Day 0⃣4⃣/2⃣0⃣ -- [Hacking A Web Application Via Password Change Functionality]
➡️ Day 4, Hack A Web Application Via "Password Change Functionality"
➡️ Below are Tips & References (Feel Free To Share)🧵🧵👇👇
#BugBounty
#bugbountytips
#cybersecuritytips "No Resting Only Hacking!"
➡️ Day 4, Hack A Web Application Via "Password Change Functionality"
➡️ Below are Tips & References (Feel Free To Share)🧵🧵👇👇
#BugBounty
#bugbountytips
#cybersecuritytips "No Resting Only Hacking!"
5/n
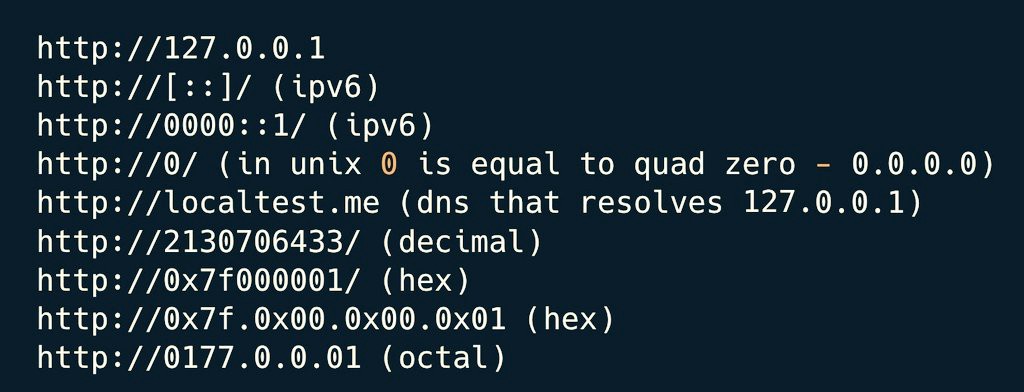
Weak Password Reset Implementation - Token Leakage via Host Header Poisoning
medium.com/@sathvika03/we…
Weak Password Reset Implementation - Token Leakage via Host Header Poisoning
medium.com/@sathvika03/we…
6/n
Weak Password Reset Implementation - Rather than generating a new password for the user, some applications will send the user their existing password. This is a very insecure approach, as it exposes their current password over unencrypted email.
Weak Password Reset Implementation - Rather than generating a new password for the user, some applications will send the user their existing password. This is a very insecure approach, as it exposes their current password over unencrypted email.
7/n
Weak Password Reset Implementation - Token is Not Invalidated After Use
Weak Password Reset Implementation - Token is Not Invalidated After Use
8/n
Password Reset token/link is not invalidated after use
Password Reset token/link is not invalidated after use
10/n
Password link encoded in base64.
Password link encoded in base64.
11/n
Reset password bypassing the current password.
Reset password bypassing the current password.
12/n
Password Reset Link Leaked In Refer Header In Request To Third Party Sites
hackerone.com/reports/751581
Password Reset Link Leaked In Refer Header In Request To Third Party Sites
hackerone.com/reports/751581
19/n
“Let me reset your password and login into your account “-How I was able to Compromise any User Account via Reset Password Functionality
infosecwriteups.com/bugbounty-how-…
“Let me reset your password and login into your account “-How I was able to Compromise any User Account via Reset Password Functionality
infosecwriteups.com/bugbounty-how-…
20/n
Remote Command Execution(RCE) Vulnerability PoC
Remote Command Execution(RCE) Vulnerability PoC
n/n
Practice Makes Perfect!
Have a lovely weekend, Don't Drink & Drive!
Happy Hacking :)
See you here same time tomorrow!
Practice Makes Perfect!
Have a lovely weekend, Don't Drink & Drive!
Happy Hacking :)
See you here same time tomorrow!
• • •
Missing some Tweet in this thread? You can try to
force a refresh