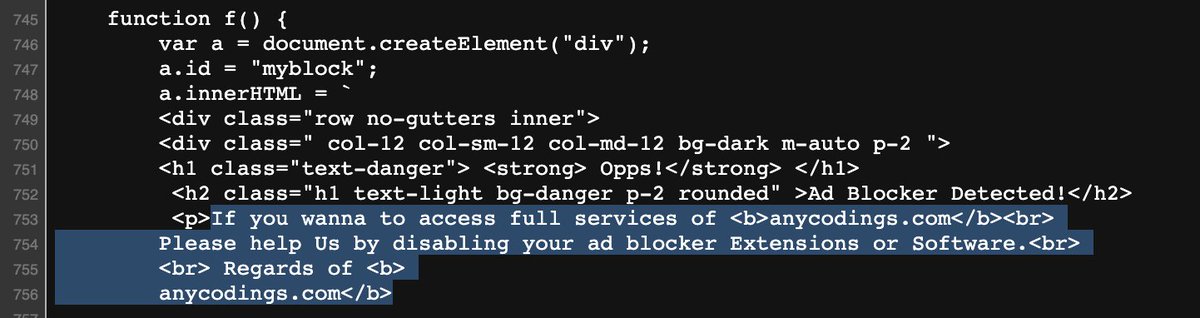
Stage 1: The injected site. These are compromised sites where a JavaScript implant is present in the HTML Source of the page.
These are plentiful (more than 1000 active at any time).
They come in 2 varieties currently:
1x B64 encoded and 2x B64 encoded
These are plentiful (more than 1000 active at any time).
They come in 2 varieties currently:
1x B64 encoded and 2x B64 encoded
Stage 2: Payload Host...aka the site Stage 1 pulls the "fakeupdate" from. (/report/blah)
These are less plentiful than Stage 1. Their TTL is measured in days or weeks. There are some currently that are approaching months.
These are a more reliable IOC to block vs Stage 1.
These are less plentiful than Stage 1. Their TTL is measured in days or weeks. There are some currently that are approaching months.
These are a more reliable IOC to block vs Stage 1.
Stage 3: SocGholish Payload aka the "fakeupdate".
The package is served in the form of a zip file, inside is a JavaScript file named [browser][digits]update.
When executed it executes WMIC queries via scripting host against the victim system. ...cont
The package is served in the form of a zip file, inside is a JavaScript file named [browser][digits]update.
When executed it executes WMIC queries via scripting host against the victim system. ...cont
Stage 3 cont.
This activity establishes persistence as well as executing recon. The big goal here is to determine what rights the user has, if the target host is joined to a domain.
All this data is sent to the STAGE 3 INFRA (aka) SG C2.
...cont
This activity establishes persistence as well as executing recon. The big goal here is to determine what rights the user has, if the target host is joined to a domain.
All this data is sent to the STAGE 3 INFRA (aka) SG C2.
...cont
Stage 3 cont.
Stage 3 INFRA (aka) SG C2s are even more stable than the stage 2 payload hosts though harder to get. You have to be able to defeat the logic checks to actually get the payload from Stage 2 and then decode the package to get the SG C2, which are host with /pixel.
Stage 3 INFRA (aka) SG C2s are even more stable than the stage 2 payload hosts though harder to get. You have to be able to defeat the logic checks to actually get the payload from Stage 2 and then decode the package to get the SG C2, which are host with /pixel.
Stage 4: Follow On
If the target host is joined to a domain (usually) Cobalt Strike is deployed. Goal is Ransomware deployment.
If not, a RAT DuJour is deployed...historically NetSupport Rat. Goal is infostealing.
Cont..
If the target host is joined to a domain (usually) Cobalt Strike is deployed. Goal is Ransomware deployment.
If not, a RAT DuJour is deployed...historically NetSupport Rat. Goal is infostealing.
Cont..
Stage 4 cont.
If Cobalt Strike is deployed we will be talking about another layer of infrastructure for C2 called a Teamserver.
If a RAT...RAT C2.
If Cobalt Strike is deployed we will be talking about another layer of infrastructure for C2 called a Teamserver.
If a RAT...RAT C2.
I didn't add all the details in the world here but I'm just trying to clarify a lot of the questions I get in my DMs every day. Hope this helps.
My goal is to try to move left on TA569 and to start getting blocks/kills/takedowns on infra as far left as is reasonably possible.
My goal is to try to move left on TA569 and to start getting blocks/kills/takedowns on infra as far left as is reasonably possible.
That is before a fakeupdate hits disk and an IR team uploads it to VT.
Happy Hunting!
Happy Hunting!
• • •
Missing some Tweet in this thread? You can try to
force a refresh