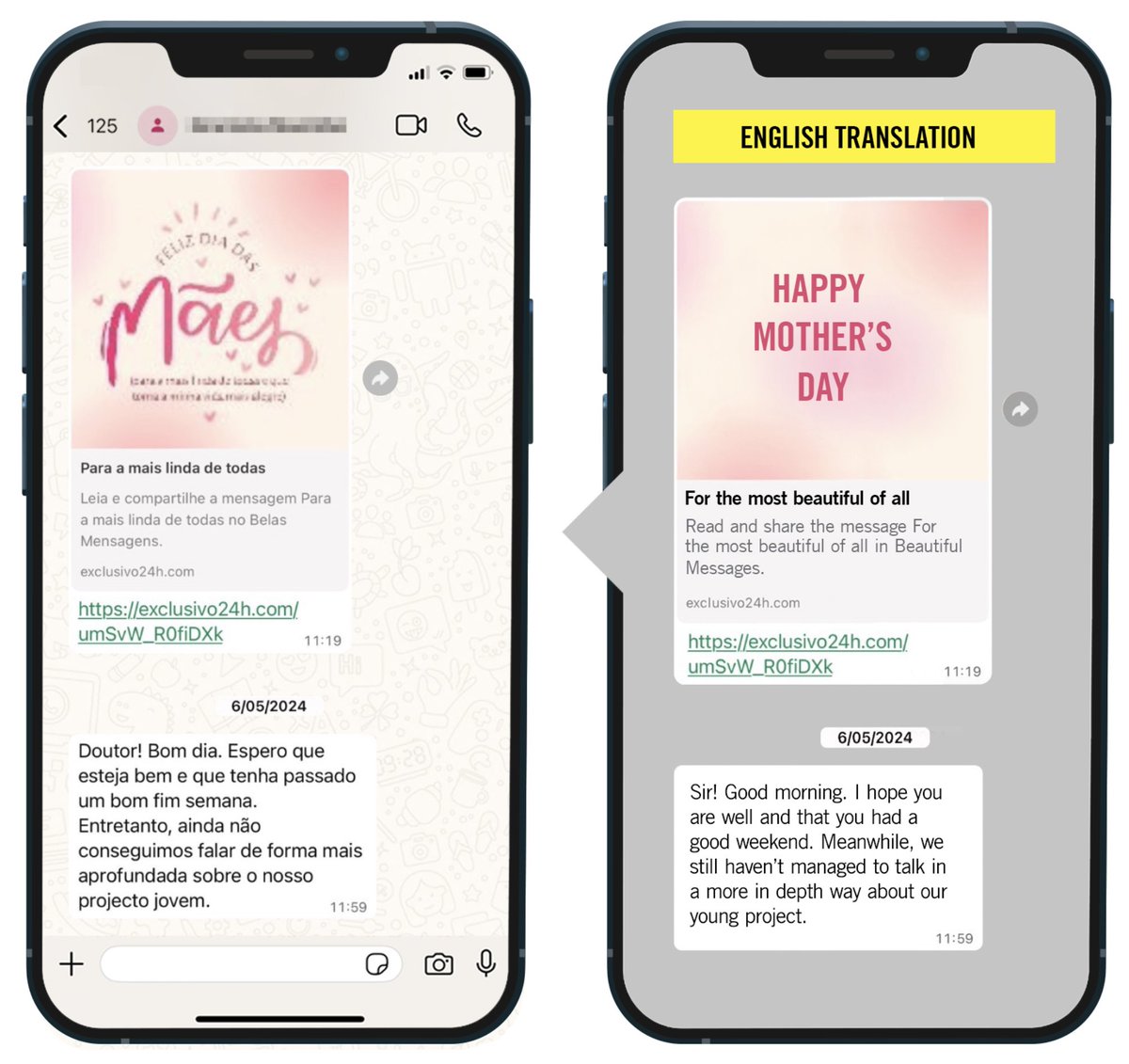
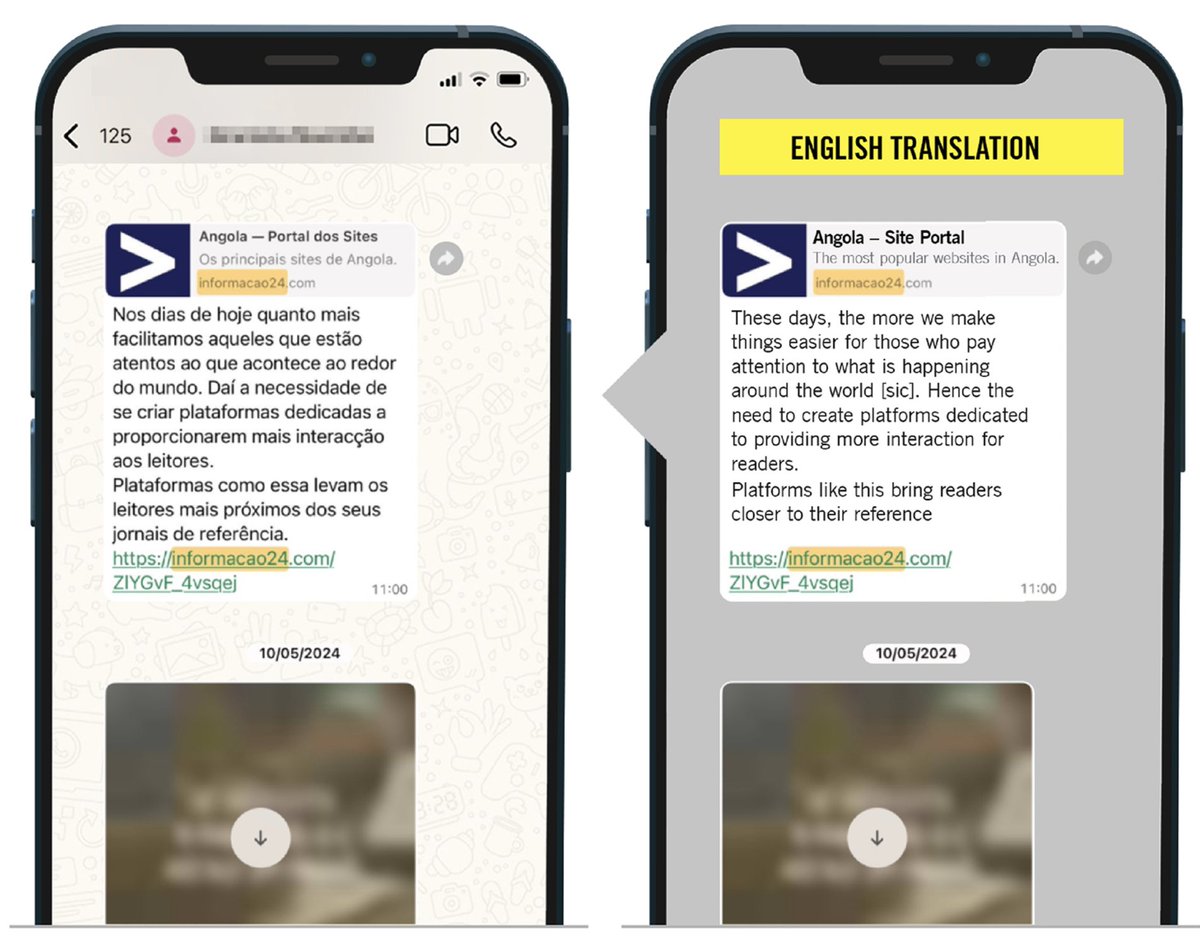
Just saw a wild armed politician video?
Felt a strong need to Quote Tweet?
That's because YOU are the target audience.
You're helping this person enter the news cycle.
Stop it.
Here's how: Quote Tweet friends, screenshot enemies.
Better yet, focus elsewhere.
Felt a strong need to Quote Tweet?
That's because YOU are the target audience.
You're helping this person enter the news cycle.
Stop it.
Here's how: Quote Tweet friends, screenshot enemies.
Better yet, focus elsewhere.

Your angry engagement is depressingly predictable.
Twitter doesn't know that a Quote Tweet means you disagree!
Politicians know this, and use it.
Your amplification signals to algorithms & traffic hungry editors that the person is relevant.
You are gifting them more exposure.
Twitter doesn't know that a Quote Tweet means you disagree!
Politicians know this, and use it.
Your amplification signals to algorithms & traffic hungry editors that the person is relevant.
You are gifting them more exposure.
Our enemies are Rage Farming us to victory.
Here's what you can do to fight the urge, right now.
With @MollyJongFast & @mehdirhasan
Full:
Here's what you can do to fight the urge, right now.
With @MollyJongFast & @mehdirhasan
Full:
Like donuts, rage farming content is *designed for dunking.*
To get the perfect dunk, big accounts share the content w/their followers.
Thus, they also get rewarded w/engagement for perpetuating the cycle.
The only winning move is not to play.
To get the perfect dunk, big accounts share the content w/their followers.
Thus, they also get rewarded w/engagement for perpetuating the cycle.
The only winning move is not to play.
Did you Quote Tweet a political ad?
You just donated free advertising.
Would you contribute a particular politician?
No? Then don't QT.
You just donated free advertising.
Would you contribute a particular politician?
No? Then don't QT.
Well, we did it. We got rage farmed into amplifying a disgraced toxic politician into a busy news cycle.
Next step? He'll claim censorship & that he's under attack by democrats.
Then fundraise.
This is an entirely predictable playbook.
Next step? He'll claim censorship & that he's under attack by democrats.
Then fundraise.
This is an entirely predictable playbook.

Step 1: Everyone watch this bad thing he did!
Step 2: We must drop everything & condemn him.
Step 3: Here's more bad things he did!
Step 4: Wait, why does his stuff drown out things we care about?
Meanwhile, all Twitter's algorithm hears is "SHOW US MORE OF HIM!"
Step 2: We must drop everything & condemn him.
Step 3: Here's more bad things he did!
Step 4: Wait, why does his stuff drown out things we care about?
Meanwhile, all Twitter's algorithm hears is "SHOW US MORE OF HIM!"
"So, should we ignore it when politicians say extreme things?"
No. We're in dark place & need to fight it.
But we must be smart, especially on Twitter.
That means learning how algorithms 'hear' us.
And making sure we aren't baited into inadvertently platforming our opponents.
No. We're in dark place & need to fight it.
But we must be smart, especially on Twitter.
That means learning how algorithms 'hear' us.
And making sure we aren't baited into inadvertently platforming our opponents.
Whomever cooked up his rage farming knew exactly what they were doing.
Predictably, he followed up by amplifying critical coverage in the WaPo that... included his video.
Of course, people angrily Quote Tweet that, too.
And so he's done it. And we've helped at every step.
Predictably, he followed up by amplifying critical coverage in the WaPo that... included his video.
Of course, people angrily Quote Tweet that, too.
And so he's done it. And we've helped at every step.
• • •
Missing some Tweet in this thread? You can try to
force a refresh