
I've just posted slides from my #OBTS v5 talk: "Making oRAT, Go" 🍎🐀
speakerdeck.com/patrickwardle/…
After creating a custom C&C server, we can uncover the malware’s full capabilities - simply by asking (tasking) the right questions! 🤭
speakerdeck.com/patrickwardle/…
After creating a custom C&C server, we can uncover the malware’s full capabilities - simply by asking (tasking) the right questions! 🤭
1️⃣ First, we must understand how the malware figures out how to find its C&C server - so we can coerce it to talk to our C&C instead!
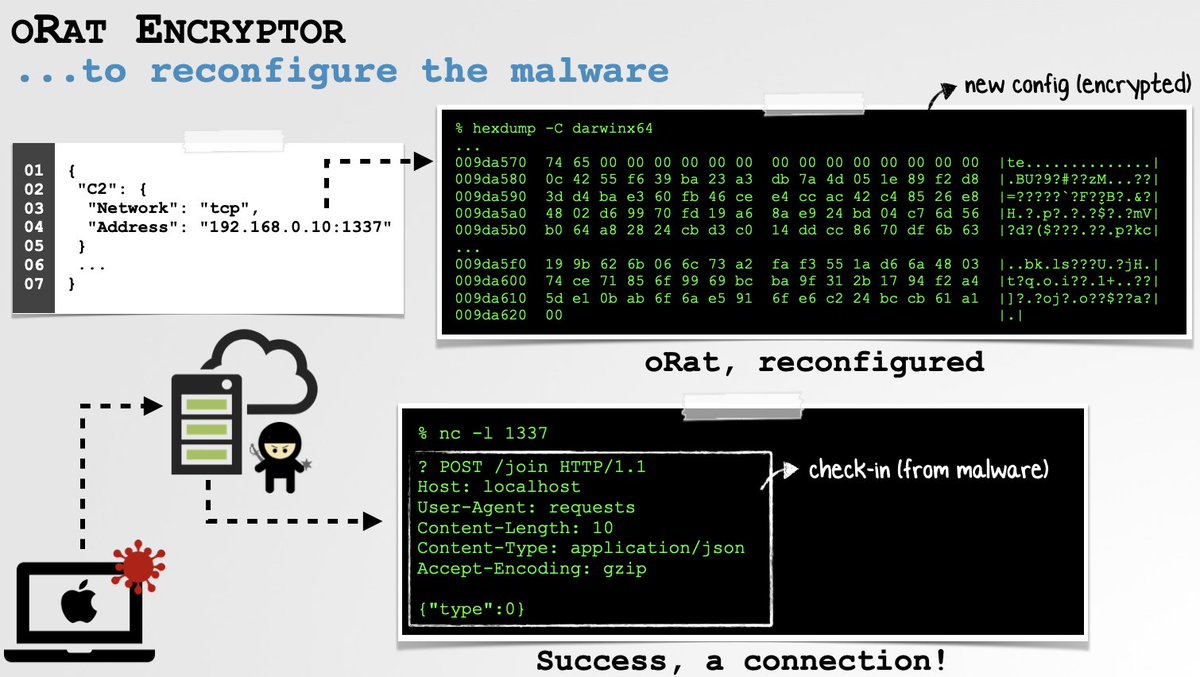
As this (encrypted) info is embedded within the malware, we can write a simple decryptor/encryptor to (re)configure the malware 👾🔓✍🏼🔒 → 🖥✅

As this (encrypted) info is embedded within the malware, we can write a simple decryptor/encryptor to (re)configure the malware 👾🔓✍🏼🔒 → 🖥✅

2️⃣ Second, we need to understand its protocol, so we can task the malware to reveal its capabilities.
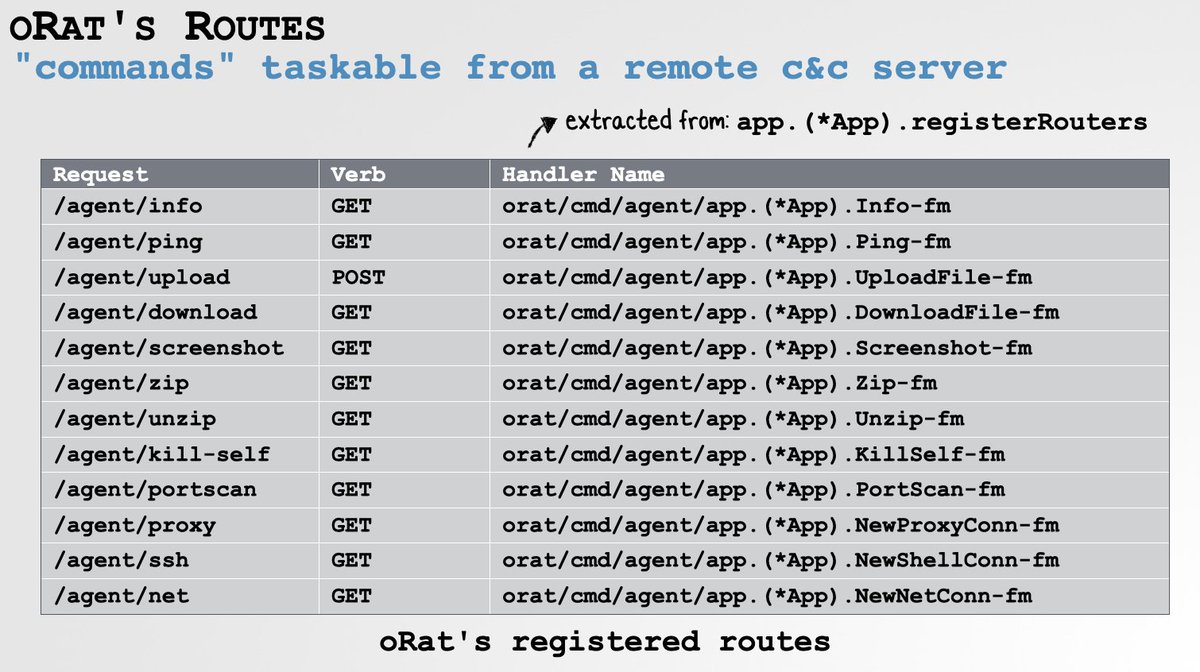
A brief triage of the malware's binary shows us it sets up a local server and registers various "routes" - taskable via requests from a remote C&C server.

A brief triage of the malware's binary shows us it sets up a local server and registers various "routes" - taskable via requests from a remote C&C server.

3️⃣ As the malware multiplexes all comms, our C&C server uses the same open-source mux library ("smux").
Our C&C can now task oRAT! 🤭
Via monitors tools (proc/file/network) + the malware's responses, we efficiently gain a comprehensive understanding of this insidious threat!💥



Our C&C can now task oRAT! 🤭
Via monitors tools (proc/file/network) + the malware's responses, we efficiently gain a comprehensive understanding of this insidious threat!💥




Worth noting, armed with a (re)configurable malware sample, plus a compatible C&C server, one could rather easily launch "plausibly-deniable" CNE campaigns 😈
...but of course we won't do that! 😇
...but of course we won't do that! 😇
👾 Grab an oRAT sample from @objective_see's malware collection: objective-see.com/downloads/malw… (pw: infect3d)
And mahalo to @TrendMicro for their initial oRat triage 🙏🏽🙏🏽
"New APT Group Earth Berberoka Targets Gambling Websites With Old and New Malware"
trendmicro.com/en_us/research…
And mahalo to @TrendMicro for their initial oRat triage 🙏🏽🙏🏽
"New APT Group Earth Berberoka Targets Gambling Websites With Old and New Malware"
trendmicro.com/en_us/research…
Slides also detail an 0day in Parallel's macOS installer, that affords a local unprivileged attacker or malware, root privs! 🔓👀 



• • •
Missing some Tweet in this thread? You can try to
force a refresh






