🔥最近RedLine黑客更新了产品视频,我们来看下他们的攻击手法、常用工具等:1/🧵
🔥The RedLine hackers have recently updated their product videos, so let's take a look at their attack techniques, common tools and more: 1/🧵
@SlowMist_Team @evilcos @wallet_guard
🔥The RedLine hackers have recently updated their product videos, so let's take a look at their attack techniques, common tools and more: 1/🧵
@SlowMist_Team @evilcos @wallet_guard
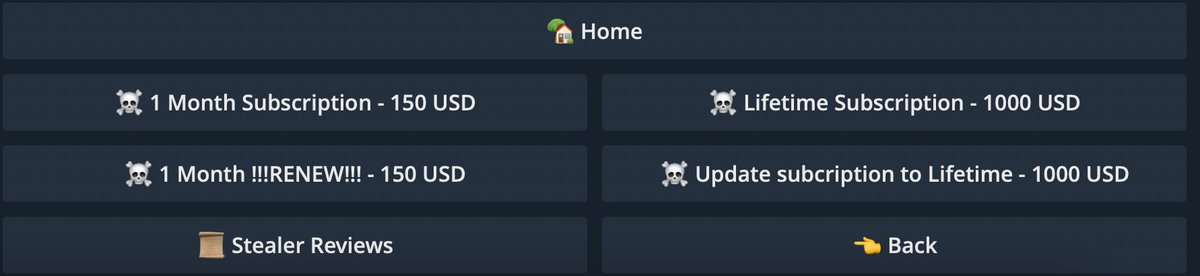
@SlowMist_Team @evilcos @wallet_guard 2/🧵首先他们是Saas服务,Bot恶意机器人的模式,通过下图这样的方式来传播、钓鱼虚拟货币用户:
Firstly they are Saas services, Bot malicious bots in the mode of spreading, phishing virtual currency users by means such as the following.
Firstly they are Saas services, Bot malicious bots in the mode of spreading, phishing virtual currency users by means such as the following.

@SlowMist_Team @evilcos @wallet_guard 3/🧵 教使用者如何通过社交网络、邮件钓鱼,使用什么在线工具绕过杀毒软件查杀、做SEO、投放诱饵
3/🧵 Teach users how to phish through social networks, emails, and what online tools to use to bypass anti-virus software、Doing SEO, placing bait
3/🧵 Teach users how to phish through social networks, emails, and what online tools to use to bypass anti-virus software、Doing SEO, placing bait

@SlowMist_Team @evilcos @wallet_guard 4/🧵攻击者是典型俄语使用者,视频用使用俄语、英语双语,电脑操作系统都是俄语。( 图:发送钓鱼邮件)
The attacker is a typical Russian speaker, the video is bilingual in Russian and English and the computer operating system is all in Russian
The attacker is a typical Russian speaker, the video is bilingual in Russian and English and the computer operating system is all in Russian
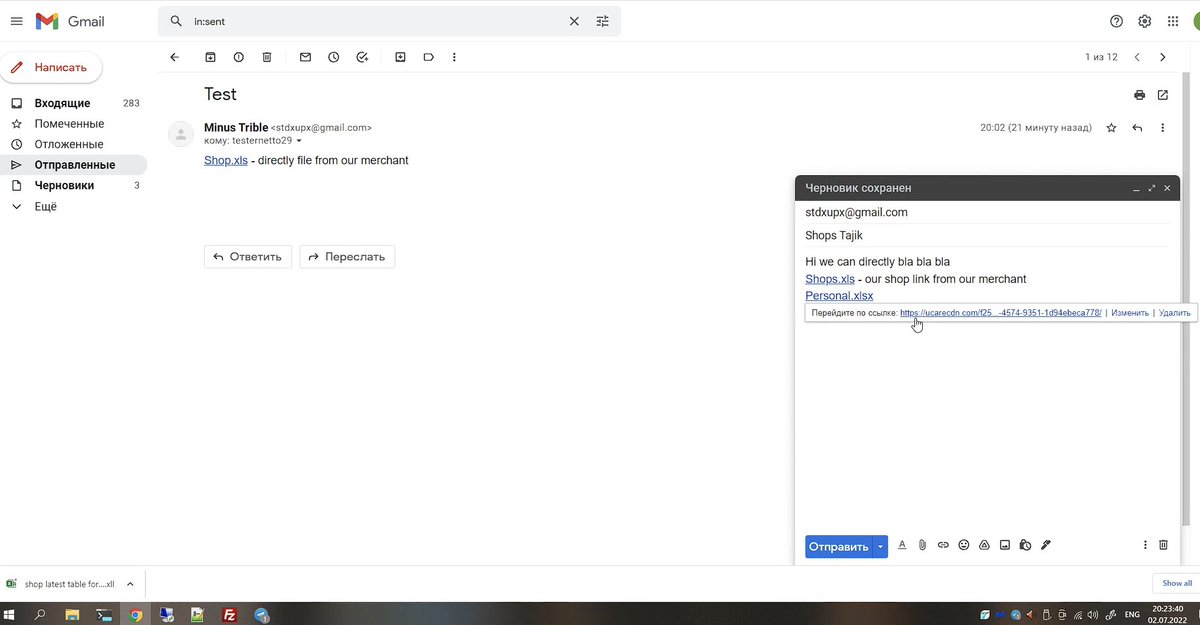
@SlowMist_Team @evilcos @wallet_guard 5/🧵各种专业的钓鱼、盗窃工具展示、使用,窃取虚拟货币。
Various professional fishing and theft tools on display and in use,Stealing virtual currency.


Various professional fishing and theft tools on display and in use,Stealing virtual currency.
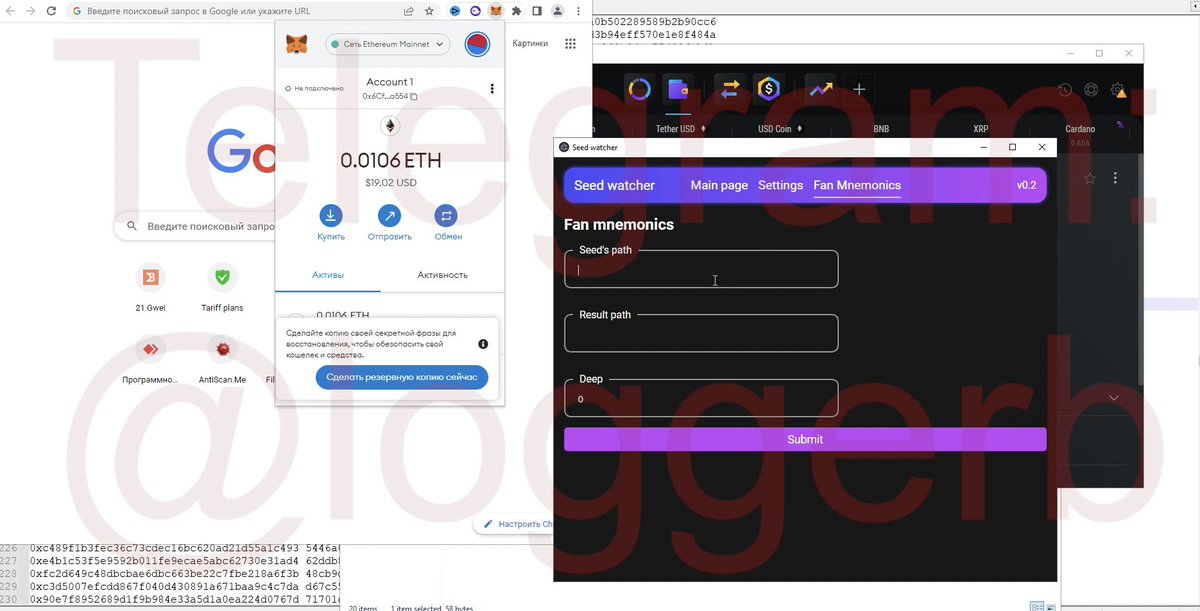
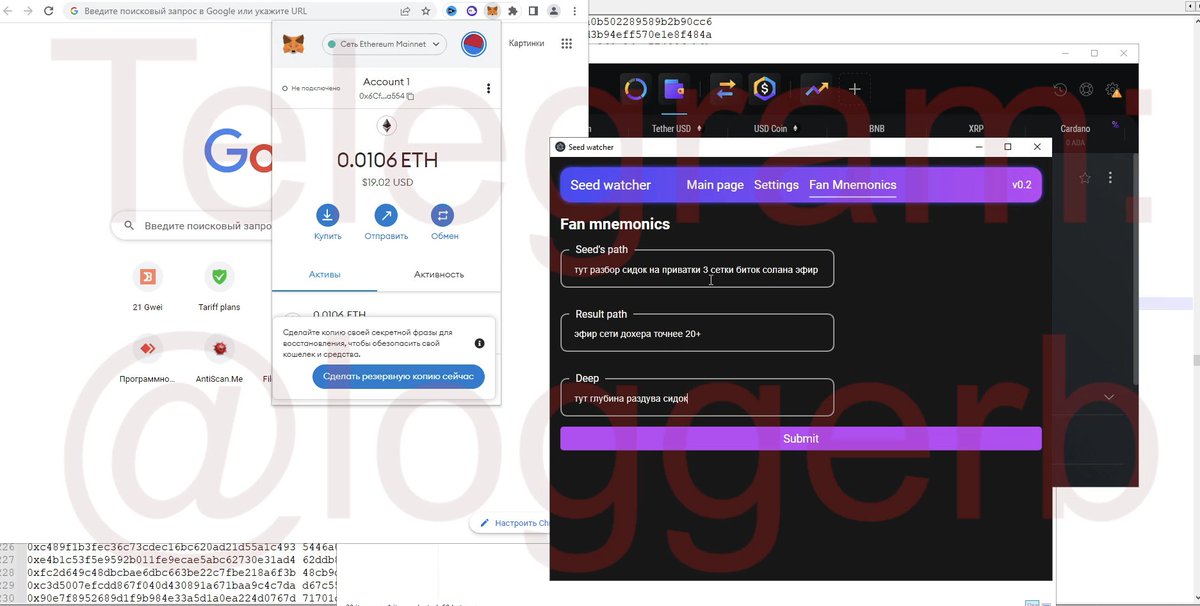
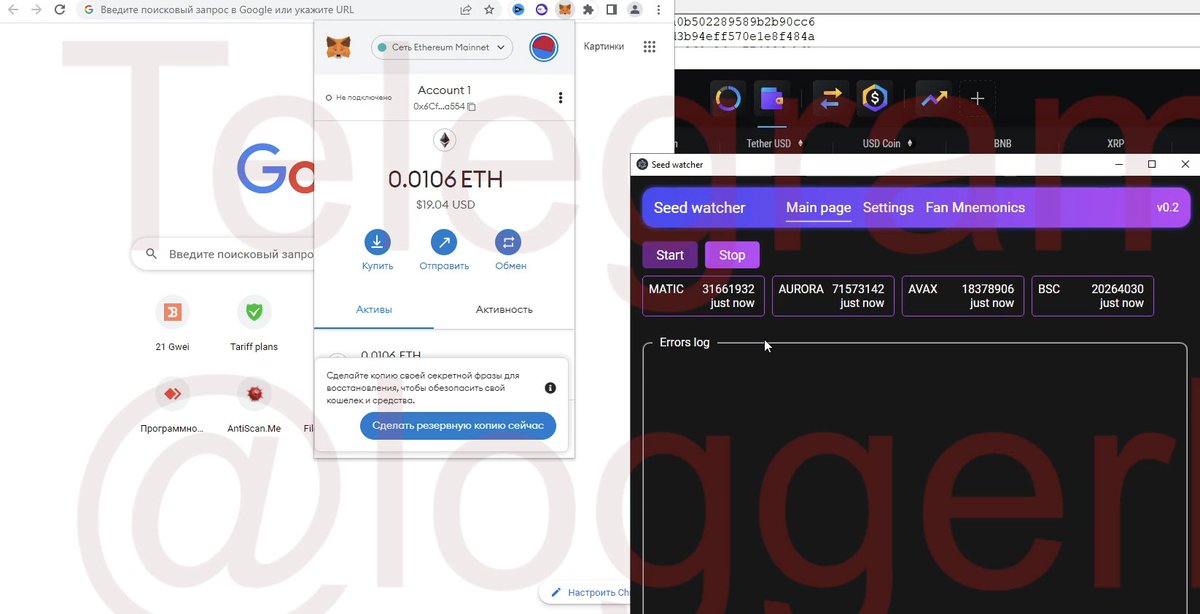
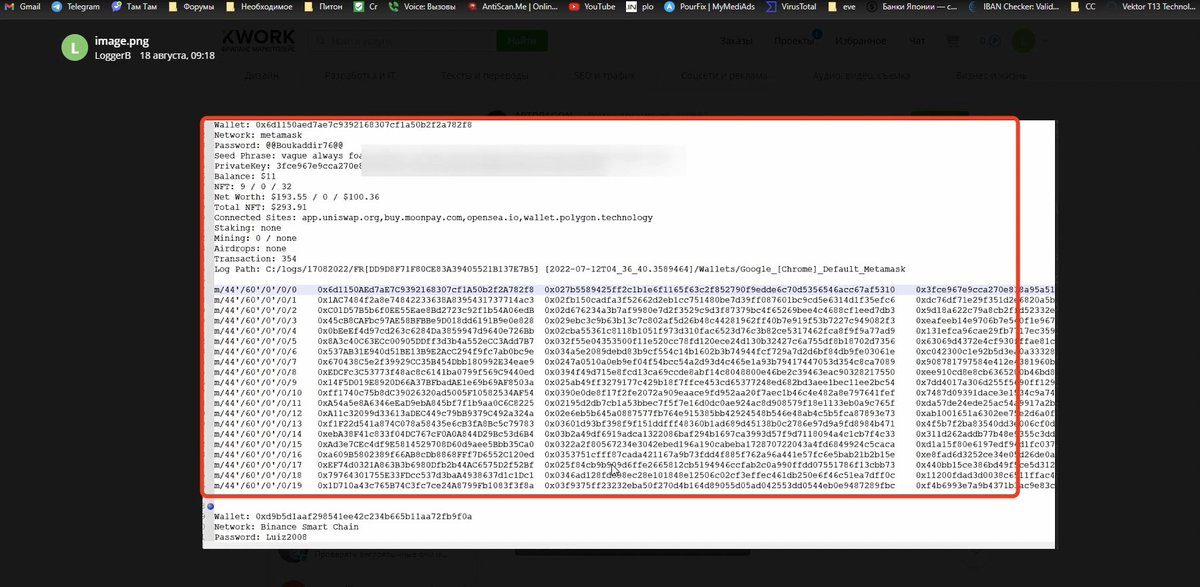
@SlowMist_Team @evilcos @wallet_guard 6/🧵专业盗窃木马,用户中招木马,木马就扫描本地电脑钱包、密码、私钥等上传到恶意服务器。
Professional theft Trojan, the user is hit by the Trojan and the Trojan scans the local computer for wallets, passwords, private keys, etc. and uploads them to a malicious server.
Professional theft Trojan, the user is hit by the Trojan and the Trojan scans the local computer for wallets, passwords, private keys, etc. and uploads them to a malicious server.

@SlowMist_Team @evilcos @wallet_guard 7/🧵演示密码、浏览器、加密货币钱包盗窃方式,可以看到使用的hashcat等专业黑客工具
Demonstration of password, browser, and cryptocurrency wallet theft, with the use of professional hacking tools such as hashcat visible



Demonstration of password, browser, and cryptocurrency wallet theft, with the use of professional hacking tools such as hashcat visible
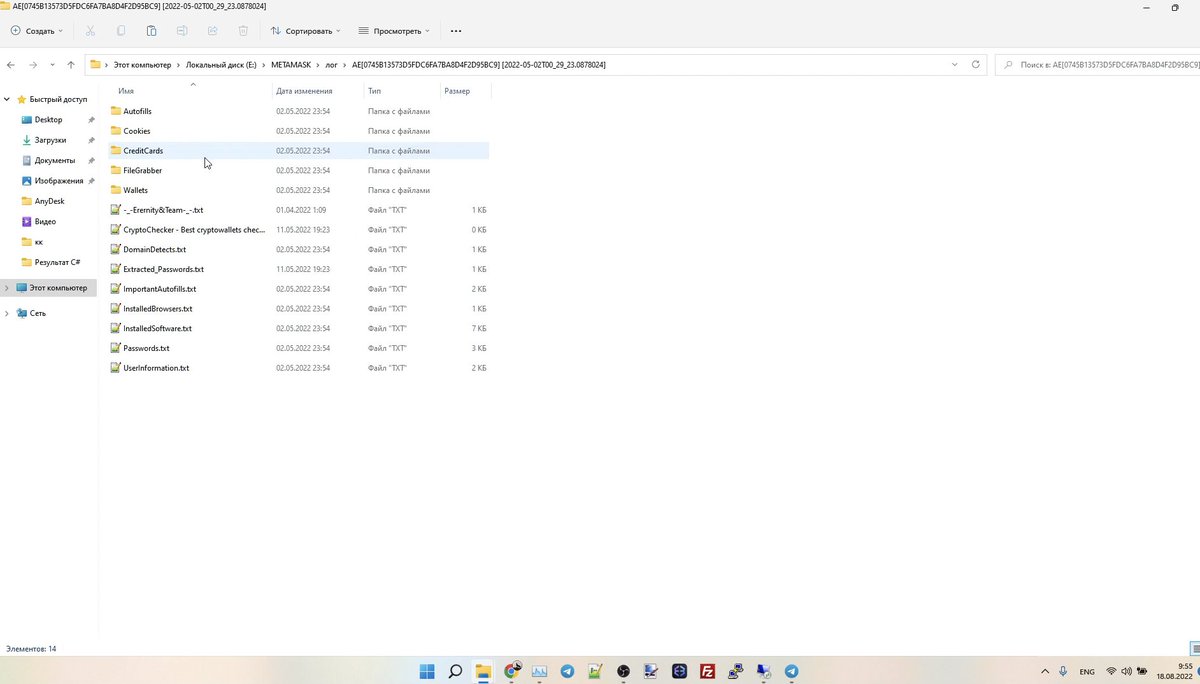
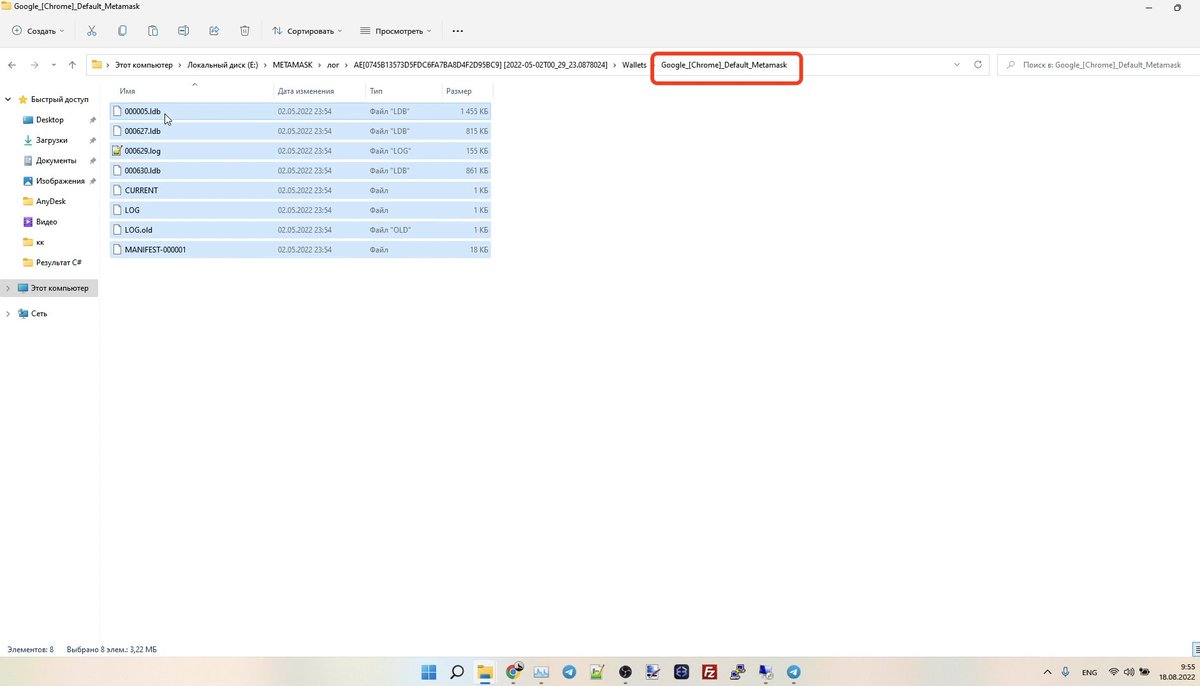
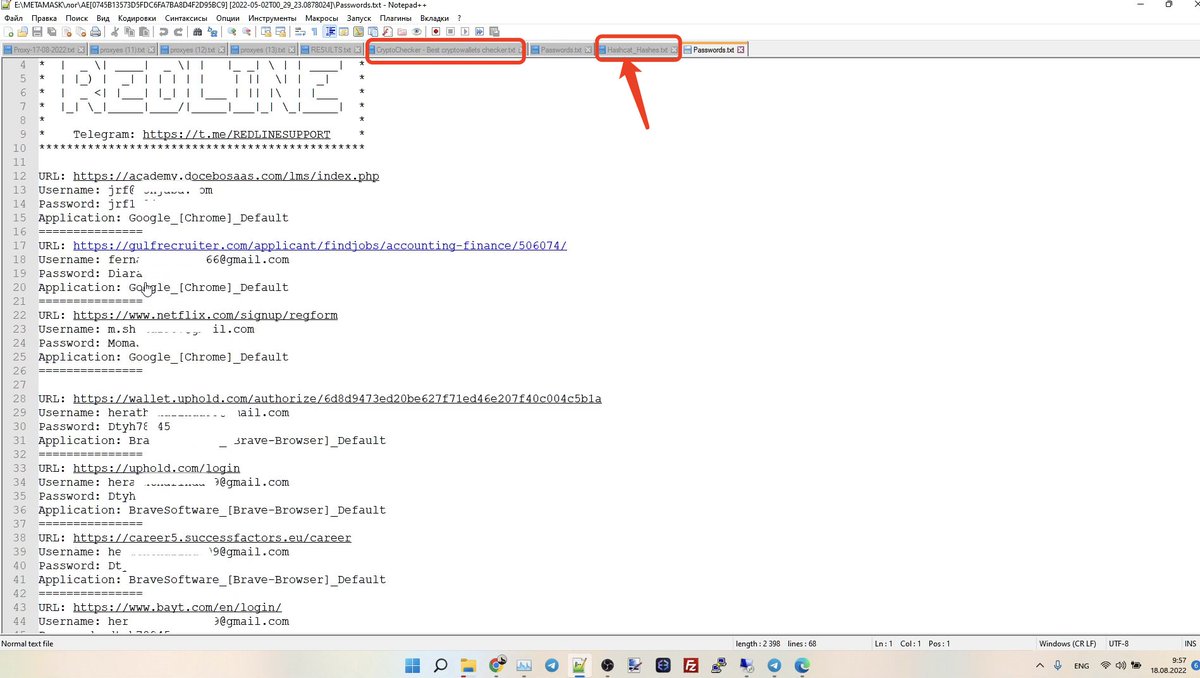
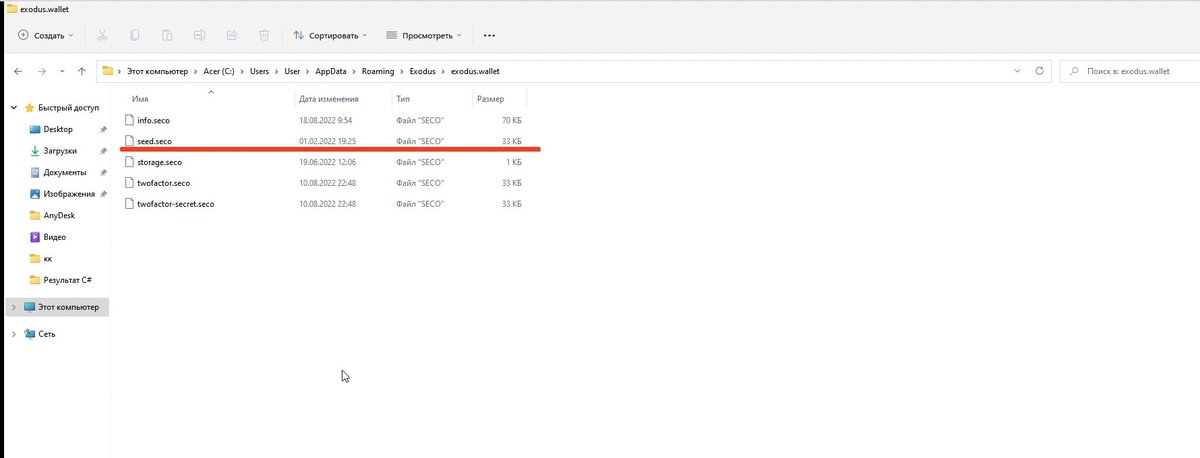
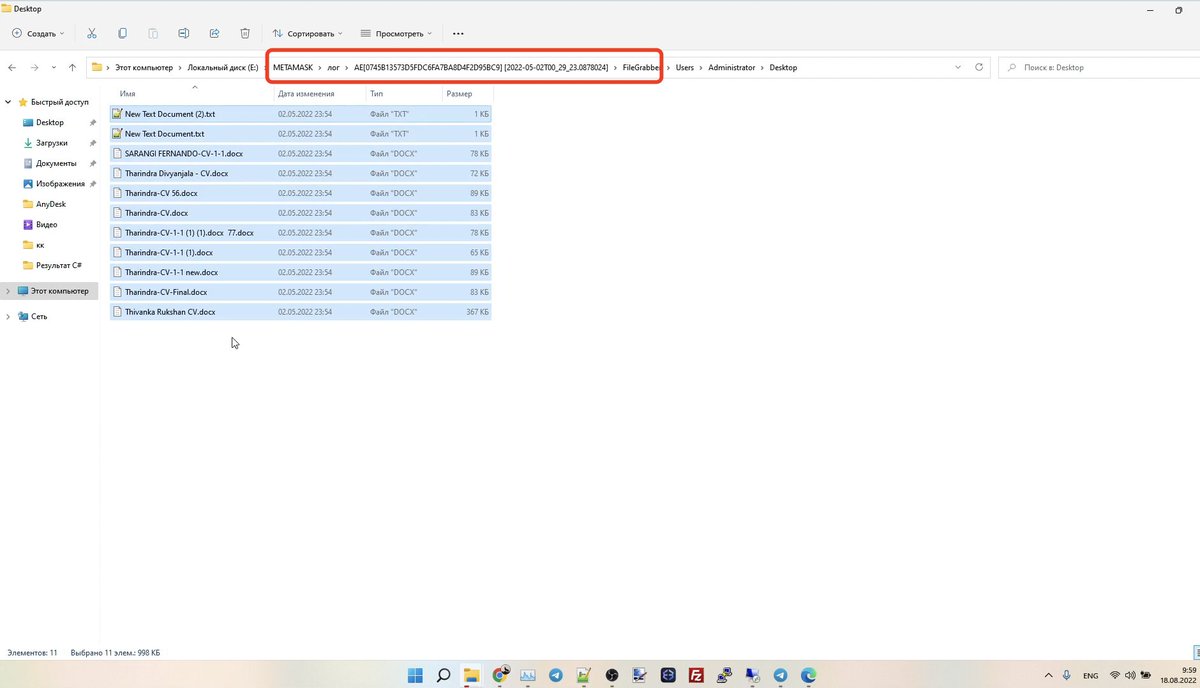
@SlowMist_Team @evilcos @wallet_guard 8/🧵 恶意软件记录的受害者详细信息。
Details of the victim recorded by the malware

Details of the victim recorded by the malware
@tayvano_ @NFTherder @keenz_eth @BoxMrChen @Mudit__Gupta Spread the word to prevent more people from being scammed. Thanks~
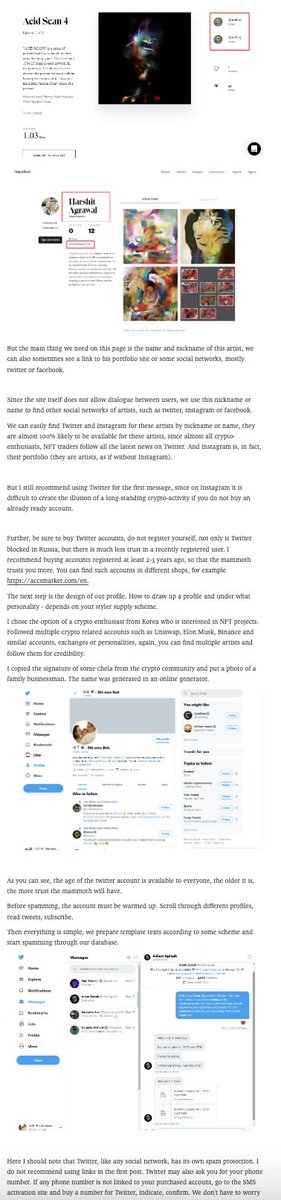
9/🧵而且远不止,包括最火的NFT,他们都有全套诈骗教程:伪造艺术家信息-伪造推特账号-发布作品-诈骗完成。And far more, including the hottest NFT, who have a full tutorial on scams: fake artist info - fake Twitter account - post work - scam complete. 
• • •
Missing some Tweet in this thread? You can try to
force a refresh