
🦖Day 36 of the @velocidex #velociraptor #ArtifactsOfAutumn series
Artifact: MacOS[.]System[.]QuarantineEvents
Link: docs.velociraptor.app/artifact_refer…
Artifact: MacOS[.]System[.]QuarantineEvents
Link: docs.velociraptor.app/artifact_refer…

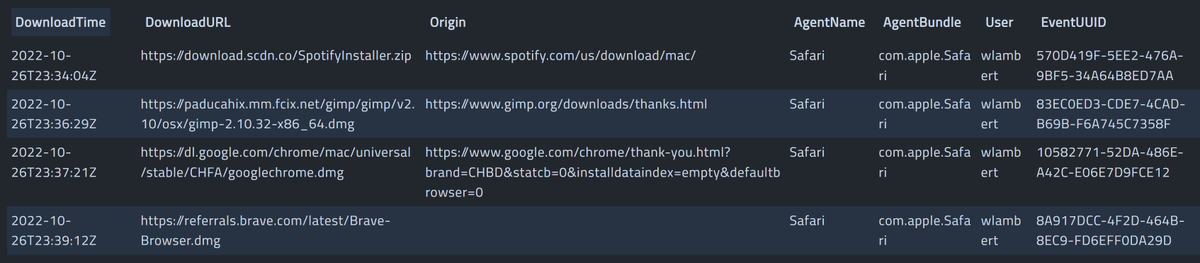
This artifact parses the 'com[.]apple.LaunchServices.QuarantineEventsV2' sqlite database to provide defenders with information around files that have been downloaded from the internet.
Information includes:
- DL Time
- DL URL
- Origin
- Agent Name/Bundle
- User
- Event UUID
Information includes:
- DL Time
- DL URL
- Origin
- Agent Name/Bundle
- User
- Event UUID
On macOS, when a user downloads a file from the internet/third party source, the file will have an extended attribute associated with it called 'com[.]apple.quarantine'.
This asserts that the file will not be opened/executed, until explicitly allowed by the user (via prompt).
This asserts that the file will not be opened/executed, until explicitly allowed by the user (via prompt).

If we look a little closer ('xattr -l'), we can actually see where the file came from, and a unique identifier assigned to it for the quarantine attribute.
This is excellent information to have as an incident responder, as it provides greater context during an investigation.
This is excellent information to have as an incident responder, as it provides greater context during an investigation.

We can interpret the value of the quarantine attribute as such:
'0083;6359d263;Safari;88E8F4A7-C78B-45B6-B31A-68E8C68DCC60'
0083 - Flags
6359d263 - DL time (Unix, in hex)
Safari - Name of DLing application
88E8F4A7-C78B-45B6-B31A-68E8C68DCC60 - UUID to tie in w/ QEvents DB
'0083;6359d263;Safari;88E8F4A7-C78B-45B6-B31A-68E8C68DCC60'
0083 - Flags
6359d263 - DL time (Unix, in hex)
Safari - Name of DLing application
88E8F4A7-C78B-45B6-B31A-68E8C68DCC60 - UUID to tie in w/ QEvents DB
In recent versions of macOS file downloads are recorded in the QuarantineEventsV2 sqlite database stored in '/Users/*/Library/Preferences/com[.]apple.LaunchServices.QuarantineEventsV2', regardless of whether the quarantine attribute gets removed from the file (approval/etc). 
As mentioned previously, we can see the associated UUID ('88E8F4A7-C78B-45B6-B31A-68E8C68DCC60') used for tracking the download in the database, as evidenced in the extended 'quarantine' attribute for the file (image). 

To recap, this is a great way to confirm a particular file was downloaded, or to gather insight into what files have been downloaded by a user, in general.
Using this artifact across a fleet of many hosts, we can identity outliers and commonalities at scale.
Using this artifact across a fleet of many hosts, we can identity outliers and commonalities at scale.
That's it for now! Stay tuned to learn about more artifacts! 🦖
Also, check out the article below by @0xmachos for more information about macOS quarantine functionality!
0xmachos.com/2019-02-01-Qua…
#DFIR
#Infosec
#ThreatHunting
Also, check out the article below by @0xmachos for more information about macOS quarantine functionality!
0xmachos.com/2019-02-01-Qua…
#DFIR
#Infosec
#ThreatHunting
• • •
Missing some Tweet in this thread? You can try to
force a refresh











