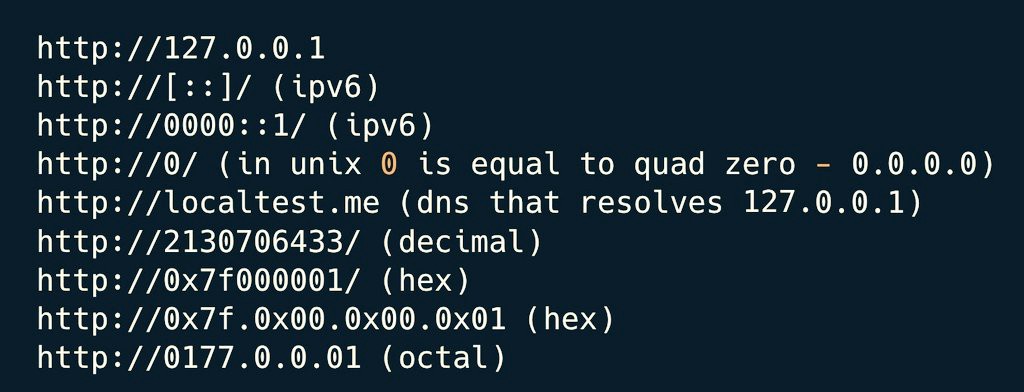
Day 0⃣5⃣/2⃣0⃣ -- [Web Application Profile/Dashboard Hacking]
➡️ Day 5, Profile Update/Dashboard Vulnerabilities & References.
➡️ Below are Tips & References (Feel Free To Share)🧵🧵👇👇
#BugBounty
#bugbountytips
#cybersecuritytips
➡️ Day 5, Profile Update/Dashboard Vulnerabilities & References.
➡️ Below are Tips & References (Feel Free To Share)🧵🧵👇👇
#BugBounty
#bugbountytips
#cybersecuritytips
1/n
IDOR on the dashboard
IDOR on the dashboard
2/n
Instagram IDOR
Instagram IDOR
3/n
OS Command Injection
OS Command Injection
4/n
Stored XSS on profile dashboard POC
Stored XSS on profile dashboard POC
5/n
Stored XSS Filter bypass on dashboard
Stored XSS Filter bypass on dashboard
6/n
Remote Command Execution(RCE) Vulnerability PoC
Remote Command Execution(RCE) Vulnerability PoC
7/n
CSRF while adding an Address Book
CSRF while adding an Address Book
8/n
Hot to test for CSRF
Hot to test for CSRF
9/n
Change Email & Password CSRF
Change Email & Password CSRF
10/n
CSRF while adding a payment method
CSRF while adding a payment method
11/n
PayPal CSRF that leads to adding a donate button
PayPal CSRF that leads to adding a donate button
12/n
Application Layer DDOS while adding an Address/Manage Address Book
Application Layer DDOS while adding an Address/Manage Address Book
13/n
RCE via File Upload in MartDevelopers-Inc/KEA-Hotel-ERP
RCE via File Upload in MartDevelopers-Inc/KEA-Hotel-ERP
14/n
Tesla Lack Of Password/Authentication When Disabling 2FA.
Tesla Lack Of Password/Authentication When Disabling 2FA.
15/n
Email Change Confirmation Bypass
Email Change Confirmation Bypass
n/n
Practice Makes Perfect!
Happy Hacking :)
See you here same time tomorrow!
Practice Makes Perfect!
Happy Hacking :)
See you here same time tomorrow!
• • •
Missing some Tweet in this thread? You can try to
force a refresh