SSRF Story | Scan The Network
1. Found SSRF and get Cloud Metadata.
2. Common high risk with disclosed cloud metadata is about security credential, but not found at this point :(
3. Found the instance public IP in latest/meta-data/public-ipv4, access the IP and got 404 response


1. Found SSRF and get Cloud Metadata.
2. Common high risk with disclosed cloud metadata is about security credential, but not found at this point :(
3. Found the instance public IP in latest/meta-data/public-ipv4, access the IP and got 404 response



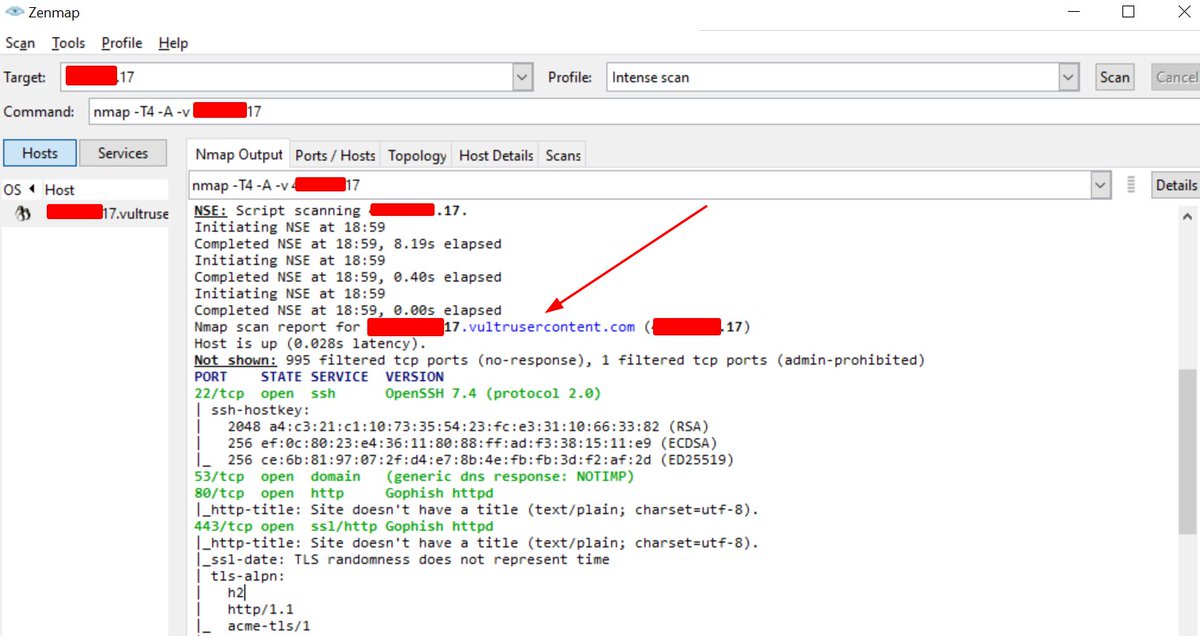
4. Nmap the IP, nmap identified the server was located in Vultr cloud provider with open port 22,53,80 and 443.
5. Trying to get more exposure with SSRF with scan all port.
6. Amazed, got some firewalled port, port 8080 was run the Traefik application.


5. Trying to get more exposure with SSRF with scan all port.
6. Amazed, got some firewalled port, port 8080 was run the Traefik application.


7. Found the Traefik API documentation, and trying to reach the every single endpoint but still got 404 response (?). Until get the information from the version endpoint that identified running version is v1.7.4, the reason that why API was different from the latest API doc. 



8. Go to Traefik repo and select 1.7.4 branch version to get API resources, apparently the API call can be performed without authentication!
9. API Security introduced in 2.0 version.

9. API Security introduced in 2.0 version.


10. Access the API endpoint through SSRF, and got very juicy information about infrastructure host application.
11. This information bring to the right path without having tired of guessing the internal network interfaces.
11. This information bring to the right path without having tired of guessing the internal network interfaces.

12. Now i can visit every single host and identifying more security hole possibilities.
13. Maybe i can start with graphql introspection, check the open-source based apps, or even with leaked source code price based apps.
14. Have fun!
#ssrf

13. Maybe i can start with graphql introspection, check the open-source based apps, or even with leaked source code price based apps.
14. Have fun!
#ssrf


• • •
Missing some Tweet in this thread? You can try to
force a refresh




