A hacker stole $100 million from the bridge connecting Ethereum and @harmonyprotocol a few hours ago.
Let's explore how the #harmony bridge works and what allowed this to happen 1/9
Let's explore how the #harmony bridge works and what allowed this to happen 1/9
The bridge is relatively simple - users lock tokens on the Ethereum side and a multisig mints tokens on Harmony.
When going the opposite way users burn tokens on Harmony and a multisig requiring 2 signatures unlocks tokens on Ethereum 2/9
When going the opposite way users burn tokens on Harmony and a multisig requiring 2 signatures unlocks tokens on Ethereum 2/9

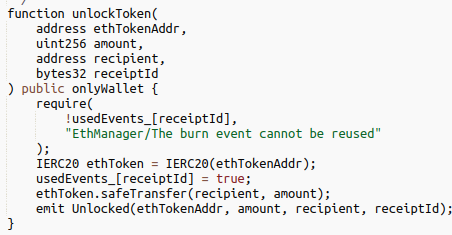
Every time an unlock happens on Ethereum the bridge smart contract emits an event that includes the transaction id of the associated burn transaction on the Harmony blockchain.
Let's follow a normal Harmony to Ethereum unlock 3/9
Let's follow a normal Harmony to Ethereum unlock 3/9
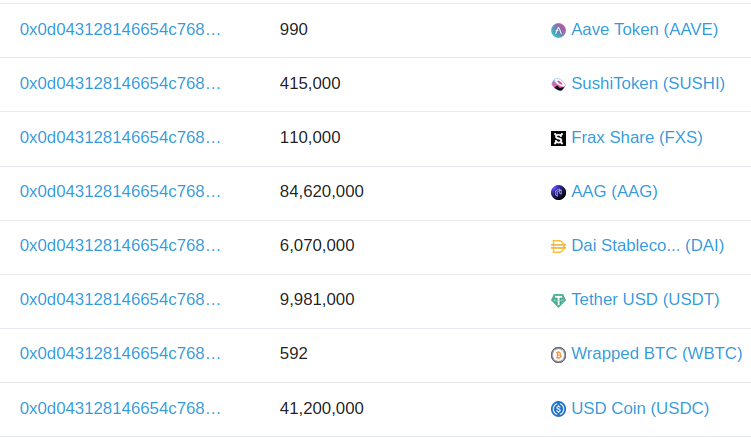
This was one of the last transactions before the bridge was paused: etherscan.io/tx/0x723a1dde9…
If we look at the emitted events we see that it's associated with the following Harmony transaction: explorer.harmony.one/tx/0x7cd65d048…
Everything looks fine. 4/9
If we look at the emitted events we see that it's associated with the following Harmony transaction: explorer.harmony.one/tx/0x7cd65d048…
Everything looks fine. 4/9
Now let's look at one of the transactions used to drain the bridge. $10 million USDT is unlocked on Ethereum: etherscan.io/tx/0x6487952d4…
The unlock is associated with the following transaction on Harmony: 0xD48D952695EDE26C0AC11A6028AB1BE6059E9D104B55208931A84E99EF5479B6
The unlock is associated with the following transaction on Harmony: 0xD48D952695EDE26C0AC11A6028AB1BE6059E9D104B55208931A84E99EF5479B6

However, no such transaction exists on Harmony. I looked for it in the block explorer, I also tried calling hmyv2_getTransactionReceipt from several Harmony RPC nodes but they all return null.
This is the case for all transactions initiated by the hacker. 6/9
This is the case for all transactions initiated by the hacker. 6/9
What does that mean?
If the attacker managed to unlock tokens on Ethereum without burning tokens on Harmony that most likely means that this is another Ronin-style hack. 7/9
If the attacker managed to unlock tokens on Ethereum without burning tokens on Harmony that most likely means that this is another Ronin-style hack. 7/9
The hacker probably managed to get access to the 2 private keys that are part of the multisig which can calls unlock() on the Ethereum side.
@_apedev wrote a thread a few months ago asking Harmony how these EOA are secured:
@_apedev wrote a thread a few months ago asking Harmony how these EOA are secured:
https://twitter.com/_apedev/status/1510007663832223751
This also explains why the Harmony team added more signers to the multisig after the hack.
Securing bridges is hard.
I hope this will serve as a reminder that even if your smart contracts are secure your off-chain code & opsec must be on point as well. 9/9
Securing bridges is hard.
I hope this will serve as a reminder that even if your smart contracts are secure your off-chain code & opsec must be on point as well. 9/9
• • •
Missing some Tweet in this thread? You can try to
force a refresh







